
The security was tight enough, but the raider knew exactly where the weak point in the system was. He had undergone special training to help him slip unnoticed through loopholes like these and infiltrate the network. The raider creates the loophole that lets others in — spies, thieves or secret agents, who then force the system to operate according to their bosses’ wishes. As long as the loophole stays open…
This is not a scene from a computer game, this type of scenario is played out using exploits -programs that take advantage of vulnerabilities in software and stealthily penetrate the computers under attack.
Vulnerabilities and exploits
A vulnerability is a flaw in software code that malicious users can, under certain conditions, use for their own purposes. An exploit is a program that takes malicious advantage of, or exploits, a software vulnerability on a local or remote computer.
The main objective of an exploit is to infect a targeted computer using a specific malicious threat. Since an exploit is rarely large, in most cases, it performs the function of a downloader. As a rule, all malicious actions take place in the background, without the user noticing. Of course, sometimes it may cause the web browser to crash, but the average user probably won’t suspect anything out of the ordinary.
Vulnerabilities are found in just about every type of software program, and popular programs are no exception. It seems as though some developers are very lax in their attitude towards the avoidance of errors in their program code. Vulnerabilities can be found in programs used to process various file formats, as well as in virtual machines that run scripts. The result is an opportunity for malicious users to include exploits in different file formats such as: JPEG, TIFF, BMP, GIF, ANI and LNK, with the help of different protocols. Sometimes, a file itself is an exploit, such as those written in JavaScript that target vulnerabilities in Internet Explorer.
In the overwhelming majority of cases, exploits contain a so-called shell code. The shell code looks like a byte sequence and is a selection of machine instructions that can be executed by a processor. Typically, the code is downloaded to a user’s computer and then the full malicious program is launched. However, there are also vulnerabilities that do not involve the execution of shell code. For example, an exploit that targets the CVE-2010-1885 vulnerability in Microsoft’s help desk and support center executes HTML code that generally includes a tag and contains its own malicious script designed to carry out specific actions. Then there is the use of the CVE-2010-2568 vulnerability in LNK files, this exploit triggers the download of a dynamic directory saved to the memory and is covered in more detail below.
Some exploits pose a threat because their actions are carried out indirectly by a trusted application. For example, an exploit that targets a vulnerability in an Internet browser could download a malicious program. In this scenario, the firewall won’t block the download because it is being performed by a program that the firewall considers to be authorized to download files.
Your computer is being targeted
There are plenty of ways to deliver an exploit to user computers. The most common method is to infect legitimate resources, and malicious users most often opt for the Gumblar and Pegel script downloaders when they want to do this. A malicious script containing a number of exploits is downloaded to the user’s computer when they visit a site infected with these threats.
In cases such as these, cybercriminals typically use a so-called exploit pack, which is essentially a set of exploits that target vulnerabilities in a variety of browsers and applications. The cybercriminals’ plan is simple: there are a number of different programs on a targeted computer, which is why using a collection with a variety of exploits increases the chance of at least one bearing fruit. For example, if a victim’s computer runs patched versions of Chrome and Adobe Reader, but a Java engine from Sun still has a vulnerability, then one of the exploits in the pack targeting loopholes in Java will work and download the malware to the victim’s computer.
This type of attack has been dubbed a “Drive-by Download.” These drive-by attacks are particularly threatening as the user will remain completely unaware of what has happened. It is no coincidence that a number of Internet threats have recently propagated via drive-by downloads, including the dangerous and complex Zbot/ZeuS, TDSS, Sinowal, and Virut.ce threats.
The following diagram shows how a user’s computer might become infected by Zbot/ZeuS.

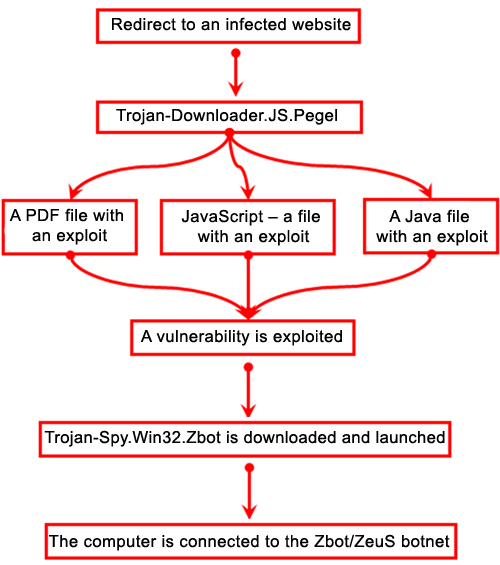
How a computer is infected with Zbot/ZeuS using exploits
The first step of the process is to redirect the user to a website infected with Trojan-Downloader.JS.Pegel. Then, Pegel redirects the user to a website containing an exploit pack. Next, attempts are made to directly download and install the bot. The last step is to connect the infected computer to the botnet’s command center and include it in the botnet.
Social engineering methods are also widely used to spread exploits. For example, a user might receive a link to a new message, allegedly from Facebook, or an email purporting to be from a bank with an invitation to visit a specific webpage in order to unblock their account. The link will lead the user to a fake message that may cause them to unwittingly download an exploit to their computer.
When a computer is already infected by a Trojan Downloader, the Trojan may download and install any number of threats, including those that exploit vulnerabilities.
However, the most effective means of spreading exploits is from an infected computer to a local network. In this case, a special network request is generated and sent to all computers on the system, leading to any vulnerabilities that exist being exploited. This is how the most threatening worms such as Kido and Lovesan are spread. This method will infect an entire local network in a very short space of time. The infection cannot be stopped until the vulnerability is fully patched.
They did it
Recently, the most significant events in information security have typically been related to the cybercriminals’ use of various vulnerabilities.
Without exaggeration, the emergence of the Kido/Conficker network worm can be called the most important event of the last decade in the IT industry. What makes this threat so significant is the ease with which it spreads, i.e., by exploiting the MS08-067 vulnerability in the Windows server. All that is necessary is to send a special network packet to the target computer and if the operating system isn’t patched, the malicious code will launch.
Another relatively important event in recent times was the targeted attack against Microsoft and Google designed to steal confidential data from both companies. The attack was launched using the malicious Aurora script and targeted the CVE-2010-0249 vulnerability in Microsoft Explorer.
The Stuxnet worm is another relative newcomer. This worm exploits the CVE-2010-2568 in LNK files. To spread this threat, a special LNK shortcut is generated and delivered to the target computer. When the user opens a network packet containing the shortcut, the malicious program launches. Compromised shortcuts can also be spread by email. If an email client attempts to display the icon, the computer will start to download the malicious program. Currently, more and more threats are emerging that exploit vulnerabilities in LNK files. For example, Sality.ag droppers were recently detected and these are spread using compromised shortcuts.

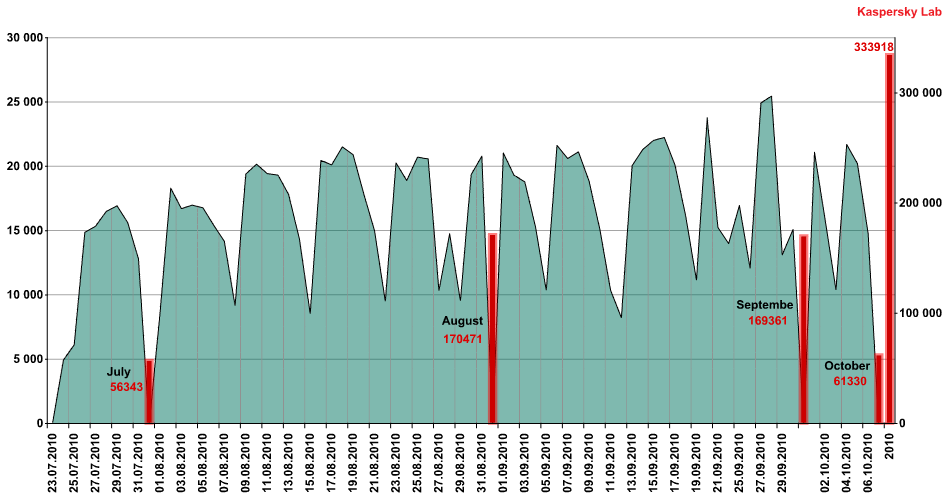
Detection statistics for exploits targeting the CVE-2010-2568 vulnerability
Judging by the number of exploits detected that target the CVE-2010-2568 vulnerability, which hasn’t changed despite Microsoft releasing an official patch on 2 August (MS10 – 046), we can presume that this vulnerability remains popular with malicious users. Remarkably, each Sunday we see a drop on the charts – presumably because less people use their computers at weekends.
Program patches
Clearly, unpatched vulnerabilities in commonly used software can have undesirable consequences. That is why software developers release patches. Patches are small programs that eliminate vulnerabilities.
Automatic program updates that are installed on user computers are critical and truly influence the safety of the operating system as a whole. Microsoft’s products are used on the overwhelming majority of computers around the world and the company leads the field in the release of patches. From the Windows 98 operating system onwards, users have been able to take advantage of the free Windows Update service. This service distributes and encourages users to install patches for vulnerable applications, in addition to providing updated drivers and additional components for the Windows system. Over time, this service has morphed into the more global Microsoft Update service. Microsoft Update is also free and scans a user’s system for any necessary updates for certain Microsoft products, such as SQL Server, Visual Studio, MS Office and others.
Previously, cybercriminals mainly targeted vulnerabilities in the MS Windows family of operating systems. However, over the last few years they have shifted their focus to include Adobe products such as Flash Player and Adobe Reader. Initially, Adobe was reluctant and slow to patch the security loopholes in its programs. However, with time it became clear that end user needs were not being met. As a result, a new product called Adobe Updater was released to perform a function similar to that of Windows Update: the automatic download and installation of patches for programs installed on users’ computers. At present, Sun, whose Java engine also has vulnerabilities targeted by exploits, is also trying to resolve its update situation.
Meanwhile, antivirus developers are not sitting idly by. They are also releasing updates for potentially dangerous exploits as they are detected. This helps to restrain the activities of malicious users until an official update can be released by the developer of the software being targeted. Cooperation among Microsoft, Adobe and the antivirus companies minimizes the response time to threats and helps to provide users with better protection.
Better now than never
These days, most Internet attacks stem from the use of exploits, which help cybercriminals download their chosen malware onto a user’s computer without the user’s knowledge or consent. Furthermore, many vulnerabilities give cybercriminals the ability to gain full access to a user’s system. So, how can you protect yourself against these attacks?
The first and most important step is to promptly download and install any updates that may be available for your software. Unfortunately, according to Kaspersky Lab’s data, many users do not regularly update the software on their computers– we detect numerous vulnerabilities on user machines. What’s more, the patches for the most widespread vulnerabilities were often released months — even years — ago.
In the third quarter of 2010, Kaspersky Lab found 31,425,011 unpatched vulnerabilities in applications and files on users’ computers. At the close of the quarter, the TOP 10 threats featured vulnerabilities that were detected in 2009, 2008…and even as long ago as 2007!
Many users get confused and believe that the cybercriminals only target new security loopholes. However, among the various exploits that feature in our top monthly malware statistics, we constantly see ones that target older vulnerabilities. For example, in August 2010, virus writers often chose to work with such dated exploits as CVE-2009-3867, CVE-2010-0806 and CVE-2010-0094.
Updates need to be monitored carefully. When necessary, they should be installed manually. Users should always activate services such as Microsoft Update and Adobe Updater on their computers. In addition to Microsoft and Adobe products, users are also advised not to ignore updates for other programs, like the popular Winamp music player.
Don’t ignore the basic rules of computer security: do not open unknown emails that appear in your inbox, do not click on unknown links, etc… Most of the latest browsers, such as Google Chrome, Mozilla Firefox and Internet Explorer feature special filters that block phishing and other malicious websites. Use a web browser with these filters built in.
Lastly, always use a comprehensive antivirus solution on your computer and ensure you install the latest updates in order to counteract exploits targeting any unpatched vulnerabilities.





















Cybercrime Raiders