
The Mirai botnet, which is made up of IoT devices and which was involved in DDoS attacks whose scale broke all possible records, causing denial of service across an entire region, has been extensively covered by the mass media. Given that the botnet’s source code has been made publicly available and that the Internet of Things trend is on the rise, no decline in IoT botnet activity should be expected in the near future.
To put this in perspective, recall the year 2012, when the source code of the Zeus banker Trojan was made publicly available. A huge number of modifications of the Trojan appeared as a result of this, many of which are still active and rank among the most widespread financial malware. Similarly, the recent leak is likely to result in the emergence of Mirai modifications, created by cybercriminals and based on the source code that was made public.
The botnet remains active. We carried out an analysis of its activity to find out how Mirai operates, what objectives its owners are pursuing and, most importantly, what needs to be done to avoid becoming part of the botnet in the future.
How Mirai Works
Based on the botnet’s source code that was published on a user forum, Mirai consists of the following components:
- a command-and-control center (C&C) that contains a MySQL database of all infected IoT devices (bots) and sends commands to intermediate command distribution servers;
- a Scan Receiver component that collects the results of each bot’s operation and forwards them to the component that downloads the bot onto vulnerable devices (the Distributor);
- a downloader component, which delivers the bot’s binary file to a vulnerable device (using the wget and tftp utilities – but if they are not present in the system, it uses its own proprietary downloader);
- a bot, which, after being launched on an infected device, connects to the command-and-control center, scans an IP range (SYN scanning) for vulnerable IoT devices and sends the scan results to the Scan Receiver component in order for further malicious code to be subsequently downloaded to the device.
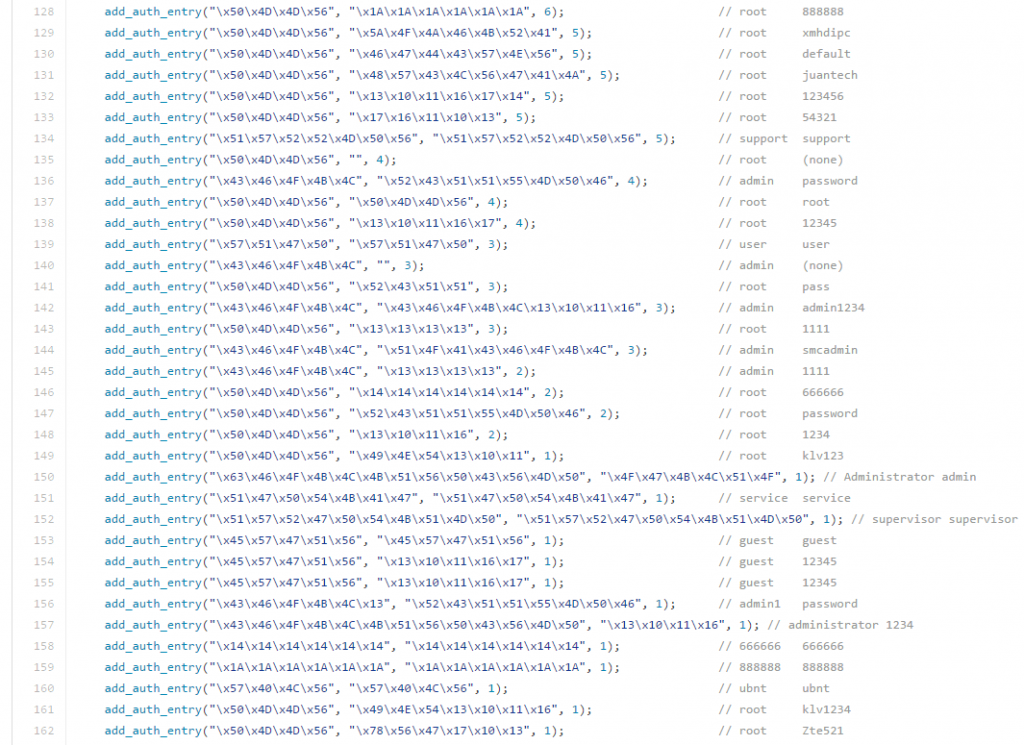
An important feature of the way the Mirai botnet scans devices is that the bot uses a login and password dictionary when trying to connect to a device. The author of the original Mirai included a relatively small list of logins and passwords for connecting to different devices. However, we have seen a significant expansion of the login and password list since then, achieved by including default logins and passwords for a variety of IoT devices, which means that multiple modifications of the bot now exist.
List of logins and passwords used by the original Mirai in its search for vulnerable IoT devices
However, this is by no means all the Mirai botnet can tell us about itself.
Analysis of the Botnet’s Activity
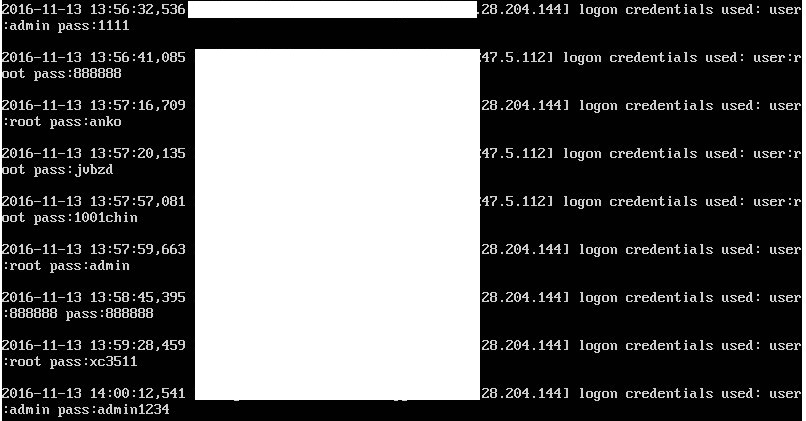
All you need to do to evaluate the Mirai botnet’s current activity is to deploy a server with an open telnet port somewhere on the Internet and analyze connection attempts made by different bots. For example, we detected the first attempts to connect to our telnet port, by several different hosts, within three minutes of putting our experimental server online.
Two facts indicate that these connections are made by bots of the original Mirai or its modifications (i.e., by infected devices):
- the accounts used by the bots in their attempts to establish a connection are found on the original botnet’s brute force word list;
- an analysis of connection sources has shown that infected hosts that perform scanning are in most cases IoT devices (cameras and routers of different manufacturers).
Connection attempts by infected Mirai workstations in search of IoT devices using default passwords
Here is a list of login and password pairs most often used by Mirai bots in connection attempts:
| “Login:password” combinations | |
| 1 | admin : admin |
| 2 | root : xc3511 |
| 3 | root : vizxv |
| 4 | root : juantech |
| 5 | root : default |
| 6 | admin : admin1234 |
| 7 | root : password |
| 8 | root : root |
| 9 | root : xmhdipc |
| 10 | admin : smcadmin |
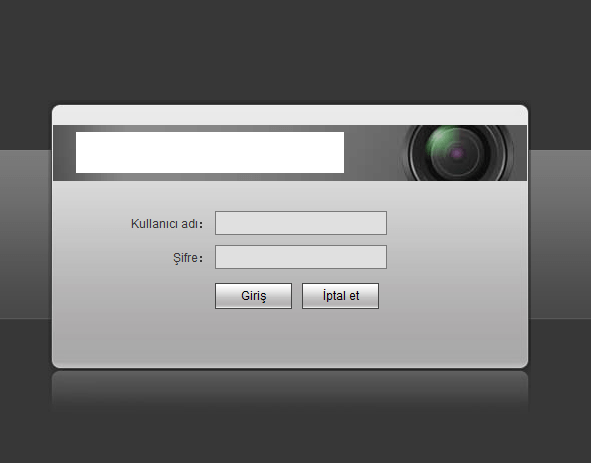
If you ignore trivial combinations like “root:root” or “admin:admin”, you can get a good idea of which equipment the botnet is looking for. For example, the pairs “root:xc3511” and “root:vizxv” are default accounts for IP cameras made by rather large Chinese manufacturers.
Admin panel for managing an IP camera that is part of the botnet
As for the activity of the botnet itself, you can analyze the number of login attempts over 24 hours and see for yourself. On December 13, 2016 we recorded 5,553 attempts by Mirai bots to connect to our server, while 10 days before that, on December 3, 2016, we recorded 8,689 connection attempts. Does this mean that the botnet is losing power? Reduced activity related to searching for new potential bots might certainly be an indication that the rate at which Mirai is infecting new devices is falling, but it is too early to draw any conclusions.
How to Avoid Becoming Part of the Mirai Botnet
We recommend the following measures to prevent your devices from being included in the Mirai botnet:
- Change the default account parameters on each of your devices. Account passwords should be at least 8 characters long and include digits, upper-case letters and special characters.
- On each device, install the latest updates provided by the manufacturer.
- It is a good idea to block all potential entry points to the operating system on your devices (telnet/SSH/web panel, etc.) from being accessed over the Internet.
More details about the Mirai botnet are available to Kaspersky Intelligence Services reports’ subscribers. For more information, email intelreports@kaspersky.com





















Is Mirai Really as Black as It’s Being Painted?