
I’m sure regular readers of this blog remember the story of GpCode, which used RSA algorithms to encrypt user data. ‘Blackmailer‘ article covered this malicious program in detail.
Some of you may have been wondering why we haven’t blogged about any similar programs recently – after all, ‘Blackmailer’ concluded with the idea that we were likely to see more of these programs in the future. But there’s been a curious lull of more than a year…
So you can imagine our feelings this weekend, when some of our non-Russian users told us their documents, photos, archive files etc had turned into a bunch of junk data, and a file called read_me.txt had appeared on their systems. Sadly, the contents of this file were all too familiar:
(http://en.wikipedia.org/wiki/RSA).
You will need at least few years to decrypt these files without our
software. All your private information for last 3 months were
collected and sent to us.
To decrypt your files you need to buy our software. The price is $300.
To buy our software please contact us at: xxxxxxx@xxxxx.com and provide us
your personal code -xxxxxxxxx. After successful purchase we will send
your decrypting tool, and your private information will be deleted
from our system.
If you will not contact us until 07/15/2007 your private information
will be shared and you will lost all your data.
Glamorous team
Does this signal the return of the unknown shake-down artist? This text is clearly not written by a native speaker of English. And the email address is one that we’ve seen before in LdPinch and Banker variants, programs which were clearly of Russian origin.
Of course, we’ve analyzed the files, and in spite of the text above, there’s no sign of RSA-4096. Interestingly, this nasty little piece of work, which we detect as Virus.Win32.Gpcode.ai, has a very limited shelf life, from 10th to 15th July 2007. Why? We can only guess.
Kaspersky Anti-Virus 6.0 detects this Trojan proactively – once as Trojan-Generic and once as Invader:
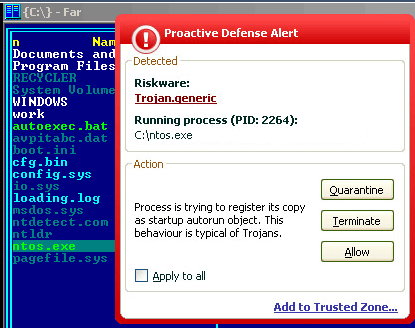
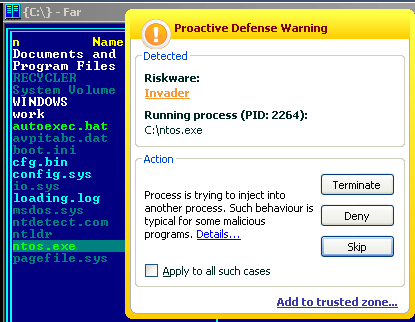
Of course, we’re also working on a decryption routine for encrypted user files to add to our antivirus databases.
But in the meantime, we’d just like to remind you – if you’ve fallen victim to Gpcode or any other type of ransomware, you should never pay up under any circumstances. Always contact your antivirus provider and make sure you back up your data on a regular basis.






















Blackmailer – the return of Gpcode