
In early August we detected several cases of a banking Trojan being downloaded automatically when users viewed certain news sites on their Android devices. Later it became apparent that this was being caused by advertising messages from the Google AdSense network, and was not restricted to news sites. In fact, any site using AdSense to display adverts could potentially have displayed messages that downloaded the dangerous Trojan-Banker.AndroidOS.Svpeng and automatically saved it to the device’s SD card. This behavior surprised us: typically, the browser warns users about downloading a potentially dangerous file, and offers them a choice of whether or not to save the file. We intercepted traffic coming from the attacked device when this sort of “advert” was displayed, and figured out how the malicious program was downloaded and automatically saved.
Some statistics
First of all, let’s provide some information about the latest versions of Trojan-Banker.AndroidOS.Svpeng. It is limited to Russia and the CIS (more about this later). Below is a graph showing detections of the Trojan’s latest version – Svpeng.q.
And here is the graph for the previous version that was distributed in July 2016, also via AdSense:
As you can see from the graphs, within a two-month period Svpeng was detected on the computers of approximately 318,000 users, with the detection rate peaking at around 37,000 attacked users in one day. The high rates and abrupt changes in the number of detections are easy to explain: Google has been quick to block the ads that the Trojan uses for propagation. However, this is a reactive rather than a proactive approach – the malicious ads were blocked after the Trojan was already on thousands of Android devices. It is also worth noting that there were multiple occasions in the past two months when these ads found their way on to AdSense; similar attacks have been occurring up to the present time, with the most recent attack registered on 19 October 2016.
Now for the juicy part
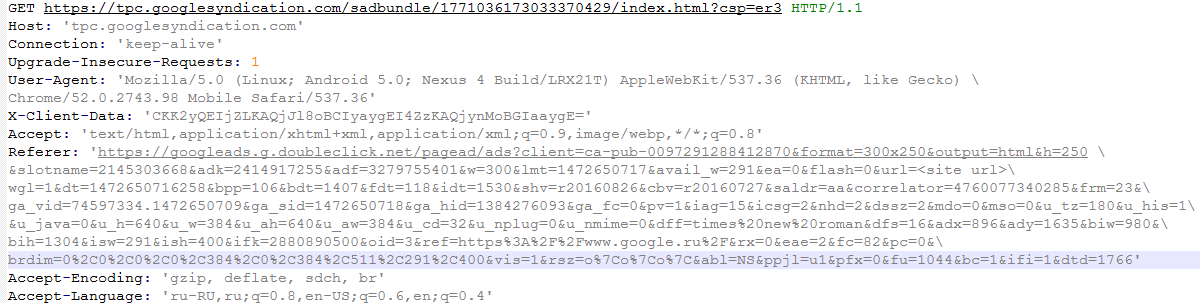
Let’s look at how the displaying of an ad is related to the automatic download of the APK file containing the Trojan and it being saved to the SD card. Below is the HTTP request that leads to the cybercriminals’ advert being displayed:
In response to this request, the server sends a Javascript script that displays the ad message. However, this script contains a hidden surprise: at the beginning there is some heavily obfuscated code. Let’s look, step by step, at what this code actually does:
- Declares the variables necessary for operation and deciphers the payload:
- Defines the function that will save the file.
- Breaks the decrypted APK file into blocks of 1024 bytes.
- Sets the handler for a page load event. Handler activation initiates the automatic saving of the APK file to the SD card.
We can see that the APK file was downloaded in the form of an encrypted array of bytes in the script. Now it just needs to be saved to the SD card.
The code checks the availability of functions from various browser engines, and if they are unavailable, defines its own function. The object URL and the element <a> (the latter being an HTML notation for a link) are created in this function. The resulting link is assigned the attribute ‘href’ (where the link leads to), and the malicious program emulates a click on this link. This method is not new; quite possibly the Trojan’s creators borrowed it from here, and only added obfuscation and a restriction: the click simulation is only done on touchscreen devices, which for the most part are smartphones.
Apart from the extra checks to see if the script runs on the smartphone or not, there is an important check in the code to identify the language used on the device. The attackers only target smartphones with a Russian-language interface – these are typically devices belonging to users in Russia and, to a lesser degree, CIS states.
Where’s the catch?
The method described above only works in Google Chrome for Android. When an APK file is downloaded via a link leading to an external web resource, the browser displays a warning that a potentially dangerous object is being downloaded, and prompts the user to choose whether or not to save the file.
When an APK file is broken down into pieces and handed over to the save function via Blob() class, there is no check for the type of the content being saved, so the browser saves the APK file without notifying the user.
We notified Google about this browser behavior and that it was being exploited to distribute malicious content. At the time of publishing a patch had been released that fixed this problem in Google Chrome and will become available to users the next time the browser is updated.
In all other browsers, this method either does not work, or the user is asked if they want to save the file or not. Kaspersky Lab recommends updating Google Chrome to prevent infection by the malware when viewing sites that use AdSense.
Conclusion
Of course, just downloading the Trojan is not enough for it to work; the user also has to install it. To ensure this, the attackers resort to social engineering. The Trojan may be downloaded with any of the following names:
- last-browser-update.apk
- WhatsApp.apk
- Google_Play.apk
- 2GIS.apk
- Viber.apk
- DrugVokrug.apk
- Instagram.apk
- VKontakte.apk
- minecraftPE.apk
- Skype.apk
- Android_3D_Accelerate.apk.
- SpeedBoosterAndr6.0.apk
- new-android-browser.apk
- AndroidHDSpeedUp.apk
- Android_update_6.apk
- WEB-HD-VIDEO-Player.apk
- Asphalt_7_Heat.apk
- CHEAT.apk
- Root_Uninstaller.apk
- Mobogenie.apk
- Chrome_update.apk
- Trial_Xtreme.apk
- Cut_the_Rope_2.apk
- Установка.apk
- Temple_Run.apk
These names imitate the names of popular legitimate apps or try to convince users that the downloaded app is important and has to be installed. In the latest versions of Android, installation of apps downloaded from unknown sources is blocked by default, but the cybercriminals are obviously counting on users disabling this setting to install an “important browser update” or a newer version of a popular app that is already on their phone.
So far, those behind Svpeng have limited their attacks to smartphone users in Russia. However, next time they push their “adverts” on AdSense they may well choose to attack users in other countries; we have seen similar cases in the past. After all, what could be more convenient than exploiting the most popular advertising platform to download their malicious creations to hundreds of thousands of mobile devices?
Disassembling a Mobile Trojan Attack






























Christopher
so that shuld google do so this staff don’t happens again?
JH Marchal
Good job guys!
Is this malware also related to this one: http://thehackernews.com/2016/11/chrome-android-virus.html ? because it just happened on my Android phone.
EK
yes, it is.