
Continuing our investigation into Winnti, in this post we describe how the group tried to re-infect a certain gaming company and what malware they used. After discovering that the company-s servers were infected, we began to clean them up in conjunction with the company-s system administrator, removing malicious files from the corporate network. This took a while because it was not clear at first exactly how the cybercriminals had penetrated the corporate network; we couldn-t find a way to completely stop attacks penetrating the network and malicious files kept appearing. An analysis performed by the gaming company itself led us to the conclusion that the infection started after establishing working contacts with a South Korean gaming company. This was also confirmed by our research: as we wrote before, the Winnti group is most active in East Asia and we identified 14 infected gaming companies in South Korea.
In the course of our efforts to remove the infection, the gaming company sent us suspicious files that were appearing on their computers. Many of these files were samples of Winnti malware. As soon as information about the malicious files was added to our antivirus databases, our products were used to remove Winnti malware from the gaming company-s corporate network. However, the attackers reacted very rapidly: new malware samples mysteriously appeared on computers from which the infection had been completely removed the previous day. Eventually, though, our efforts proved successful and further access to the gaming company-s computers was denied to the attackers.
However, just as we expected, it was too early to celebrate. Exactly one month after the gaming company-s network had been cleaned, the Winnti group returned. The system administrator sent us suspicious files, which had been attached to messages sent to company employees. This was run-of-the-mill spearphishing: the attackers introduced themselves as computer game developers and pretended to be looking for opportunities related to working with large publishers.
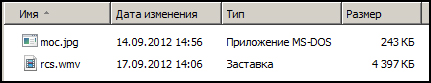
The messages were written sloppily, with numerous mistakes, showing that their authors did not have a very good command of English. This was particularly ludicrous in a message supposedly sent by a budding gaming company from Los Angeles. There were RAR archives attached to the messages. The archives contained executable files whose extensions had been hidden using a well-known technique for reversing text with the help of the 0x202e special character. As a result, the executables vmw.scr and gpj.com were displayed in the Windows Explorer as rcs.wmv and moc.jpg, as if these were a video file and a jpeg image.
The Far file manager displays the file names correctly, with the 0x202e special character shown at the beginning of the file names as a question mark.
The attackers- idea was that an employee receiving one of these messages would unpack the attached archive, see an image or a video contained in it and open the file without thinking. The executables would be launched, resulting in an infection.
Those executable files proved to be malicious. To our surprise, the malware was from the PlugX family, which was already familiar to us. It was bizarre to see a malware family which had previously been detected in attacks targeting political activists and government organizations being used in attacks on gaming companies. During our analysis, we found no data indicating that PlugX had been used by several different cybercriminal groups. Naturally, this leads us to a question: could it be possible that the Winnti group was behind both the attacks on gaming companies and those targeting, e.g., Tibetan activists?! Given the amount of work the attacks on gaming companies clearly require, one might well ask: how do these attackers find the time? For a long time, while studying the PlugX family, we were unable to find any connections between the PlugX samples distributed by the Winnti group and the PlugX samples used in attacks against non-gaming targets. However, later it became clear that the Winnti group, even if it was not behind the PlugX attacks on non-gaming companies, was definitely connected to another group (or other groups) involved in such attacks.
By analyzing the message subjects v and keeping in mind that the company had been attacked a short while before v we concluded that this was a targeted attack and that the Winnti group had decided to penetrate the company-s network again. The system administrators switched to an emergency operating mode to keep malware from penetrating the network. After that, the attacks came one after the other. This demonstrated the very essence of the Winnti group: initially, they did not bother to organize sophisticated attacks; they only switched to a more complicated approach after running into resistance, trying to minimize their efforts every time. After the initial attack the cybercriminals began to send 7z, lzh and tbz archives containing self-extracting Rar and 7zip archives with PlugX inside, under the following names:
v Company Profile.7z, containing a self-extracting RAR archived named 2013plan.exe with a file called 11.EXE inside, which in turn contained a CAB archive with PlugX components. In addition, a short fragment of a porn video was found in the resources of 11.EXE;
v MyPhotos.7z, containing photos and the file myphotos\myphotos.exe;
v Resume.7z, containing Resume.exe;
v Documents.7z, containing My Documents.exe;
v Programm.7z, containing Programm.exe;
v _____.lzh, containing Desktop.exe;
v Desktops.7z, containing FreeWord.doc and a self-extracting RAR archive named Documents.exe. FreeWord.doc actually was not MS Word document but the following JPEG image:
v 21. Dezember 2012.tbz, which contained a document named 21. Dezember 2012.doc and Dezember.exe;
v Game Creative Board.pdf.7z, which contained the documents Game Creative Board.pdf, Game Creative Board 1.pdf and Game Creative Board 2.pdf, which were actually Microsoft Word documents, and the file Game Creative Board.exe;
v Work.7z, containing My work.exe and Work.exe;
v My work.rar, containing My doc.exe and My ppt.exe;
The attacks were so intensive that the system administrators had to resort to extreme measures and block message attachments from being sent to corporate mailboxes. The attackers responded in a very straightforward way: they sent messages to the company-s employees, explaining v quite correctly v that their attachments were not making it to the recipients- mailboxes and asking the recipients to follow a link provided in the message, download an archive and open it. The archive with malicious contents was located on the compromised site www.linfairrecords.com. But this was a one-off attempt: the attackers changed their tactics and no more messages like this were received.
For the first time since launching the campaign to re-infect the network, the attackers decided to make an effort and come up with something slightly unusual. They sent messages to the personal inboxes of the company-s employees on behalf of other employees. To make the messages more convincing, they included the photos of those employees on whose behalf they were sending the messages. Naturally, the attachments contained the same PlugX payload. However, the staff had been warned about the on-going attacks against the company and this trick did not go unnoticed. It should be noted that the gaming company being attacked is not located in an English-speaking country, so its employees are not native speakers of English. In this situation, it would have looked strange if employees had started sending each other emails in English. The attackers realized this, so the messages were written in the recipients- native language. The initial versions of the emails were poorly written, clearly showing that the authors were not writing in their own language. Later, the cybercriminals improved the text so that it looked halfway decent.
These attacks continued on a regular basis for nearly three months. Although most of these spearphishing attacks were not too sophisticated and convincing (these emails would make any competent person suspicious), when dealing with large numbers of people (the company does have a large staff), even highly improbable events can happen: one of the company-s employees didn-t notice anything wrong with one of these messages and launched the malicious program attached to it. However, we processed, analyzed and tracked all of the malware sent in these emails. Consequently, we knew the control centers used for the malware which was sent. So when a backdoor on the employee-s infected computer attempted to connect to its control server, the system administrators detected this and the infected computer was promptly identified and isolated from the corporate network.
As a result of these efforts, the attacks came to an end. On the one hand, this is good news, but on the other v the cybercriminals stopped attacking via emails, but have they discontinued all attempts to penetrate the company-s network at all? They might well be considering more reliable infection vectors. While the situation with the emails was clear, it should now be kept in mind that the attackers may resort to completely new methods. It is unclear where any new attacks may come from v so extra care and vigilance is needed.
Here we will clarify the issue: was it the Winnti group who organized the second wave of attacks attempting to infect networks with PlugX? There might be another team, completely separate from Winnti, targeting the game company we cooperated with. However, there are a few factors that suggest this is unlikely.
1. The interval between attacks: the perpetrators started sending emails with PlugX attached exactly a month after access to the corporate network was blocked. The same thing happened with another game company: almost exactly a month after Winnti malware was removed, its computers were infected again. It seems that after the Winnti presence is detected and the corporate network is cleaned of the malware, the Winnti group leaves the target for a month.
2. The perpetrators distributed PlugX messages to employees- personal addresses, claiming to come from fellow members of staff. The letters contained photos of alleged senders. Along with the photos, all the information about personal mailboxes could have been collected during the group-s initial presence on corporate workstations.
3. We discovered PlugX samples signed with certificates stolen from two different game companies: MGAME and ESTsoft, both are from South Korea and deal with the computer game industry.
4. Besides, ESTsoft is a producer and developer of the MMORPG ?CABAL Online¦. Here at Kaspersky Lab we regularly receive KSN notifications about Winnti samples discovered in CABAL distributives. Several names of CABAL Online-s regional ESTsoft partners are seen in Winnti malware tags, describing its target.
5. We discovered the following ?live¦ third-level domains in Winnti control center zones:
est.gasoft.us
est.gcgame.info
est.zzsoft.info
We have already written the Winnti team repeatedly created third-level control center domains, so that the sub-domain name is correlated with the name of an infected company. That suggests that the domains mentioned above are likely to have been created to manage ESTsoft-s infected computers.
6. While studying the PlugX family, the following control centers were defined in a PlugX sample:
bot.jgame.in
bot.dongevil.info
udp.jjevil.com
The domain name jgame.in obviously has something in common with game themes. A lot of Winnti domains were registered with the address evilsex@gmail.com. Another two domains dongevil.info and jjevil.com might be registered by the same person v someone who clearly likes using ?evil¦ in names.
7. Another sample that was discovered contained information about the following control centers:
bot.xiaotian123.com
kr.jjevil.com
jj.nexon-nss.com
Obviously, the domain jjevil.com is linked to nexon-nss.com. And we know about these Winnti control centers:
nexoncorp.us
nexongame.net
nexononline.com
NEXON Corporation is a gaming company; we already explained that the Winnti group likes to name their control center domains according to the domains of the game companies- websites. Moreover, the name of NEXON was found in the target tags of several Winnti samples.
8. PlugX control center zones
dongevil.info
jjevil.com
are registered with the email address huise123@yahoo.com. The same address is used for the domain
ibmsupport.net
But there is another Winnti control center
ibm-support.net
registered with whoismydns@gmail.com. There is a certain likeness:
ibmsupport.net ibm-support.net
huise123@yahoo.com whoismydns@gmail.com (on the basis of whois)
9. The other day, when this article was being prepared for publication, we discovered a PlugX sample containing these control centers:
tank.hja63.com
tho.pad62.com
These zones were the location of the domains that connected to the Winnti backdoors found in a gaming company-s computers:
tank.hja63.com (complete match with the PlugX control center)
soft.hja63.com
ru.pad62.com
Both domains v hja63.com and pad62.com v were registered with one and the same email address v huisengaunr@sina.com.
And putting all that into a diagram:
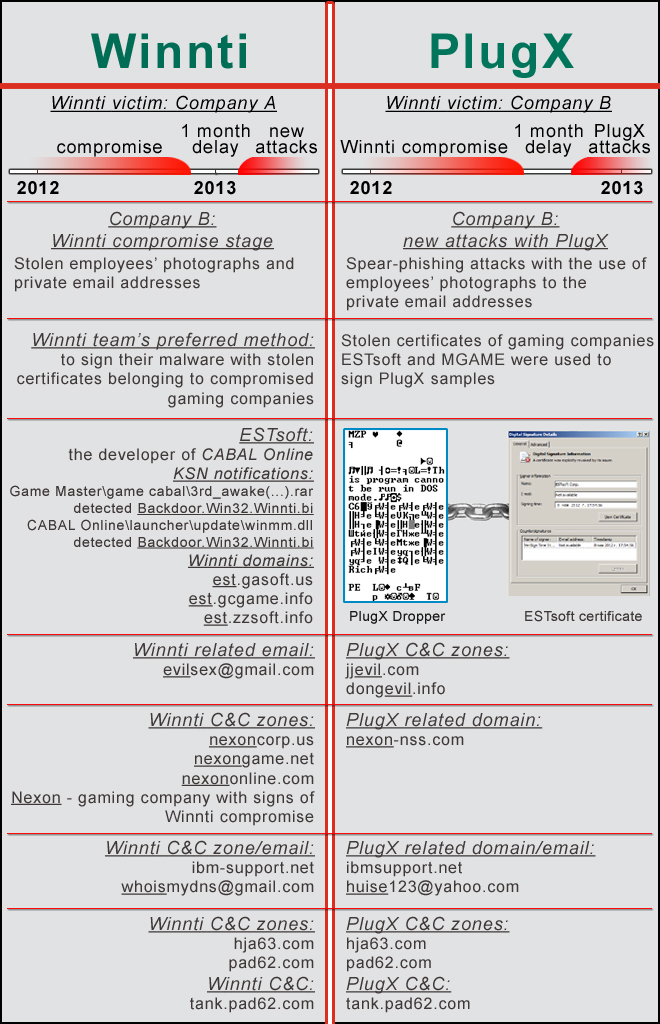 Winnti and PlugX correlation
Winnti and PlugX correlation
This data means we can be certain that it was the Winnti group that attacked the game company with PlugX messages. It was trying to return a month after they were denied access to the corporate computers. Besides, the compilation date of the major functional component of the PlugX sample (which contained domains in the zones which apply both to PlugX and Winnti) is May 21, 2012, meaning the Winnti group has been using the PlugX remote administration tool since at least May 2012. Among all the pieces of PlugX malware that we discovered, the compilation dates of earlier PlugX samples v which we believe were distributed by Winnti team members v are from the beginning of May 2012. Yet it remains unclear whether there is a single organization, combining the Winnti group which targets gaming companies and those who have used PlugX against political and governmental targets. We believe they are somehow connected.
Perhaps some group members have worked on both projects; some may work in one group and then move to another, bringing their experience and material v this may also explain the intersection.
As we have already pointed out in our full report about Winnti, searching for traces left by one of the group members on the Internet, we stumbled upon a job offer posted on a Chinese hacker forum. Here-s a rough translation of the offer:
Subject: Looking for information security researcher
From: Southland sword
Time: 2012-04-06 00:38
Subject: Security researcher job
Responsibilities:
1. Full target penetration alone or with a team depending on available resources;
2. Penetration testing report and recommendations
Technical requirements:
1. Knowledge of penetration testing, methods, processes, proficiency in a variety of penetration testing tools;
2. Knowledge of common Web development languages (asp, php, jsp), experience with SQL-injection, XSS, common websecurity exploits and patches;
3. Experience with all kinds of operating systems and databases for common security vulnerabilities;
4. Good verbal and written language skills;
5. Be able to work in a team; individuals who lose trust, do not listen to the teamleader and not accepting the rules will be kicked out;
Work Location: Guangdong (OR Guangzhou Shenzhen)
Baochibaozhu package, Relatively free playing time.
Salary: monthly allocation of the total amount of work and cooperation share more than 1W.
Vacancies: 5 people
For candidates: first contact me (preferably work resume), after my check the resume will be passed to the head coordinator for arranging a personal meeting.
Salary: free meal and apartments, office location is in a senior villa suite of 200 square meters, computers are available but please bring your own hard drive with environment and tools you are familiar with. Even a single completed project will provide you with money for your monthly expenses.
Powerful background. No comments!
Those who are competent, please contact:
Email: Infosec@cntv.cn QQ: admin@inessus.com
And a Winnti group member, who was a regular on that forum, replied:
?Aren-t you recruiting people for APT? Guangzhou is too far, but anyway I support it.¦
There were also some interesting comments in the forum thread regarding the reference to ?Powerful background¦ in the job offer. Some people in the thread speculated that it might mean the work is supported by the government.
It is obvious that the targeted attacks business is booming in China. There-s little doubt that there-s some form of cooperation between some gangs such as sharing information and tools, and even group members. Ordinary employees probably migrate from one criminal group or organization to another. It is clearly a challenging situation, and is only likely to improve with the political will and the intervention of law enforcement agencies.

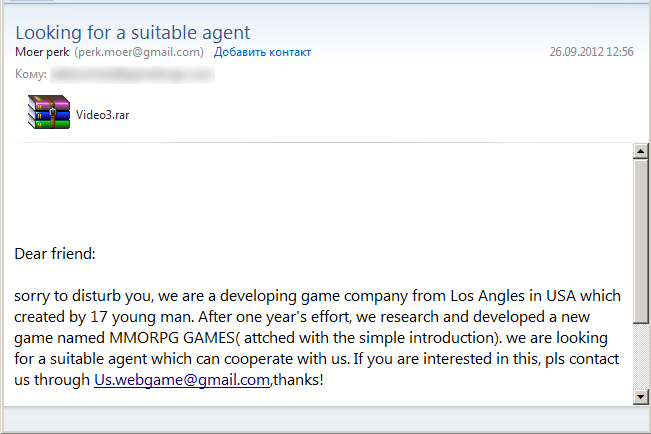
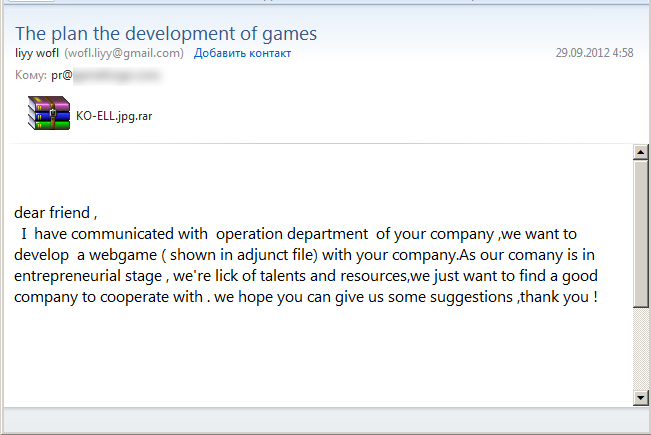




















Winnti returns with PlugX