
This article provides an overview of the methods currently used by cyber criminals to attack financial institutions and banks in particular. It reviews general trends and takes how malicious programs targeting financial institutions are designed to evade detection by antivirus solutions. The article also covers phishing, money mules, the technical steps which cyber criminals may take when launching an attack (such as redirecting traffic, man-in-the-middle and man-in-the-endpoint attacks). Finally, the article provides recommendations on how to tackle the insecurity inherent in online banking.
The article is written with the aim of giving IT professionals a more detailed understanding of the ways in which financial institutions can be attacked by cyber criminals and what can be done to mitigate these attacks.
General Trends
In 2007, antivirus vendors saw a huge increase in the number of malicious programs targeting banks (financial malware). In spite of a lack of clear information from the financial sector, this indicates a corresponding increase in the number of attacks on banks.
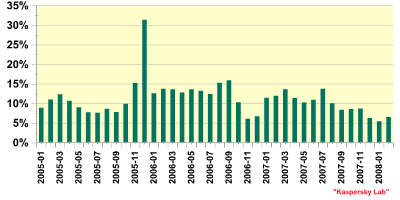
Fig. 1. Percentage of financial malware among all malicious programs detected
Notwithstanding an increased number of attacks, as the graph above shows, the percentage of financial malware detected each month is dropping. The reasons for this are detailed below:
- Malware authors constantly change their programs in order to evade detection by antivirus solutions. However, if the changes made are minor, AV vendors will still be able to detect new malware samples using signatures created for previous variants.
- The graph above only covers financial malware. However, banking attacks are usually a multi-step process: social engineering, phishing, and the use of Trojan-Downloaders which then download the financial malware. It’s easier for the criminals to modify the Trojan-Downloader programs (which are usually smaller in size, and generally less complex) than the financial malware itself.
In addition to an increasing number of malicious programs targeting financial institutions, there’s also been an increase in malware which is capable of attacking more than one bank or institution at once. However, percentage-wise, the amount of malware attacking more than three financial institutions is also decreasing, as the graph below shows:
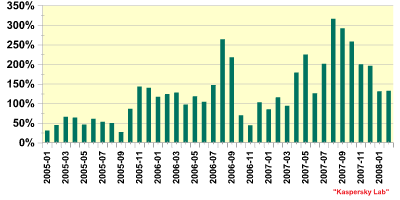
Fig. 2. Financial malware which attacks more than 3 financial organizations
This means that the vast majority of such malicious programs is designed to attack between one and three banks. The reason for this is that financial malware tends to be highly regional, with specific programs being designed to target specific banks or institutions within a single region. Individual pieces of malware will therefore be designed to attack the most widely used banks within a region such as the USA, Germany, Mexico or the UK.
The vast majority of financial malware targets a relatively small number of banks, as the graph below shows. There are probably two reasons why these banks are such popular targets: first, because they have a large number of customers, and secondly, it is relatively easy to obtain credentials to access accounts held with these banks, due to lax security.
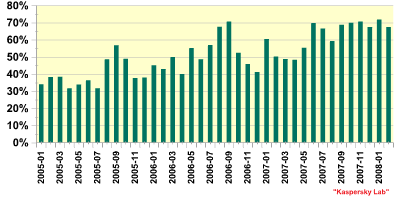
Fig 3. Percentage of malware attacking top ten banks among all financial malware
In 2007, there was also an upsurge in the number of password stealing Trojans designed to steal all data entered into web forms. These target the most popular browsers i.e. Internet Explorer, Opera and Firefox. Such Trojans can obviously be used to steal credit cards, and using such malware may be enough to breach a bank’s defences – it all depends on the sophistication of the security measures employed. Many banks which use single-factor authentication are vulnerable to relatively simple attacks.
Evading detection
The overall trends in infection vectors used by malware are mirrored by financial malware, with the vast majority of malicious programs targeting banks infecting the victim machine or systems via web surfing. While a certain number of such programs are still delivered to the victim via email, there are clear reasons why those attacking financial institutions prefer to use the Internet.
Firstly, malicious programs delivered via email are more likely to attract the attention of antivirus vendors and financial institutions, not to mention the media and end users. Stealth is a key factor in the success of attacks on financial institutions, so conducting a drive-by download using exploits is obviously an attractive method. If the user does not notice anything wrong with his/ her machine, s/he will continue to use it as normal – and in this case, continue to enter confidential data which can then be stolen and used by cyber criminals.
Secondly – and this is a significant factor in terms of evading quick detection by antivirus solutions – malicious programs which infect victim systems via the web are hosted on a web server. This means that the cyber criminals using these programs to conduct attacks can modify the malicious files very easily using automated tools – a method known as server-side polymorphism. In contrast to regular host polymorphism (where the algorithm used to modify the code is contained in the body of the malicious program) it’s impossible for antivirus researchers to analyse the algorithm used to modify the malware, as it’s located on the remote server. Although it is possible to create generic detection routines for programs which use server-side polymorphism, this takes longer.
In addition to the factors above, some of the more sophisticated Trojan-Downloaders used to deliver financial malware to its eventual destination are designed to self-destruct (or ‘melt’) once they have successfully or unsuccessfully downloaded the financial malware. This naturally hinders analysis conducted by antivirus and forensic specialists.
Money mules
The increase in financial malware is the result of the increasing criminalization of cyberspace, with malware being used to make money. In addition to stealing funds, cyber criminals need a method for accessing these funds. Obviously, the criminals can’t transfer stolen money to their own accounts as this would make them easily identifiable and significantly increase the risk of arrest and prosecution.
Banks have responded to the increased number of attacks by investing more time, money and effort into developing mechanisms for detecting fraud and illegal activity. One safeguard is for an alert to be triggered if a large amount of money is transferred to a ‘suspicious’ region of the world.
In order to sidestep this, cyber criminals have taken to using ‘money mules’. Mules are often recruited via seemingly legitimate job offers – for instance, the cyber criminals might advertise for a ‘financial manager’. If the would-be mule accepts the offer s/he is likely to receive official looking documents to sign to make it all seem legitimate. The mule makes his/ her bank account available to receive transactions, and then transfers 85% – 90% of the money onwards via a service such as MoneyGram or E-Gold. Such services are used because they guarantee anonymity, reducing the likelihood that the cyber criminal will be caught. The remaining funds are the mule’s ‘commission’ – naturally money which has been earned illegally via phishing or financial malware.
Acting as a money mule may seem like an easy way to make money, and some mules may be under the impression they are performing a legitimate job. However, they are legally viewed as being accessories to a crime, in contrast to victims who fall for a phishing scam. Mules run the risk of being tracked down and arrested, particularly if they reside in the same country as the victim.
There are several advantages for cyber criminals in using money mules. Firstly, if the mule(s) is located in the same country as the fraudster, automated bank systems are less likely to tag the transactions as suspicious. Secondly, the fraudster can use several mules and split the amount to be transferred – for instance, s/he may choose to transfer $5,000 in ten transactions rather than $50,000 in a lump sum. This limits the likelihood that the transaction will be stopped as potentially suspicious, and also limits the losses if one or two transactions are stopped.
Naturally, there is a risk in working with money mules; the cyber criminals have to be sure they can trust the chosen mule. There is, after all, little to no guarantee that the mule won’t simply disappear with the money that was transferred to his/ her account.
Phishing
When looking at the question of phishing, it’s important to have a clear definition of it. This article defines phishing as spoofed messages which allegedly come from a (financial) organization and which are designed to trick the user into giving up confidential information. This is strictly a matter of social engineering, and once malware is involved, the attack can no longer be considered phishing.
The never ending stream of phishing emails and phishing construction kits clearly demonstrate that phishing is still a very effective way of getting users to give up their credentials. There are several reasons for this. Firstly, user education has not had the desired effect, and people are still clicking on the links included in phishing email. Related to this, users are either unaware of security mechanisms (such as https), don’t pay sufficient attention to them, or simply ignore warnings about invalid or un-trusted web site certificates. Additionally, in an effort to maximize their returns, cyber criminals are constantly devising ever more ingenious social engineering schemes to deceive the more security-savvy user.
The second problem is that the defences of the majority of financial institutions can be breached by a very simple (phishing) attack. A quick review of the security measures taken by a number of banks in the USA, UK and elsewhere showed that they employ a simple static username and password to access the online banking system. All a cyber criminal has to do is obtain the username and password and s/he is free to perform almost any transaction. Another disadvantage of using a static username and password is that data can be stored and this means that unauthorized users or cyber criminals don’t have to process the data in real time; this job can be done later.
Banks which have better security policies will use at least one dynamic password: a single-time password that is only valid during a specific session. This dynamic authentication can be used either when the user logs on or signs a transaction and preferably both. Using this approach means it is impossible to sign a transaction with an expired password, and ideally makes even logging on impossible.
In order for a cyber criminal to be able to perform transactions when dynamic passwords are in place using phishing, s/he has to use a Man-in-the-Middle attack. This type of attack is discussed later in the article. Setting up a MitM attack is inherently more difficult than setting up a standard phishing site; however, there are now MitM kits available, so cyber criminals can create attacks on popular banks with a minimum of effort.
Given that phishing continues to be widespread, it is obviously a successful method of attack. Phishing attacks work on all major operating systems. However, there’s one major downside from the cyber criminal’s point of view: the user has the choice whether or not to click on a link contained in an email, and is then able to choose whether or not to enter his/ her credentials.
This element of choice is inherent in all social engineering approaches. A technical approach involving the use of malware removes this element of choice, making those users who didn’t fall for a phishing scam are still a viable target.
Automated Attacks
Financial malware comes in all shapes and sizes, and will often be tailored to target a single organization. The way the malware operates is normally determined by the bank’s defences. This means there’s no requirement for the cyber criminals to spend time creating unnecessarily complex malware. There are several methods which malware authors can use to get around banking security and harvest user information. For instance, if a bank uses single-factor authentication with a static username and passwords, it’s a simple matter of capturing keystrokes. Alternatively, some banks have created dynamic keypads so that the user needs to click a ‘random’ pattern in order to enter his password. Malware authors use two different methods to circumvent this type of security – they can either create screen dumps when the user visits a specific site or simply gather the information being sent to the site by grabbing the form. In both cases, the stolen data is processed later.
The use of Transaction Authorisation Numbers (TAN) for signing transactions makes gaining access to accounts somewhat more complex. The TAN may come from a physical list issued to the account holder by the financial organisation or it may be sent via SMS. In either case, the cyber criminal does not have access to the TAN. In most cases, malware used will capture the information entered by the user in a way similar to that described above. Once the user enters the TAN, the malware will intercept this information and either display a fake error message, or send an incorrect TAN to the financial site. This may result in the user entering another TAN. An organization may require two TANS to complete a transaction – this depends on the organization and the security systems it has decided to implement. If only one TAN is required to make a transaction, the attack describe above could allow a cyber criminal to make two transactions.
The success of such an attack is highly dependent on the exact implementation of the TAN system. Some systems do not set an expiry date for TANs; it’s simply a case of the next TAN on the list has to be the next TAN used. If the next TAN on the list doesn’t reach the bank’s site then the criminal will be able to either use it immediately, or save it for later use. However, stolen TANs have a shorter lifespan than a static username and password, due to the fact that a user who is experiencing persistent problems during an online banking session is likely to call the bank to request assistance.
Where TANs are sent to the account holder via SMS, a unique TAN can be issued for each unique transaction in a method somewhat similar to two-factor authentication. From this point onward cyber criminals have to start processing data in real-time, by using a Man-in-the-Middle attack.
Redirecting traffic
Another method used by cyber criminals is to redirect traffic. There are several ways of doing this, and the easiest of these is to modify the Windows “hosts” file.
This file, which is located in the %windows%system32driversetc directory, can be used to bypass DNS (Domain Name Server) lookups. DNS is used to translate domain names, such as www.kaspersky.com, into an IP address. Domain names are used purely for convenience; it’s the IP addresses which are used by computers. If the hosts files is modified to point a specific domain name to the IP address of a fake site, the computer will be directed to that site.
Another method for redirecting traffic is to modify the DNS server settings. Instead of trying to bypass DNS lookups, the settings are changed in such a way that the machine uses a different, malicious, DNS server for the lookups. Most people surfing from home use the DNS server belonging to their ISP for lookups. As a result, the vast majority of this type of attack has been directed at workstations. However, when a router is used to access the internet, by default it’s the router performing DNS lookups and passing them on to the workstations. There have been a number of attacks on routers which were designed to modify the router’s DNS server settings. Given the increased attention to router insecurity, it’s likely that such attacks will become more widespread. XSS attacks can be used to modify certain key settings, such as the DNS servers used, simply by causing the user to visit a specific web site.
Yet another method which can be used to redirect traffic is to place a Trojan on the victim machine which monitors the sites visited. As soon as the user connects to a banking site (or that of another financial organization) the Trojan will redirect the traffic to a fake website. The traffic may be redirected from an HTTPS site to an HTTP (potentially insecure) site. In such cases, the Trojan is usually able to suppress any warning message issued by the browser.
From the point of view of cyber criminals, however, this method can have its downsides: such Trojoans are usually Browser Helper Objects, which means that they will only work in Internet Explorer. Additionally, although the traffic is redirected, it may not be processed in real time, which gives the victim the chance to contact his/ her bank to stop the transaction.
Man-in-the-Middle attack
More sophisticated malware will use a MitM attack; this not only enables cyber criminals to attack more banks, but also ensures a higher return, as data is processed in real time. A MitM attack uses a malicious server to intercept all traffic between the client and the server i.e. the customer and the financial organization. Although everything will seem normal to the user, when s/he is asked to authorize a transaction, s/he is actually authorizing a transaction created by the cyber criminal. Malware which uses a MiTM attack typically either hides browser notifications about false web site certificates or, more commonly, shows a fake notification. However, depending on the approach used by the malware, it may do neither of these things, simply because it isn’t necessary. For example, if a user logs onto a bank’s web site and the malware takes control and starts directing traffic to the MitM server, the malware will simply ‘update’ the bank’s page, making it appear to the user that s/he is still viewing the same site.
A lot of the more sophisticated financial malware which uses MitM attacks also makes use of HTML injection.
This normally manifests itself in one or two ways. Trojan-Spy.Win32.Sinowal, a very common family of malicious programs which can attack over 750 banks, often shows pop-ups where the user should enter information. Sinowal may actually show pop-ups which ask for non-related information in an attempt to persuade the user to enter other confidential details. The screenshot below shows a pop-up generated by Sinowal on a banking site – it is asking the user for credit card details which are not translated to the current transaction.
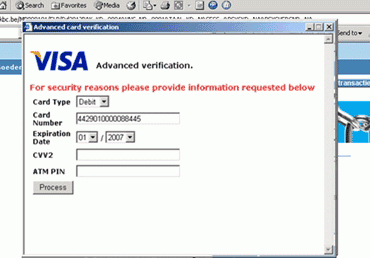
Fig 5. Popup generated by Sinowal
A more popular use for HTML injection is to add an additional form to the banking web site: the text accompanying the form asks the user to enter additional information.
Normally the requested data are the credentials needed to sign a transaction. This way MitM server can automatically complete a transaction even where two-factor authentication is used.
Although this method isn’t necessary for the successful completion of a MitM attack, it’s the easiest for malicious attackers to automate. However some MitM attacks use a different tactic. They make it possible for a transaction to be added or the original transaction approved by the customer to be modified – naturally without notifying the victim. While such MitM attacks tend to be successful, there are some drawbacks from a cyber criminal’s point of view. A MitM attack tends to make browsing noticeably slower and this may cause a user to become suspicious. Additionally, banks are reviewing their security systems specifically in an attempt to identify illegitimate transactions heuristically. For instance, if a customer logs on from a certain IP address 99 times and the 100th time s/he logs in from an IP address located in a completely different country, the system will raise a flag.
With cyber criminals remaining eager to maximise their returns and remain at liberty, they have been examining other ways of conducting attacks. Thus, we are now seeing an increase in so-called next generation financial malware – Man-in-the-Endpoint (MitE).
The Next Generation
Although the concept of MitE attacks has been discussed for a number of years, it’s only recently that it has been actively used in the wild. In contrast to a MitM attack, a MitE attack doesn’t involve an additional server to intercept traffic between the client and server. Instead, all changes are made on the local system.
There are several significant advantages to this approach. Firstly, there’s a direct connection with the financial organisation so there’s no chance of a transaction being tagged simply because a user has logged on from an unknown IP address. Secondly, a MitE will have a better success rate than a MitM attack if used against a system which employs complex defences.
However creating MitE malware requires a lot of time and effort on the part of the malware writer. One attack scenario is where a system is infected with a Trojan designed to capture all HTTPS traffic. The captured traffic is then sent to the malware writers, providing them with a blueprint of the website. This blueprint is in turn used to create another Trojan.
Cyber criminals usually use MitE attacks to target banks using two factor authentication; a safeguard that makes it difficult for the cyber criminal to gain access to the actual transaction area on the bank’s website. The method described above is effective from a technical point of view. It also eliminates the need for recruiting an insider who can provide the criminal with valid credentials to log on to the site.
The Trojans used in the attack will often be able to receive data from a Command & Control server where criminals store information regarding the account number and amount of money they should transfer. As this can be done dynamically details can be sent to each infected machine, with each machine transferring funds to the respective money mules involved.
It’s noticeable that malware writers will modify malware variants from the same family in accordance with a specific bank’s security mechanisms. This is done with a view to making an attack as effective as possible. For instance, with one bank the Trojan will secretly add an extra transaction, but with another bank the Trojan secretly replaces the user’s transaction in order not to arouse suspicion.
Solutions
Financial institutions around the world are seeing increasing losses from cybercrime. Investing in better security costs a lot of money. However, this is a choice that banks clearly have to make. As this article demonstrates, single-factor authentication can be bypassed extremely easily by cyber criminals – all that is needed is a simple generic key-logging program. It is therefore encouraging that many of the banks which have not implemented two-factor authentication are planning to do so.
However, there’s a clear trend: the increased usage of two-factor authentication by financial organizations has resulted in an increase in malware capable of defeating this type of authentication. This means that the eventual adoption of two-factor authentication will not have any significant long-term effect. It will simply raise the benchmark for financial malware.
On the other hand, it should be noted that most banks currently using two-factor authentication have not yet configured their systems for maximum security. This means that there’s still a window of opportunity open during which the security industry will be able to counteract the actions of the cyber criminals.
Nonetheless, there is a fundamental problem with two-factor authentication, namely that though the session may be secure, whatever happens during that session goes unchecked. In order to increase security, some additional form of communication, such as the use of a cryptographic token or SMS messages (already implemented by some financial institutions) is required. SMS messages could set limits on the lifetime of the TAN, the account numbers being accessed and the maximum permissible transaction amount.
Obviously there is a potential downside to the method detailed above: it could lead to virus writers creating malware to run on the devices which receive the SMS messages. A cryptographic token is therefore a better solution as it’s not possible to install any additional software on such a token. Ideally, it would have separate algorithms for both logging on to a site and signing a transaction.
Currently, when signing a transaction, customers are presented with a cryptographic challenge. One major issue is that to date these challenges are meaningless for the customer. Therefore there should be an additional challenge for each separate transaction. Using the total amount to be transferred as an additional challenge is not a secure method. Certain Trojans are already defeating this mechanism by changing the account number instead of adding another transaction.
A secure challenge would require the customer to enter the details of the account s/he wants to transfer the funds to – something which cannot be predicted by malware or cyber criminals. Another plus in this scenario is that the customer is actively using the account number; theoretically this means that s/he’s more likely to detect a bad transaction rather than just reading the content from an SMS.
Moreover, such a mechanism could be made more user-friendly by offering the option for the customer to create an allowlist of account numbers which would not require additional authentication. However, this would then require efforts to secure both the allowlist and the procedure for accessing it.
Obviously, a huge amount depends on financial institutions and banks, and their willingness to implement appropriate security measures. Given that security for online banking procedures is relatively new, antivirus vendors have a responsibility: can security solutions detect current financial malware? How capable are they of detecting new malware variants and phishing attacks?
Last, but not least, any security solution and process is as strong as the weakest link: in this case, it’s the customer. Will s/he click on a link or an attachment? Is his/ her system up-to-date, with all patches applied? Financial institutions are already taking such factors into account, and some organizations are already stating they will not provide restitution for losses if the attacked system was not fully patched.
Unfortunately, the experience of the anti-virus industry shows that user education has a limited effect, and that security measures taken by institutions can be somewhat hit-and-miss. It therefore seems that when the subject comes down to attacks on banks, the anti-virus industry is still in the front line in terms of protecting both users and financial institutions against losses.






















Attacks on banks