
Q3 events
Cybercrime as a Service
In the last few months the scale of the global ‘Cybercrime as a Service’ infrastructure has been revealed – fully commercialized, with DDoS as one of the most popular services capable of launching attacks the likes of which have never seen before in terms of volume and technological complexity.
Against this background, Europol published the 2016 Internet Organized Crime Threat Assessment (IOCTA) on 28 September, which is based on the experiences of law enforcement institutions within the EU member states. The report clearly ranks DDoS in first place as a key threat and that any “Internet facing entity, regardless of its purpose or business, must consider itself and its resources to be a target for cybercriminals”.
Most likely, this stems from early September when Brian Krebs, an industry security expert, published an investigation outlining the business operations of a major global DDoS botnet service called vDOS and its principal owners, two young men in Israel. The culprits have been arrested and investigations are ongoing, but the sheer scale of their business is stunning.
Based on a subscription scheme, starting from $19.99 per month, tens of thousands of customers paid more than $600,000 over the past two years to vDOS. In just four months between April and July, vDOS launched more than 277 million seconds of attack time, or approximately 8.81 years’ worth of attack traffic.
It was no wonder, that shortly afterwards a DDoS attack brought down Brian Krebs’s website with a traffic volume close to 620 Gbps, making it one of the biggest attacks the Internet has ever witnessed, only to be topped several days later by another attack close to 1 Tbps that hit France’s OVH. The attack vector, as Octava Klaba, CTO at OVH reported, looks like the same Internet of Things (IoT) botnet totaling 152,464 devices – mainly webcams, routers and thermostats – that brought down Brian Krebs’s website.
To make the situation even worse, hackers just released the Mirai source code, which, according to security experts, was responsible for the aforementioned DDoS attacks. The code includes a built-in scanner to look for vulnerable IoT devices and enrolls them into a botnet. With this, we expect to see a new wave of commercial services like vDOS and DDoS attacks in the coming months.
The Internet of Things is increasingly becoming a powerful tool for attackers, facilitated by the neglect for information security both on the part of vendors and users.
So, check that your devices connected to the Internet have a strong security setup.
‘Political’ DDoS attacks
DDoS is widely used in politics. In July of this year, an international tribunal stated China’s territorial claims to the Spratly archipelago in the South China Sea were groundless, and almost immediately at least 68 sites belonging to various Philippine government institutions were subjected to powerful DDoS attacks. The international press called these incidents part of a long-term cyberespionage campaign launched by China in its struggle for sovereignty of the Spratly archipelago.
Attack on a broker
Cybercriminals have identified the most vulnerable targets for DDoS extortion purposes – broker companies. They are high-turnover businesses that are also extremely dependent on web services. The Taiwanese company First Securities recently received a demand for 50 bitcoins (about $32,000) from unknown persons. After refusing to pay, the company’s website was targeted by a DDoS attack, which made bidding for the company’s clients impossible. Meanwhile, the president of First Securities released a statement to the press saying they had experienced a “trade slowdown” that only affected some of their investors.
Assessing the damage caused by DDoS attacks
B2B International, at the request of Kaspersky Lab, conducted the study called IT Security Risks 2016. According to the results, corporations are suffering increasing damage from DDoS attacks: a single attack can cost a company more than $1.6 billion in losses. At the same time, 8 out of 10 companies are subjected to several attacks per year.
Trend of the quarter: SSL-based DDoS attacks
According to Kaspersky DDoS Protection, the number of “smart” HTTPS-based DDoS attacks on applications increased in the third quarter of 2016. These attacks boast a number of important advantages that make a successful attack more likely.
Establishing a secure connection requires considerable resources, despite operating speeds for cryptographic algorithms constantly increasing (e.g., the elliptic curve algorithm has made it possible to enhance the performance of encryption while maintaining the persistence level). For the sake of comparison, a properly configured web server is capable of processing tens of thousands of new HTTP connections per second, but when processing encrypted connections this capacity falls to just hundreds of connections per second.
The use of hardware crypto accelerators makes it possible to significantly increase this value. However, this doesn’t help much considering the current reality of cheap and readily available rented servers, high-capacity communication channels, as well as known vulnerabilities that allow cybercriminals to build larger botnets. They can carry out a successful DDoS attack by creating a load that exceeds the performance of expensive hardware solutions.
A typical example of a “smart” attack is a relatively small number of queries being sent to the “load-heavy” parts of websites (as a rule, search forms are chosen) inside a small number of encrypted connections. Those requests are almost invisible in the overall traffic flow, and at a low intensity they are often very effective. At the same time, decryption and analysis of traffic is only possible on the web-server side.
Encryption also complicates the operation of specialized systems designed to protect against DDoS attacks (especially solutions used by communications providers). Decrypting traffic on-the-fly in order to analyze the content of network packets is often not possible during such attacks due to technical or security reasons (it’s not permitted to pass a server’s private key to third-party organizations, mathematical limitations prevent access to the information in encrypted packets in transit traffic). This significantly reduces the effectiveness of protection against such attacks.
The growing proportion of “smart” DDoS attacks is caused in no small part by the fact that amplification-type attacks, the most popular attack type in recent times, are becoming increasingly difficult to implement. On the Internet, the number of vulnerable servers that can be used to organize such attacks is steadily falling. In addition, most of these attacks have similar features, making it easy to block them completely, and ensuring their effectiveness is eroded over time.
The desire of website owners to protect data and improve privacy levels, combined with cheaper computing capacities have resulted in a growing trend: classic HTTP is being replaced by HTTPS, leading to an increase in the proportion of resources using encryption. The development of web-based technology encourages active implementation of the new HTTP/2 protocol, in which operations without encryption are not supported by the latest browsers.
We believe that the number of encryption-based attacks will grow. For developers of information security solutions this requires an immediate reappraisal of their approach to combating distributed attacks, because today’s tried and tested solutions may soon become ineffective.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience in combating cyber threats, including DDoS attacks of various types and levels of complexity. The company’s experts monitor botnet activity with the help of the DDoS Intelligence system.
DDoS Intelligence (part of Kaspersky DDoS Protection) is designed to intercept and analyze commands sent to bots from command and control (C&C) servers, and does not have to wait until user devices are infected or cybercriminal commands are executed in order to gather data.
This report contains the DDoS Intelligence statistics for the third quarter of 2016.
In the context of this report, a single (separate) DDoS attack is defined as an incident during which any break in botnet activity lasts less than 24 hours. If the same web resource was attacked by the same botnet after a break of more than 24 hours, this is regarded as a separate DDoS attack. Attacks on the same web resource from two different botnets are also regarded as separate attacks.
The geographic distribution of DDoS victims and C&C servers is determined according to their IP addresses. In this report, the number of DDoS targets is calculated based on the number of unique IP addresses reported in the quarterly statistics.
It is important to note that DDoS Intelligence statistics are limited to those botnets detected and analyzed by Kaspersky Lab. It should also be noted that botnets are just one of the tools used to carry out DDoS attacks; therefore, the data presented in this report does not cover every DDoS attack that has occurred within the specified time period.
Q3 Summary
- Resources in 67 countries (vs. 70 in Q2) were targeted by DDoS attacks in Q3 2016.
- 62.6% of targeted resources were located in China.
- China, the US and South Korea remained leaders in terms of both the number of DDoS attacks and number of targets. For the first time both rankings included Italy.
- The longest DDoS attack in Q3 2016 lasted for 184 hours (or 7.6 days) – significantly shorter than the previous quarter’s maximum (291 hours or 12.1 days).
- A popular Chinese search engine was subjected to the largest number of attacks (19) over the reporting period.
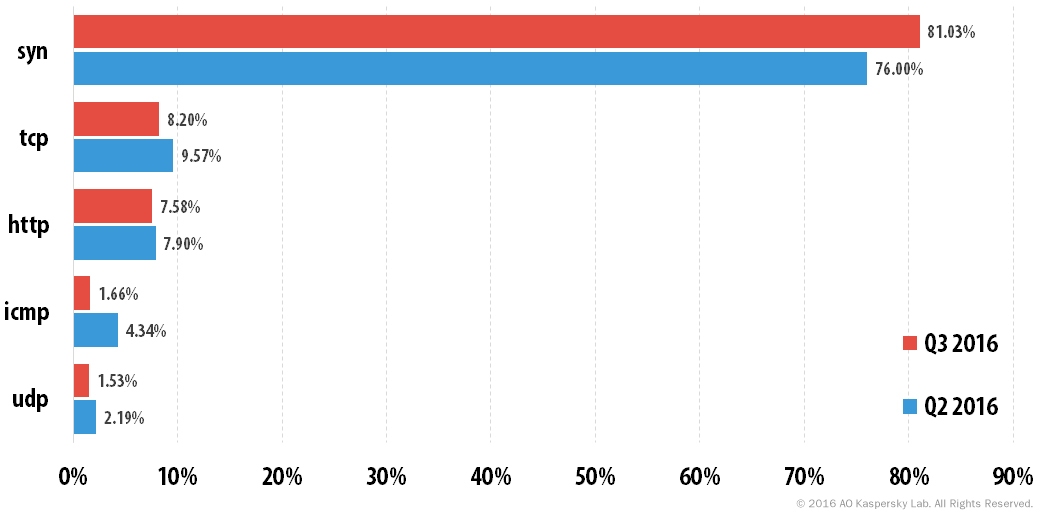
- SYN DDoS, TCP DDoS and HTTP DDoS remain the most common DDoS attack scenarios. The proportion of attacks using the SYN DDoS method continued to grow, increasing by 5 p.p., while the shares of TCP DDoS and HTTP DDoS continued to decline.
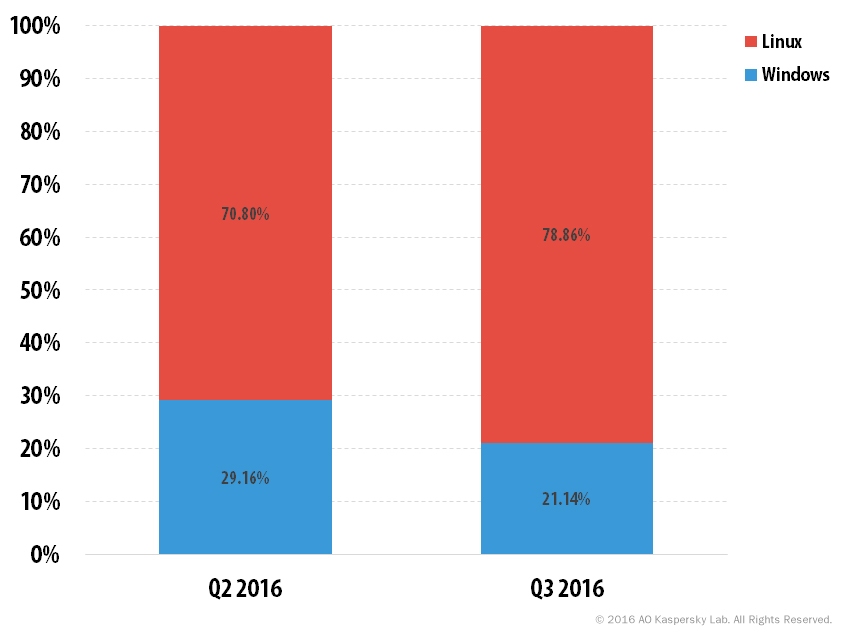
- In Q3 2016, the percentage of attacks launched from Linux botnets continued to increase and reached 78.9% of all detected attacks.
Geography of attacks
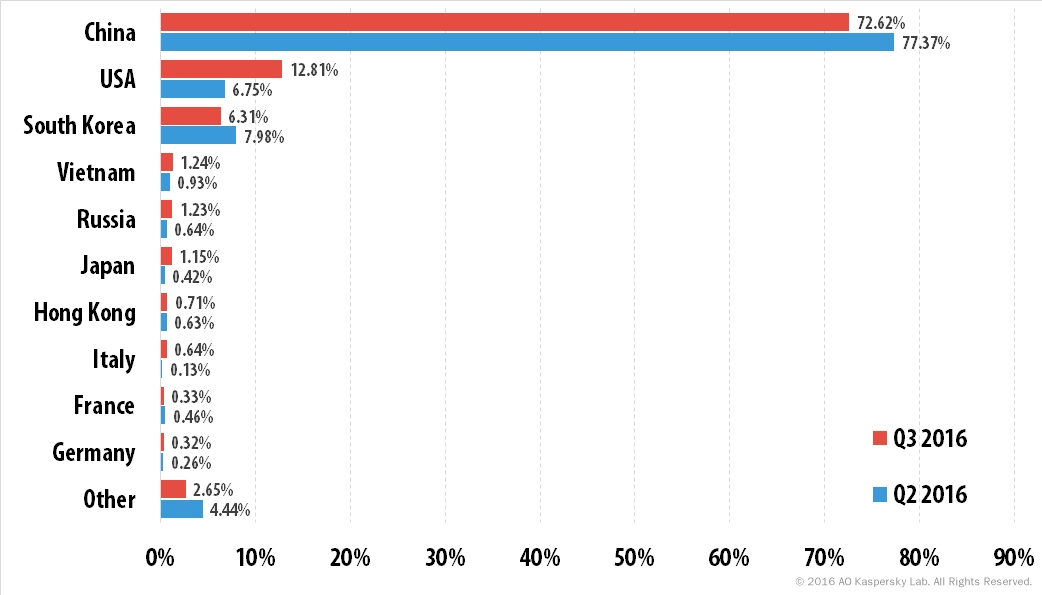
In Q3 2016, the geography of DDoS attacks narrowed to 67 countries, with China accounting for 72.6% (4.8 p.p. less than the previous quarter). In fact, 97.4% of the targeted resources were located in just 10 countries. The other two countries in the top three switched places – the US (12.8%) overtook South Korea (6.3%) to become the second most targeted country.
Distribution of DDoS attacks by country, Q2 2016 vs. Q3 2016
One entry of note to the rating of most targeted countries was Italy, appearing for the first time ever and accounting for 0.6% of all attacks. In all, the TOP 10 included three Western European countries (Italy, France and Germany).
This quarter’s statistics show that targets within the leading 10 countries accounted for 96.9% of all attacks.
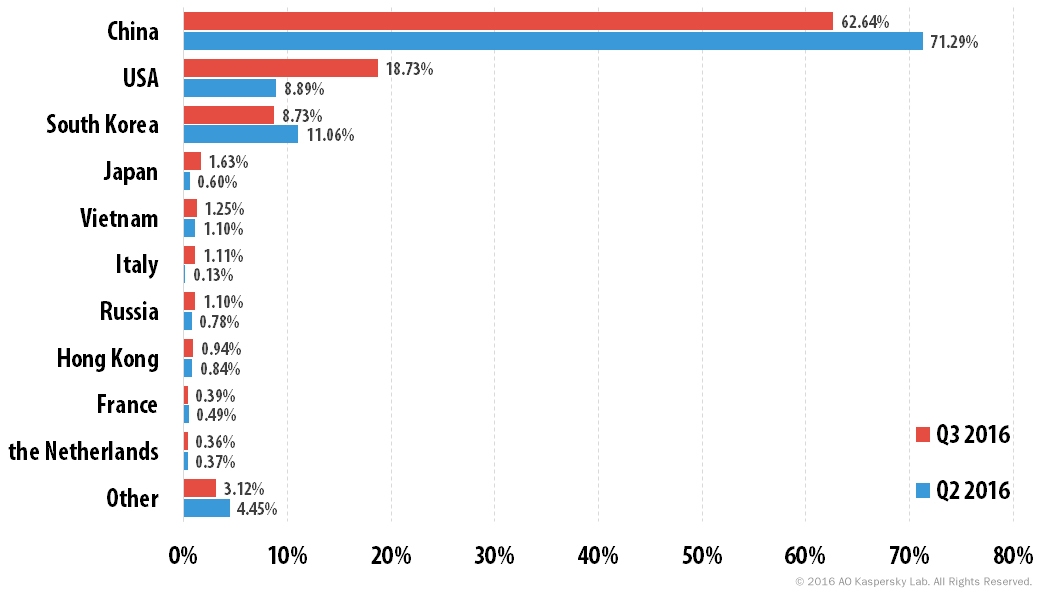
Distribution of unique DDoS attack targets by country, Q2 2016 vs. Q3 2016
In Q3 2016, 62.6% of attacks (8.7 p.p. less than the previous quarter) targeted resources located in China. However, targets in the US became more attractive for cybercriminals – the country’s share accounted for 18.7% compared with 8.9% in the previous quarter. South Korea rounded off the top three – its contribution decreased by 2.4 p.p. and amounted to 8.7%.
The shares of the other countries in the TOP 10 increased, with the exception of France (0.4%), which saw a fall of 0.1 p.p. Japan (1.6%) and Italy (1.1%) each saw a 1 p.p. increase, and as a result, Italy entered the TOP 10 for the first time and went straight in at 6th place (Ukraine left the TOP 10). The proportion of attacks targeting Russia also grew significantly – from 0.8% to 1.1%.
This rating also included three Western European countries – Italy, France and the Netherlands.
Changes in DDoS attack numbers
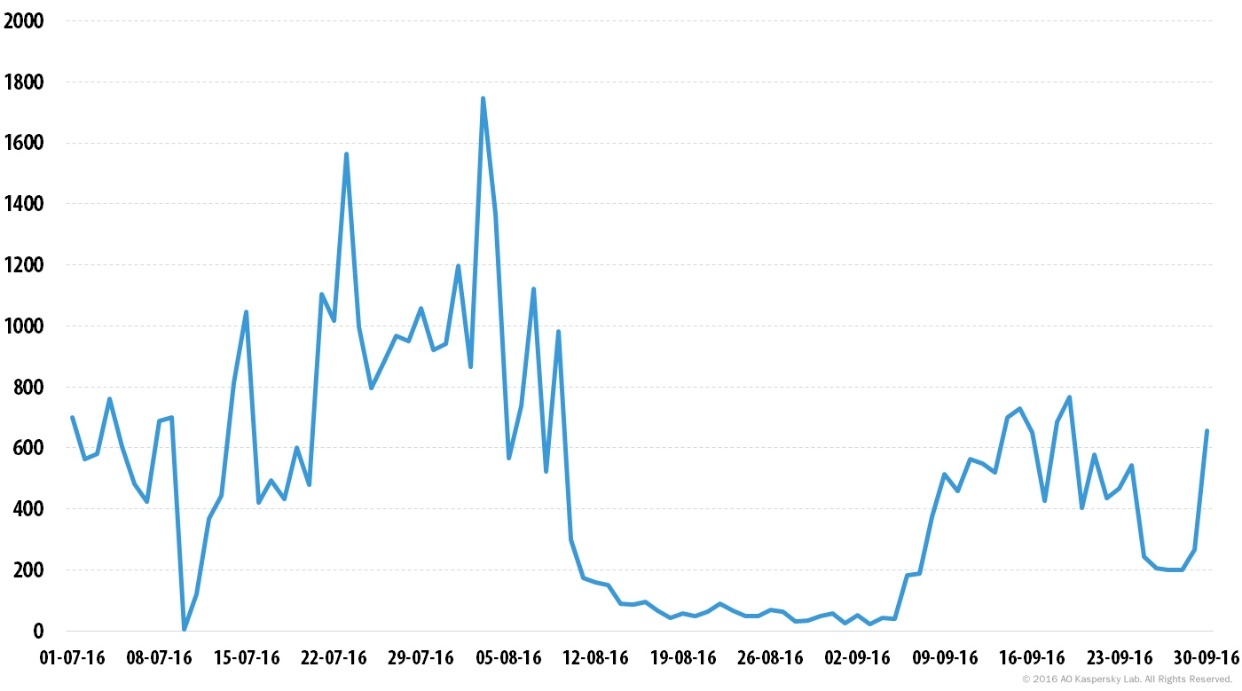
DDoS activity was relatively uneven in Q3 2016. The period between 21 July and 7 August was marked by the highest DDoS activity, with peaks in the number of attacks registered on 23 July and 3 August. From 8 August, DDoS activity plummeted and resulted in a lull which lasted from 14 August till 6 September. The smallest number of attacks was recorded on 3 September (22 attacks). The largest number of attacks was observed on 3 August – 1,746 attacks. Note that this is the highest figure for the first three quarters of 2016. Most of these attacks took place on the servers of just one service provider located in the United States.
Number of DDoS attacks over time* in Q3 2016
*DDoS attacks may last for several days. In this timeline, the same attack can be counted several times, i.e. one time for each day of its duration.
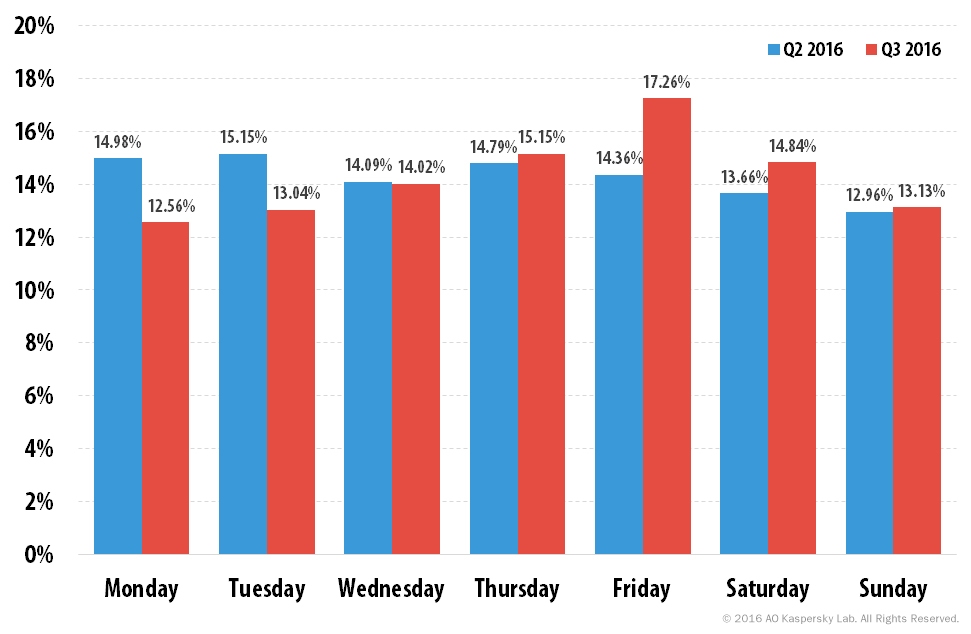
In Q3, Friday was the most active day of the week for DDoS attacks (17.3% of attacks), followed by Thursday (15.2%). Monday, which was second in Q2 with 15%, became the quietest day of the week in terms of DDoS attacks (12.6%).
Distribution of DDoS attack numbers by day of the week, Q2 and Q3 2016
Types and duration of DDoS attacks
The rating of the most popular attack methods saw no considerable changes from the previous quarter. The SYN DDoS method has further strengthened its position as leader: its share increased from 76% to 81%. The proportion of the other attack types decreased slightly. ICMP DDoS was most affected: its share decreased by 2.6 p.p.
Distribution of DDoS attacks by type, Q2 and Q3 2016
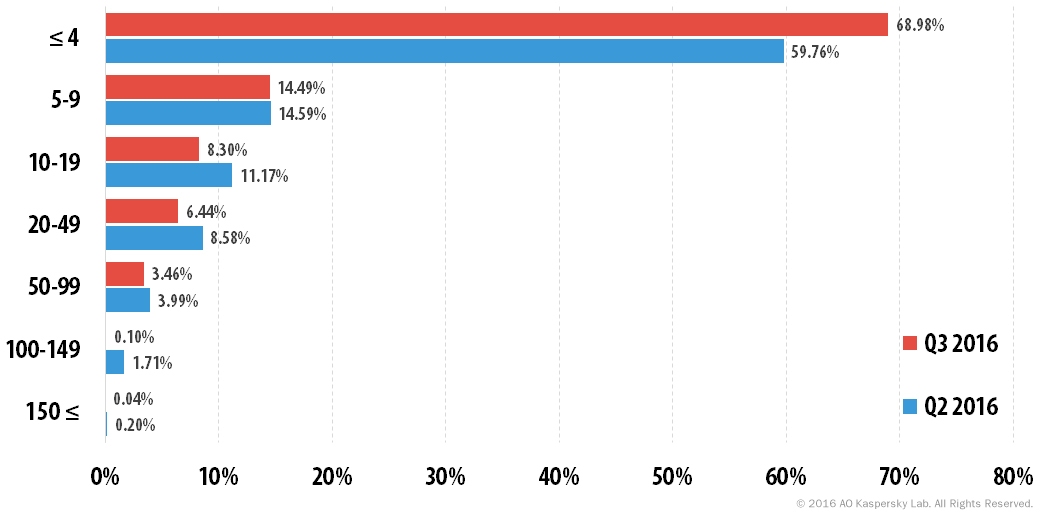
Attacks that last no more than four hours remained the most popular: in Q3 their share increased by 9.2 p.p., accounting for 69%. Attacks that lasted 5-9 hours remained in second. Meanwhile, the percentage of longer attacks decreased considerably – the share of attacks lasting 100-149 hours fell from 1.7% in Q2 to 0.1% in the third quarter. There were very few cases of attacks lasting longer than that.
Distribution of DDoS attacks by duration (hours), Q2 and Q3 2016
The longest DDoS attack in Q3 2016 only lasted for 184 hours (targeting a Chinese provider), which is significantly lower than the Q2 maximum of 291 hours. A Chinese search engine had the unenviable distinction of being attacked most – it was targeted 19 times during the quarter.
C&C servers and botnet types
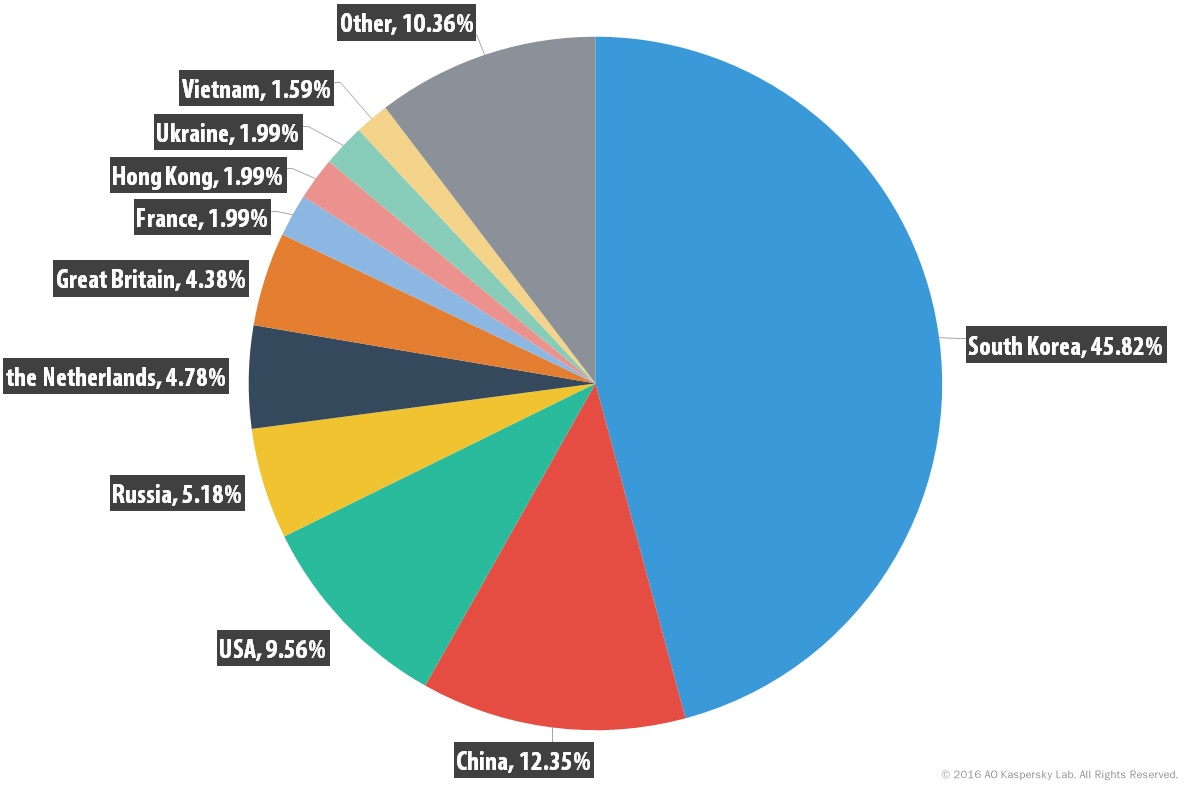
In Q3, the highest number of C&C servers (45.8%) was detected in South Korea, although this country’s contribution is considerably smaller compared to the previous quarter (69.6%).
The top three countries hosting the most C&C servers remained unchanged – South Korea, China and the US – although their total share was 67.7% vs. 84.8% in Q2.
The number of active C&C servers in Western Europe is growing – the TOP 10 included the Netherlands (4.8%), the UK (4.4%), and France (2%). To recap, three Western European countries entered both the TOP 10 countries subjected to the highest number of attacks and the TOP 10 countries with the highest number of targets.
Among the newcomers to the C&C rating were Hong Kong and Ukraine, each with a share of 2%.
Distribution of botnet C&C servers by country in Q3 2016
In Q3, Linux-based DDoS bots remained the clear leader and the share of attacks launched from Linux botnets continued to grow, accounting for 78.9% vs. 70.8% in Q2. This correlates with the growing popularity of SYN DDoS for which Linux bots are the most appropriate tool. In addition, this can be explained by the growing popularity of Linux-based IoT devices used for DDoS attacks, and will most probably be boosted further after the leakage of Mirai.
Correlation between attacks launched from Windows and Linux botnets, Q2 and Q3 2016
Q3 continues the trend of Linux dominance from the previous quarter. Prior to Q2 2016, the difference between the share of Windows- and Linux-based botnets did not exceed 10 p.p. for several quarters in a row.
The majority of attacks – 99.8% – were carried out by bots belonging to a single family. Cybercriminals launched attacks using bots from two different families in just 0.2% of cases.
Conclusion
‘Classic’ botnet attacks based on widespread malware tools such as Pandora, Drive, etc. have been well researched by analysts who have developed effective and simple methods of neutralizing attacks that utilize these tools. This is increasingly forcing cybercriminals to use more sophisticated attack methods, including data encryption and new approaches to the development of tools used for organizing attacks and building botnets.
Another interesting trend this quarter was the increased activity of DDoS botnets in Western Europe. For the first time in a year the TOP 10 most attacked countries included three Western European countries – Italy, France and Germany. This correlates with the increased number of active C&C servers in Western Europe, particularly in France, the UK and the Netherlands. Overall, Western European countries accounted for about 13% of active DDoS botnet C&C servers.
Kaspersky DDOS intelligence report for Q3 2016




















Cristian Servin
Que buen informe
nick
Hi,
I would like on know if SYN attack is most popular than UDP attack. From most reports it is obvious that UDP attack is much more popular but you mention on top SYN attack. Is it possible to explain this to me?
Thank you very much.
Nick