
Today my colleague Vitaly Kamluk wrote about a new GpCode-like ransomware which encrypts user’s files with RSA-1024 and AES-256 crypto-algorithms. We’re continuing to investigate this malware and will notify you about our findings.
However, GpCode.ax is not the only piece of ransomware we found today. We’ve just discovered a malware which overwrites the master boot record (MBR) and demands a ransom to retrieve a password and restore the original MBR. This malware is detected as Trojan-Ransom.Win32.Seftad.a and Trojan-Ransom.Boot.Seftad.a.
This ransomware is downloaded by Trojan.Win32.Oficla.cw.
If Seftad.a was downloaded by Oficla.cw and run, the victim’s PC is rebooted and the following message appears on the screen:
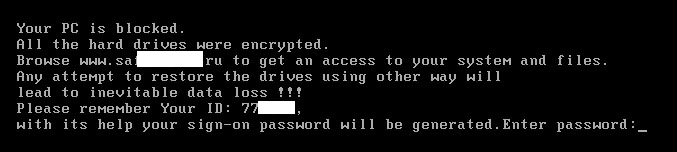
The victim does not know the ransomware password. So, after three incorrect attempts, the infected machine will reboot and the same message will appear on the screen.
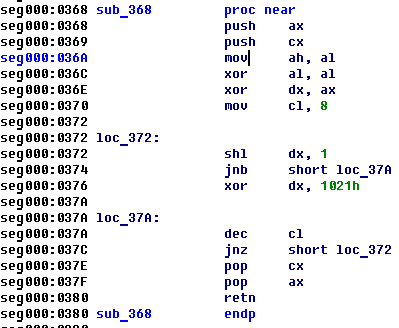
The entered symbols will be read with int 16h and then the following procedure will calculate the value and compare it with 2 bytes hash:
Fortunately, the hard drives or files are not encrypted as the malware author claims. This ransomware only overwrites the original MBR with a malicious one:

The original MBR is saved in the fourth sector of the hard drive with the malware’s infection marker stored at 0x9FE:

If the victim browses the malware author’s website, he is asked to pay $100 using ‘Paysafecard’ or ‘Ukash’.
If you are infected by this malware do not visit the website. Use the password ‘aaaaaaciip’ (without quotes) to restore the original MBR. If the password doesn’t work, you can cure your MBR with Kaspersky Rescue Disk 10.
UPD: We’ve just found a new version of Trojan-Ransom.Win32.Seftad. Detection will be added as soon as possible. Use the password ‘aaaaadabia’ (without quotes) to restore the original MBR.
UPD2: Do not use ‘fixmbr’ utility in case you are infected with this trojan because it will not restore your partition table and you won’t be able to boot your OS. If you are infected and passwords are invalid plug in your hard drive to a working computer and use this free tool which will restore your MBR.





















And Now, an MBR Ransomware