
The shopping event of the year, Black Friday, is almost here, and while the big day does not officially arrive until Friday, November 25th, deals are already starting. The day kickstarts the frenzied holiday shopping season with eye-catching promotional deals that lure shoppers into spending more of their hard-earned cash. In the weeks leading up to Black Friday, we have already seen discounts reaching 70% and even 80%, grabbing the attention of millions of customers.
Today, e-commerce sales make up 21% of global retail sales, which is a 50% increase on the pre-pandemic levels. Besides, 94% of shoppers now do at least some of their shopping online. As the volume of purchases around Black Friday increases, the attention of cybercriminals to e-commerce intensifies proportionally. The risk of being scammed runs even higher. While on ordinary days, the customer can easily see that if the product is too cheap, it is most likely a scam, during the Black Friday sales, it gets harder to tell. Shoppers become less vigilant, and therefore, an easy target for cybercriminals. That is why we constantly monitor the landscape of shopping-related cyberthreats and protect users from these risks. Here is what we have found this year.
Methodology
In this research, we analyze various types of threats, such as financial malware and phishing pages mimicking the world’s biggest retail platforms, banking and payment systems, and discuss recent trends. The threat statistics we use come from Kaspersky Security Network (KSN), a system for processing anonymized cyberthreat-related data shared voluntarily by Kaspersky users, for the period from January through October 2022. In addition, we analyzed Black Friday-related spam and phishing pages mimicking popular BNPL (buy now, pay later) services, which have proven to be particularly popular during shopping seasons like Black Friday.
Key findings
- Over the first ten months of 2022, Kaspersky prevented 38,596,555 financial phishing attacks.
- In 2022, the number of attacks using banking Trojans doubled when compared to the same period of 2021, reaching almost 20 million.
- The number of financial phishing attempts for online shopping platforms (16,424,303) comprised 42.55% of all financial phishing attempts.
- The number of phishing pages mimicking the most popular shopping platforms (Apple, Amazon, eBay, Walmart, Aliexpress, and Mercado Libre) totaled 12,787,534 in the first ten months of 2022.
- Apple was consistently the most popular lure among online shopping platforms, with phishing attempts using its name reaching 9,858,254 in the first ten months of 2022.
- Spam campaigns intensify as Black Friday approaches. In the first three weeks of November, Kaspersky telemetry spotted 351,800 spam emails that contained the word combination “Black Friday”. This is five times more than September’s figure.
Phishing for shopping credentials: financial threats in numbers
One of the prime threats during the shopping season is financial phishing. Kaspersky distinguishes several types of financial phishing: banking, payment system, and online store phishing. Banking phishing includes fake banking websites that cybercriminals create to mislead their victims into giving up their credentials and card details. Payment system phishing involves pages mimicking well-known payment systems, such as PayPal, Visa, MasterCard and American Express. The third type of phishing mimics online stores, such as Amazon, eBay, Aliexpress, or smaller ones.
Number of attempts to visit phishing pages using banking, online payment and online retail brands as a lure, January–October 2022 (download)
During the first ten months of 2022, Kaspersky products detected 38,596,555 phishing attacks targeting users of online shopping platforms, payment systems and banking institutions. We count one attempt to open a phishing link detected by Kaspersky as one phishing attack. During the first ten months of this year, the number of financial phishing attempts for online shopping platforms comprised 42.55% of all financial phishing attempts, which is 10.19 p.p. higher than the share of online payment phishing (32.36%), and 17.47 p.p. higher than the share of banking phishing (25.08%). Moreover, some of the payment system and banking phishing cases may be related to online store phishing. For example, if a phishing or scam page mimicking Amazon redirects the user to a payment page mimicking PayPal, these two pages will be categorized as online store and payment system phishing, respectively. In total, Kaspersky solutions detected 16,424,303 online store phishing attacks, 12,491,239 online payment phishing attacks, and 9,681,013 banking phishing attempts. We also observed a sharp spike in the number of attacks on online store users in June–July 2022. This was caused by a massive phishing campaign involving a fake Apple device giveaway, which Kaspersky security solutions successfully repelled.
Number of attempts to visit phishing pages using Apple as a lure, January–October 2022 (download)
Overall, the number of phishing attacks mimicking the most popular shopping platforms (Apple, Amazon, eBay, Walmart, Aliexpress, and Mercado Libre) amounted to 12,787,534 for the ten months of 2022. The majority of these attacks targeted Apple users: 9,858,254 phishing attempts, most of them occurring during the summer campaign mentioned above.
Number of attempts to visit phishing pages using popular shopping platforms (excluding Apple) as a lure in 2022 (download)
Amazon was the second most popular lure, with phishing attempts using its name peaking in April at 342,829. In total, 2,101,599 phishing attacks exploiting the Amazon brand were detected between January and October of 2022. The third most popular lure was, for most of 2022, Mercado Libre. Although the marketplace is local to Latin America, cybercriminals notably abused it much more via phishing attacks than global corporations like eBay or Walmart. Specifically, attackers used the brand name of Mercado Libre most heavily during the summer season, with 56,099 attempts in June and 42,862 in August, which is more than the summer figures for eBay, Walmart, and Aliexpress. Curiously, the number of phishing sites mimicking Walmart’s platform peaked in February, likely because of Valentine’s Day. During that month, we detected 76,618 phishing attempts abusing Walmart, which is 45% of all phishing attempts that targeted Walmart users in the first ten months of 2022.
“Pick a prize and cry in surprise”
A large share of fake e-commerce pages comprises scams: juicy fake offers, often made in the name of a popular brand, which draw buyers. Scam websites will typically display a discount, giveaway or another attractive deal that supposedly expires soon, urging the user to hurry while the products are free or heavily discounted. This is where cybercriminals catch customers who are hungry for freebies and fail to double-check where they are about to enter their details: on a phishing page or the official website.
A brightly colored phishing site with a Mercado Libre logo on it lights up with, “Pick a prize and cry in surprise” written in Spanish. The surprise box can contain anything: the latest iPhone, an expensive TV set, or a much-needed lawn mower for the garden. To get it, the user just needs to pay a small delivery fee. However, all they really get if they fall for the trick is their money lost and bank card details compromised.
Fake Mercado Libre site in Spanish that reads, “Pick a prize and cry in surprise”
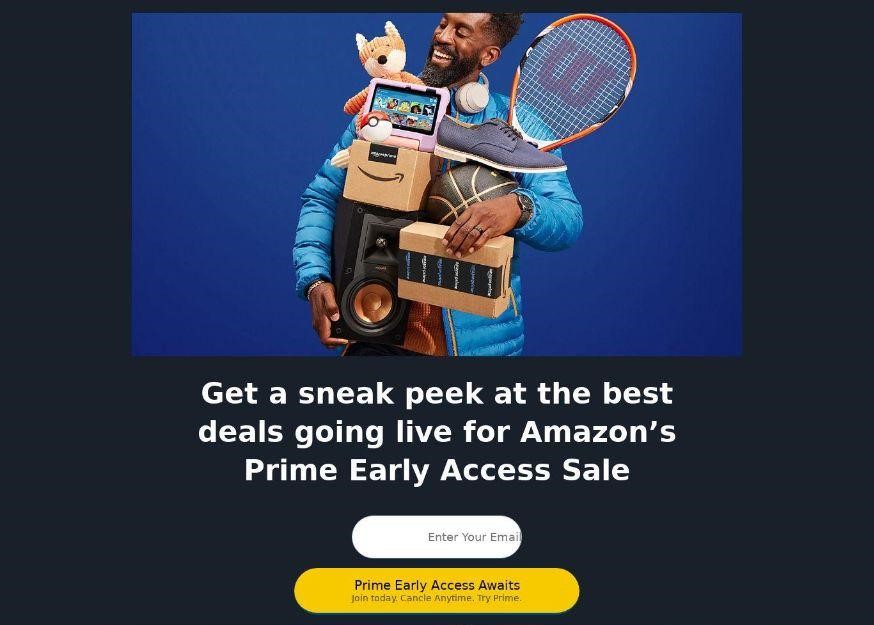
Cybercriminals often start to spread phishing and scam pages even before Black Friday sales begin in order to squeeze out the shopping season as much as possible. One scam site, for example, offers users early access to all Amazon deals a few days before the discounts become effective, to grab everything they want before other customers sweep the shelves. To get the “early access”, you have to subscribe to “Amazon Prime” on the scammers’ website. However, paying for the subscription will not get users access to Amazon’s offers. Instead of being the first among buyers, they will join the ranks of scam victims.
Users are offered early access to Amazon sales
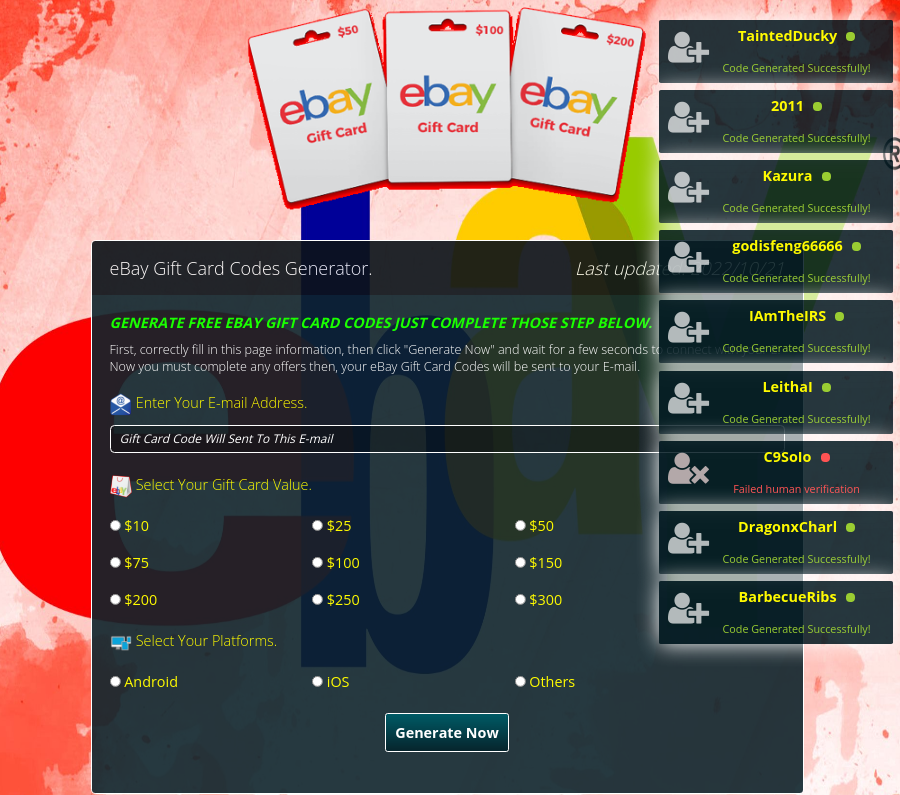
In addition to promises of early access, attackers use other tricks to lure victims. For example, they offer eBay gift cards for free. In order to generate a gift card code, users are asked to select an amount to add to the gift card account: from $10 to $300. They will then be asked to fill out a simple survey and to pay a small fee for the card, which the scammers promise to send by email. However, victims will not get any gift cards, but just lose their money to the scammers.
Victims are promised that gift card codes will be sent to their emails, which does not happen
A promise of cashback is another kind of bait used by cyberthieves. That is how they lured victims into a phishing scheme that targeted users of the Indian payment system PhonePe. The attackers sent out text messages promising cashback to users who followed a link. The phishing page urged victims to enter their UPI PIN: the secret code that is used to confirm transactions.
Fake cashback page phishing for UPI PINs
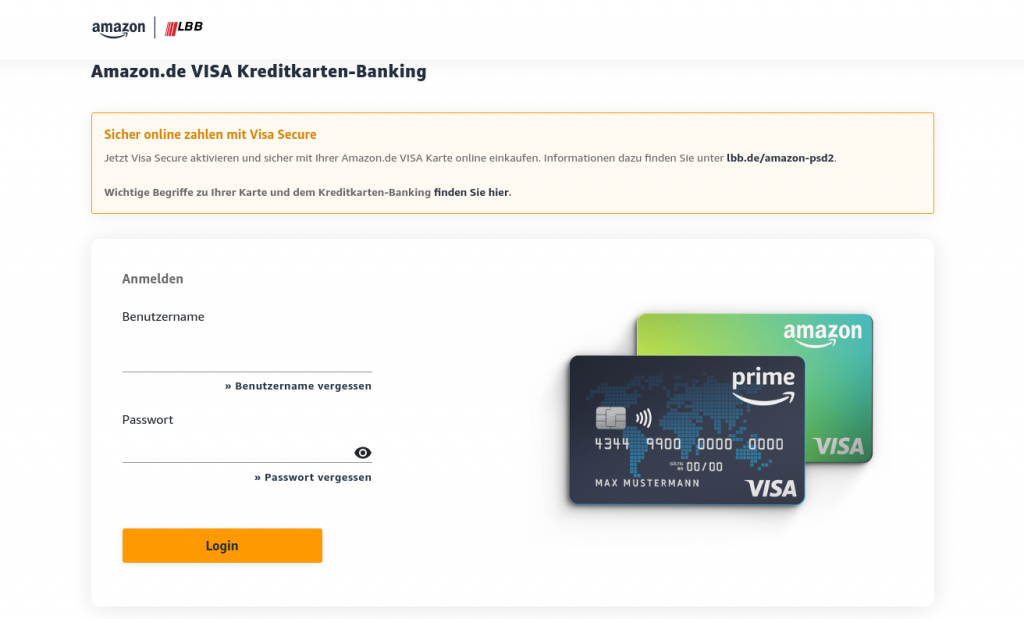
In certain cases, cybercriminals exploited several brands with one phishing page. On the screenshot below, the fake website mimics the login page for Landesbank Berlin’s Amazon.de cards. It offers users to “activate Visa Secure to pay safely with their Amazon.de Visa card”. To do that, the victim needs to enter their Landesbank Berlin login credentials, which will then be stolen by the attackers.
Users are prompted to log in to their Landesbank Berlin account to allegedly activate Visa Secure option
“Buy now, regret later”: phishing examples for BNPL services
“Buy now, pay later” (BNPL) services allow customers to split the cost of a purchase into several interest-free installments. These services appeal to consumers, especially youngsters, and have proven to be particularly popular during shopping days like Black Friday. Juniper Research assesses the BNPL user base at 360 million in 2022 and predicts this number to surpass 900 million globally by 2027. All of this makes BNPL an attractive target for cybercriminals.
BNPL phishing on the eve of Black Friday 2022
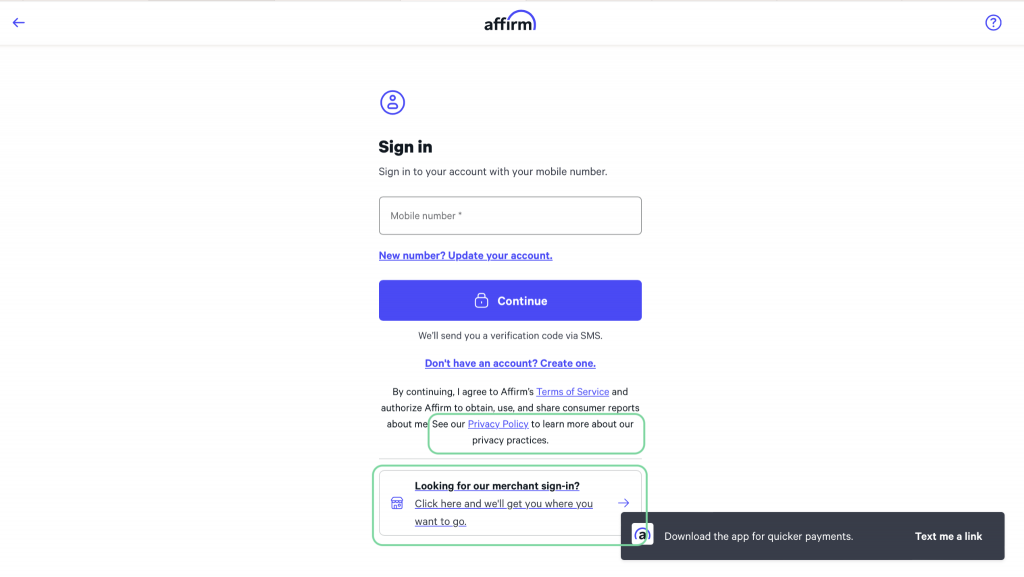
One of the most popular BNPL services is Affirm, with around 12.7 million active users worldwide. According to the official website, a user can shop online or in-store and pay later with the service at checkout. Another option is to request a virtual card in the app. Payments are managed in the app or online. The service offers a browser extension for Chrome.
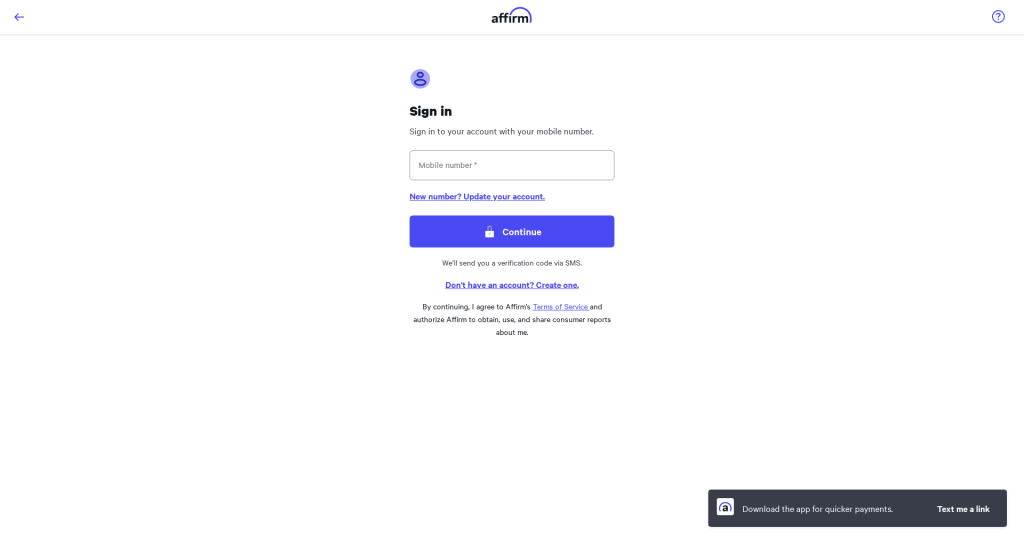
Cybercriminals have created a nearly perfect replica of the official Affirm login page—the only difference is missing links to the privacy policy and merchant login. By creating the malicious lookalike, the attackers are trying to gain access to victims’ Affirm accounts.
Affirm phishing page
The real Affirm login page (Differences highlighted)
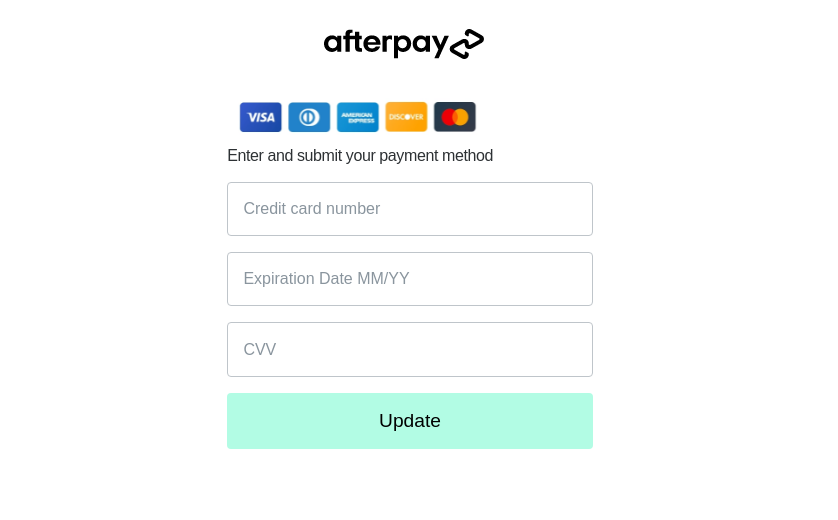
Another pre-Black Friday phishing site found by Kaspersky researchers spoofs an even more popular service named Afterpay (Clearpay in the U.K. and Italy), which has 20 million active users globally. Perpetrators have set up a page that mimics the official website, apparently trying to trick unsuspecting visitors into entering their bank card details, including the CVV, into a fake form.
A further example of a phishing page mimicking Afterpay is aimed at gaining access to potential victims’ accounts.
Phishing distribution
To attract potential victims to phishing pages, attackers usually send links to these pages by email. The email body employs social engineering techniques, for instance, to convince the user that they need to update their payment data, or that a lucrative deal awaits them on the phishing site. However, there are other ways of delivering phishing links, such as instant messages, social media, or SMS.
Phishing and scam: red flags
More often than not, a vigilant user can recognize phishing and scam pages. The text on the page can contain typos, while the domain name in the URL can differ from that of the official website by a few characters, contain extra words, or look totally unrelated to the brand whose users it targets. The only functional buttons are often those related to the main phishing or scam functionality: “pick your prize”, submit buttons, etc. All other buttons such as “I forgot my password”, the menu, etc. are typically unclickable or lead nowhere. That said, links to the terms of use and privacy policy in the footer of a phishing page can lead to the documents published on the original website, and thus help to conceal the website’s malicious purpose.
Spam
Despite all the benefits of online shopping, one of its most annoying downsides is finding your inbox clogged up with unsolicited email. Spam campaigns tend to intensify dramatically around the shopping and holiday seasons. From November 1 through November 17, 2022, Kaspersky telemetry recorded 351,800 emails containing the word combination “Black Friday”. This is more than five times the number of such emails recorded in October, when we saw 65,608. Compared to September, the increase is more than 32 times.
The number of spam emails containing “Black Friday”; September, October, and November 2022 (download)
When left unfiltered by antispam systems, spam is an annoyance and a waste of time. Our recent study revealed that employees who receive 30–60 external emails per day could be wasting as much as 11 hours annually looking through and identifying spam messages. For employees receiving between 60–100 emails a day, the figure increases to 18 hours per year, which is more than two business days.
Additionally, an important email might be lost in a deluge of spam and unintentionally deleted. Needless to say, many spam emails contain links to phishing and scam websites, or malicious attachments.
Banking Trojans go after payment credentials
Banking Trojans (bankers) are a staple in the arsenal of cyberthieves who seek to profit from the sales season. These are malicious computer programs that obtain access to confidential information stored or processed by online banking and payment systems. Bankers use webinjects and form-grabbing functionality to steal credentials, card details, or even all of the data a user enters on the target website.
After a sharp drop in banking Trojan attacks in 2021, cybercriminals reverted to using the tool heavily: from January through October 2022, Kaspersky products detected and prevented almost 20 million attacks, a 92% increase year on year.
Overall number of banking Trojan attacks, January–October 2020–2022 (download)
Conclusion
The shopping season is a profitable time not just for stores owners and consumers but also for cybercrooks. Every year, we see how fraudsters step up their activities amid the sales season by exploiting the names of popular stores, retail platforms and financial services. Unfortunately, the trend is not likely to go anywhere. This means users should be prepared and know how to stay protected at least from the “traditional” types of threats we observe every year: spam, phishing, and banking Trojans.
To enjoy the best that Black Friday has to offer this year, be sure to follow a few safety tips.
- Protect all devices that you use for online shopping with a reliable security solution.
- Do not trust any links or attachments received by email; double-check the sender’s name and email address before opening anything.
- Check that the online store address is correct and the page has no errors or visual defects on it before filling out any forms there.
- In order to protect your data and finances, it is a safe practice to make sure the checkout page is secure, and there is a locked padlock icon beside the address.
- If you want to buy something from an unfamiliar company, check customer reviews before making the decision.
- Despite taking as many precautions as possible, you probably will not know whether something is amiss until you see your bank account statement. So, if you are still getting paper statements, do not wait until they hit your mailbox. Get online to see if all of the charges look legitimate, and if not, contact your bank or card issuer immediately.























Black Friday shoppers beware: online threats so far in 2022