
The most common method for wireless transmission of data is Bluetooth. Almost all mobile phones have a wireless module which enables the transmission of data to other Bluetooth enabled devices, and also enables the user to work in hands-free mode. It is an integral part of smartphones, PDAs and many notebooks.
As do most technological developments, Bluetooth quickly attracted the attention of hackers. Their attempts to find ways to use the protocol for their own ends were aided not just by users, who weren’t fully aware of the specifics of Bluetooth, but also by the errors which inevitably occurred when Bluetooth was implemented in mobile devices. In short, the protocol itself contains errors.
At the beginning of 2006, Kaspersky Lab published an overview of Bluetooth architecture, which included details of the most common Bluetooth vulnerabilities. We continued this research, as we think it is essential to look at Bluetooth from the point of view of the threat posed by malicious code. Mobile phones have already fallen victims to a range of viruses, including Cabir. This worm is the most widespread malicious virus, and uses Bluetooth in order to replicate.
There are three fundamental issues:
- Social engineering: hackers can access information on a user’s phone, either by using Bluetooth to established a ‘trusted device’ connection, or by persuading the user to lower security/ disable authentification for Bluetooth connections.
- Vulnerabilities in the protocol itself. Hackers can steal data from the telephone, make calls or send messages, conduct DoS attacks on the device, use a Bluetooth earpiece to listen to calls etc.
- Malicious code. A telephone can be infected by a worm, which will then send itself to other devices, by Bluetooth or by MMS. Data on the victim telephone may be corrupted, stolen, or encrypted.
It should be noted that in order for a Bluetooth handset to be attacked, it generally needs to be in ‘visible to all’ mode. Although there are ways to detect telephones which have Bluetooth enabled, but which are in invisible mode, this is complex, and therefore this article will not cover them. In order to detect a telephone in invisible mode, the attacker has to determine the phone’s MAC address; this not only takes a considerable amount of time, but there is also no guarantee of success.
At the end of 2005 and beginning of 2006 we conducted some research in Moscow, collecting statistics on the number of telephones with Bluetooth enabled. The tests were conducted in busy areas such as supermarkets and the Moscow metro. We detected approximately 100 devices in visible to all mode in the space of about one hour. Although this isn’t a very high number, it does indicate a potential dangerous concentration, and an significant virus outbreak could be caused if one of these devices was infected by Cabir.
At InfoSecurity 2006 in London, we planned to collect data both on WiFi networks and on Bluetooth devices. InfoSecurity seemed an ideal place for such research due to the large number of visitors. We also planned to conduct similar tests in other areas of London – including in the Underground – in order to compare the data with that collected in Moscow.
During the three days that we spent on our research, we detected more than 2000 Bluetooth enabled devices in visible to all mode. More than half these devices were detected at InfoSecurity, and belonged both to visitors and exhibitors. Similar research was recently conducted by one of our partners, the Finnish company F-Secure, at CeBIT 2006.
In addition to collecting statistics, which we then used almost immediately as part of our InfoSecurity presentation, we also went hunting for mobile viruses. We configured our telephones and laptops so that they were in visible to all mode, and so that all files would be automatically accepted and automatically saved. Device names were chosen to reflect the fact that the majority of mobile worms scan for accessible devices, and then send themselves to the first one listed.
We used BlueSoleil, Blue Auditor, and BT Scanner in our tests.
The first part of our testing took place, as mentioned above, at InfoSecurity. At one stage the number of devices within range was so large that the software had trouble processing all the data, with more than 100 devices in visible to all mode in a radius of 100 metres. On the last day of the exhibition there were fewer visitors; however, we still managed to detect over 700 devices in a mere one hour. If a single telephone had been infected, nearly all vulnerable devices would have been infected in the space of less than an hour.
The second part of our testing was conducted simulataneously with research into WiFi networks at Canary Wharf. We also went hunting on the London Underground during rush hour, and at Victoria, King’s Cross and Waterloo, three of London’s major train stations.
We have used data on epidemics caused by biological viruses and some mathematical epidemiological models in order to estimate the likelihood of a mobile virus epidemic. According to these estimates, using an average number of mobile devices per square metre, a worm for mobile devices would be able to infect nearly all vulnerable devices in Moscow within a period of 15 days. In reality, of course, it would probably take longer, but this does show that a local epidemic is a dangerous reality: it did actually come to pass last year, in Helsinki, at the World Athletics Championship (see F-Secure http://www.f-secure.com/weblog/archives/archive-082005.html#00000621).
Types of device
The data below shows which types of device use Bluetooth:
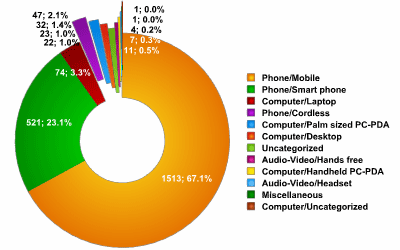
The vast majority of devices (over 70%) detected are standard mobile phones; handsets without a fully functional operating system, which theoretically can be infected only by viruses written for J2ME (Java Mobile). However, all of these telephones are vulnerable to Bluetooth attacks which exploit vulnerabilities in the Bluetooth protocol. During our testing in Moscow, we established that approximately 25% of the devices we detected were vulnerable to BlueSnarf attacks.
We did not attempt to gather such data at InfoSecurity, as we were unsure as to the legality of scanning for vulnerabilities. We therefore only collected data which is openly transmitted by devices, and used this data to draw our conclusions.
The second most widespread type of device was smartphones, making up approximately 25% of the total. This indicates the growing popularity of devices using Windows Mobile and Symbian operating systems. Given such a growth rate, it may well be that the number of standard handsets and smartphones will be equal by this time next year. Smartphones running under Symbian are currently the main target for virus writers; however, with Windows Mobile increasing in popularity, and overtaking Symbian in many countries, there will be an increased number of viruses targeting this operating system.
Laptops with Bluetooth adapters came in third place. Although they made up only 3% of all devices detected, they are probably more at risk of hackers attacks than standard telephones or smartphones. This is because the data stored on a laptop will be far more extensive, and far more potentially useful to hackers than data stored on a telephone.
Among other devices, we were surprised to detect a very small number of PDAs – less than 2% of all devices detected. This may be an indirect indication of the fact that PDA users are aware of Bluetooth security issues and exercise corresponding caution.
In all, we detected more than 2000 devices of 12 different types. This included devices detected as Uncategorized or Miscellaneous, but these made up less than 1% of the total.
Equipment manufacturers
The data collected on equipment manufacturers allows us to draw some conclusions about the state of the mobile device market. Data about the equipment manufacturer makes it possible to establish which operating system smartphones and PDAs are running, and to gain an overall picture of the manufacturer’s market share.
Overall, 35 separate manufacturers were detected, with 6 being the most popular. These 6 made up more than 67% of all devices detected. In a significant number of cases – 25.5% we were unable to establish the manufacturer.
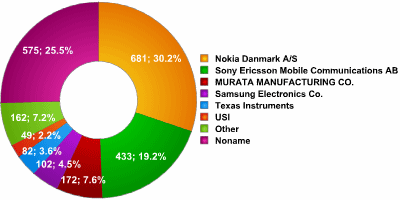
As the data shows, Nokia handsets are the overall leader, with handsets from Sony Ericsson coming second. USI achieved 6th place due to the number of computers and laptops detected.
As we have mentioned what type of equipment is produced by which manufacturers, it’s interesting to take a look at the following data:
| Nokia | |
| Phone/Smart phone | 26.7% |
| Phone/Mobile | 73.3% |
| Sony Ericsson | |
| Phone/Smart phone | 10.9% |
| Phone/Mobile | 88.9% |
| Miscellaneous | 0.2% |
| Murata | |
| Phone/Mobile | 99.4% |
| Computer/Desktop | 0.6% |
| Samsung | |
| Phone/Mobile | 65.7% |
| Phone/Cordless | 34.3% |
| Texas Instruments | |
| Phone/Mobile | 62.2% |
| Computer/Handheld PC-PDA | 26.8% |
| Phone/Smart phone | 9.8% |
| Computer/Palm sized PC-PDA | 1.2% |
| USI | |
| Computer/Laptop | 81.6% |
| Computer/Desktop | 18.4% |
| Unknown manufacturers | |
| Phone/Mobile | 50.8% |
| Phone/Smart phone | 41.9% |
| Computer/Laptop | 4.9% |
| Phone/Cordless | 2.1% |
| Computer/Desktop | 0.2% |
| Audio-Video/Hands free | 0.2% |
Accessible services
Data about accessible services is of interest both because it gives an idea about what hacker attacks can be carried out, and also the likelihood of a given device being infected with mobile malware. When a Bluetooth enabled device establishes a connection with another device, it makes a range of services available to the second device. For instance, if you establish a connection with your friend in order to transmit data, your handset simulateneously provides your friend with the ability to make calls and send SMSs from your phone, to look at your phone book etc. Put a hacker in the place of your friend – either because the hacker has used social engineering, or exploited a vulnerability in Bluetooth – and suddenly your phone is open to abuse.
The data we collected gives an idea of which services malicious users could access and then exploit.
Firstly, let’s look at the data on services overall. On the more than 2000 devices detected, we identified approximately 6000 services:
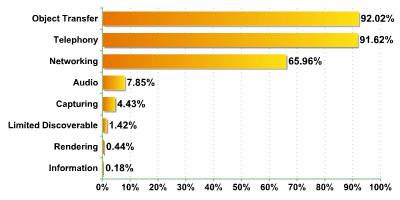
This means that on average (6000 divided by 2000) each device would have three accessible services. We did detect devices with 5 or 6 accessible services.
As the data above shows, the most common services were as follows:
- Object Transfer (transmitting/ receiving files) – used in more than 90% of devices
- Telephony (making/ receiving calls, messages) – used in more than 90% of devices
- Networking (provides Internet access using an internal modem) – used in more than 65% of devices
Given that telephones and smartphones are the most popular Bluetooth enabled devices, it’s worth taking a separate look at data for these devices.
Smartphones
The ratio of number of devices to services was approximately 1:2.
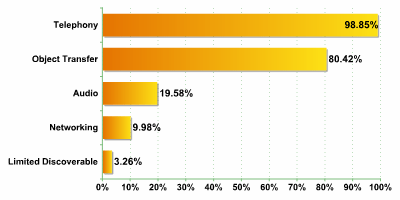
The data presented above differs significantly from the overall figures.
Overall, the most widespread service was OBEX. However, this service was detected on less than 90% of smartphones, with first place being taken instead by telephony. Audio, rather than the expected Networking, in third place, was also a surprise. It seems that smartphones are used to connect to wireless audio devices far more often than connecting the device to a network.
It should be stressed again that it is smartphones which are the main target for mobile malware, which requires Object Transfer to propagate. Approximately 30% of all smartphones detected were manufactured by Nokia, and consequently run under Symbian, the platform most used by mobile malware, including the worms Cabir and Comwar.
Telephones
The ratio of devices to accessible services for the telephones we detected was approximately 1:3. This was somewhat surprising, as smartphone functionality is far greater than that of standard telephones. However, this is probably due to the fact that the security policy of smartphone services is better configured.
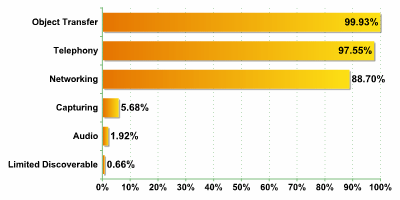
The top three services differ very little from the overall data which we gathered. This is hardly surprising given that telephones made up almost 70% of all the data detected.
Interestingly, the OBEX/ Telephony service ratio is the opposite to the data collected for smartphones. More than 97% of telephones had file transmission accessible, in contract to 80% of smartphones. The Networking service was also far more popular, being accessible in almost 90% of telephones.
In reality, vulnerabilities which can be exploited while using the Telephony service present a danger to both telephones and smartphones. The vulnerabilities and potential infection by viruses, which can be exploited during file transmission, are more of a threat to standard telephones than to smartphones. The Networking service, which is the basis of a number of other attacks, is also more common in telephones than in smartphones.
And what about our virus hunting? We didn’t manage to accept a single infected file. We did not detect any attempt to transmit an infected file. We did receive a number of files, mainly while we were in London itself rather than at InfoSecurity. However, they were all harmless; either bluejacking (sending music, graphics and games fils) is as common in Moscow as it is in London, or these files were sent by mistake. However, sending and receiving such files also presents a security risk for both parties: the sender may transmit the file to the wrong recipient, and the recipient may happily accept a virus file on the principle that all the files s/he has received until now have been harmless.
The results of our research make it clear that users should continue to be informed about the threat posed by the use of Bluetooth. Manufacturers of smartphones and telephones should also start paying increased attention to Bluetooth vulnerabilities and security loopholes in services which could be exploited by malicious users.






















Bluetooth: London 2006