
Recent months have produced little of interest among worms written in Java and script languages such as JavaScript and VBScript. The main reason behind this was the limited proficiency of the virus writers, whose creations were anything but remarkable. However, a couple of malware samples grabbed our attention; their complexity is testimony to the fact that professionals sometimes get involved as well.
Kaspersky Lab’s products detect these special worms as Worm.JS.AutoRun and Worm.Java.AutoRun. They are also detected by heuristic methods as HEUR:Worm.Script.Generic and HEUR:Worm.Java.Generic respectively.
These two worms have three key features in common: heavy obfuscation, backdoor-type essential payloads, and similar methods of propagation. Both worms spread by copying themselves and the configuration file autorun.inf into the root folders of logical volumes of removable storage media and network disks. If these infected storages are opened on other computers, the infection can spread. Having infected the operating system and established a foothold on the victim computer, the malicious programs deploy their principal payload.
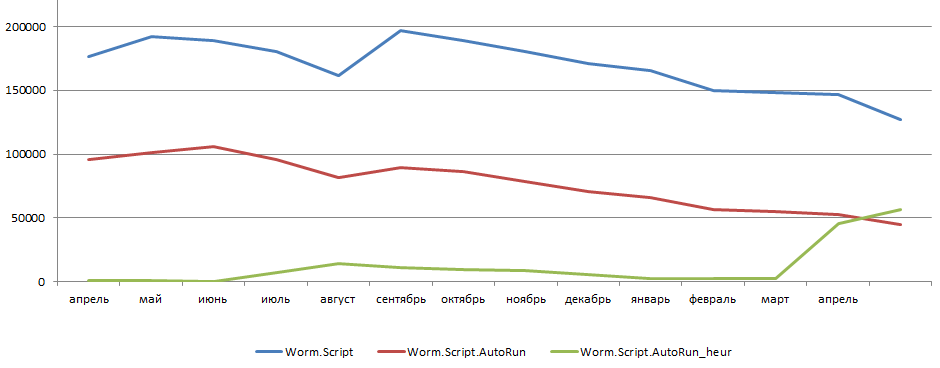
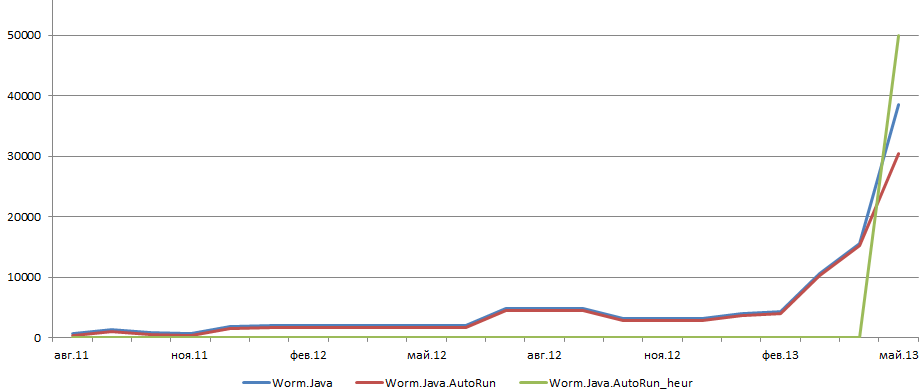
For months, the number of AutoRun worms detected on Kaspersky Lab users’ computers remained essentially unchanged. According to Kaspersky Security Network data, half of all script worms spread themselves this way. As for Java worms, this is not their usual method of propagation. However, in the last three months we have seen a dramatic rise in the number of new Worm.Java.AutoRun modifications.
Detection levels for unique script worms, AutoRun script worms, and heuristically detected AutoRun script worms April 2012 – May 2013
Detection levels for Java worms, AutoRun Java worms, and heuristically detected AutoRun Java worms August 2011 – May 2013
Both worms are polymorphic: they modify their bodies during propagation, complicating their detection. This is one of the reasons why they have become more prominent compared with “regular” worms.
Below is a narrative of what we have encountered.
Worm.Java.AutoRun
There are not many Java-based resident malware programs for PC, and worms are especially rare. So we undertook a detailed analysis of this sample.
The worm deploys itself on an infected computer in the form of four files:
- Java archive: the core component; its name changes in each infection attempt. It is located in the users’ temporary folder %TEMP%jar_cache*.tmp.
- Autorun.inf: a configuration file which ensures the worm is launched automatically when infected external storage media or a mounted network drive is opened.
- DLL file: an auxiliary (Win 32) DLL which is responsible for part of the propagation task. The name of this file also varies: it is defined at the time when the computer is infected. The DLL is copied to the user’s temporary folder: %TEMP%hsperfdata_%USERNAME%
- Java.exe is a legal executable file of the pre-installed JAVA package. The worm uses it to ensure it can always load itself into the memory of an infected computer. When an infection occurs, this executable file is coped from %ProgramFiles% to the user’s temporary folder (beside the above DLL) and is given a name associated with a system process, e.g. winlogon, csrss, or services. Then it is executed using the launch parameters of the Java archive, which is the core component.
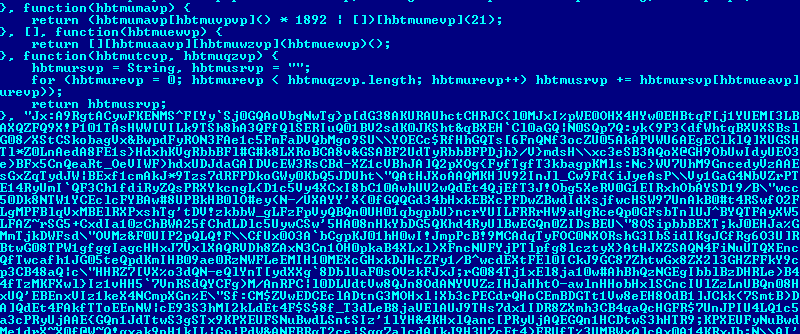
Fragment of the class-file of a malicious JAVA archive
Once initialized, the malicious Java archive extracts a dll from itself, copies itself to the temporary user catalogue and also copies the executive file Java.exe from %ProgramFiles% to the same catalogue, giving it a “trusted” name and executing it with the launch parameters of the duplicated Java archive. Then the Java archive injects the above library into the process created to distribute the worm to any available network sections and removable media. The launched malware occasionally sends requests to a command center to receive instructions from the cybercriminal.
As well as these quirks, this worm also uses strong obfuscation. Here a packer is used in conjunction with Zelix KlassMaster obfuscation. Also, as mentioned above, the worm is polymorphic. This makes it more difficult for antivirus solutions to detect.
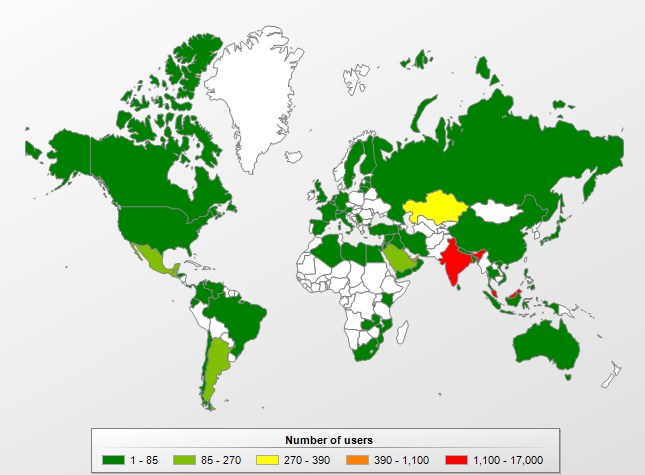
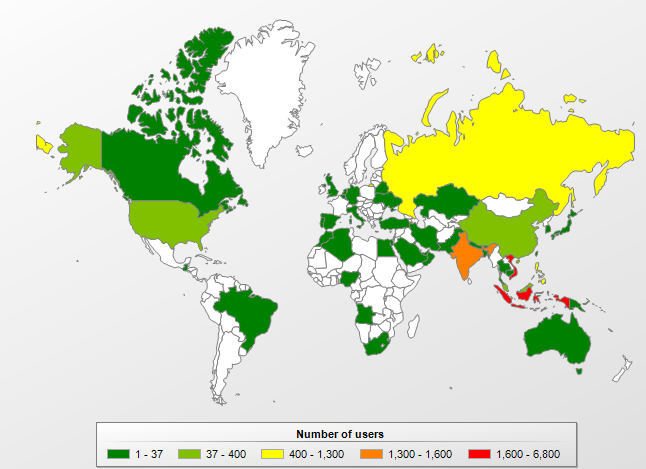
According to Kaspersky Security Network, the worm is most widely distributed in India and Malaysia. The overall picture is shown on the map below.
Geographical distribution of users protected against Worm.Java.AutoRun, January-May 2013
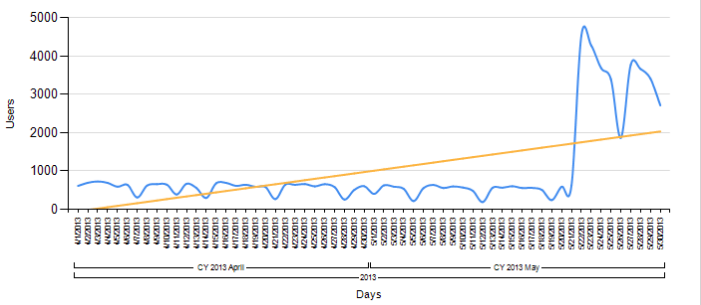
According to the same data, the worm was most frequently picked up by Kaspersky Lab products at the end of May. Most of these detections referred to its most recent modifications, those which provoked the sudden spike in detections. This worm is still actively distributing itself, so we are continuing to closely monitor its activities.
Number of users protected against Worm.Java.AutoRun, April-May 2013
Worm.JS.AutoRun
The distribution model of this worm not only uses the above method with autorun.inf, but also FTP-servers, file share sites, shared folders and CD/DVDs burned on the infected computers.
The worm multiplies itself in catalogues and adds its launch to auto launch. At this time it checks the environment where it was launched. If the worm is launched on a non-virtual machine, it starts to search for active monitoring and PC protection tools. If they are detected, the worm terminates their work.
The malware receives commands via a file downloaded from the command center. These instructions are mostly about collecting information from the infected system. In particular, cybercriminals want the worm to gather information about the system, the user and the installed software.
Like Worm.Java.AutoRun, this sample is well-encrypted and can change its form in different infections.
Code fragment for Worm.JS.AutoRun
Like the Java worm, this malware is most widespread in Southeast Asia, though this variant is more active in Vietnam and Indonesia.
Geographical distribution of users protected from Worm.JS.AutoRun from the beginning of 2013 to the end of May, 2013
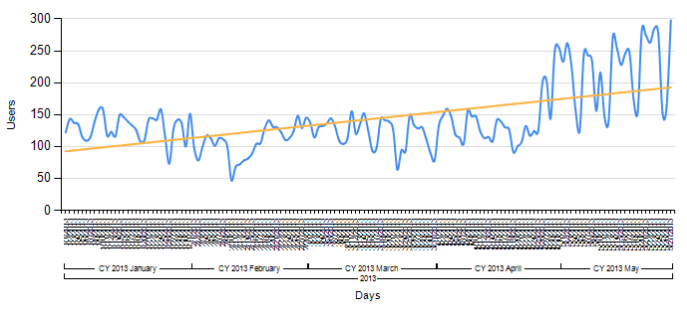
Number of users protected from Worm.JS.AutoRun in the beginning of 2013 till the end of May, 2013
In this diagram you can see the number of users protected with the signature method only. Far more users are protected with heuristic methods, as shown in the first diagram.
According to Kaspersky Security Network data, Windows XP is widely used in those countries with large numbers of malware detections. More recent Microsoft versions ask users to confirm autorun execution, which decreases the chances of getting infected. Starting from Windows 7, only CD/DVD carriers are allowed to run automatically. When using external storage devices (for instance, a USB flash drive), autorun is switched off.
In order to protect your computer from infection, we advise you to update critical OS units and antivirus databases installed on the computer. You will find the guidelines about how to set the autorun function and links to updates in the following Microsoft article: http://support.microsoft.com/kb/967715

















AutoRun. Reloaded