
Friday May 12th marked the start of the dizzying madness that has been ‘WannaCry’, the largest ransomware infection in history. Defenders have been running around with their heads on fire trying to get ahead of the infection and to understand the malware’s capabilities. In the process, a lot of wires have gotten crossed and we figured it’s time to sit down and set the record straight on what we know, what we wish we knew, and what the near future might hold for us going forward.
In the interest of standing by our stated mission, ‘We’re Here to Save the World’, we’re also sharing IOCs and Yara rules below.
Please remember: Patch, Patch, Patch!
For a refresher on the weekend of madness, please see our original blog.
How did it all start? Was there an e-mail attack vector? Phishing link?
To date, we could not find an e-mail attack vector for Wannacry. We are still investigating leads that suggest compromised sites were used to target some customers. So far, we can confirm that our users are getting attacked using an implementation of the famous EternalBlue exploit leaked by the Shadowbrokers in April. The exploit installs the DoublePulsar backdoor, which is further leveraged to infect a system. Even if the EternalBlue exploit fails in the first place, the attack code still tries to leverage the DoublePulsar backdoor which might have been installed in a previous attack.
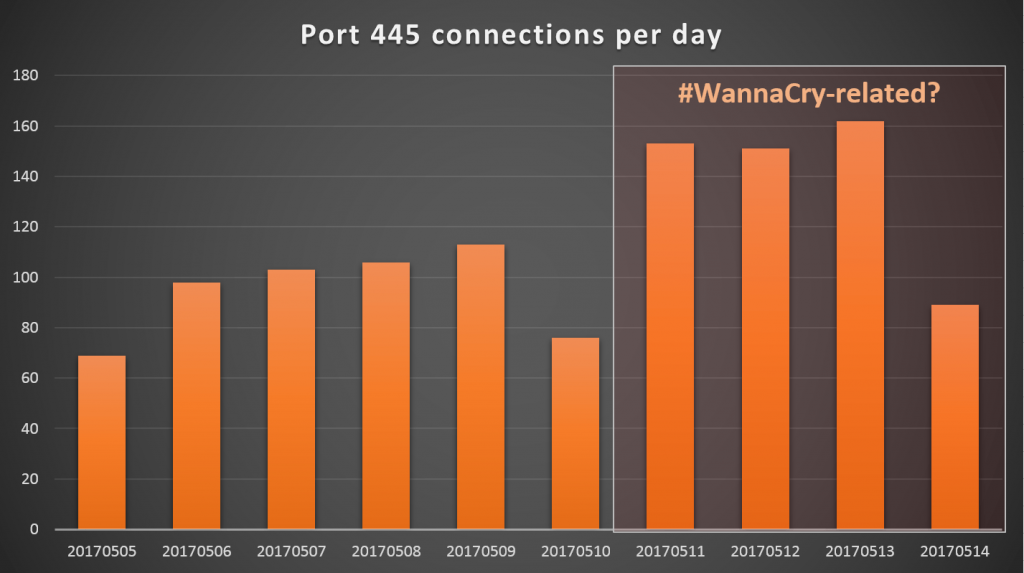
Perhaps the main reason why Wannacry was so successful is the fact that the EternalBlue exploit works over the Internet without requiring any user interaction. It works on top of TCP port 445. Last week, our internet facing sensors registered an uptick in port 445 connections on Thursday May 11th, one day before the major outbreak noted on Friday. This means it’s possible the worm was released on Thursday, possibly even late Wednesday evening. The uptick in Port 445 traffic is also confirmed by the SANS DShield project’s graphics.
Port 445 connections per day
I’ve seen conflicting reports about the exploit. Is it targeting SMBv1 or SMBv2?
The vulnerability exploited by the EternalBlue tool lies in the SMBv1 implementation. However, to exploit it, the tool also uses SMBv2. This means that it uses both SMBv1 and SMBv2 packets during the attack. Disabling SMBv1 or SMBv2 prevents the infection; however, while disabling SMBv1 (an old protocol) has no significant impact on modern systems, disabling SMBv2 can cause problems. This is why it is highly recommended to disable SMBv1 for the current attack and for the future.
What is the killswitch? Can we rely on it?
The worm-spreading part of the Wannacry – which is designed to infect other computers — has a special check at the beginning. It tries to connect to a hardcoded website on the Internet and if the connection FAILS, it continues with the attack. If the connection WORKS, it exits. Thus, by registering this domain and pointing it to a sinkhole server, a researcher from the U.K. successfully slowed the spread of the worm.
Can we ultimately rely on this? Well, there has been a lot of speculation about the effectiveness of this killswitch. On the one hand, it does stop further spread of the infection. However, only if the worm is able to connect to the Internet. Many corporate networks have firewalls blocking internet connections unless a proxy is used. For these, the worm will continue to spread in the local network. On the other hand, there is nothing stopping the attackers from releasing a new variant that does not implement a killswitch.
Why did the attackers add a killswitch in the first place?
This is a very good question. Some possible explanations:
- They were afraid the attack might get out of control and wanted a way to stop the propagation.
- They coded it as an anti-sandbox check (some sandboxes emulate all internet connections and make them appear to work even if they do not exist)
Has this attack been contained?
We started tracking the attack early today to determine if it’s spiking again. Since 06.00 UTC/GMT Monday 15th May, we observed a sixfold decrease in attacks across our customer base than during the first hours on Friday May 12th.
This suggests infections based on current variants may be under control.
Wait, what do you mean by “current variants”? Is there a second wave of attacks?
Over the weekend two notable variants emerged. Kaspersky Lab does not believe any of these variants were created by the original authors –they were most likely patched by others keen to exploit the attack separately and independently.
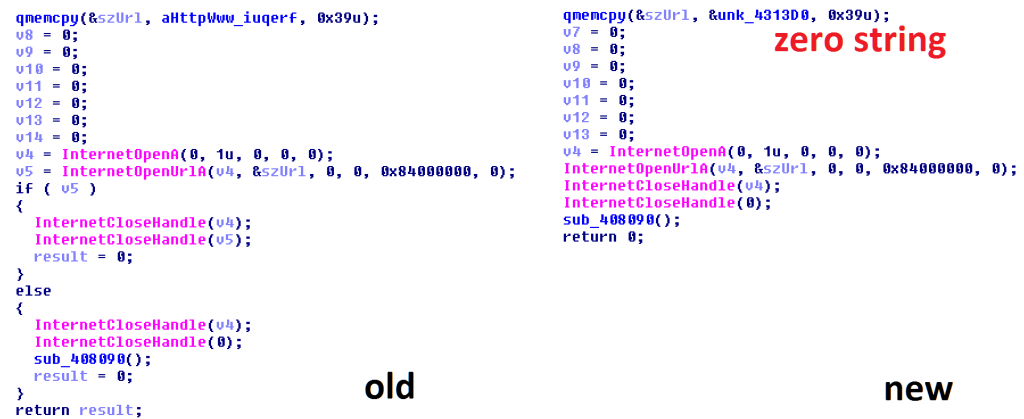
The first one started spreading on Sunday morning, at around 02.00 UTC/GMT and was patched to connect to a different domain (ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com). Kaspersky Lab has so far noted three victims for this variant, located in Russia and Brazil.
Code patch from d724d8cc6420f06e8a48752f0da11c66
The second variation that appeared during the weekend appears to have been patched to remove the killswitch. This variant does not appear to be spreading, possibly due to a bug.
| Sample MD5 | In the wild | Killswitch present? | Domain killswitch |
| d5dcd28612f4d6ffca0cfeaefd606bcf | Yes | Yes | ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com |
| d724d8cc6420f06e8a48752f0da11c66 | No | No | n/a |
Does the second wave contain the killswitch?
The d5dcd28612f4d6ffca0cfeaefd606bcf sample distributed on Sunday night (first reports around 02:00am UTC) contains a killswitch domain. This domain (ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com) is only two bytes different from the original:
| Sample MD5 | Killswitch domain |
| Old | iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com |
| New (see above) | ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com |
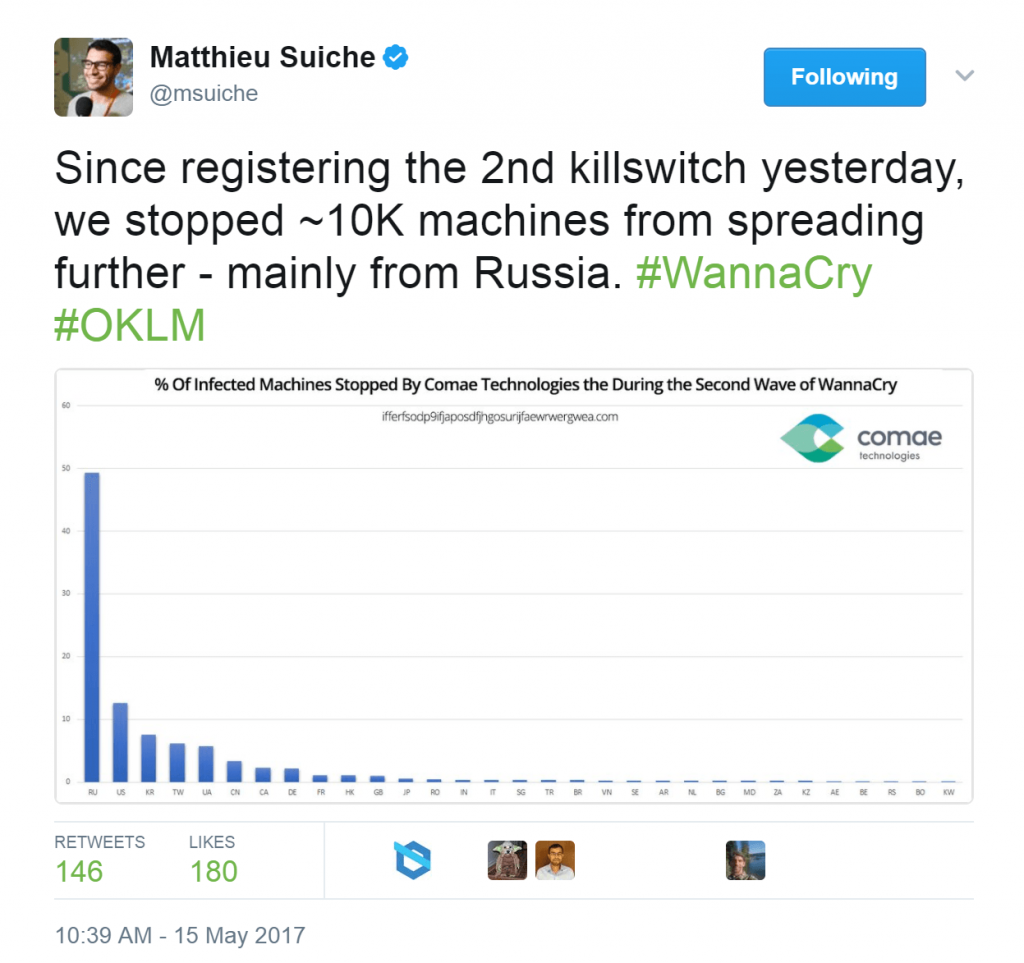
The second domain was sinkholed by Matt Suiche of Comae Technologies, who reported stopping about 10,000 infections from spreading further:
How much money has been paid by victims so far?
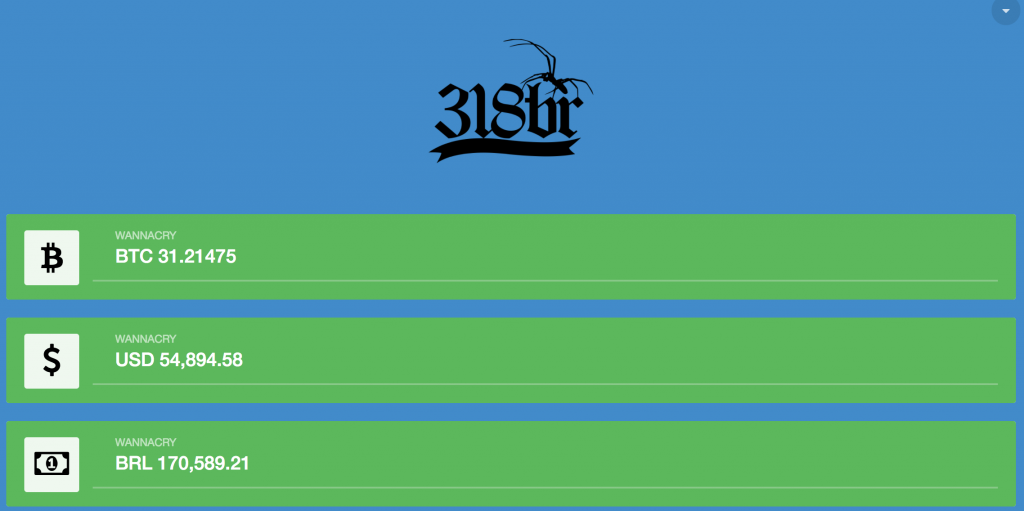
WannaCry Wallet Tracker as of Monday May 15th.
Multiple attempts have been made at tracking transactions to known bitcoin wallets used by WannaCry. The tracker ‘howmuchwannacrypaidthehacker.com’ has the latest count (at the time of writing) at upwards of 31BTC, or close to $55,000 USD.
What will the attackers do with the money?
An Evil Lair?
We believe it’s unlikely the attackers will be able to do anything with the bitcoins, considering the current high level of interest in this story. Even though the wallet owners are anonymous, the transactions are visible to everybody and can be tracked. Once the bitcoins reach a payment point, where the attackers use them to purchase something in the real world, that payment can be tracked to shipment details, services, or other IPs, effectively, increasing the chances of getting caught.
Does payment guarantee the recovery of files?
We don’t know. Since we are dealing with criminals, there is no reason to expect them to honor the deal, especially in a situation where all the world is closely tracking this campaign and disrupting it as much as possible. Paying the ransom amounts to funding the next wave.
Do not pay the ransom.
How does the worm spread inside a local corporate network?
The malware includes a worm functionality that tries to infect other unpatched Windows machines inside the local network, generating large SMB traffic. Basically it scans LAN IPS for SMB/445 port open. Where it finds any, it delivers the EternalBlue exploit.
Have any other exploits been used?
The only exploit observed so far being used in this campaign is the EternalBlue exploit leaked by Shadow Brokers.
Interestingly, once the malware infects a computer, it runs shellcode to drop and execute its payload. The payload code is available for both 32- and 64-bit systems, runs in ring-0, and seems to be based on the DoublePulsar backdoor leaked by Shadow Brokers in their ‘Lost in Translation‘ blog post .
Can you explain what happens for victims behind a proxy?
The killswitch prevented the main strain of the malware from encrypting the files in the infected computers, basically by checking if a given domain was registered or not. However WannaCry does not check for the presence of any proxy, so it is likely that samples running inside of an organization will not be able to reach the killswitch domain, even if it’s already registered. That means their files will continue to be encrypted.
Who is behind the attack? Is it just one group or multiple groups of attackers?
The attackers didn’t leave many clues about their identities or whereabouts. We are still investigating several possible leads and we’re sharing all relevant information with law enforcement.
At the moment, we haven’t seen any indicators that point towards any known groups. Some early variants of the Wannacry ransomware seem to have been used in March 2017, maybe some as early as February 2017. We are still researching these early variants, scraping them for clues.
Is this primarily targeting Russians?
The spread of the worm does not target a specific geolocation. The distribution is random, selecting IPs from the internet and affected local networks. Nevertheless, a large amount of the infections are in Russia, about 66% of the total attacks we have seen. The skew in distribution is likely due a combination of our increased visibility into Russia as well as a likely prevalence of unpatched systems.
Are you working with law enforcement to help contain this attack?
Yes, we are working with several law enforcement agencies and have provided them with information to help mitigate the attack.
Microsoft is warning against governments stockpiling cyberweapons and called for a Digital Geneva Convention. Will this help?
Kaspersky Lab supports Brad Smith’s call-to-action for governments and industries around the world to take critically important steps to help make a better digital future for all. We strongly believe the world needs an international digital convention and support with the creation of a neutral international cyber organization and firmly supports a pledge from companies to not conduct offensive cyber activities and protect their users from all cyberattacks. For more details please see: https://www.forbes.com/sites/eugenekaspersky/2017/02/15/a-digital-geneva-convention-a-great-idea/#abeff891e6e1
What should I do right now to make sure my organization is protected?
Our recommendations:
- Install the MS Security Bulletin patches for MS17-010. Please note that Microsoft also released an emergency patch for Windows XP, which is out of support!
- Disable SMBv1.
- Backup your data on a regular basis and be sure to store the backups offline.
- Limit administrative privileges in the network.
- Segment your network.
- Make sure all nodes have security software installed and updated.
- Kaspersky users: make sure System Watcher is enabled and the software updated. System watcher will ensure rollback of any encrypted files.
- For those who do not use Kaspersky Lab solutions, we suggest installing the free Kaspersky Anti-Ransomware Tool for business (KART).
- WannaCry is also targeting embedded systems. We recommend ensuring that dedicated security solutions for embedded systems are installed, and that they have both anti-malware protection and Default Deny functionality enabled.
Did Kaspersky block the attack for every target that had the software installed?
Our recent products include a module named System Watcher, which is designed to stop ransomware attacks. It was successful in blocking the damage from Wannacry, proving once again its effectiveness. Additionally, our products include specific detection subroutines which stopped the spreading of the attacks inside local networks. Since Saturday, our products also blocked the network level attacks through IDS components.
I’m running Windows XP – how can I protect myself?
First of all, stop running Windows XP. It is a 16-year-old operating system which is no longer officially supported by Microsoft. We recommend you upgrade to Windows 8.1 or 10. If you absolutely need to run Windows XP, you can download the emergency patch from Microsoft here:
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
However, prepare for a rough ride ahead, as other vulnerabilities will most likely remain open and leave you vulnerable in the future to other attacks.
Do you have YARA rules and IOCs for everything we know so far?
Multiple YARA rules have been released so far, with varying degrees of accuracy. Florian Roth has published a good Wannacry YARA set on his GitHub. Another set of YARA rules has been published by US-CERT, however, they produce false positives and are not recommended at this time. Our own YARA rules can be found below.
Indicators of Compromise
Network traffic to the following hosts:
- iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
- ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
Filenames on disk:
- mssecsvc.exe
- taskdl.exe
- taskse.exe
- wannacry.exe
- tasksche.exe
Hashes for the variants with different kill switches:
- d5dcd28612f4d6ffca0cfeaefd606bcf
- d724d8cc6420f06e8a48752f0da11c66
For more malware hashes, please see our previous blogpost.
Yara rules
rule crimeware_Wannacry_worm {
meta:
description = “Find Wannacry worm carrier samples”
date = “2017-05-14”
version = “1.0”
author = “Kaspersky Lab”
tlp = “GREEN”
strings:
- $a0=”__TREEID__PLACEHOLDER__” ascii wide fullword
- $a1=”__USERID__PLACEHOLDER__” ascii wide fullword
- $a2=”userid” ascii wide fullword
- $a3=”treeid” ascii wide fullword
- $a4=”__TREEPATH_REPLACE__” ascii wide fullword
- $a5=”\\\\%s\\IPC$” ascii wide fullword
- $a6=”Microsoft Base Cryptographic Provider v1.0″ ascii wide fullword
- $a7=”mssecsvc2.0″ ascii wide fullword
- $a8=”Microsoft Security Center (2.0) Service” ascii wide fullword
- $a9=”%s -m security” ascii wide fullword
- $a10=”C:\\%s\\qeriuwjhrf” ascii wide fullword
- $a11=”tasksche.exe” ascii wide fullword
condition:
- ((uint16(0) == 0x5A4D)) and (filesize < 15000000) and
- (8 of ($a*))
}
rule crimeware_Wannacry_ransomware {
meta:
- description = “Find Wannacry ransomware module”
- date = “2017-05-14”
- version = “1.1”
- author = “Kaspersky Lab”
- tlp = “GREEN”
strings:
-
- //list of extensions targeted by the ransomware module
- $a1={
- 2E 00 64 00 65 00 72 00 00 00 00 00 2E 00 70 00
- 66 00 78 00 00 00 00 00 2E 00 6B 00 65 00 79 00
- 00 00 00 00 2E 00 63 00 72 00 74 00 00 00 00 00
- 2E 00 63 00 73 00 72 00 00 00 00 00 2E 00 70 00
- 31 00 32 00 00 00 00 00 2E 00 70 00 65 00 6D 00
- 00 00 00 00 2E 00 6F 00 64 00 74 00 00 00 00 00
- 2E 00 6F 00 74 00 74 00 00 00 00 00 2E 00 73 00
- 78 00 77 00 00 00 00 00 2E 00 73 00 74 00 77 00
- 00 00 00 00 2E 00 75 00 6F 00 74 00 00 00 00 00
- 2E 00 33 00 64 00 73 00 00 00 00 00 2E 00 6D 00
- 61 00 78 00 00 00 00 00 2E 00 33 00 64 00 6D 00
- 00 00 00 00 2E 00 6F 00 64 00 73 00 00 00 00 00
- 2E 00 6F 00 74 00 73 00 00 00 00 00 2E 00 73 00
- 78 00 63 00 00 00 00 00 2E 00 73 00 74 00 63 00
- 00 00 00 00 2E 00 64 00 69 00 66 00 00 00 00 00
- 2E 00 73 00 6C 00 6B 00 00 00 00 00 2E 00 77 00
- 62 00 32 00 00 00 00 00 2E 00 6F 00 64 00 70 00
- 00 00 00 00 2E 00 6F 00 74 00 70 00 00 00 00 00
- 2E 00 73 00 78 00 64 00 00 00 00 00 2E 00 73 00
- 74 00 64 00 00 00 00 00 2E 00 75 00 6F 00 70 00
- 00 00 00 00 2E 00 6F 00 64 00 67 00 00 00 00 00
- 2E 00 6F 00 74 00 67 00 00 00 00 00 2E 00 73 00
- 78 00 6D 00 00 00 00 00 2E 00 6D 00 6D 00 6C 00
- 00 00 00 00 2E 00 6C 00 61 00 79 00 00 00 00 00
- 2E 00 6C 00 61 00 79 00 36 00 00 00 2E 00 61 00
- 73 00 63 00 00 00 00 00 2E 00 73 00 71 00 6C 00
- 69 00 74 00 65 00 33 00 00 00 00 00 2E 00 73 00
- 71 00 6C 00 69 00 74 00 65 00 64 00 62 00 00 00
- 2E 00 73 00 71 00 6C 00 00 00 00 00 2E 00 61 00
- 63 00 63 00 64 00 62 00 00 00 00 00 2E 00 6D 00
- 64 00 62 00 00 00 00 00 2E 00 64 00 62 00 00 00
- 2E 00 64 00 62 00 66 00 00 00 00 00 2E 00 6F 00
- 64 00 62 00 00 00 00 00 2E 00 66 00 72 00 6D 00
- 00 00 00 00 2E 00 6D 00 79 00 64 00 00 00 00 00
- 2E 00 6D 00 79 00 69 00 00 00 00 00 2E 00 69 00
- 62 00 64 00 00 00 00 00 2E 00 6D 00 64 00 66 00
- 00 00 00 00 2E 00 6C 00 64 00 66 00 00 00 00 00
- 2E 00 73 00 6C 00 6E 00 00 00 00 00 2E 00 73 00
- 75 00 6F 00 00 00 00 00 2E 00 63 00 73 00 00 00
- 2E 00 63 00 00 00 00 00 2E 00 63 00 70 00 70 00
- 00 00 00 00 2E 00 70 00 61 00 73 00 00 00 00 00
- 2E 00 68 00 00 00 00 00 2E 00 61 00 73 00 6D 00
- 00 00 00 00 2E 00 6A 00 73 00 00 00 2E 00 63 00
- 6D 00 64 00 00 00 00 00 2E 00 62 00 61 00 74 00
- 00 00 00 00 2E 00 70 00 73 00 31 00 00 00 00 00
- 2E 00 76 00 62 00 73 00 00 00 00 00 2E 00 76 00
- 62 00 00 00 2E 00 70 00 6C 00 00 00 2E 00 64 00
- 69 00 70 00 00 00 00 00 2E 00 64 00 63 00 68 00
- 00 00 00 00 2E 00 73 00 63 00 68 00 00 00 00 00
- 2E 00 62 00 72 00 64 00 00 00 00 00 2E 00 6A 00
- 73 00 70 00 00 00 00 00 2E 00 70 00 68 00 70 00
- 00 00 00 00 2E 00 61 00 73 00 70 00 00 00 00 00
- 2E 00 72 00 62 00 00 00 2E 00 6A 00 61 00 76 00
- 61 00 00 00 2E 00 6A 00 61 00 72 00 00 00 00 00
- 2E 00 63 00 6C 00 61 00 73 00 73 00 00 00 00 00
- 2E 00 73 00 68 00 00 00 2E 00 6D 00 70 00 33 00
- 00 00 00 00 2E 00 77 00 61 00 76 00 00 00 00 00
- 2E 00 73 00 77 00 66 00 00 00 00 00 2E 00 66 00
- 6C 00 61 00 00 00 00 00 2E 00 77 00 6D 00 76 00
- 00 00 00 00 2E 00 6D 00 70 00 67 00 00 00 00 00
- 2E 00 76 00 6F 00 62 00 00 00 00 00 2E 00 6D 00
- 70 00 65 00 67 00 00 00 2E 00 61 00 73 00 66 00
- 00 00 00 00 2E 00 61 00 76 00 69 00 00 00 00 00
- 2E 00 6D 00 6F 00 76 00 00 00 00 00 2E 00 6D 00
- 70 00 34 00 00 00 00 00 2E 00 33 00 67 00 70 00
- 00 00 00 00 2E 00 6D 00 6B 00 76 00 00 00 00 00
- 2E 00 33 00 67 00 32 00 00 00 00 00 2E 00 66 00
- 6C 00 76 00 00 00 00 00 2E 00 77 00 6D 00 61 00
- 00 00 00 00 2E 00 6D 00 69 00 64 00 00 00 00 00
- 2E 00 6D 00 33 00 75 00 00 00 00 00 2E 00 6D 00
- 34 00 75 00 00 00 00 00 2E 00 64 00 6A 00 76 00
- 75 00 00 00 2E 00 73 00 76 00 67 00 00 00 00 00
- 2E 00 61 00 69 00 00 00 2E 00 70 00 73 00 64 00
- 00 00 00 00 2E 00 6E 00 65 00 66 00 00 00 00 00
- 2E 00 74 00 69 00 66 00 66 00 00 00 2E 00 74 00
- 69 00 66 00 00 00 00 00 2E 00 63 00 67 00 6D 00
- 00 00 00 00 2E 00 72 00 61 00 77 00 00 00 00 00
- 2E 00 67 00 69 00 66 00 00 00 00 00 2E 00 70 00
}
condition:
((uint16(0) == 0x5A4D)) and (filesize < 15000000) and
any of them
}
WannaCry FAQ: What you need to know today





















Chinnon Santos
Very Good Post, KIS is the Best…
Kieren Brown
very informative. But one question I have is not answered here… that is which”files” are being encrypted ransomed off? from my experience it can take a few hours to encrypt the contents of an entire hard drive. so assume only part of the victims hard drive is being encrypted?
if so how does it decide what to encrypt?
Graves
It can take hours to encrypt the hard drive, but the ransom screen doesn’t pop up til it’s complete. Most ransomware attacks like this run for a few hours to encrypt the disk, then pop the screen, so it’s critical for the software to remain undetected while it runs.
Sabu
Very informaitve and helpful
Vaibhav Tyagi
Thanks KIS
Reg Farrar
How do you disable SMBv1
TheWickerMan
https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
Frank_Castle
Hah, the bitcoin will be washed thru a bitcoin tumbler, any rookie hacker knows how to do that. It will be untraceable, unless they are really noob hackers. These guys will be as good as gone, unless one breaks OPSEC, they will not be found.
Gary Younkin
How do I obtain the Microsoft MS17-010 for installation on the second computer under your care, same ISP???
Bogdan
Disable SMB v1 in Managed Environments with Group Policy:
https://blogs.technet.microsoft.com/staysafe/2017/05/17/disable-smb-v1-in-managed-environments-with-ad-group-policy/
https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1-smbv2-and-smbv3-in-windows-and-windows-server
SN Prasadd Dodla
It is very good information to acquire update information
Steven Harris
How does an ATM open an infected fire? Something about the mode of transmission is missing. With a new virus or any human disease the investigators always want to know how it is spread. Just to say it might be an email is not truly helpful. Can I get this from going on my bank web site, or shopping online?
Thanks.
Allen Leinwand
Thank you for this excellent article.
I am running XP on on older laptop, with no local network. I was planning to upgrade to Windows 7. (The laptop does not have enough memory to run W 10). But you say “We recommend you upgrade to Windows 8.1 or 10”.
Questions:
–Can W7 be made secure enough?
–Is there a downloadable test to check if the laptop can run W8.1?
–Where can I get W8.1, if that is the only solution?