
Introduction and trends
The gaming industry continues growing. The Newzoo report for 2023 reveals that two in five — more than three billion — across the globe are gamers, which is 6.3 percent more than last year.
Globally, gaming revenue amounts to an estimated US$242.39 billion, with almost half of that generated by the Asia Pacific. By the year 2030, this worldwide total is expected to more than double to US$583.69 billion.
New game titles have appeared this year, such as The Legend of Zelda: Tears of the Kingdom, Hogwarts Legacy and Star Wars Jedi: Survivor, while older titles have continued to be popular with fans. Millions around the world are still building new worlds in Minecraft and honing their skills in multiplayer online battle arenas, such as Defense of the Ancients (DOTA 2), and tactical shooters, such as Counter-Strike: Global Offensive (CS:GO), with the latter only growing in popularity.
With the revenue and the number of gamers on the rise, the gaming industry continues to be a lucrative target for cybercriminals, with long-awaited and just popular titles being used as a lure in malicious campaigns. Given that nearly a quarter of players were underage as of 2022, they may be easy prey for the attackers. In this report, we provide our insights into the gaming-related threat landscape in 2023.
Methodology
To gain an insight into the current landscape of gaming-related cybersecurity risks, Kaspersky has conducted extensive research into prevalent threats targeting the gaming community. Our investigation encompassed attacks that involved threats disguised as game apps, mods and cheats, and features analysis of some of the most active malware families operating in this domain. We also analyzed phishing pages using various game titles and gaming platforms as a lure. Our analysis drew on data sourced from the Kaspersky Security Network (KSN), which is a system for processing anonymized cyberthreat-related data shared voluntarily by Kaspersky users, from July 1, 2022 to July 1, 2023.
Kaspersky experts researched threats related to the top 14 games available for download or poised for release on streaming platforms, such as Origin and Steam, as well as platform-agnostic titles, to provide a comprehensive overview of current threats. The list of titles is based on several rankings of the most popular games available on the internet.
Our team analyzed threats associated with mobile (where applicable) and desktop versions of Minecraft, Roblox, Counter-Strike: Global Offensive (CS:GO), PlayerUnknown’s Battlegrounds (PUBG), Hogwarts Legacy, Defense of the Ancients 2 (DOTA 2), League of Legends, World of Warcraft, Apex Legends, Diablo IV, Star Wars Jedi: Survivor, The Legend of Zelda, Baldur’s Gate 3 and Final Fantasy XVI.
Key findings
From July 1, 2022 to July 1, 2023:
- In total, Kaspersky detected 4,076,530 game-related desktop infection attempts over the past year, which affected 192,456 gamers worldwide.
- The most common threat was Downloaders (89.70%), followed by Adware (5.25%) and Trojans (2.39%).
- The top game used as a lure was Minecraft, which saw 70.29% of all detections, followed by Roblox (20.37%), Counter-Strike: Global Offensive (4.78%) and PlayerUnknown’s Battlegrounds (2.85%).
- Our mobile solutions detected 436,786 gaming-related infection attempts that affected 84,539 users.
- Minecraft users (90.37%) were the biggest targets for mobile malware, with PlayerUnknown’s Battlegrounds (5.09%), Roblox (3.33%) and Baldur’s Gate (0.68%) being the next most often used lures.
Desktop statistics: Minecraft still a big malware target
From July 1, 2022 to July 1, 2023, Kaspersky solutions detected 4,076,530 attempts to download a total of 30,684 unique files, which were being distributed under the guise of popular games or mods, cheats and other game-related software, and affected 192,456 users worldwide. Most of these files were unwanted software called “Downloaders” (89.70%). Not dangerous in itself, this type of software downloads various other programs including malware onto the device. Adware (5.25%) and Trojans (2.39%) were also in the top three desktop gaming-related threats.
TOP 10 threats using popular games as a lure, July 1, 2022 to July 1, 2023 (download)
Of the 14 games we chose for this research, Minecraft (70.29%) remained the most popular one with cybercriminals. This evergreen sandbox game has more than 160 million monthly active players in 2023, and is still one of the world’s most-played computer games. Threats using this game as a lure affected 130,619 users globally during the reporting period.
Malware and unwanted software mentioning Roblox – the second most-targeted game title – in file names triggered 20.37% of alerts on the computers of 30,367 users, followed by Counter-Strike: Global Offensive (4.78%), PUBG (2.85%), Hogwarts Legacy (0.60%), DOTA 2 (0.45%) and League of Legends (0.31%).
Games by number of related threat detections, July 1, 2022 to July 1, 2023 (download)
| Game title | Unique users |
| Minecraft | 130,619 |
| Roblox | 30,367 |
| CS:GO | 23,429 |
| PUBG | 5,891 |
| Hogwarts Legacy | 4,007 |
| DOTA 2 | 1,922 |
| League of Legends | 986 |
| World of Warcraft | 387 |
| Apex Legends | 322 |
| Diablo IV | 264 |
| Star Wars Jedi: Survivor | 216 |
| Legend of Zelda | 214 |
| Baldur’s Gate 3 | 153 |
| Final Fantasy XVI | 7 |
Games by number of users affected by related threats, July1, 2022 to July 1, 2023
| Game title | Unique files |
| Minecraft | 14,405 |
| Roblox | 8,682 |
| CS:GO | 4,498 |
| PUBG | 2,569 |
| Hogwarts Legacy | 945 |
| League of Legends | 523 |
| DOTA 2 | 418 |
| Apex Legends | 350 |
| World of Warcraft | 263 |
| Star Wars Jedi: Survivor | 88 |
| Diablo IV | 54 |
| Baldur’s Gate 3 | 53 |
| Legend of Zelda | 37 |
| Final Fantasy XVI | 6 |
Games by number of unique files using their name as a lure, July1, 2022 to July 1, 2023
Mobile gaming-related threats
The mobile gaming community, playing video games on mobile devices like smartphones and tablets, has become a driving force since the pandemic. As it offers convenient and accessible gaming anywhere, it is attracting big user numbers around the world, especially in the United States and Asia Pacific. According to Statista, the number of mobile gamers is to reach 2.3 billion by 2027.
Although not all games on our list are officially ported to mobile phones and tablets, with some mobile versions shut down soon after being launched or even on the development stage, every now and then third party mobile adaptations appear, as well as malicious traps for those willing to know if it is at all possible to play the game on mobile.
Mobile statistics
From July 1, 2022 to July 1, 2023 Kaspersky solutions detected 436,786 attempts to infect mobile devices of 84,539 users. Most of the researched game titles were used as a lure for mobile gamers at least once.
Games by number of related mobile malware and unwanted software detections, July 1, 2022 to July 1, 2023 (download)
Once again, Minecraft players were the primary targets, with 90.37% of attacks relating to this title. These attacks impacted 80,128 gamers.
In one instance, Indonesian mobile gamers were targeted by cybercriminals who used Minecraft as their gateway for Trojan.AndroidOS.Pootel.a, which opens the Minecraft page in an alternative application marketplace when the application launches on the user’s phone.
Then, by using malicious code, it begins to quietly register mobile subscriptions. To obtain the phone number, which is necessary for completing a subscription, the application uses the Google Phone Number Hint API. It then opens the subscription activation page in an invisible window and inserts the received user number into the appropriate field. After that, it clicks the Subscribe button, intercepts the confirmation code from an incoming text message and pastes it into the required field on the confirmation page.
Kaspersky gaming threat research also revealed that the most frequently targeted mobile Minecraft gamers were those from the Islamic Republic of Iran. In this country, 140,482 alerts were triggered, impacting 54,467 Minecrafters.
PUBG: Battlegrounds Battle Royale – the second most popular mobile game recorded by Kaspersky – logged 5.09% of all alerts, most of these coming from players in the Russian Federation.
Roblox (3.33%) was third by number of detections, but second by number of affected users – 2351 against 1294 for PUBG. One of the malware families targeting Roblox fans, was the SpyNote spy Trojan, which was being distributed among users under the guise of a mod. It has a number of spying capabilities, such as logging keystrokes, recording the screen and broadcasting video from phone cameras, and it can also imitate the official Google and Facebook apps to trick the user into revealing their passwords.
The fourth most-targeted mobile game was Baldur’s Gate (0.68%), a role-playing video game series set in a forgotten realm’s dungeons and dragons world, which does not have an official mobile version. Most of the affected gamers were located in Russian Federation, Brazil and Turkey.
| Game title | Unique users |
| Minecraft | 80,128 |
| Roblox | 2,351 |
| PUBG | 1,294 |
| Baldur’s Gate 3 | 304 |
| Final Fantasy VI | 115 |
| Diablo IV | 108 |
| CS:GO | 72 |
| Legend of Zelda | 63 |
| Apex Legends | 29 |
| Dota 2 | 27 |
| League of Legends | 26 |
| World of Warcraft | 19 |
| Star Wars Jedi: Survivor | 3 |
Games by number of unique users targeted by game-related threats, July 1, 2022 to July 1, 2023
Phishing: get scammed for free
In this section, we provide insights into phishing campaigns that use some of the 14 games covered in the report, along with some other titles, as a lure.
Fake game distribution pages
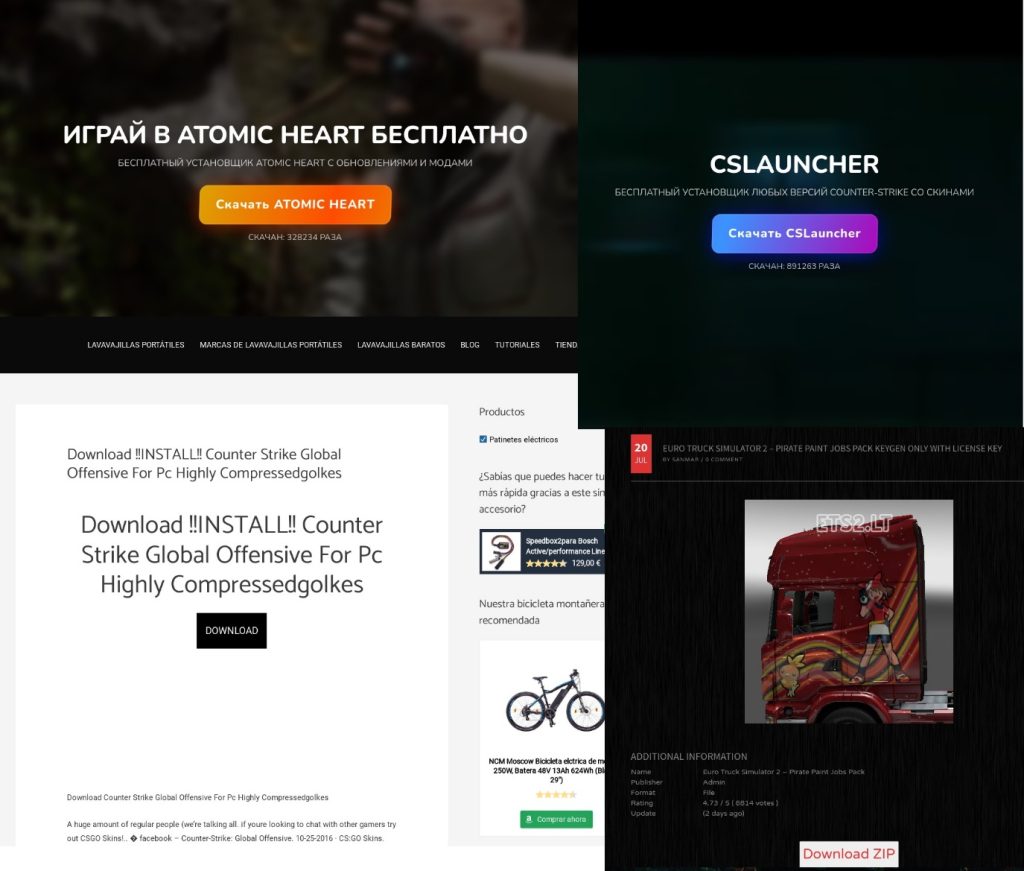
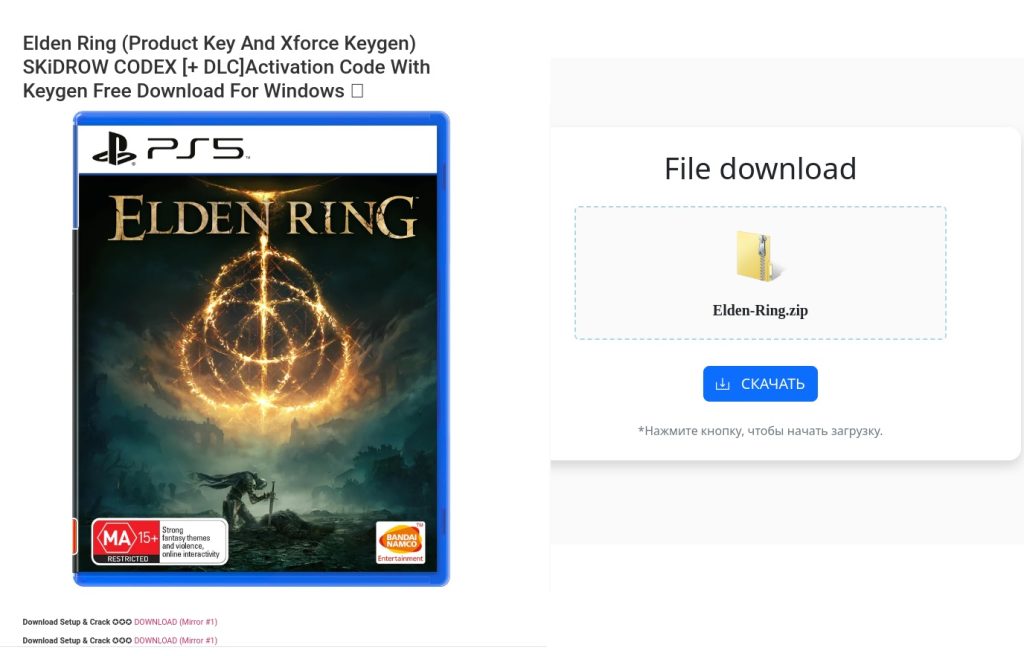
Malicious and unwanted software disguised as popular games is often distributed by third-party websites that offer pirated versions of the titles. In the screenshot below, you can see examples of such websites, offering to download Atomic Heart, CS:GO and Euro Truck Simulator “for free”.
Some of these pages show a relatively high number of downloads below the Download button, most likely to assure the user that the software is safe. Clicking the button downloads an archive, which may contain unwanted or even dangerous software, but not necessarily the game itself.
Hunting for gaming accounts
As most games allow users to purchase and sell valuable in-game items, gaming accounts are a lucrative target for cybercriminals, especially those that contain a good collection of popular titles in addition to a linked credit card.
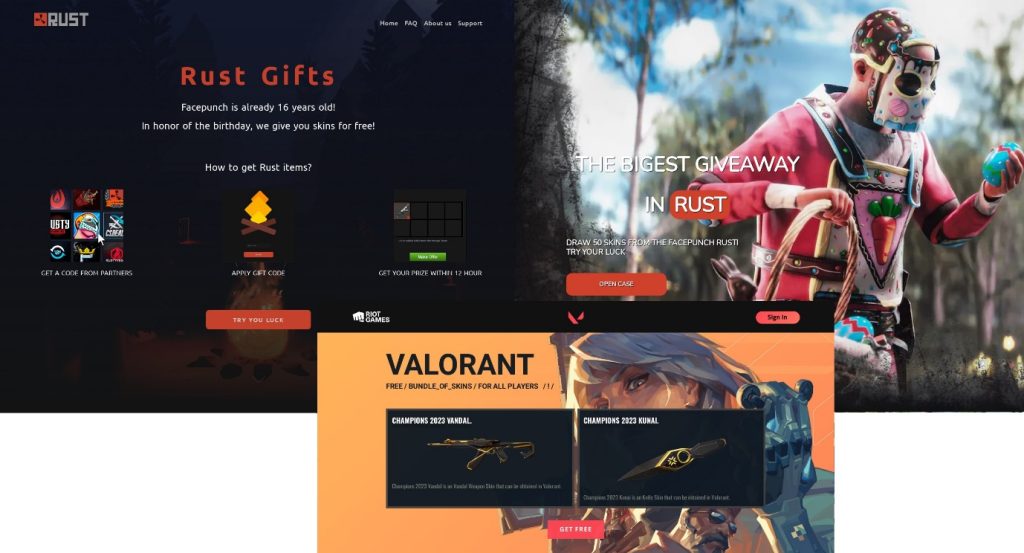
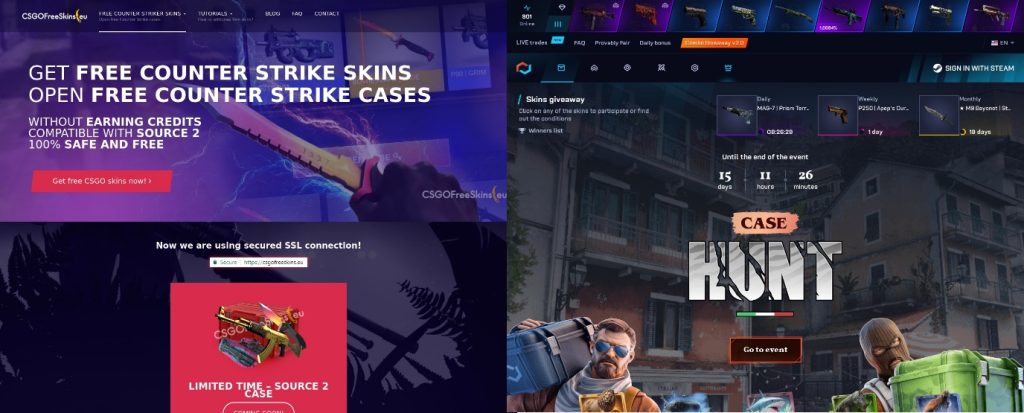
One of the most popular lures in case of games is free giveaway of in-game items or skins. The generous offers on the screenshots below will most probably result in your Steam or Riot Games account being stolen. The scheme is simple: to take part in the fake giveaway, you have to sign in to your account, which means entering your credentials on the phishing website.
Counter-Strike fans are often targeted with “free” skins, which may be valuable property in this game. Last year, a user lost two million dollars’ worth of skins after their account was hacked. Unfortunately, those falling for phishers’ offers will lose what they already have rather than get a valuable skin for free.
Another site offers something named “Counter-Strike 2 limited test”, but only to those who are willing to link their Steam account. However, if a user does link it, it will be compromised, and no access to the beta version of the game will be granted.
Besides gaming accounts, cybercriminals target gamers’ social media profiles. These are valuable to the fraudsters, as they typically contain a lot of personal data and linked payment details. Moreover, social media accounts are often used to sign in to other services including online games. Last but not least, through a stolen social media account, cybercriminals can target the victim’s friends and relatives with various scams.
In the screenshot above, phishers lure PUBG players with an in-game item giveaway. To participate, you need to sign in to your Facebook, X (ex-Twitter) or other social media account on the fake website. As soon as you do that, your credentials will be stolen.
Gaming-related scams
Similar bait is used in scams where users are tricked into paying cybercriminals a certain amount of money to obtain a gift card, in-game currency or a brand-new game. Typically, on such websites, you need to first enter some personal details and fill out a simple survey. A page is then shown, telling you that you have won a valuable prize. The only thing left to do before you can claim it is pay a small delivery fee. However, by doing this, a victim not only loses the money paid, but also compromises their bank card.
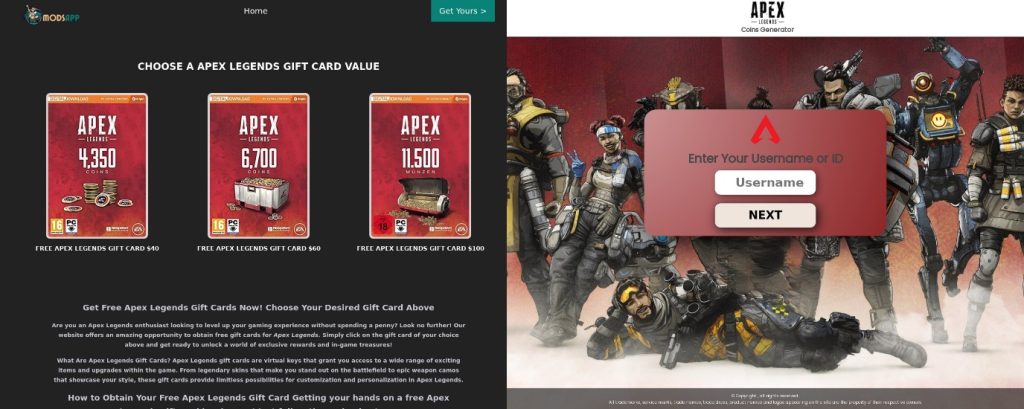
In the screenshot below, you can see a typical example of this scam. The cybercriminals offer users “free Apex Legends gift cards”. To get those, you have to first enter your username, then answer several questions and pay for your prize.
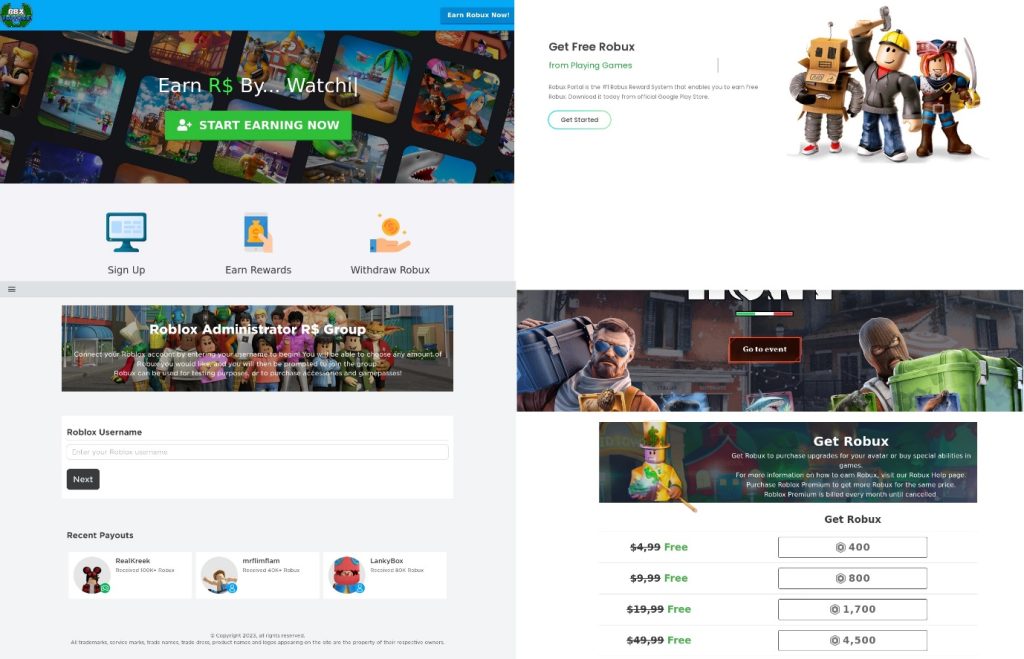
To Roblox players, the fraudsters often offer to earn, generate or just get some Robux (Roblox in-game currency) for free. Similarly to the Apex Legends example, if a user tries to withdraw the “earned” or generated money, they have to make a payment on a fraudulent website.
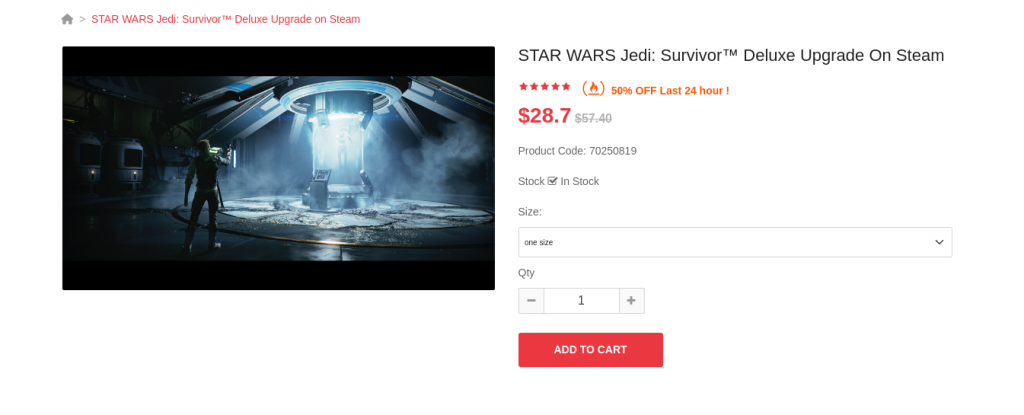
Another option scammers often resort to, is offering a hefty discount for a hot title. In the screenshot below, a rogue website pretends to be selling Star Wars Jedi: Survivor for $28.7, which is less than a half of the official price.
Should the user pay, most likely, they will get nothing, but lose their money and bank card details.
Conclusion
Gaming platforms have always been attractive targets for cybercriminals as they store a wealth of personal and financial data that ranges from payment details to email addresses and other personally identifiable information. Fraudsters make money by stealing in-game items and currency, which often have real-world value, or selling hacked accounts.
Cybercriminals are also increasingly using games – such as Minecraft and Roblox – aimed at young audiences, as a lure to exploit inexperienced computer users who lack cybersecurity awareness, with malicious or unwanted software.
With this in mind, it is imperative that young gamers’ parents educate themselves, so they can help protect their kids. There is a plethora of excellent resources online explaining the major threats to help new gamers have fun and stay safe, even if you are not a natural techie.
To keep your kids safe online, Kaspersky recommends that users:
- Show interest in their kids’ online activities. Ask them if you can watch their favorite series or listen to music tracks together. As an option, you can learn some secure practices to stay safe online together.
- Explore the option of parental control apps allowing you to control your kid’s online activity. When going down that route, it is essential to discuss the subject with the child to explain how these apps work and why they are needed to keep them safe online.
- Explain to their kids what sensitive information is and why it should only be shared with people they know in real life. You can be a role model and show your children examples of proper behavior.
- Spend more time talking to your kids about ways to be safe online. Try paying attention to your own habits. Do you use your smartphone while eating or talking? Are your kids mimicking any of your habits or behavior patterns? Do they react in a different way when you put your phone away?
- Make conversations about cybersecurity more enjoyable and exciting by discussing them with your child through games and other entertaining formats.
That being said, it is worth keeping in mind that it is not just young gamers that are targeted. Cybercriminals often seek to infect as many machines as possible and steal as many accounts as possible. Moreover, grown-up gamers often invest more money in their hobby, so their accounts are a more attractive target than those of kids. That is why it is important to stay vigilant, avoid downloading anything from shady third-party websites or sharing any personal details with those. Needless to say, the developers of gaming cheats and hacks may well cheat on their audience themselves, so you should think twice before downloading software like that.
To stay safe while gaming, Kaspersky recommends:
- Download your games from official stores like Steam, Apple App Store, Google Play or Amazon Appstore only. Games from these marketplaces are not 100% safe, but they at least are checked by store representatives and there is some kind of screening system: not every app can get listed.
- If you wish to buy a game that is not available through the major stores, purchase it from the official website only. Double-check the URL of the website and make sure it is authentic. To additionally protect your purchases, use online banking protection, such as Safe Money feature in Kaspersky products.
- Beware of phishing campaigns and unfamiliar gamers. Do not open links received by email or in a game chat unless you trust the sender. Do not open files you get from strangers.
- Do not download pirated software or any other illegal content, even if you are redirected to it from a legitimate website. It’s safer to buy games only on official sites and wait for the sales — they regularly take place, so you won’t be sitting on your hands for long.
- Use a strong, reliable security solution, which will not slow down your computer while you are playing, while protecting you from malware, phishing and other threats. As an example, Kaspersky Premium works smoothly with Steam and other gaming services, and can protect computers and mobile devices.






















Gaming-related cyberthreats in 2023: Minecrafters targeted the most