
A few days ago, Microsoft published the “critical” MS16-120 security bulletin with fixes for vulnerabilities in Microsoft Windows, Microsoft Office, Skype for Business, Silverlight and Microsoft Lync.
One of the vulnerabilities – CVE-2016-3393 – was reported to Microsoft by Kaspersky Lab in September 2016.
Here’s a bit of background on how this zero-day was discovered. A few of months ago, we deployed a new set of technologies in our products to identify and block zero-day attacks. These technologies proved their effectiveness earlier this year, when we discovered two Adobe Flash zero-day exploits – CVE-2016-1010 and CVE-2016-4171. Two Windows EoP exploits have also been found with the help of this technology. One is CVE-2016-0165. The other is CVE-2016-3393.
Like most zero-day exploits found in the wild today, CVE-2016-3393 is used by an APT group we call FruityArmor. FruityArmor is perhaps a bit unusual due to the fact that it leverages an attack platform that is built entirely around PowerShell. The group’s primary malware implant is written in PowerShell and all commands from the operators are also sent in the form of PowerShell scripts.
In this report we describe the vulnerability that was used by this group to elevate privileges on a victim’s machine. Please keep in mind that we will not be publishing all the details about this vulnerability because of the risk that other threat actors may use them in their attacks.
Attack chain description
To achieve remote code execution on a victim’s machine, FruityArmor normally relies on a browser exploit. Since many modern browsers are built around sandboxes, a single exploit is generally not sufficient to allow full access to a targeted machine. Most of the recent attacks we’ve seen that rely on a browser exploit are combined with an EoP exploit, which allows for a reliable sandbox escape.
In the case of FruityArmor, the initial browser exploitation is always followed by an EoP exploit. This comes in the form of a module, which runs directly in memory. The main goal of this module is to unpack a specially crafted TTF font containing the CVE-2016-3393 exploit. After unpacking, the module directly loads the code exploit from memory with the help of AddFontMemResourceEx. After successfully leveraging CVE-2016-3393, a second stage payload is executed with higher privileges to execute PowerShell with a meterpreter-style script that connects to the C&C.
EOP zero-day details
The vulnerability is located in the cjComputeGLYPHSET_MSFT_GENERAL function from the Win32k.sys system module. This function parses the cmap table and fills internal structures. The CMAP structure looks like this:
The most interesting parts of this structure are two arrays – endCount and startCount. The exploit contains the next cmap table with segments:
To compute how much memory to allocate to internal structures, the function executes this code:
After computing this number, the function allocates memory for structures in the following way:
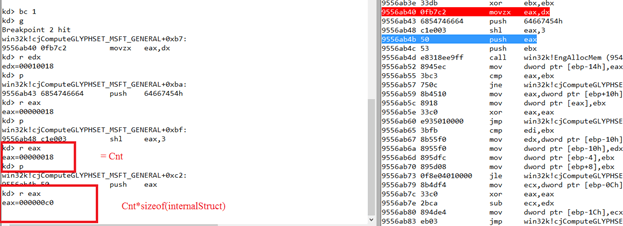
The problem is that if we compute the entire table, we will achieve an integer overflow and the cnt variable will contain an incorrect value.
In kernel, we see the following picture:
The code allocates memory only for 0x18 InternalStruct but then there is a loop for all the segments range (this value was extracted from the file directly):
Using the cmap table, the v44 variable (index) could be controlled and, as a result, we get memory corruption. To achieve it, the attacker can do the following:
- Make an integer overflow in win32k!cjComputeGLYPHSET_MSFT_GENERAL
- Make a specific segment ranges in font file to access interesting memory.
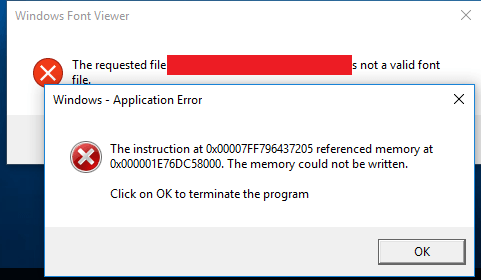
What about Windows 10? As most of you know, the font processing in Windows 10 is performed in a special user mode process with restricted privileges. This is a very good solution but the code has the same bug in the TTF processing.
As a result, if you load/open this font exploit in Windows 10, you will see the crash of fontdrvhost.exe:
Kaspersky Lab detects this exploit as:
- HEUR:Exploit.Win32.Generic
- PDM:Exploit.Win32.Generic
We would like to thank Microsoft for their swift response in closing this security hole.
* More information about the FruityArmor APT group is available to customers of Kaspersky Intelligence Services. Contact: intelreports@kaspersky.com





























Windows zero-day exploit used in targeted attacks by FruityArmor APT