
Part 1 of gaming-related cyberthreat report
Second part of the report: BloodyStealer and gaming assets for sale
The video game industry is soaring, not in the least thanks to the lockdowns, which forced people to look for new ways to entertain themselves and socialize. Even with things going back to normal, gaming is expected to have a very bright future. Newzoo estimates the industry to gross 175.8 billion USD in 2021, which is slightly less than the total revenue in 2020 but still significantly above the pre-pandemic figures.
This rapid growth owes a lot to the surge in mobile gaming and focus on social interaction during the pandemic. With 2.7 billion gamers worldwide, virtual worlds offer not just an opportunity to unwind, but to connect with people from every part of the globe. Additionally, the number of gamers will continue to rise.
Mobile games especially draw ever more users. Analysts predict that mobile gaming will account for $90.7 billion to $120 billion of the revenue in 2021, which is more than half of the estimated gaming industry value. Last year’s lockdowns gave a boost to the mobile market, with users downloading thirty percent more mobile games per week in Q1 2021 than in Q4 2019 globally, reaching over one billion weekly downloads. Global consumer spending on mobile games reached $44.7 billion in the first half of 2021.
With the growth of the gaming industry being this rapid, we as cybersecurity researchers ask ourselves what this means for user security. Earlier in 2021, we looked at the dynamics of gaming-related web attacks over the course of the pandemic, identifying an increase in that sector. But with so many platforms offering to play threats are not limited to web.
To get a better grasp of the threat landscape that gamers are faced with, we decided to take a closer look at gaming-related cyberthreats. In this report, we cover PC and mobile threats as well as various phishing schemes that capitalize on popular games.
Methodology
To measure the level of the cybersecurity risk associated with gaming, we investigated several types of threats. We examined malware and unwanted software disguised as popular PC and mobile games. We also looked in greater detail at some of the strains of malware being distributed and the dangers they pose for users. Additionally, we checked our database for gaming-related spam campaigns and phishing schemes that are used in the wild.
This report contains threat statistics obtained from Kaspersky Security Network, which processes anonymized cybersecurity data voluntarily provided by users of Kaspersky products. These statistics indicate how often and how many users of our products have encountered gaming-related cyberthreats during the reporting period.
Most of the statistics presented in the report were collected between July 1, 2020 and June 30, 2021. Pandemic-related statistics cover the period of January 2020 through June 2021.
As a result, we discovered the following:
- The total number of users who encountered gaming-related malware and unwanted software from July 1, 2020 through June 30, 2021 was 303,827, with 69,244 files distributed under the guise of twenty-four most-played PC games;
- Quarterly dynamics showed that the number of users affected by PC-specific gaming-related cyberthreats rose at the beginning of the pandemic but then dropped in Q1-Q2 2021 compared to Q1-Q2 2020 as the lockdowns forced more users to search for free games. Meanwhile, mobile games show a different trend, with the number of users affected growing by 185% at the beginning of the pandemic and declining by just 10% by Q2 2021, meaning that mobile threats were still actively employed by cybercriminals.
- The top five PC games used as bait in the attacks targeting the largest number of users are Minecraft, The Sims 4, PUBG, Fortnite and Grand Theft Auto V.
- We uncovered a massive, coordinated campaign that distributed Swarez Dropper via numerous warez sites that were SEO-optimized. With its payload gathering secrets from browsers, crypto wallets and other applications, this malware affected users in forty-five countries.
- The top three mobile games most often used as bait were Minecraft, PUBG Mobile and Among Us.
- A total of 50,644 users attempted to download 10,488 unique files disguised as the ten most-played mobile games, generating a total of 332,570 detections in July 2020 through June 2021.
- Most threats uncovered on PC and mobile devices were unwanted applications, but dangerous malware was also present: from stealers to bankers, often leading to the loss of not just credentials but money, including cryptocurrency.
- Gaming-themed phishing schemes are highly versatile and with more gaming events taking place, cybercriminals are expanding scenarios in which they attempt to extract user data.
Cyberthreats for PC gamers
To assess the gaming-related threat landscape, we compiled four lists of the ten most-played PC games on online platforms like Origin or Steam and a list of platform-independent games, and removed duplicates along with titles that are too general for filtering out threats specific to a particular game. As a result, we ended up with twenty-four popular PC games.
| 1. Apex Legends
2. Battlefield V 3. Chivalry 2 4. Counter-Strike: Global Offensive 5. Dota 2 6. FIFA 21 7. Fortnite 8. Grand Theft Auto V 9. Minecraft 10. NBA 2K21
|
11. Need for Speed Heat
12. PLAYERUNKNOWN BATTLEGROUNDS (PUBG) 13. Rocket League 14. Rogue Company 15. Star Wars Battlefront 16. Team Fortress 2 17. The Sims 4 18. Titanfall 2 19. Unravel Two 20. Valheim |
21. League of Legends
22. Battlefield 1 23. Warframe 24. Tom Clancy’s Rainbow Six Siege
|
TOP 24 PC games analyzed in this report
We used the titles of the games as keywords and ran these against our telemetry to determine the scale of distribution of malicious files and unwanted software under the guise of these games, as well as the number of users attacked by these files.
Over the course of the last year, from July 2020 through June 2021, 69,244 files were distributed under the names of popular games, with 303,827 users encountering these files globally. In total, Kaspersky solutions detected 5,846,032 attacks involving these files during the reporting period.
By using the number of users who unwittingly attempted to download malware and unwanted software in hopes of having fun gaming, we also compiled a list of the ten most popular games used as a coverup for malware and unwanted software. The rankings largely correlate with those for distributed files and associated detections, with nine games in the top ten being the same in all rankings.
Minecraft took the first place with 36,336 distributed files affecting 184,887 users and resulting in 3,010,891 attempted infections detected over the course of July 2020 through June 2021. Other games that affected the largest numbers of users were The Sims 4, PUBG, Fortnite and Grand Theft Auto V. Notably, the number of unique users that tried to download Minecraft exceeded the number of users affected by the rest of the top ten games combined by more than 40%. Furthermore, 250% more files were disguised as Minecraft than PUBG, the game that follows Minecraft in file distribution.
This overwhelming popularity of Minecraft may be explained by the fact that there are multiple versions and a myriad of mods: modifications that can be installed on top of the core game to diversify gameplay. Mods are created by users and are unofficial, so they provide a convenient disguise for malicious payloads or unwanted software.
| Game title | Users affected | |
| 1 | Minecraft | 184887 |
| 2 | The Sims 4 | 43252 |
| 3 | PUBG | 26724 |
| 4 | Fortnite | 14702 |
| 5 | Grand Theft Auto V | 14261 |
| 6 | Counter-Strike Global Offensive | 13625 |
| 7 | Rocket League | 4631 |
| 8 | League of Legends | 4166 |
| 9 | FIFA 21 | 3109 |
| 10 | Need for Speed Heat | 2069 |
TOP 10 games used as a lure for distribution of malware and unwanted software, by attacked users, July 1, 2020 through June 30, 2021
| Game title | Files | |
| 1 | Minecraft | 36336 |
| 2 | PUBG | 10360 |
| 3 | Fortnite | 6109 |
| 4 | The Sims 4 | 5844 |
| 5 | Grand Theft Auto V | 4953 |
| 6 | League of Legends | 3794 |
| 7 | Counter-Strike Global Offensive | 2281 |
| 8 | FIFA 21 | 2138 |
| 9 | NBA 2K21 | 1045 |
| 10 | Rocket League | 987 |
TOP 10 games used as a lure for distribution of malware and unwanted software, by the number of files, July 1, 2020 through June 30, 2021
| Game title | Detections | |
| 1 | Minecraft | 3010891 |
| 2 | The Sims 4 | 1266804 |
| 3 | PUBG | 484528 |
| 4 | Counter-Strike Global Offensive | 327976 |
| 5 | Fortnite | 267598 |
| 6 | Grand Theft Auto V | 187114 |
| 7 | League of Legends | 56710 |
| 8 | Rocket League | 37751 |
| 9 | Need for Speed Heat | 27786 |
| 10 | Dota 2 | 22175 |
TOP 10 games used as a lure for distribution of malware and unwanted software, by detected attacks, July 1, 2020 through June 30, 2021

Geography of PC gaming-related cyberthreats by number of attaks per 1000 users in the country, July 1, 2020 through June 30, 2021 (download)
Gaming malware home delivered
We also looked at the dynamics of gaming-related cyberthreat distribution over the past year and a half to see whether the pandemic had an effect. In Q2 2020, when many countries went on lockdown, the number of detections of malware and unwanted software disguised as PC games skyrocketed, reaching 2,481,915 and affecting 165,207 users worldwide. In Q2 2021 by comparison, the number of detections was just 636,904, and the number of affected users was 53,439, reflecting a drop of 3.8 and three times, respectively. This suggests that as the lockdown measures were being cancelled and restrictions worldwide were relaxed in Q2 2021, the number of users looking for PC games and mods decreased significantly.
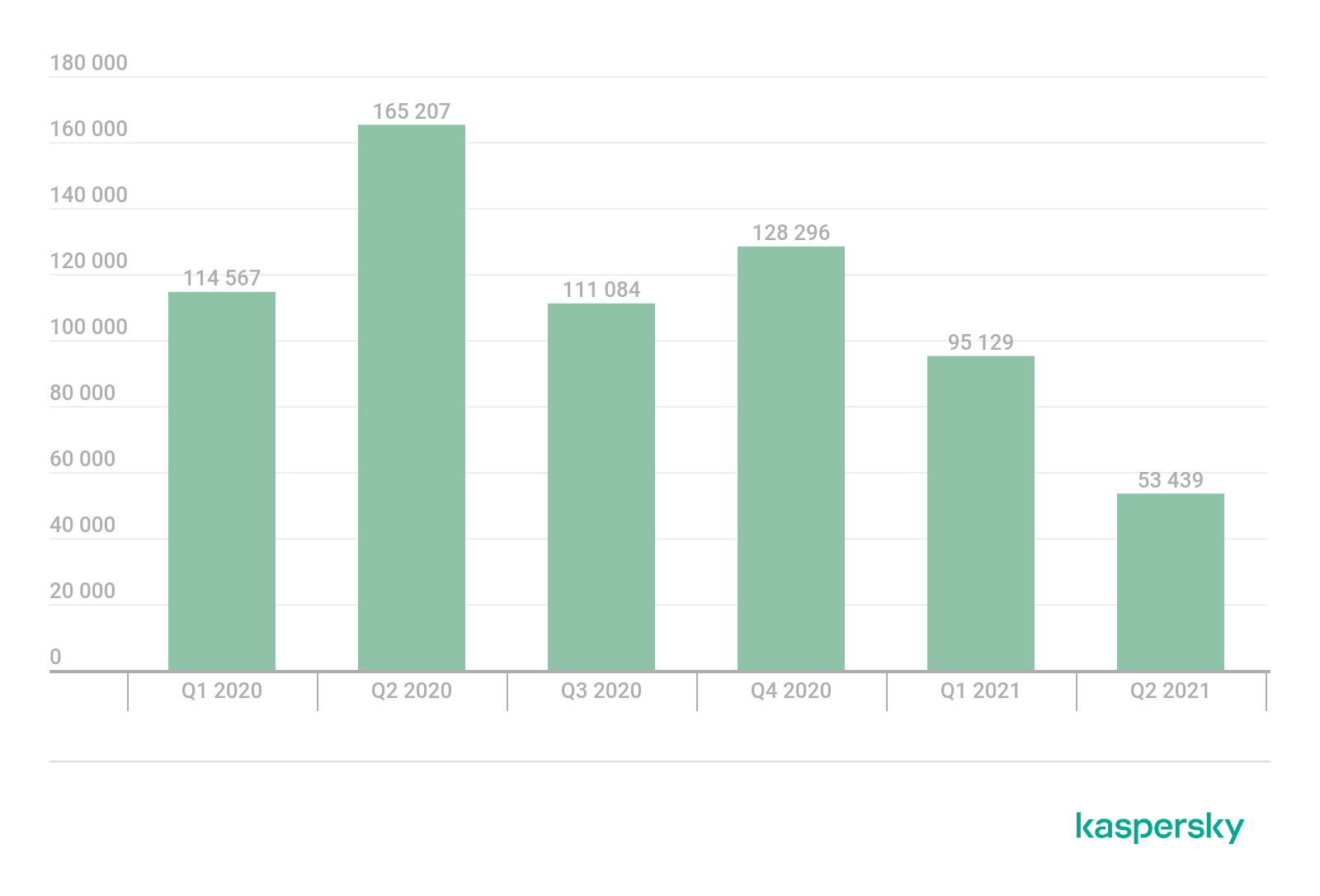
Users attempting to download malicious or unwanted files disguised as games, by quarter, Q1 2020 – Q2 2021 (download)
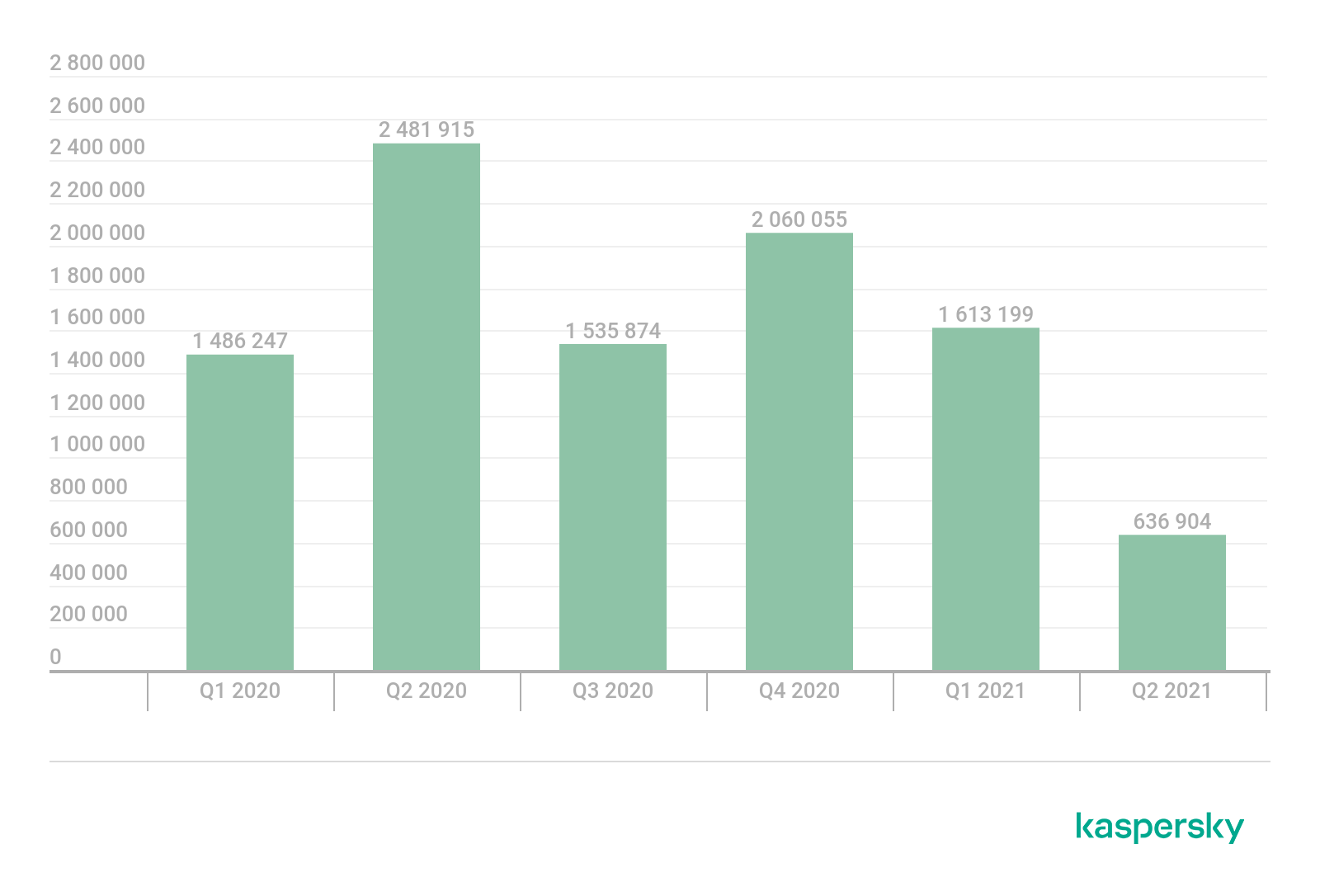
Attempts to download malicious or unwanted files disguised as games, by quarter, Q1 2020 – Q2 2021 (download)

The number of malicious and unwanted files disguised as games, by quarter, Q1 2020 – Q2 2021 (download)
Hello! Is the gamer home? Threats disguised as games
The types of malware and unwanted software distributed under the guise of games are somewhat unsurprising and reflect the overall trends in files distributed as illegal or cracked software. The statistics show downloaders accounted for an overwhelming majority (87.24%) of the software being spread. While this type of software is not malicious in itself, downloaders are often used to load other threats onto devices. Another common type of software spread as games is adware, which shows illicit advertising against users’ wish.
Other threats distributed under the titles of popular games include various Trojans, such as Trojan-Droppers and Trojan-Downloaders.
| Threat | Infection cases, % |
| not-a-virus:Downloader | 87.24 |
| not-a-virus:AdWare | 7.34 |
| Trojan | 2 |
| Trojan-Downloader | 0.73 |
| not-a-virus:WebToolbar | 0.71 |
| DangerousObject | 0.49 |
| not-a-virus:RiskTool | 0.46 |
| Hoax | 0.22 |
| Trojan-Dropper | 0.19 |
| Trojan-PSW | 0.11 |
TOP 10 threats distributed worldwide under the guise of popular games, July 1, 2020 through June 30, 2021
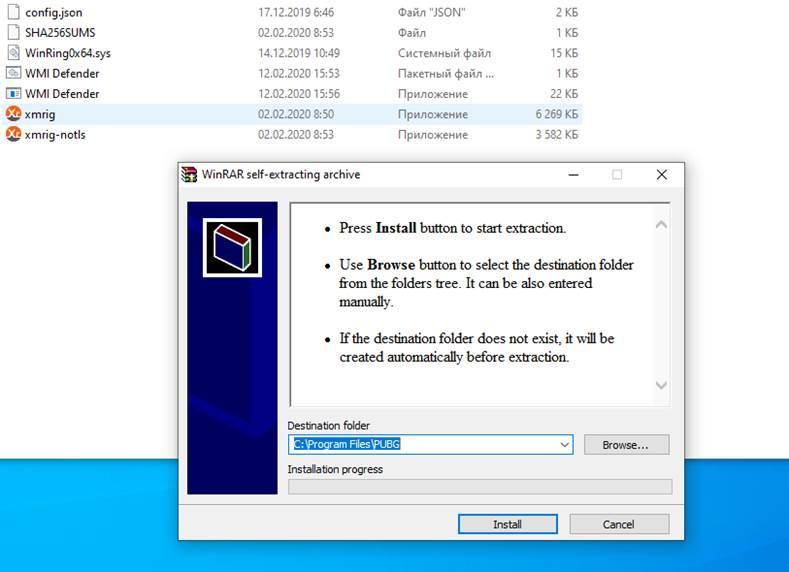
Miners are worth mentioning among the threats to PC gamers. They were detected under various verdicts such as Trojans, RiskTools etc, accounting for 0.11% of all threats. Miners targeting gamers sounds logical, as gaming computers have greater processing power. Miners can often remain unnoticed for long periods of time, only giving themselves away through the amount of energy consumed by infected devices. One miner detected by our products mimicked a PUBG installer. As user launches the installation process of what they believe to be a popular game, the miner is installed and programmed to run automatically.
This self-extracting archive mimicking a PUBG installer contains an XMRig miner
Swampy Swarez delivering a strelaer Trojan to gamers
In April 2021, we observed a massive, well-coordinated campaign distributing a dropper we dubbed “Swarez”, which loaded a stealer to victim machines. The dropper was delivered through dozens of fake warez websites: platforms that specialize in freely distributed copyrighted materials, considered a violation of copyright law.
We have observed a lot of similar websites providing malware under the guise of cracks for various software products, including anti-malware, photo or video editors and popular games. According to our telemetry, gamers in forty-five countries attempted to download this malicious software believing that it was a game.
| 1. Among Us
2. Battlefield 4 3. Battlefield V 4. Control 5. Counter-Strike Global Offensive 6. FIFA 21 7. Fortnite 8. Grand Theft Auto V 9. Minecraft 10. NBA 2K21 11. Need for Speed Heat 12. PLAYERUNKNOWN BATTLEGROUNDS 13. Rust 14. The Sims 4 15. Titanfall 2 |
The list of games which the Swarez dropper used as cover
There are long lists of tags under each post, designed to place the target pages at the top of web search results. This approach resulted in some of the sites distributing malware ending up in the top three results of popular search engines.
A search for Minecraft crack keys offers websites handing out Swarez among the top results
When trying to download something from the site, a chain of redirects lands the user on a download page and finally, drops a ZIP archive containing another password-protected ZIP and a text file with the key to unpack that. After several stages, the main payload, a Taurus stealer with functionality to exfiltrate valuable data from browsers, crypto wallets and other applications, is decrypted and executed.
An example of a warez site page used for distributing Swarez
This downloaded malware emulates cracked software to trick users into installing it
During the first infection stage, the Swarez dropper executes an obfuscated CMD script that decrypts a legitimate AutoIt interpreter. Using that, the malware runs an AutoIt script, which is also obfuscated. After several checks that the file is not running in an emulated environment, it decrypts the payload with an RC4 algorithm. The resulting file is injected in a system process and executed in its context. That file is a Taurus Trojan, a paid stealer developed by the Predator cybercriminal group, which is rich in features, flexible and configurable. It is capable of stealing cookies, saved passwords and autofill data from browsers, stealing cryptowallet secrets, gathering information about the system, fetching .txt files from users’ desktops and even taking screenshots. All this information is then uploaded to C&C servers.
Cyberthreats for mobile gamers
To further understand the gaming-related cyberthreat landscape, we also looked at mobile games. Mobile games often attract a different audience and generally have very different gaming patterns – not in the least because cellphones can be carried around and mobile games often require less engagement than their PC counterparts. Furthermore, as mobile tech progresses, popular PC games are brought onto mobile platforms, too, and not unfrequently, the mobile versions are free to play.
Similar to the PC threats analysis, we selected the top ten mobile games in line with the compiled lists of top ten mobile games from a number of ranking platforms. Our telemetry showed that in the period from July 2020 through June, 2021, 50,644 users attempted to download 10,488 unique files disguised as these games, generating a total of 332,570 detections.
Minecraft was by far the most popular mobile game disguise for unwanted application distributors. As many as 3982 files titled as Minecraft mods were detected on devices of 44,335 users in July 2020 through June 2021, generating a total of 302,611 detections. We have written before about various threats that lurk behind the facade of this popular game. In 2020, we wrote about twenty applications on Google Play that disguised themselves as mods for Minecraft, and in 2021, we found even more of such apps. Most of these apps were useless from a user perspective and mostly pushed extremely intrusive advertising, with some essentially rendering the devices unusable. Minecraft is followed by Among Us (2755 users affected by 1887 files, 9616 detections in total) and the mobile version of PUBG (1534 users, 9084 detections of 1713 files).

Rankings of mobile game titles used as a cover-up for distributing unwanted applications, by unique users, July 2020 through June 2021 (download)
| Game title | Unique users | Detections | Unique files | |
| 1 | Minecraft | 44335 | 302611 | 3982 |
| 2 | Among US | 2755 | 9616 | 1887 |
| 3 | PUBG Mobile | 1534 | 9084 | 1714 |
| 4 | Free Fire | 1226 | 6065 | 1217 |
| 5 | Brawl Stars | 613 | 2025 | 881 |
| 6 | Roblox | 513 | 2120 | 603 |
| 7 | Call of Duty (Mobile) | 403 | 1358 | 543 |
| 8 | Clash of Clans | 170 | 511 | 212 |
| 9 | Clash Royale | 116 | 359 | 112 |
| 10 | Genshin Impact | 28 | 63 | 40 |
The pandemic and risks for mobile gaming
Similar to the dynamics of PC gaming-related cyberthreats, the number of users and detected attempts at infecting mobile devices soared with the beginning of the pandemic, growing by 185% from 1138 users in February 2020 to 3253 users in March 2020.
However, unlike the situation with PC threats, the number of users attempting to download malicious files and unwanted applications thinking it is a mobile game reached its highest levels not in the Q2 2020 when lockdowns had just been introduced, but in Q3, specifically in August 2020, when 6341 users tried to download apps that they thought were games, resulting in a total of 42,664 detections.
Furthermore, even though detections peaked in the summer of 2020, the number of users striving to unwind with their mobile phones did not drop significantly in 2021, showing just a 10% average drop in users attacked monthly in Q2 2020 versus Q2 2021.

Users affected by mobile gaming-related cyberthreats, January 2020 through June 2021 (download)
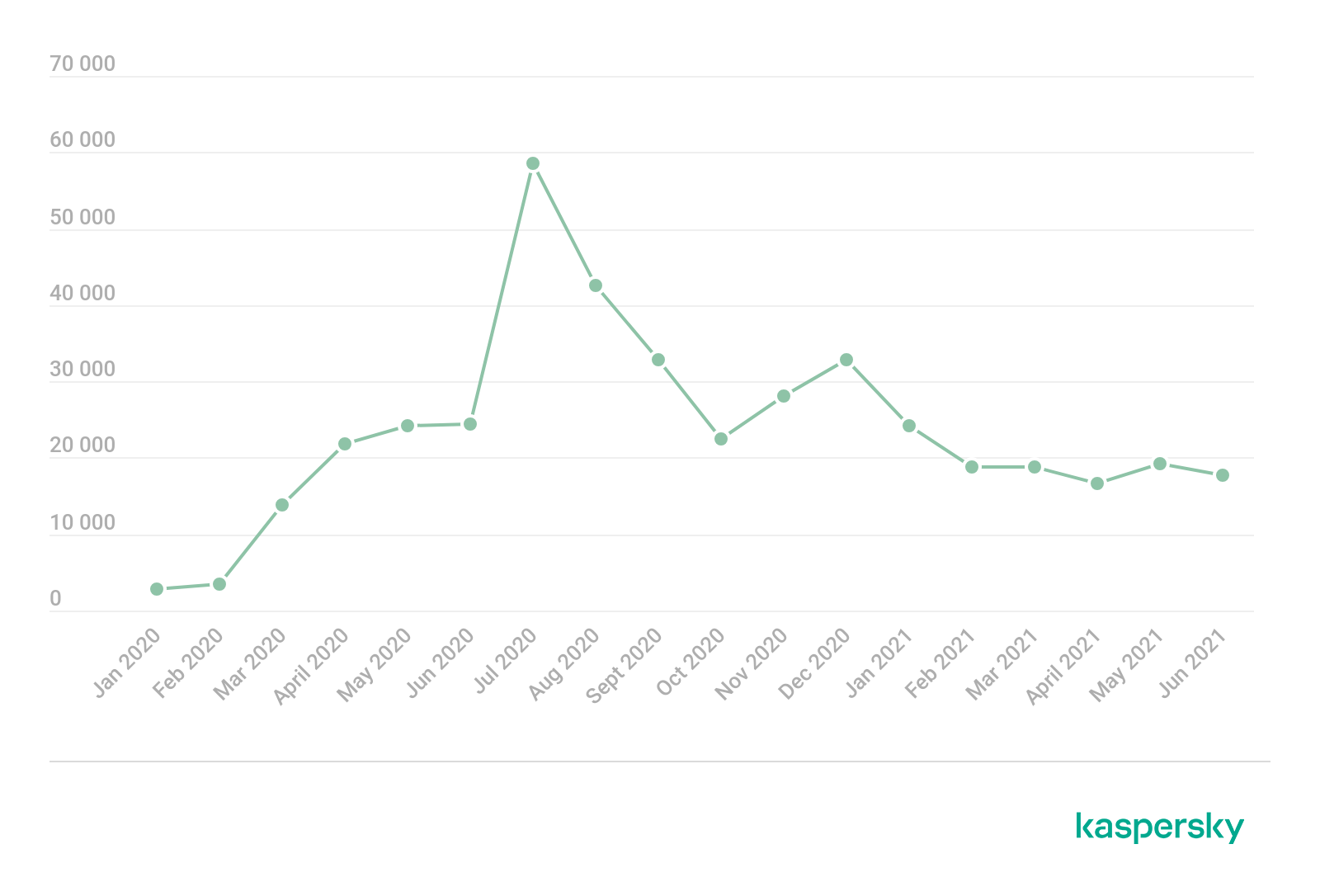
Detections of mobile gaming-related cyberthreats, January 2020 through June 2021 (download)
Let’s see what you got on your phone
An overwhelming majority (83%) of files distributed under the guise of mobile games are adware. In July 2020 through June 2021, we detected 8710 such files, which affected 48,492 users. While adware is not malicious, illicit advertisements decrease the quality of the user experience and put user data at risk. Furthermore, being highly intrusive, adware often renders mobile devices useless, as it constantly opens web pages, shows ads and drains the battery.

TOP 10 types of threats that went under the disguise of gaming-related categories, by the number of files, July 2020 – June 2021. Source: Kaspersky Security Network (download)

TOP 10 types of threats that went under the disguise of gaming-related categories, by the number of attacked users, July 2020 – June 2021. Source: Kaspersky Security Network (download)
The top ten malware strains encountered by users searching for mobile games from July 2020 through June 2021 represented various adware families. The most common one was AdWare.AndroidOS.Fyben.a, encountered by as many as 33,693 users. Second, third and fourth, as well as seventh and tenth places belonged to members of the HiddenAd family.
| Verdict | Users |
| AdWare.AndroidOS.Fyben.a | 33693 |
| AdWare.AndroidOS.HiddenAd.os | 7077 |
| AdWare.AndroidOS.HiddenAd.ri | 650 |
| AdWare.AndroidOS.HiddenAd.lu | 652 |
| AdWare.AndroidOS.MobiDash.bg | 641 |
| AdWare.AndroidOS.FakeAdBlocker.a | 607 |
| AdWare.AndroidOS.HiddenAd.mn | 651 |
| AdWare.AndroidOS.FakeAdBlocker.c | 599 |
| AdWare.AndroidOS.FakeAdBlocker.e | 287 |
| AdWare.AndroidOS.HiddenAd.tm | 278 |
TOP 10 verdicts that represent gaming-related files, by the number of attacked mobile users, July 2020 through June 2021. Source: Kaspersky Security Network
Pick a hand: a game or an SMS Trojan?
We took a closer look at some of the threats that were distributed as popular mobile games, and which could cost a user dearly. One of the Trojans that our solutions detect as HEUR:Trojan.AndroidOS.Vesub.b disguises itself as the Brawl Stars and PUBG Mobile games. When launched, the application simulates the loading process, while in fact, it collects and sends information about the user’s device to the control server, receiving commands in response. After the user notices that the game is not starting and decides to exit, the app icon is hidden, but the work does not end there. The application continues to work in the background, receiving commands to subscribe, send text messages or display ads, including unexpected playback of videos on YouTube, application pages in Google Play and advertising pages in the browser.
This page offers to download PUBG Mobile, while in fact, all that the user is getting is unwanted software
 |
 |
A fake PUBG app takes its time to load, while gathering data from the user’s device
The Vesub Trojan sends an infected system’s data to a C&C server and receives command to enter a subscription
Among the distributed threats is also the well-known Triada Trojan, detected as HEUR:Trojan.AndroidOS.Triada.bu. It is capable of showing unwanted advertising, and downloading and installing apps without users’ consent. This Trojan is hidden within a modified version of Minecraft. The game itself does, in fact, work, so the unwitting user at least gets to play.
The Triada Trojan is programmed to display ads, and download and install apps without the user’s permission – all while the user gets to play a Minecraft mod
Another type of malware distributed under the guise of Minecraft is the dropper HEUR:Trojan-Dropper.AndroidOS.Hqwar.as, known for delivering banking Trojans. This app operates in a particularly covert way. Once active on the victim’s device, the app displays a message that it was installed with an error and offers to remove it. The user has no choice but to click “Delete”. The app then informs the user that it has been deleted, while in fact, only the icon of what is believed to be Minecraft is removed from the UI. The malware then drops Trojan-Banker.AndroidOS.Grapereh, capable of sending and receiving text messages, making phone calls, and sending USSD commands.
 |
 |
 |
Once installed, the fake Minecraft app notifies the user about an installation error and requests deletion, which never actually happens
The phishy games we play
In the previous sections of the report, we discussed malware and unwanted software disguised as popular games. However, there is another common threat: phishing. This is a form of cybercrime that relies on social engineering techniques by creating convincing replicas of pages of well-known brands or desirable products. Phishing is often used for luring users into giving up their data and cash or into downloading malware. When it comes to devising attractive baits, phishers do their best, coming up with some creative scenarios that can fool unwitting users. Gaming is an especially lucrative topic for cybercrooks. Let us take a look at some of the schemes employed.
Free gold?
In the past few years, many popular games have introduced their own in-game currency that can be used for purchasing in-game goods, assets and upgrading characters. In-game currency is an additional way of monetizing games, while some users, quite expectedly, try to spend less on gaming.
Some phishers prey on this desire to reduce expenses and offer to generate in-game currency for free. We found examples of these schemes, targeting players of Apex Legends, FIFA21, Candy Crush, GTA5, Pokemon Go and PUBG. Of course, the pages do not actually deliver coins – only collect emails, usernames for specific games, gaming IDs, mobile phone and social media handles via so-called “human verification” surveys. These can later be used for additional targeting or sold in databases on the darknet.
 |
 |
Leave your username and ID and get nothing in return: that is how phishers roll
Free games, goodies and gift cards
A lot of phishing pages offer games for free or for a very small price: as low as 0.5 USD for a set of games. All they ask for is to share your social media handle or email and complete a couple of assignments. This data may be collected for further use. Also, if you pay even a very small amount of money on this kind of a site, your credit card details are very likely gone. The same is true when the site asks you to provide credit card details without charging any fee at all. Some pages offer free game downloads without any surveys or forms to fill. In this case, what you really download is most probably malware or adware.
This phishing page offers packages with 30 to 100 games for less than a dollar
A phishing page is offering a fake copy of The Sims 4 Cottage Living
Dota 2 bundles offered for free still require credit card details, which can later be found in databases on the dark web
Some phishers go so far as to mention that other software may include hidden malware, a good way of throwing the scent off
Letting off some Steam
Popular online gaming platforms, such as Steam, are also used as bait. Being careless may result in giving up your gaming credentials – and all what you have in your account together with those. That includes your games and the aforementioned in-game currency, too.
This phishing page may look convincing, but all it does is collecting Steam account details
The same goes for Twitch and Discord, communication platforms for the streaming and gaming communities. Phishers create pages branded after popular platforms and go after credentials and credit card details under the guise of giveaways and bargains.
This phishing page disguised as Discord will gather Discord account credentials
Cybercriminals can also promote fake giveaways on the platforms themselves. Earlier, we covered one such scheme on Twitch, where scammers created fake streamer profiles to attract user attention.
Fake it till you make it
Online tournaments are also increasingly popular, and cybercrooks have learnt that, too. We have come across phishing pages that replicate popular tournaments and even mention sponsor brands to make it more convincing. These schemes generally result in logins and passwords being stolen as well.
This finely designed tournament page is nothing more than a scam that capitalizes on well-known and trusted brands
Conclusion and advice
The effects of the pandemic on the video game industry were quite evident and led to a rise in attacks on users playing PC and mobile games. At the same time, as things are moving back to normal, we observe two very different trends: while PC gamers are becoming less likely to be attacked, mobile gamers remain a very attractive target for cybercriminals, a trend that will probably follow the rapid growth of the mobile industry as a whole.
While most of the threats distributed to gamers are unwanted applications, the smaller share of malware containing particularly dangerous strains requires attention. We have witnessed malware hiding under the guise of games – and distributed in very active coordinated campaigns that involve phishing and warez websites. Furthermore, cybercrooks continue to invest into promotion of malware landing pages and can even make it to the top of popular search engines.
The number of schemes targeting gamers is also growing, and telling a scheme apart from the real deal visually is still hard for regular users. Jumping on the bandwagon of the online platform rush and gaming tournaments, cybercriminals manage to take suspicions off themselves and trick users into giving up their data. Overall, the hunt for gaming credentials and in-game goodies continues. It also may take other forms, which we will discuss in the second part of the report. In a situation like this, the best way for users to protect themselves is to stay vigilant and employ reliable technology that can help detect a threat when human judgement fails.
To stay safe while gaming, we recommend:
- Wherever possible, protect your accounts with two-factor authentication. For other cases, comb through account settings.
- Use strong passwords – and a unique one for every account. That way, even if one of your accounts gets stolen, the rest will not go with it.
- A strong, reliable security solution will be a great help to you, especially if it will not slow down your computer while you are playing, but at the same time, it will protect you from all possible cyberthreats. For example Kaspersky Total Security works smoothly with Steam and other gaming services.
- It is safer to download your games only from official stores like Steam, Apple App Store, Google Play or Amazon Appstore. Games from these markets are not 100 % secure, but they at least are checked by store representatives and there is some kind of screening system: not every app can get into these stores.
- If you wish to buy a game that is not available through major stores, purchase them from the official website only. Double-check the URL of the website and make sure it is authentic.
- Try to avoid buying the first thing that pops up. Even during Steam’s summer sale, before forking out the dough for a little-known title, at least read some reviews. If something is fishy, other people will probably figure it out.
- Beware of phishing campaigns and unfamiliar gamers. Do not open links received by email or in a game chat unless you trust the sender. Do not open files you get from strangers.
- Carefully check the address of any resource that requests you to enter your username and password: the page might be fake.
- Do not download pirated software or any other illegal content, even if you are redirected to it from a legitimate website.
- Update your operating system and important apps as updates become available. Many safety issues can be solved by installing updated versions of software.
- Do not open questionable websites when these are offered in search results and do not install anything that comes from those.
- Use a robust security solution to protect yourself from malicious software and its activity on mobile devices, such as Kaspersky Internet Security for Android.






























Gaming-related cyberthreats in 2020 and 2021