
Part 1: Dangerous trends
Since June 2015, we have seen a steady growth in the number of mobile malware attacks that use superuser privileges (root access) on the device to achieve their goals.
Root access is incompatible with the operating system’s security model because it violates the principle that applications should be isolated from each other and from the system. It gives an application using root access a virtually unlimited control of the device, which is completely unacceptable in the case of a malicious application.
Malicious use of superuser privileges is not new in itself: in regions where smartphones are sold with privilege escalation tools preinstalled on them, malware writers have long been using this technique. There are also known cases of Trojans gaining such privileges after the user ‘rooted’ the device, i.e. used vulnerabilities to install applications that give superuser privileges on the phone.
However, the malware described in this post gains root privileges on its own, with the device owner having no idea that there is an application with superuser rights on the phone.
How it works
We analyzed the statistics we had collected from May to August 2015 and identified three main Trojan families that use root privileges without the user’s knowledge: Trojan.AndroidOS.Ztorg, Trojan-Dropper.AndroidOS.Gorpo (which operates in conjunction with Trojan.AndroidOS.Fadeb) and Trojan-Downloader.AndroidOS.Leech. All these mobile malware families can install programs; their functionality is in effect limited to providing the capability to download and install any applications on the phone without the user’s knowledge.
A distinctive feature of these mobile Trojans is that they are packages built into legitimate applications but not in any way connected with these applications’ original purpose. Cybercriminals simply take popular legit apps and add malicious code without affecting the main functionality.
After launching, the Trojan attempts to exploit Android OS vulnerabilities known to it one after another in order to gain superuser privileges. In case of success, a standalone version of the malware is installed in the system application folder (/system/app). It regularly connects to the cybercriminals’ server, waiting for commands to download and install other applications. Since subsequent behavior of the malware varies by family, we discuss each of the families separately below.
Fadeb and Gorpo families
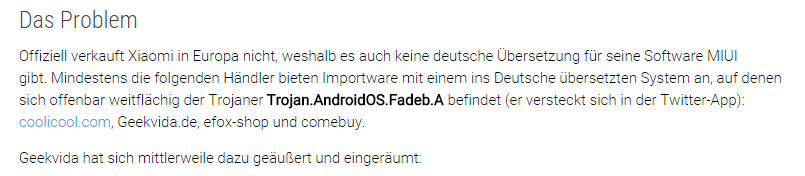
It should first be explained why we say that these two families work in conjunction with each other. An analysis of their code has shown that both malicious programs are based on the same framework, with identical methods for hiding strings used in their code. Functionally, Trojan.AndroidOS.Fadeb is responsible for downloading and installing files, while Trojan-Dropper.AndroidOS.Gorpo obtains escalated privileges on the device and then installs Fadeb in /system/app under the name LauncherXXXX.apk. Older versions of Trojan.AndroidOS.Fadeb worked on a ‘standalone’ basis and depended on the su file, installed either by the manufacturer or by the user, being present on the device.
Trojans from these two families are found on inexpensive smartphones – as packages built into popular applications, such as Twitter, Facebook, various launchers, etc. An analysis of infected devices’ firmware has shown that applications that include malicious code are not supplied by the phone manufacturer. The users themselves did not install these applications in standard ways, either. We believe that these applications may have been installed by third parties before the devices reached the users. These could be small private shops that try to install as many applications on devices as possible to make customers happy but use unsafe software sources without performing any security scans of the files they download.
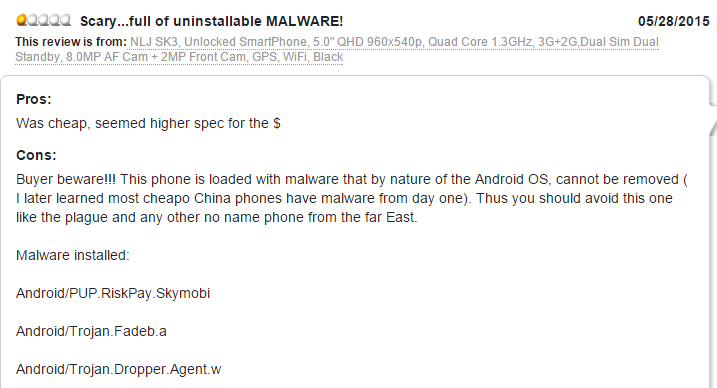
We came up with this theory after studying various websites and user forums where users described cases of devices being infected without their knowledge and Trojans being found on newly-purchased devices.
Source: https://www.androidpit.de/xiaomi-mi4-smartphones-werden-teils-mit-trojaner-ausgeliefert
Source: http://www.newegg.com/Product/SingleProductReview.aspx?ReviewID=4337361
Source: http://www.amazon.com/Lenovo-Screen-Android-Qualcomm-Snapdragon/product-reviews/B00SUWBROI
The list of infection sources does not end there: sometimes users themselves downloaded these Trojans from unofficial app stores. According to our statistics, the most popular infected applications were:
- com.leo.appmaster
- cn.cleanmaster.mguard
- com.apusapps.launcher
- cc.taosha.beautify.easylocker
- cc.taosha.toolbox.shareit
- com.twiter.android
- com.freevideo.entertainment.youtube
- com.star.android.smartTouch
- com.top.sex.positions.real.sounds
Leech family
This malware family is the most advanced of those described in this post: some of its versions can bypass dynamic checks performed by Google before applications can appear in the official Google Play Store. Malware from this family can obtain (based on device IP address, using a resource called ipinfo.io) a range of data, including country of registration, address, and domain names matching the IP address. Next, the Trojan checks whether the IP address is in the IP ranges used by Google:
- 216.58.192.0 – 216.58.223.255
- 209.85.128.0 – 209.85.255.255
- 104.132.0.0 – 104.135.255.255
- 173.194.0.0 – 173.194.255.255
- 74.125.0.0 – 74.125.255.255
If the IP address is in one of the above ranges, the malware terminates.
The domain names matching the device’s IP address were also checked for the presence of the following strings: “android”, “google” and “1e100” (a service used by Google internally; its name is the mathematical formula for the number googol). In this way, the Trojan checks whether the infected device is on Google’s corporate network. This is necessary in order to pass the dynamic tests required before an application can be made available in Google Play app store. When Leech detects that it is on the Google network, this means that it is undergoing a check of this kind, so it terminates.
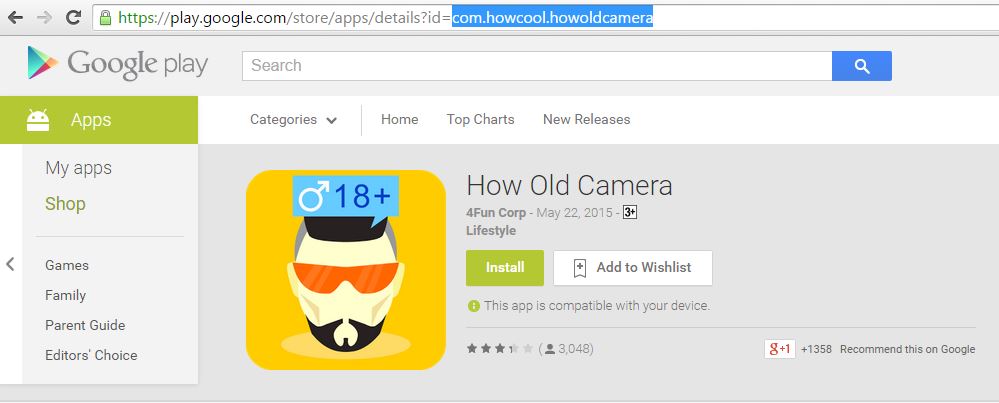
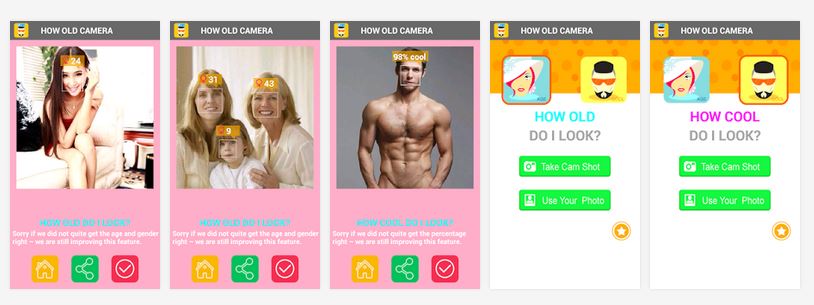
The malware also uses a dynamic code loading technique, which involves downloading all critically important modules and loading them into its context at run time. This makes static analysis of the application difficult. As a result of using all the techniques described above, the Trojan made it to the official Google Play app store as part of an application named “How Old Camera” – a service that attempts to guess people’s ages from their photos.
As we can see, the app appeared on May 22, 2015, at the peak of popularity enjoyed by a similar Microsoft service. At the time it was removed from Google Play (June 10, 2015), its number of registered installations was in the range from 100,000 to 500,000, which is a lot, particularly in view of the danger posed by the app. A package with the Trojan was also embedded in other popular legitimate applications, such as apps for downloading videos from YouTube or for installing live wallpapers.
After successfully gaining superuser privileges, Leech installs another application to /system/app folder, in addition to its own standalone version. It is an app named “com.sync.sms”, which is detected by Kaspersky Lab products as Trojan.AndroidOS.Guerilla.a. This Trojan carries out aggressive advertising campaigns for other applications. The campaigns include displaying advertising in the status bar, in third-party applications, as well as downloading and installing applications (including the ability to download apps from Google Play) and displaying any interactive elements on the device’s screen.
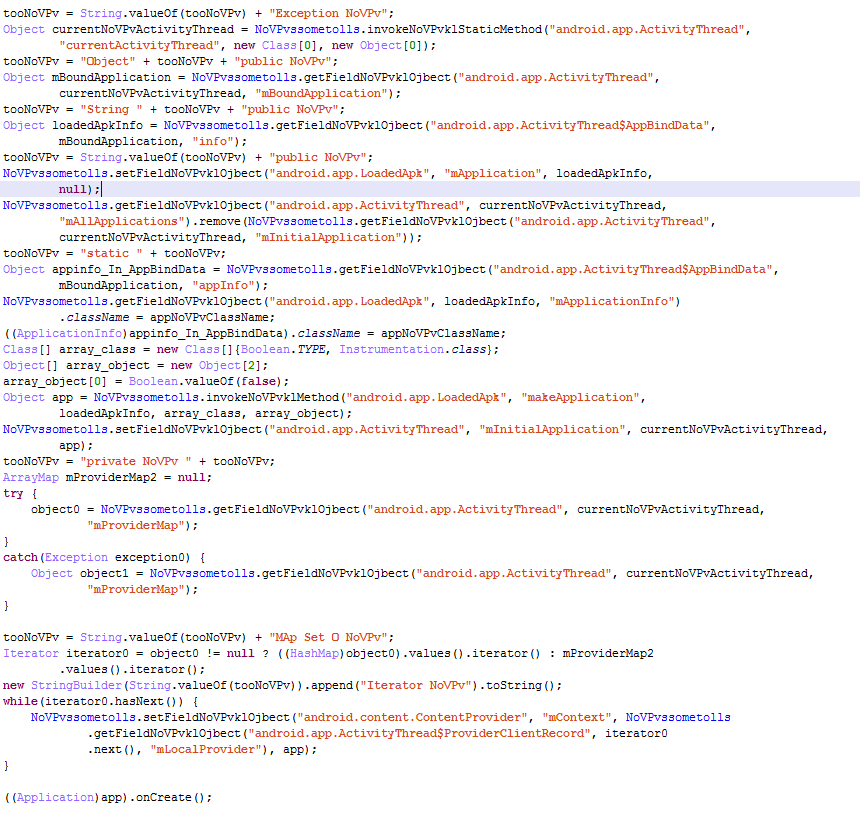
Interactive elements displayed by Trojan.AndroidOS.Guerilla.a
The Guerilla Trojan can also inject its code into system applications in device memory in order to ensure that it will keep getting launched.
Below is a list of applications advertised by the Guerilla Trojan:
- com.duotui.home
- com.mobile.indiapp
- com.polaris.newnews
- com.uf.lockscreen
- gamedangian.tienlenmiennam.gamebai
- com.flipkart.android
- com.truecaller
- com.chaatz
- com.eterno
- com.machinezone.gow
- com.moonton.magicrush
- com.zqkt.hezuobao1
- com.batterysaverplus
- com.heisha.candy150706
- com.lazada.android
- com.mfree.mp3.music
- com.mm.artifact
- com.mzve.mstc.yxjz
- com.qihoo.security
- com.schibsted.bomnegocio.androidApp
- com.uf.flashlight
- com.baidu.androidstore
- com.dianxinos.dxbs
- com.dianxinos.optimizer.duplay
- com.estrongs.android.pop
- com.ijinshan.kbatterydoctor_en
- com.quikr
- com.star.android.smartTouch
- com.weixin.gzsj
- com.wifi.free.superfast
- com.baidu.browser.inter
- com.cleanmaster.mguard
- com.looku.bee2
- com.specialapps.SecretBox
- com.voonik.android
- com.applockv43o003.amb
- com.apusapps.launcher
- com.coconuttec.teenpatti.klub
- com.cool.coolbrowser
- com.dragon.android.mobomarket
- com.hcg.cok.gp
- com.igg.castleclash_fr
- com.leo.appmaster
- com.uc.browser.en
- com.fission.sevennujoom
- com.then.dayx.hgwe
- com.wifimap.mapwifi
- net.lovoo.android
Leech provides access to infected devices not only to Guerilla but to much more dangerous malware, as well. This is why we have decided to write a separate article about this malicious program, in which we are going to describe both this remarkable Trojan and its derivatives.
Ztorg family
On the whole, Trojans belonging to this family have the same functionality as the families described above. The distribution techniques used also match those employed to spread Trojans from the Gorpo (plus Fadeb) and Leech families – malicious code packages are embedded in legitimate applications. The only significant difference is that the latest versions of this malware use a protection technique that enables them to completely hide code from static analysis. The attackers use a protector that replaces the application’s executable file with a stub, decrypting the original executable file and loading it into the process’s address space when the application is launched. Additionally, string obfuscation is used to make the task of analyzing these files, which is quite complicated as it is, even more difficult.
Ztorg versions that do not use this kind of protection are detected by Kaspersky Lab products as Trojan.AndroidOS.Ztorg.a and versions with protection are detected as Trojan.AndroidOS.Ztorg.b.
Statistics
Data on the activity of the families described above is provided below. Diagrams on the left-hand side are graphs showing the number of newly attacked users over time and the right-hand images are geographical distribution maps.
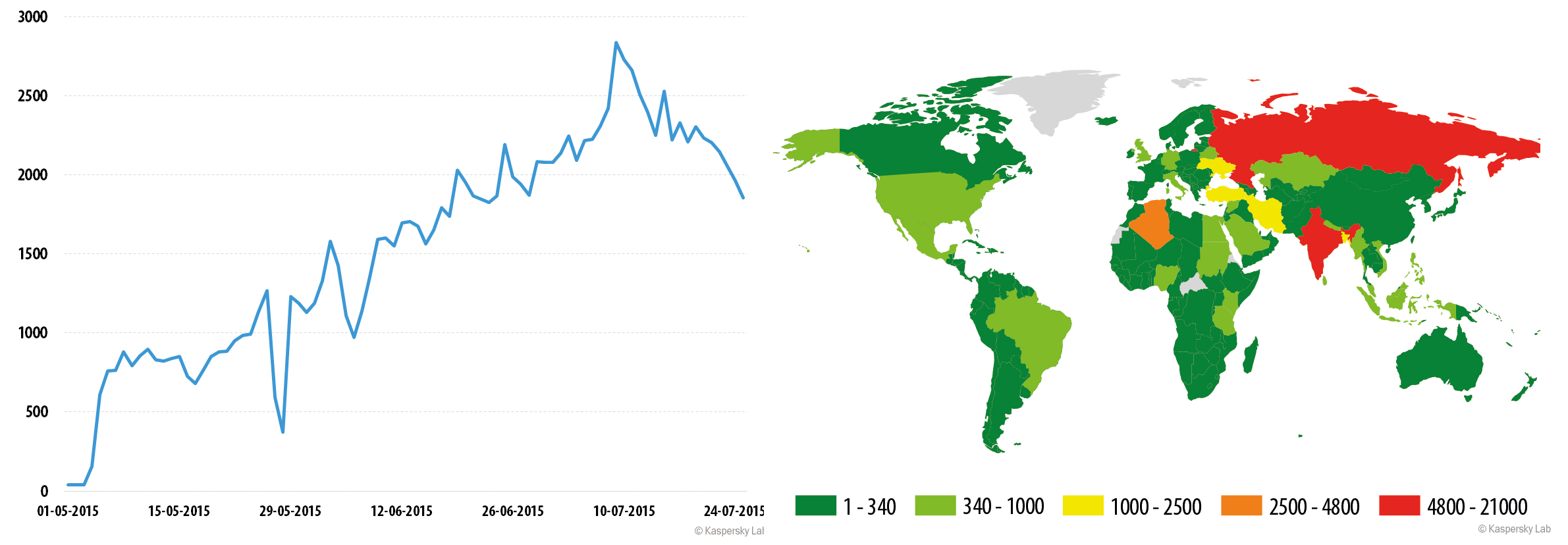
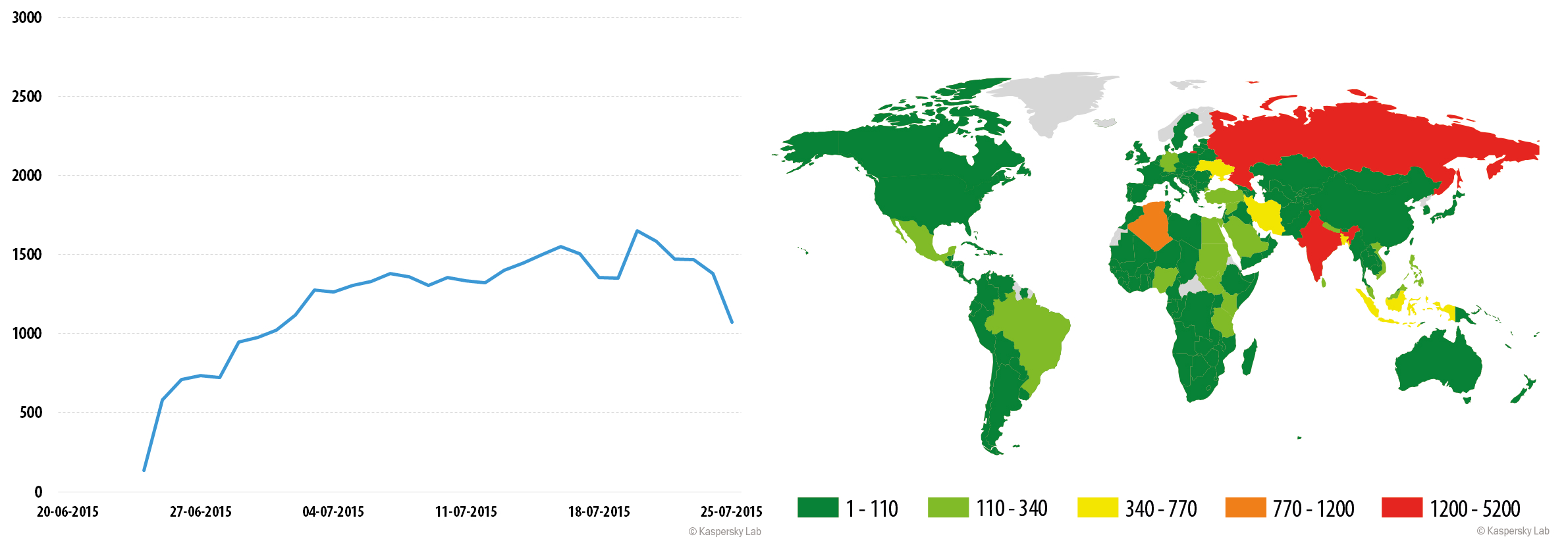
Trojan-Downloader.AndroidOS.Leech.a
The largest number of infection attempts for the Leech Trojan was recorded in the first half of July, with about 33 thousand users attacked over the two-week period. Attacks peaked on July 9 – over 2,800 potential victims.
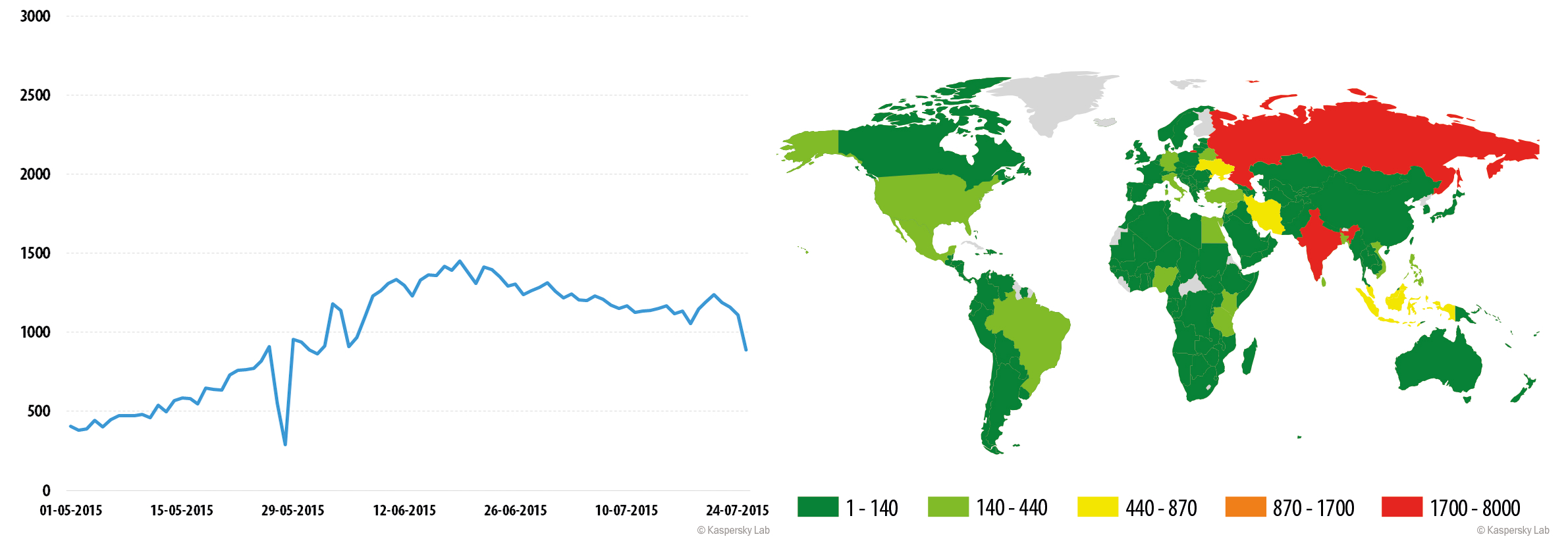
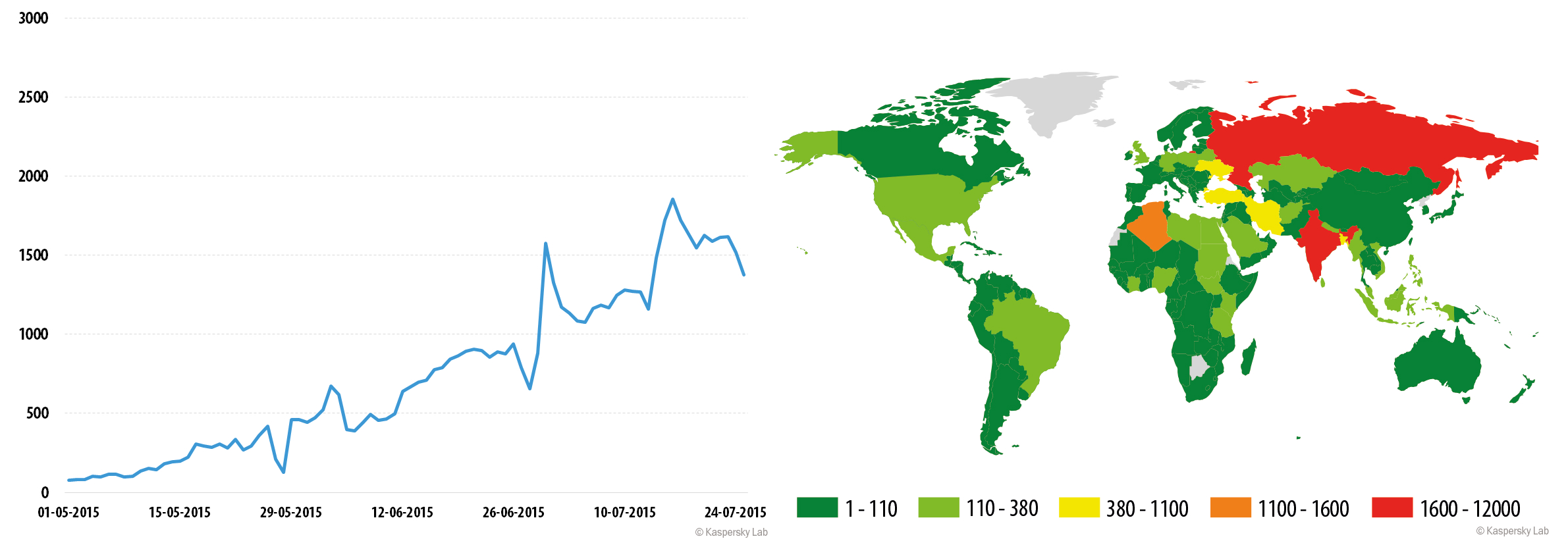
Trojan.AndroidOS.Ztorg.a
Trojan.AndroidOS.Ztorg.b
Trojan.AndroidOS.Ztorg.a was quite active in July – an average of more than 1200 users attacked per day. Around the middle of July, its popularity sharply declined, as the malware was replaced with its new modification –Trojan.AndroidOS.Ztorg.b. The Trojan’s protected version was more active and attacked about 1300 users daily in July.
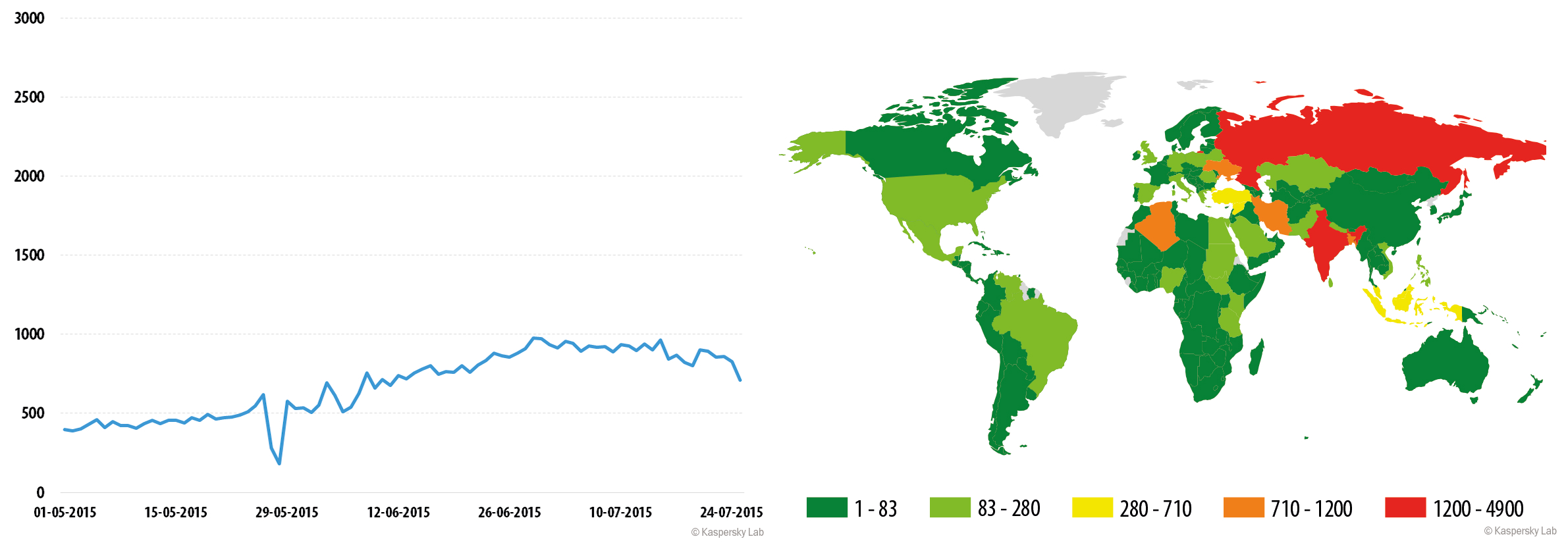
Trojan-Dropper.AndroidOS.Gorpo.a
The activity of Trojan-Dropper.AndroidOS.Gorpo.a rose gradually, starting in early May 2015. However, we recorded two surges – on June 30 and July 16. On these days, the number of users attacked exceeded 1500 and 1800, respectively.
Trojan.AndroidOS.Fadeb.a
Trojan.AndroidOS.Fadeb.a could be regarded as the least successful of the malicious programs described above. Its activity also increased starting in early May, but even in the first half of July, which was its most active period, the number of users attacked did not exceed 1,000 per day.
The majority of users attacked by the Trojans were located in Russia and India, as well as countries of the Middle East. However, tens and even hundreds of infections were recorded in other regions, too.
Conclusion
It is not very common for malicious applications to be able to gain superuser privileges on their own. Such techniques have mainly been used in sophisticated malware designed for targeted attacks. The cases described in this post show that these techniques are becoming more mainstream: run-of-the mill malware increasingly uses similar (if not more advanced) techniques. This creates a dangerous trend. Although the Trojans described above are mostly used for advertising purposes, nothing would prevent them from using their newly-gained superuser privileges to install applications that can do users much more harm than just irritation caused by annoying advertising.
Taking root

























Sunil Kr Singh
Can root targetting malware control my android even if i dont give root acccess to them ???