
In December 2014 we discovered a very interesting vulnerability in the Darwin kernel, which is an open source part of Apple’s two operating systems: OS X and iOS. As a result, OS X 10.10 and iOS 8 are also at risk. This vulnerability is connected with the processing of an IP packet that has a specific size and invalid IP options. As a result, remote attackers can cause DoS (denial of service) of a device with OS X 10.10 or iOS 8 installed. It means that attackers can send just one incorrect network packet to the victim and the victim’s system will crash.
OS X 10.10 crash after invalid network packet processing
Using vulnerability in the Darwin kernel attackers can cause DoS of a device with OS X 10.10 or iOS 8 installed
Tweet
While analyzing this vulnerability we’ve discovered that the following devices with 64-bit processors and iOS 8 installed are affected by this threat:
- iPhone 5s and later models
- iPad Air and later models
- iPad mini 2 and later models
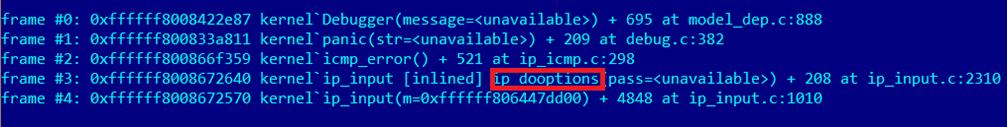
To understand the nature of this bug let’s look at a crash dump:
Kernel stack trace
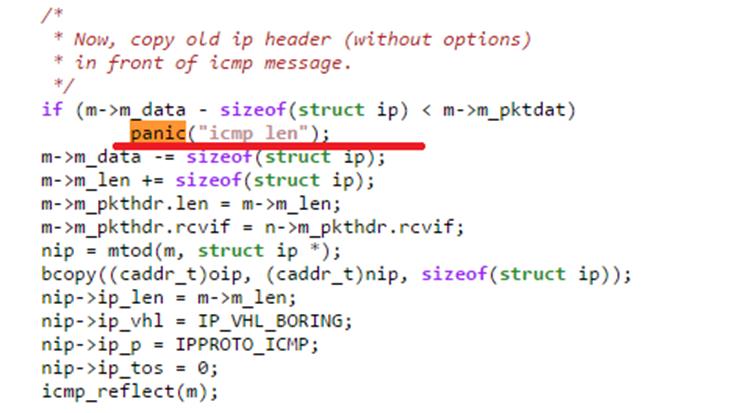
You can see from this trace that something went wrong in the icmp_error() function and it calls the panic function. This function tries to construct a new ICMP error message and resend it. This screenshot shows that the icmp_error was called after parsing packet options. The problem lies in this piece of code:
The cause of the problem
When the conditions laid down in the code are met, the panic function is engaged and the system is shut down in emergency mode. This happens because the internal kernel structures have been changed and the new buffer size is insufficient to store a newly-generated ICMP packet. To cause this, the IP packet must satisfy the following criteria:
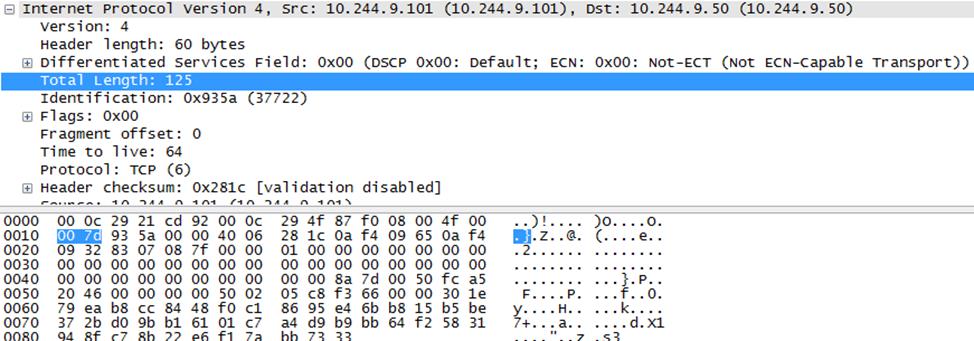
- The size of the IP header should be 60 bytes.
- The size of the IP payload should be at least 65 bytes
- There should be errors in the IP options (invalid size of option, class, etc.)
Example of packet that cause a crash
At first glance it is not obvious how this bug could be exploited effectively. However, a true professional can easily use it to break down a user’s device or even interrupt the work of a corporate network. Usually this kind of incorrect packet would be dropped by routers or firewalls but we discovered several combinations of incorrect IP options that can pass through the Internet routers.
This vulnerability no longer exists in OS X 10.10.3 and iOS 8.3. In addition, users of Kaspersky Lab’s products are secured against this vulnerability in OS X 10.10 by the Network Attack Blocker feature. Starting from Kaspersky Internet Security for Mac 15.0, this threat is detected as DoS.OSX.Yosemite.ICMP.Error.exploit.






















Darwin Nuke