
In May 2018, we discovered a campaign targeting dozens of mobile Android devices belonging to Israeli citizens. Kaspersky spyware sensors caught the signal of an attack from the device of one of the victims; and a hash of the APK involved (Android application) was tagged in our sample feed for inspection. Once we looked into the file, we quickly found out that the inner-workings of the APK included a malicious payload, embedded in the original code of the application. This was an original spyware program, designed to exfiltrate almost all accessible information.
During the course of our research, we noticed that we were not the only ones to have found the operation. Researchers from Bitdefender also released an analysis of one of the samples in a blogpost. Although something had already been published, we decided to do something different with the data we acquired. The following month, we released a private report on our Threat Intelligence Portal to alert our clients about this newly discovered operation and began writing YARA rules in order to catch more samples. We decided to call the operation “ViceLeaker”, because of strings and variables in its code.
Mobile ViceLeaker
The following table shows meta information on the observed samples, including compiler timestamps:
| MD5 | Package | Compiler | C2 |
| 51df2597faa3fce38a4c5ae024f97b1c | com.xapps.SexGameForAdults | dexlib 2.x | 188.165.28[.]251 |
| 2d108ff3a735dea1d1fdfa430f37fab2 | com.psiphon3 | dexlib 2.x | 188.165.49[.]205 |
| 7ed754a802f0b6a1740a99683173db73 | com.psiphon3 | dexlib 2.x | 188.165.49[.]205 |
| 3b89e5cd49c05ce6dc681589e6c368d9 | ir.abed.dastan | dexlib 2.x | 185.141.60[.]213 |
To backdoor legitimate applications, attackers used a Smali injection technique – a type of injection that allows attackers to disassemble the code of original app with the Baksmali tool, add their malicious code, and assemble it with Smali. As a result, due to such an unusual compilation process, there were signs in the dex file that point to dexlib, a library used by the Smali tool to assemble dex files.
The analysis of the APK was rather interesting, because some of the actions were very common spyware features, such as the exfiltration of SMS messages, call logs and other data. However, in addition to the traditional functionality, there were also backdoor capabilities such as upload, download, delete files, camera takeover and record surrounding audio.
The malware uses HTTP for communication with the C2 server for command handling and data exfiltration. Here is a command and control protocol fragment:
In total, the malicious APK handles 16 different commands:
| Command | Endpoint | Description |
| 1 | reqsmscal.php | Send specified SMS message |
| 2 | reqsmscal.php | Call specified number |
| 3 | reqsmscal.php | Exfiltrate device info, such as phone model and OS version |
| 4 | reqsmscal.php | Exfiltrate a list of all installed applications |
| 5 | reqsmscal.php | Exfiltrate default browser history (limited to a given date) |
| 6 | reqsmscal.php | Exfiltrate Chrome browser history (limited to a given date) |
| 7 | reqsmscal.php | Exfiltrate memory card file structure |
| 8 | reqsmscal.php | Record surrounding sound for 80 seconds |
| 1 | reqcalllog.php | Exfiltrate all call logs |
| 2 | reqcalllog.php | Exfiltrate all SMS messages |
| 3 | reqcalllog.php | Upload specified file from the device to the C2 |
| 4 | reqcalllog.php | Download file from specified URL and save on device |
| 5 | reqcalllog.php | Delete specified file |
| 6,7,8 | reqcalllog.php | Commands not yet implemented |
| 9 | reqcalllog.php | Take photo (muted audio) with rear camera, send to C2 |
| 10 | reqcalllog.php | Take photo (muted audio) with front camera, send to C2 |
All observed samples with Smali injections were signed by the same debug certificate (0x936eacbe07f201df).
As we know from our investigation, traces of the first development activities were found at the end of 2016, but the main distribution campaign began in 2018 (end of 2017).
Based on our detection statistics, the main infection vector is the spread of Trojanized applications directly to victims via Telegram and WhatsApp messengers. There are the following relevant detection paths (the last one is an alternative Telegram client – “Telegram X“):
| Name | Detection path |
| Sex Game For Adults 18.apk | /storage/emulated/0/WhatsApp/Media/WhatsApp Documents/ |
| 4_6032967490689041387.apk | /storage/emulated/0/Telegram/Telegram Documents/ |
| Psiphon-v91.apk | /storage/emulated/0/Android/data/org.thunderdog.challegram/files/documents/ |
Backdoored Open Source
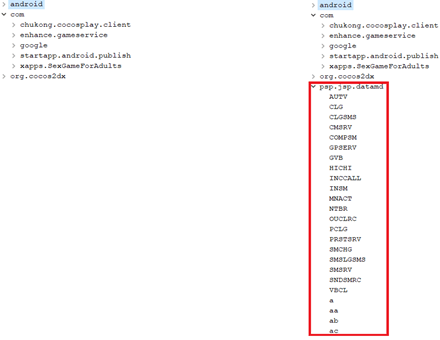
During the course of our analysis, we also found samples sharing code with the ViceLeaker malware, in particular they shared a delimiter that was used in both cases to parse commands from the C2 server.
This would be a very unusual coincidence. Even when a false flag might also be a possibility, we consider this to be unlikely.
The samples sharing this overlap are modified versions of an open source Jabber/XMPP client called “Conversations” with some code additions. The legitimate version of this app is also available on Google Play.
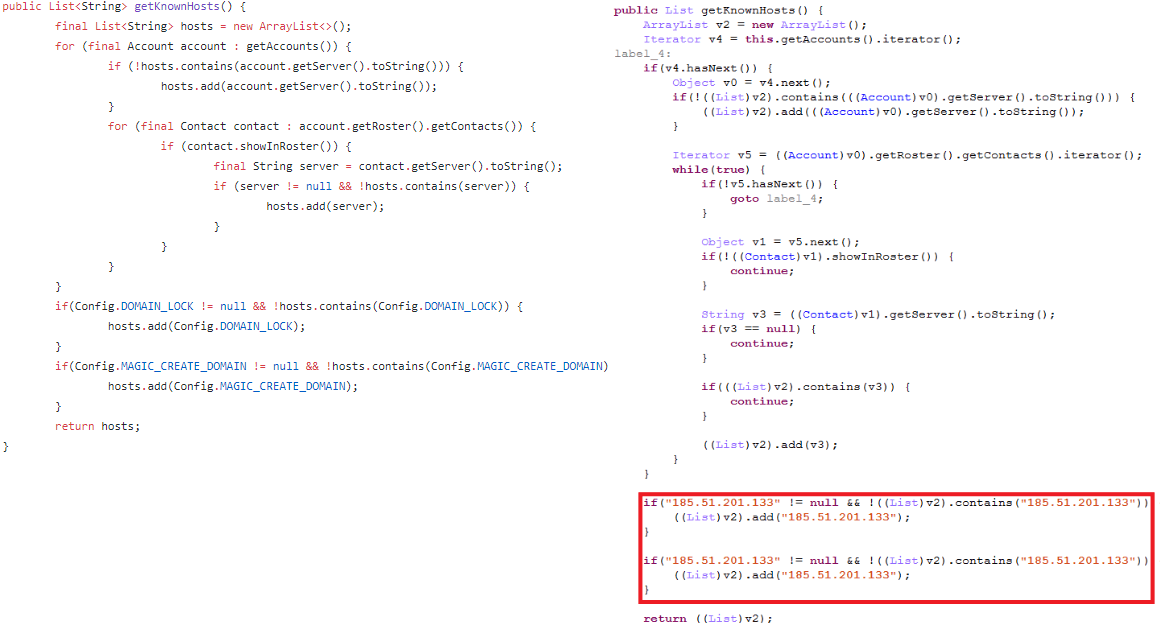
The Conversations modified samples differ from the original one in the getKnownHosts method that was modified to replace the main XMPP host with the attackers’ C2 server:
It appears that the attackers were using a specific C2 for the use of that app. Another important modification is in the message transfer process:
With this modification, an application sends device location coordinates with every message.
There are also many other modifications, fully described in our private report. In addition, we did not see traces of the Smali injection. In this case we found traces of dx/dexmerge compilers, which means that, this time, the attackers just imported the original source code into an Android IDE (such as Android Studio, for instance) and compiled it with their own modifications.
In addition to adding the code, the attackers also changed the icon and package name. We do not know why, but we suspect that it was an attempt to hide the origin of the application.
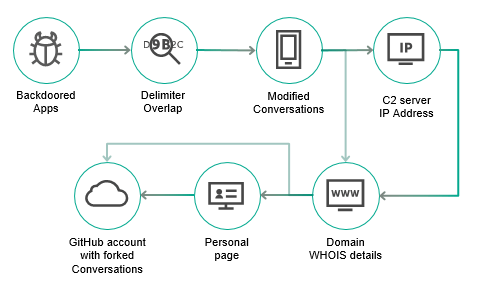
Even when we originally thought this was a backdoored version of the Conversations app, used to infect victims, we didn´t discovered anything malicious in it. This brought to us the hypothesis that this might be a version used by the group behind ViceLeaker for internal communication or for other, unclear purposes. All the detections of this backdoored app were geolocated in Iran.
Backdoored Conversations C2 server analysis
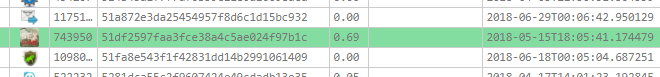
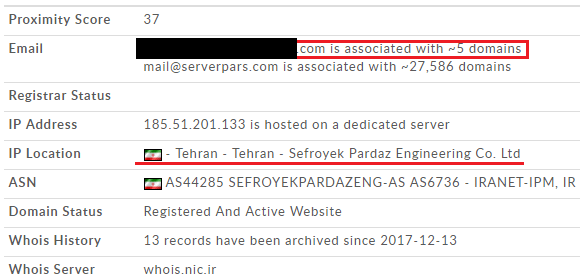
During the analysis of the Smali injected apps and their C2 server infrastructure we hadn’t found any interesting clues, but things changed when we looked at the C2 server of the linked Conversations messenger. It uses “185.51.201[.]133” as a main C2 address, and there is only one domain that is hosted on this dedicated server – iliageram[.]ir. Note that we later found versions that used the domain as a C2 directly instead of the IP address. The record contains a personal email address:
We were aware of the possibility that the attackers might be using a compromised email account, so we dug deeper to find more information related to this email address. A quick search produced results about a personal page and, what is more interesting, a GitHub account that contains a forked Conversation repository.
Summarizing all the found clues, we have the following attribution flow:
Conclusion
The operation of ViceLeaker is still ongoing, as is our research. The attackers have taken down their communication channels and are probably looking for ways to assemble their tools in a different manner. Kaspersky detects and blocks samples of the ViceLeaker operation using the following verdict: Trojan-Spy.AndroidOS.ViceLeaker.*
Actually, we are currently investigating whether this group might also be behind a large-scale web-oriented attack at the end of 2018 using code injection and exploiting SQL vulnerabilities. Even when this would not be directly related to the Android malware described in this blogpost, it would be an indicator of wider capabilities and objectives of this actor.
For more information about the ViceLeaker operation, contact us at: intelreports@kaspersky.com





























ViceLeaker Operation: mobile espionage targeting Middle East