
On 20 March, Russian law enforcement agencies announced the arrest of a cybercriminal gang involved in stealing money using the Carberp Trojan. This is very good news, but unfortunately does not mark the end of the Carberp story.
Evidently, those arrested were just one of the criminal gangs using the Trojan. At the same time, those who actually developed Carberp are still at large, openly selling the Trojan on cybercriminal forums.
Here is a recent offer for the ‘multifunctional bankbot’, which appeared on 21 March:
A post advertising the sale of Carberp
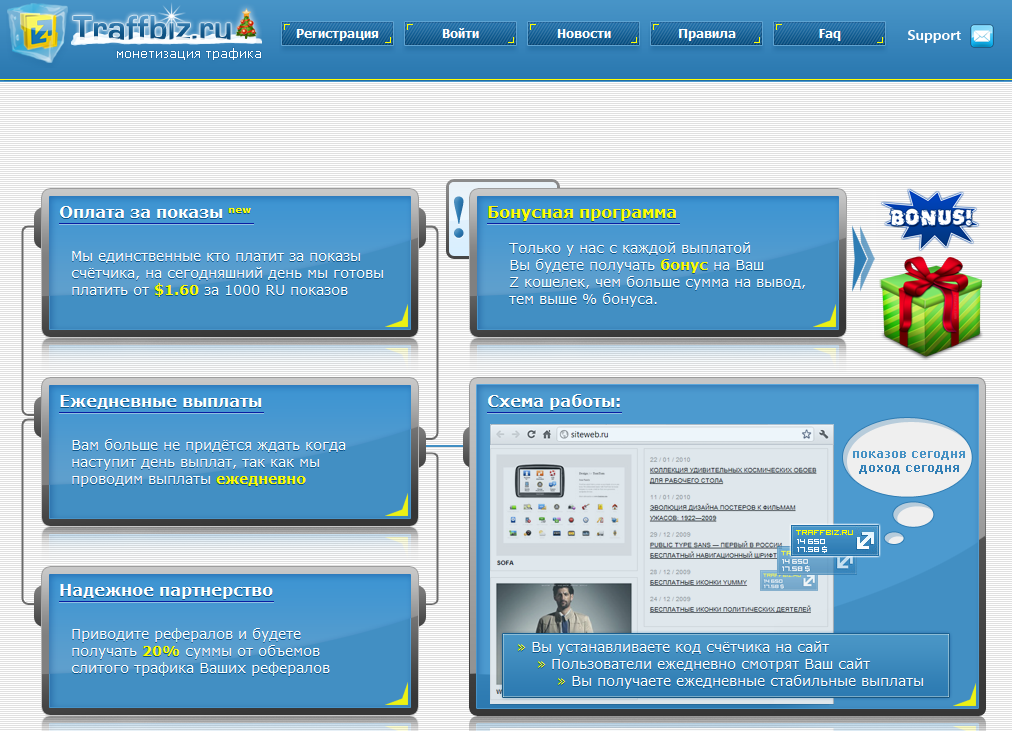
There are still numerous ‘affiliate programs’ involved in the distribution of Carberp, particularly “traffbiz.ru”.
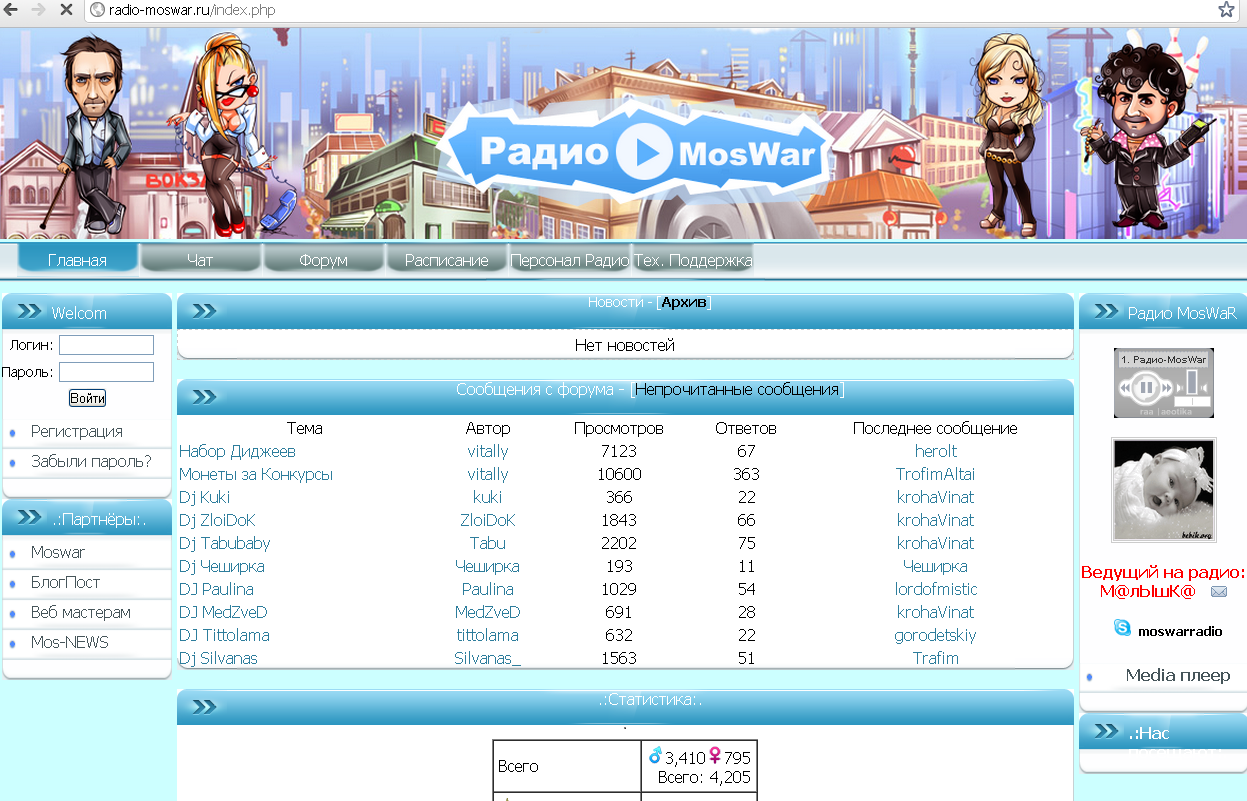
We detected a new Carberp distribution incident on 21 March. Infection was initiated at radio-moswar.ru, a website devoted to the MosWar online browser game.
The main page of radio-moswar.ru
A page on the site includes a script which quietly redirects visitors to a web page in a third-level domain.
The script redirecting users from radio-moswar.ru
The second-level domain belongs to Dyn – a company that offers free services for the creation of free *.dyndns.TLD third-level domains. Such services are popular among cybercriminals as they make it unnecessary to register new domains.
Screenshot of the dyndns.tv website
A series of redirects to different DynDns domains ultimately leads to a script of the traffbiz affiliate program. Officially, the program acts as an intermediary between webmasters and traffic buyers, but according to our information, it is mostly used by cybercriminals to distribute malware.
Screenshot of the traffbiz.ru website
A script generates the hit counter image that is demonstrated to users. The script also includes two iframes which quietly redirect users to two links.
The hit counter code on traffbiz.ru
One of the links leads to Java (CVE-2011-3544) and PDF (CVE-2010-0188) exploits that download Trojan-Spy.Win32.Carberp.epm to the victim machine and launch it.
The Trojan attempts to connect to the command server by sending requests to three domains:
****case-now.com
****ssunrise.com
****owfood-cord.com
Curiously, according to whois data, these domains were registered on 20 March:

Curiously, according to whois data, these domains were registered on 20 March.
The command server to which Carberp connects is operational. It sends the command to the bot to download configuration files specifying which information the bot should steal and how. During the attack, Carberp intercepts the content of Citibank and Raiffeisen Bank webpages on the computer, as well as pages that use software created by BSS, a company which develops and deploys automated remote banking systems.
The second link leads to the infamous BlackHole Exploit Pack, which downloads and launches two malicious programs: a version of Carberp (Trojan-Spy.Win32.Carberp.epl) and a password-stealing Trojan (Trojan-PSW.Win32.Agent.acne).
Carberp also connects to a server located in Germany which has a different IP address. The domain name ****ltd.info was registered on 21 March:

The command center is operational but is not sending any commands as yet. The Trojan receives a list of plugins from that server.
The second piece of malware installed by the BlackHole Exploit Pack is designed to steal sensitive user data, such as FTP passwords. In addition, the Trojan modifies the hosts file to redirect users from vkontakte.ru and narod.ru sites to malicious servers.
In short, those responsible for developing Carberp remain at large and the cybercriminal gangs using the Trojan remain active. In other words, victory is a long way off.


























Carberp: it’s not over yet