
An Expert Take on Targeted Attack Operations
Kaspersky Lab is currently tracking more than a hundred threat actors and sophisticated malicious operations targeting commercial and government organizations in over 80 countries. During the first quarter of 2017, there were 33 private reports released to subscribers of our Intelligence Services, with Indicators of Compromise (IOC) data and YARA rules to assist in forensics and malware-hunting.
We continue to observe a sharp rise in the sophistication of attacks with nation-state backing and a merger of tactics, techniques, and procedures (TTPs) between APT actors and financially motivated cybercriminals. We have witnessed the Middle East becoming one of the major cyber battlefields. At the same time, during Q1 2017, the discovery of a new Wiper victim in Europe raised eyebrows and suggested that these kinds of destructive attacks have now spread beyond the Middle East.
In this report, we discuss the targeted attack highlights from the first quarter of 2017, and discuss some emerging trends that demand immediate attention.
Highlights in targeted attacks
Evolution of Wipers: a new weapon for APT actors
During the last few months a new wave of wiper attacks, mainly focused against Saudi interests, raised a red flag for many companies, and for a good reason. The new wave of Shamoon attacks apparently relied on stolen credentials from Active Directory for their internal distribution stage. The investigation of these attacks lead us to the discovery of a new wiper we called StoneDrill.
We believe both Shamoon and StoneDrill groups are aligned in their interests, but are two separate actors, which might also indicate two different groups working together.
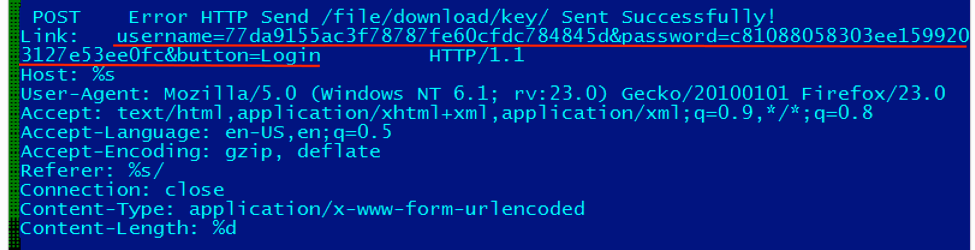
Our technical analysis of StoneDrill lead to the discovery of old samples (2014) in our collection that share their base code with the new StoneDrill samples. Interestingly, these old samples were attributed to the NewsBeef (Charming Kitten) group. The similarities between samples include sharing the same credentials (username and password) for C2 communications, which establish a very strong link between them.
Figure 1. Credentials used for C2 communication both in StoneDrill and NewsBeef samples
We believe that StoneDrill might be a more recent version of NewsBeef artifacts, effectively relating the known APT actor with this new wave of wiper attacks.
In addition, and related to the Shamoon attacks, we have collected different artifacts that might have been used by the actor during the first stages of attack. This first stage is critical, as credentials need to be stolen for the subsequent distribution of the malware at the victim’s premises.
Ismdoor is a backdoor found to be related to the Shamoon attacks, and might serve well for the attackers’ purposes. This tool was found mainly in Saudi Arabia and belongs to the oil and energy industry. The analysis revealed very interesting details about additional tools used by the attackers for lateral movement, which were mainly based in Powershell-based exploitation frameworks, following the trend of using fileless generic malware explained later in this report.
Finally, it is remarkable that we have detected the first victim of StoneDrill in Europe. The victim belongs to the energy industry, something which might be an indicator that this actor is spreading out of the Middle East. After attributing this wiper with what we believe might be a government-sponsored actor, this fact is highly worrying, as it might indicate a geopolitically-motivated spread of cyber-sabotage operations. This last assumption is yet to be confirmed.
Summary:
- Wipers are now extending their geography
- Wipers are now a part of the arsenal of APT groups. They can be used in destructive operations, as well as for deleting traces after a cyberespionage operation.
- One of the modules used in the last Shamoon wave of attacks had ransomware capabilities, which might be considered another form of not-so-obvious wiping.
- The fact that these destructive operations against energy companies might be related to some government sponsored APT actors is definitely worrying, and surpasses typical espionage operations.
BlueNoroff/Lazarus: bank robbery, evolved
A massive waterhole attack targeting Polish banks was publicly disclosed on 3 February, 2017. The attack leveraged the webserver of a Polish financial sector regulatory body, the Polish Financial Supervision Authority (www.knf.gov.pl), which was hacked and used to redirect users to an exploit kit. A very similar technique was used against the Mexican financial authority at the same time, and even if no other victims of this group were made public, it is very likely that more banks were also similarly affected.
Our analysis linked the attack with the BlueNoroff/Lazarus group, which has been responsible for multiple other bank attacks, including the famous Bangladesh bank heist. This waterhole attack revealed, for the first time, one of the strategies used by BlueNoroff for gaining a foothold in its target organizations. Although the attack didn’t use any zero days, the Flash Player and Silverlight exploit appeared to be enough to compromise a large number of banks, which were running on outdated software.
Indeed, we started tracking the BlueNoroff actor a long time ago. We originally saw this actor trying to infect banks in the South-East Asian region. BlueNoroff has developed a characteristic set of tools for lateral movement inside targeted organizations, and in several cases attempted tampering with SWIFT software for cashing out. This technique showed its enormous potential with the Bangladesh central bank heists, where attackers attempted to steal more than 900 million USD. In the February “Polish case”, we saw the group reusing these known lateral movements tools repackaged for their new wave of victims. This provided us with a high degree of confidence in attributing the attack to this actor.
Interestingly, the BlueNoroff group planted Russian words within the code, to derail investigators and avoid attribution. The code contained grammar errors a native Russian speaker wouldn’t make, and sentences were likely translated using online tools.
Summary:
- We believe BlueNoroff is one of the most active groups in terms of attacks against financial institutions and is trying to actively infect different victims in several regions.
- We think their operations are still ongoing, and in fact, their most recent malware samples were found in March 2017.
- At the moment we believe BlueNoroff is probably the most serious threat against banks.
Fileless malware: enough for the job with no attribution
Avoiding attribution is one of the key goals for many APT actors, especially since a large number of operations have been exposed in recent last years. For the most sophisticated groups, the problem is that they already have their well established procedures, specially crafted tools and training, that do not always allow them to stay unnoticed.
But that is not the case for the not-so-big actors or cybercriminals. Rather than creating and having their own tools, these use generic tools that are good enough to complete an operation, and provide an evident economic advantage, with the added value of making both analysis of the incident and attribution to a particular actor more difficult.
Nowadays there is a large number of different frameworks providing cyber-actors with many options, especially for lateral movement. This category includes Nishang, Empire, Powercat, Meterpreter, etc. Interestingly, most of these are based on Powershell, and allow the use of fileless backdoors.
We have seen such techniques being widely adopted in the last few months. We find examples in the lateral movement tools used in Shamoon attacks, in attacks against Eastern European banks, and used by different APT actors such as CloudComputating, Lungen or HiddenGecko, as well as in the evolution of old backdoors like Hikit, which evolved to new fileless versions.
This trend makes traditional forensic analysis harder, traditional IOCs such as file hashes obsolete, application allowlisting more difficult, and antivirus evasion easier. It also helps to evade most of the log activity.
On the other hand, attackers usually need to escalate privileges or steal administrator credentials, they don´t usually have a reboot survival mechanism in the machines they want to infect, and they rely on accessing them when they are reconnected to the infected network. The use of standard tools in the victim environment might also limit their options. This new paradigm is still unfolding and the best practices from a defense perspective are currently not totally clear. However, we offer our recommendations in the final section of this document.
Summary:
- No malware samples are needed for the successful exfiltration of data from a network.
- The use of standard and open source utilities, combined with different tricks, makes detection and attribution almost impossible.
- The determination of attackers to hide their activity and make detection and incident response increasingly difficult explains the latest trend of anti-forensic techniques and memory-based malware. That is why memory forensics is becoming critical to the analysis of malware and its functions.
- Incident response in cases like this is key.
How to keep yourself protected
Exploiting vulnerabilities remains a key approach to infecting systems, therefore timely patching is of utmost importance – which, being one of the most tedious IT maintenance tasks, works much better with good automation. Kaspersky Endpoint Security for Business Advanced and Kaspersky Total Security include Vulnerability & Patch management components, offering convenient tools for making patching much easier, and much less time-consuming for IT staff.
Given the trend of using Powershell-based techniques, including bodiless malware scenarios, you need to make sure that your security solution is aware of such specifics. All tiers of Kaspersky Security Endpoint Security for Business as well as Kaspersky Security for Virtualization possess the broadest range of machine learning-powered detection techniques including those specifically taking care of malware using Powershell. Our behavioral System Watcher technology is also aware of specific Wiper activities like mass file deletion; after blocking the malware, its Rollback feature brings important user files back from their deleted state.
Still, it is necessary to understand that targeted attacks are dangerous not only because of their sophistication (which sometimes is not the case), but because they are usually well-prepared, and try to leverage security gaps unobvious to their targets.
Therefore, it is highly recommended that you arm yourself not only with prevention (such as endpoint protection) but also with detection capabilities, specifically with a solution that can detect anomalies in the whole network’s ongoing activities, and scrutinize suspicious files at a much deeper level than it is possible on users’ endpoints. Kaspersky Anti Targeted Attack is an intellectual detection platform that matches events coming from different infrastructure levels, discerns anomalies and aggregates them into incidents, while also studying related artifacts in a safe environment of a sandbox. As with most Kaspersky products, Kaspersky Anti Targeted Attack is powered by HuMachine Intelligence, which is backed by on premise and in lab-running machine learning processes coupled with real-time analyst expertise and our understanding of threat intelligence big data.
And the best way to prevent the attackers from finding and leveraging security holes is getting rid of them all, including those involving improper system configurations or errors in proprietary applications. For this, Kaspersky Penetration Testing and Application Security Assessment services can become a convenient and highly effective solution, providing not only data on found vulnerabilities, but also advising on how to fix it, further strengthening corporate security.






















APT Trends report, Q1 2017