
Q1 events
We have selected the events from the first quarter of 2016 that, in our view, illustrate the main trends in the field of DDoS attacks and the tools used to perform them.
A record-breaking reflection DDoS attack
DDoS attacks using amplification/reflection techniques are still popular and allow cybercriminals to break their peak power records. From a technical point of view, amplification methods are nothing new in DDoS attacks, but cybercriminals are discovering new ways and resources to enhance the capacity of their botnets. For example, according to a recently published report, 2015 saw the largest ever DDoS attack on record at 450-500 Gbps.
DDoS attack on Trump
It’s possible that last year’s record didn’t last very long – at the very beginning of the year the official website of Donald Trump’s election campaign were subjected to DDoS attacks whose strength, according to unconfirmed sources, reached 602 Gbps. The hacktivist group New World Hacking claimed responsibility for both incidents.
Use of the DNSSEC protocol
Criminals are increasingly using the DNSSEC protocol to carry out DDoS attacks. The protocol is intended to minimize DNS spoofing attacks, but besides the domain data a standard DNSSEC reply also contains additional authentication information. Thus, unlike a standard DNS reply of 512 bytes, the DNSSEC reply comes to about 4096 bytes. Attackers exploit this feature to perform amplification DDoS attacks. They usually use domains in the government zone .gov, because in the US such domains are required by law to maintain DNSSEC.
Pingback attacks on WordPress
Web resources powered by the WordPress content management system (CMS) are still popular with cybercriminals carrying out DDoS attacks. Popular CMS-based resources often become targets of DDoS attacks exploiting the WordPress pingback function. The pingback function notifies the author of a post published on a WordPress site when someone else links to that post on another site running the same CMS. If the administrator of the site running WordPress has enabled the function, all links leading to the materials published on a site can perform a so-called pingback, i.e. send a special XML-RPC request to the original site. A huge number of pingback requests sent to the original site can cause a “denial of service”. This feature continues to attract the attention of cybercriminals and helps them perform DDoS attacks at the application level.
Linux Mint hacking
On 21 February 2016, the head of Linux Mint, Clement Lefebvre, reported that someone had managed to hack the project infrastructure including its official website and forum, and substituted the link to the legitimate ISO image of the Linux Mint 17.3 Cinnamon edition with their own URL. The hacker’s modified ISO contained malicious code that used infected machines to perform DDoS attacks.
Attacks on security companies
Cybercriminals also target companies working in information security, with most of the major players – especially those offering anti-DDoS services – having to regularly combat DDoS attacks on their resources. These attacks can’t cause much damage because all these resources are well-protected, but that doesn’t stop the cybercriminals.
In Q1 2016, resources in 74 countries were targeted by #DDoS attacks #KLreport
Tweet
In general, cybercriminals don’t go all out to bring down an IT security company’s site. The attacks tend not to last long, and in most cases, they are terminated as soon as the source notices that protection systems are working. The cybercriminals don’t want to waste their botnet resources when they could be earning money elsewhere. Nevertheless, the attacks continue.
Analysis of the correspondence on underground forums suggests that the criminal fraternity uses the websites of IT security companies as test bed, i.e. to test new methods and tools. This approach is no worse than others, but it does give us some valuable information. If worldwide DDoS statistics show the current state of things, then attacks on IT security companies allow us to some extent to predict the future of DDoS.
Data on the tactics, strength and types of attacks targeting Kaspersky Lab sites also allows us to forecast the trends in the DDoS industry for the coming months.
Once again, we have had to deal with amplification attacks. Their number has declined slightly compared to last year, but their maximum strength has increased fourfold. This confirms the trend of a general strengthening of these attacks – the criminals have to increase the strength to overcome protection measures used by Internet providers and information security companies. In our case, none of these attacks led to our sites being unavailable.
In Q1 2016, 93.6% of resources targeted by #DDoS attacks, were located in 10 countries #KLreport
Tweet
Considering the number of attacks on Kaspersky Lab resources in the first quarter of 2016, the “cream” of the cybercriminal community has gone back to the good old methods of attacks at the application level. Already in the first quarter of this year, we combated several times more HTTP(s) attacks than we did in the whole of 2015. Interestingly, there were several application-layer attacks performed simultaneously against a number of Kaspersky Lab resources. The strength of the DDoS resources was spread between several targets, reducing the effect on each target. This is most probably because the aim was not to disrupt Kaspersky Lab’s sites but to test tools and to see how we responded. The longest attack of this type lasted less than six hours.
We can assume that the proportion of Data Link layer attacks will gradually decline, and application-layer and multi-layer attacks (a combination of hardware and application-layer attacks) will come to the fore.
Powerful UDP amplification attacks came into general use a few years ago and are still a favorite tool of cybercriminals. The reasons for their popularity are clear: they are relatively easy to perform, they can be very powerful with a relatively small botnet, they often involve a third party, and it is extremely difficult to detect the source of the attack.
Although in Q1 of 2016 our Kaspersky DDoS Prevention service continued to combat UDP amplification attacks, we believe that they will gradually disappear. The once daunting task of combining the efforts of Internet providers and IT security companies to effectively filter the junk traffic generated by UDP attacks is almost solved. Having faced the risk of their main channels being clogged up due to large volumes of UDP packets, providers have acquired the necessary equipment and skills and cut this traffic off at the root. This means amplification attacks on a Data Link Layer are becoming less effective and, as a result, less profitable.
In Q1 2016, the largest numbers of #DDoS attacks targeted victims in #China, the #USA & #SouthKorea #KLReport
Tweet
To execute application-layer attacks on web services, large botnets or several high-performance servers and a wide output channel are required, as well as thorough preparatory work to study the target and find its vulnerabilities. Without this, they are ineffective. If the application-layer attack is carried out properly, it is difficult to counter it without blocking access to legitimate users – malicious requests look authentic and every bot faithfully fulfills the connection procedure. The only anomaly is the high demand for the service. We registered these sorts of attempts in the first quarter. This suggests that the DDoS market has developed so that complex, expensive attacks are becoming cost-effective, and better qualified cybercriminals are trying to make money using them.
Moreover, there is a real danger of these methods being used by cybercriminals en masse – the more popular the technique, the more tools are offered for it on the black market. And if application-layer attacks really do become widespread, we should expect to see a growth in the number of customers for this type of DDoS attack and more competent attackers.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience in combating cyber threats, including DDoS attacks of various types and levels of complexity. The company’s experts monitor botnet activity with the help of the DDoS Intelligence system.
The DDoS Intelligence system (part of Kaspersky DDoS Protection) is designed to intercept and analyze commands sent to bots from command and control (C&C) servers, and does not have to wait until user devices are infected or cybercriminal commands are executed in order to gather data.
This report contains the DDoS Intelligence statistics for the first quarter of 2016.
In the context of this report, a single (separate) DDoS attack is defined as an incident during which any break in botnet activity lasts less than 24 hours. If the same web resource was attacked by the same botnet after a break of more than 24 hours, this is regarded as a separate DDoS attack. Attacks on the same web resource from two different botnets are also regarded as separate attacks.
The longest #DDoS attack in Q1 2016 lasted for 197 hours (or 8.2 days) #KLreport
Tweet
The geographic distribution of DDoS victims and C&C servers is determined according to their IP addresses. In this report, the number of DDoS targets is calculated based on the number of unique IP addresses reported in the quarterly statistics.
It is important to note that DDoS Intelligence statistics are limited to those botnets that were detected and analyzed by Kaspersky Lab. It should also be highlighted that botnets are just one of the tools used to carry out DDoS attacks; therefore, the data presented in this report does not cover every DDoS attack that has occurred within the specified time period.
Q1 Summary
- In Q1, resources in 74 countries were targeted by DDoS attacks (vs. 69 in Q4 of 2015).
- 93.6% of the targeted resources were located in 10 countries.
- China, the US and South Korea remained the leaders in terms of number of DDoS attacks and number of targets. France and Germany were newcomers to the Top 10.
- The longest DDoS attack in Q1 2016 lasted for 197 hours (or 8.2 days) which is far less than the previous quarter’s maximum (13.9 days). Multiple attacks on the same target became more frequent (up to 33 attacks on one resource during the reporting period).
- SYN DDoS, TCP DDoS and HTTP DDoS remain the most common DDoS attack scenarios, while the number of UDP attacks continues to fall from quarter to quarter.
- Overall, command servers remained located in the same countries as the previous quarter, but Europe’s contribution increased – the number of C&C servers in the UK and France grew noticeably.
Geography of attacks
In Q1 2016, the geography of DDoS attacks narrowed to 74 countries.
93.6% of targeted resources were located in 10 countries.
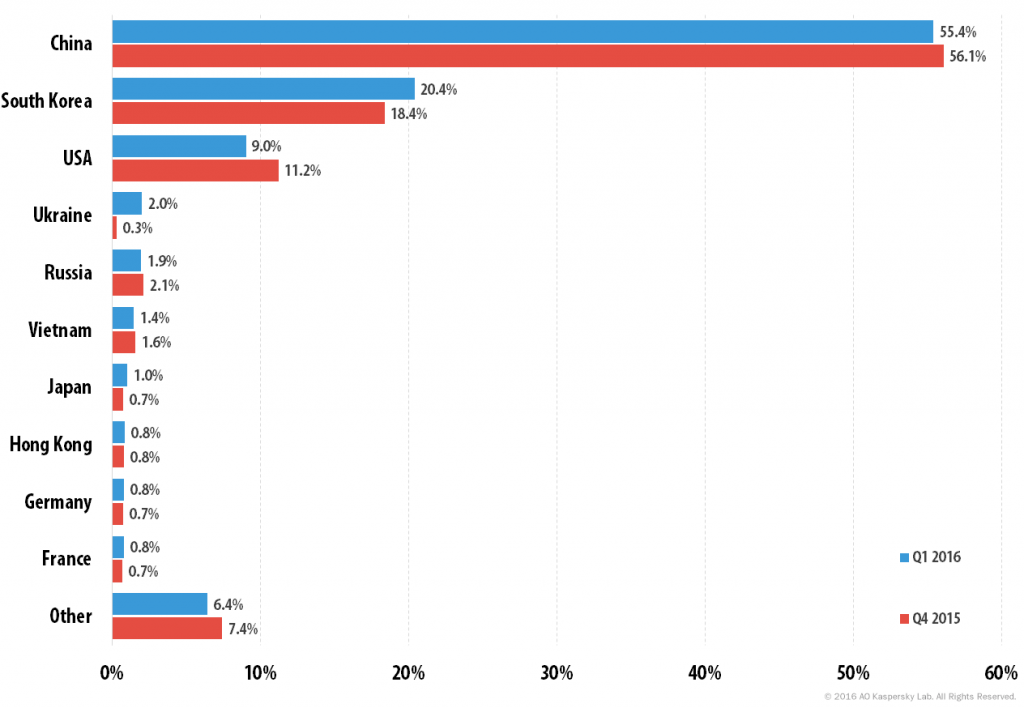
Distribution of DDoS attacks by country, Q1 2016 vs. Q4 2015
The Top 3 most targeted countries remained unchanged. However, South Korea’s share grew from 18.4% to 20.4% while the US’s contribution dropped by 2.2 percentage points. Also of note is the fact that Q1 2016 saw an increase in the number of attacks targeting resources in Ukraine – from 0.3% to 2.0%.
The statistics show that 94.7% of all attacks had targets within the Top 10 most targeted countries:
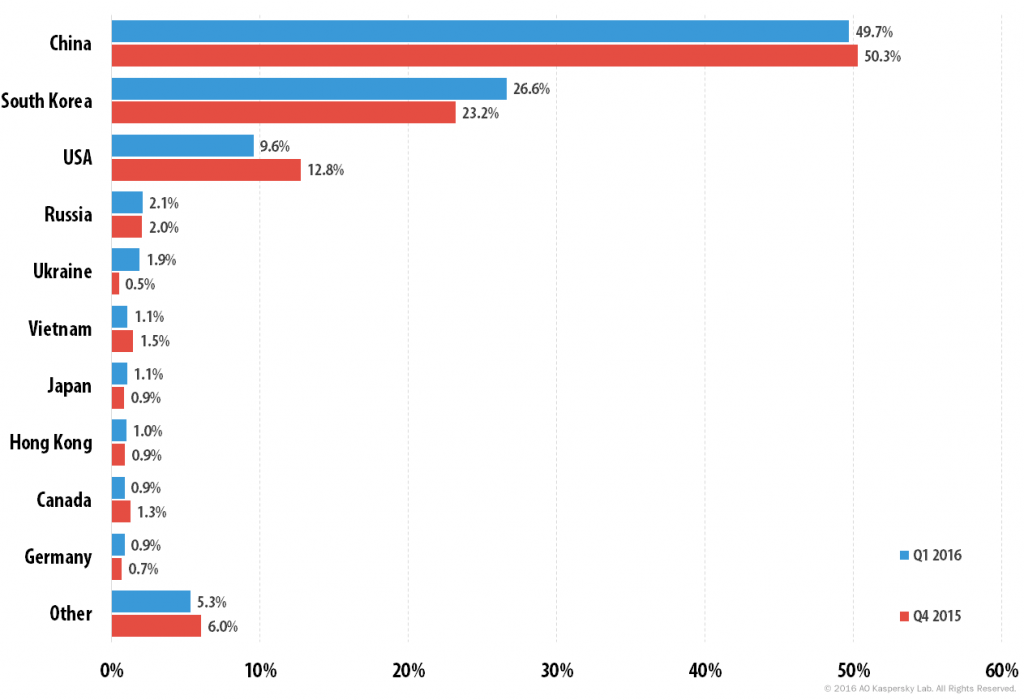
Distribution of unique DDoS attack targets by country, Q1 2016 vs. Q4 2015
The number of targets in South Korea increased by 3.4 percentage points. China’s share fell from 50.3% in Q4 2015 to 49.7% in the first three months of 2016. The percentage of DDoS attacks targeting resources in the United States also decreased (9.6% in Q1 2016 vs. 12.8% in Q4 2016). Despite the change in figures, South Korea, China and the US maintained their positions in the Top 3, coming well ahead of all other countries.
SYN #DDoS, TCP DDoS & HTTP DDoS remain the most common DDoS attack scenarios in Q1 2016 #KLreport
Tweet
The first quarter of 2016 saw Ukraine enter the Top 5 DDoS targets: its share grew from an insignificant 0.5% at the end of last year to 1.9% in Q1 2016.
Taiwan and the Netherlands’ share fell 0.8 and 0.7 percentage points respectively, meaning both dropped out of the Top 10 most attacked countries.
Changes in DDoS attack numbers
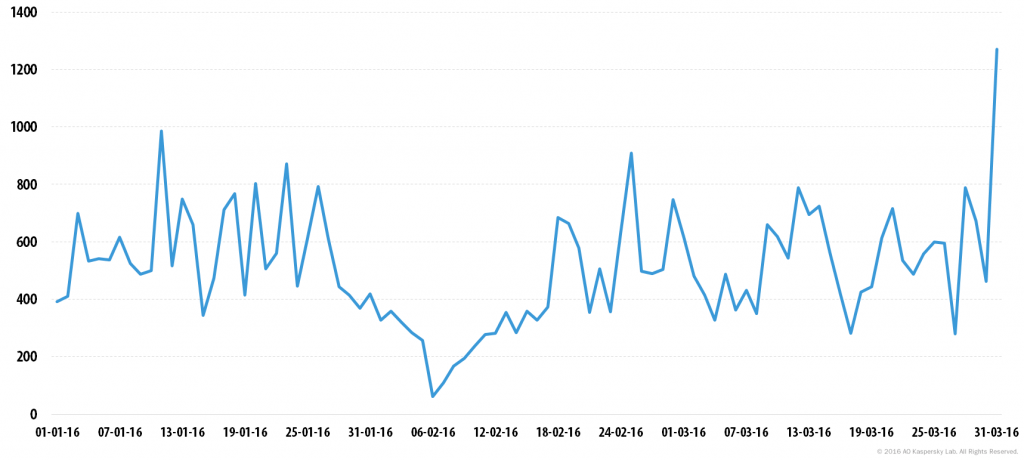
In Q1 2016, DDoS activity was distributed more or less evenly, with the exception of one peak on 6 February. The peak number of attacks in one day was 1,272, recorded on 31 March.
Number of DDoS attacks over time* in Q1 2016.
* DDoS attacks may last for several days. In this timeline, the same attack can be counted several times, i.e. one time for each day of its duration.
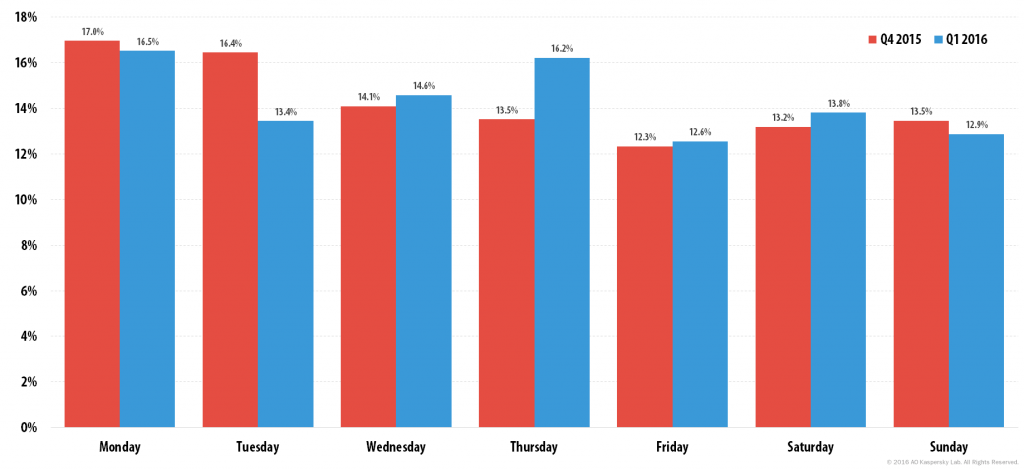
As in the previous quarter, Monday (16.5% of attacks) was the most active day of the week for DDoS attacks. Thursday moved up to second (16.2%). Tuesday, which was in second place in Q4 2015 (from 16.4% to 13.4%), became the quietest day of the week in terms of DDoS attacks.
Distribution of DDoS attack numbers by day of the week
Types and duration of DDoS attacks
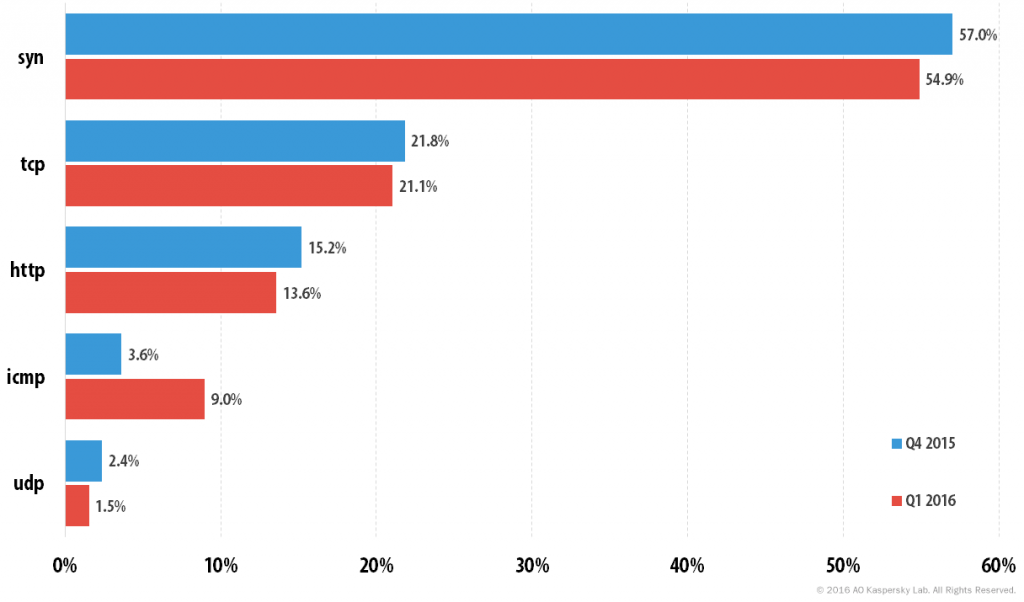
The ranking of the most popular attack methods remained constant from quarter to quarter. Those used most often were the SYN DDoS method, although its share fell compared to the previous quarter (57.0% vs 54.9%), and TCP DDoS which fell by 0.7 percentage point. The proportion of ICMP DDoS attacks grew significantly, rising to 9%; however, it did not affect the order of the Top 5.
Distribution of DDoS attacks by type
Noticeably, the figure for UDP DDoS has fallen continually over the last year: from 11.1% in Q2 2015 to 1.5% in Q1 2016.
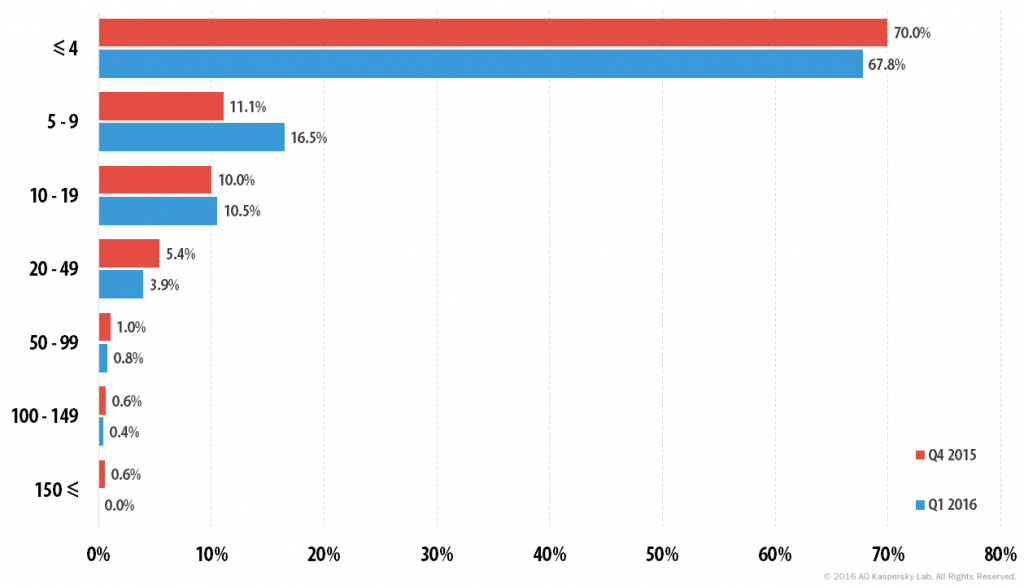
Like the previous quarter, about 70% of attacks lasted no more than 4 hours. At the same time, the maximum duration of attacks decreased considerably. The longest DDoS attack in the last quarter of 2015 lasted for 333 hours; in Q1 2016, the longest registered attack ended after 197 hours.
Distribution of DDoS attacks by duration (hours)
C&C servers and botnet types
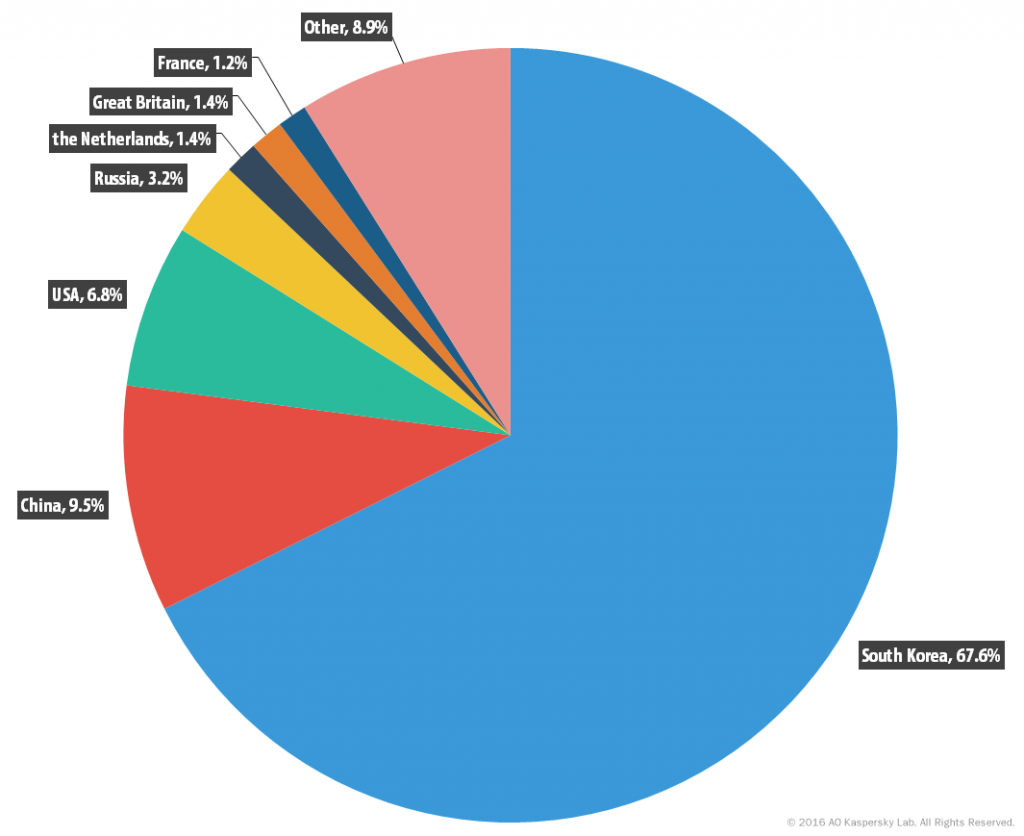
In Q1, South Korea remained the leader in terms of the number of C&C servers located on its territory, with its share growing from 59% in the previous quarter to 67.7% in the first quarter of 2016.
China came second; its share grew from 8.3% to 9.5%. As a result, China pushed the US down to third (6.8% vs 11.5% in Q4 of 2015). For the first time during the reporting period France appeared in the Top 10 countries hosting the most C&C servers. This correlates with the increased number of attacks in the country.
Distribution of botnet C&C servers by country in Q1 2016
99.73% of DDoS targets in Q1 2016 were attacked by bots belonging to one family. Cybercriminals launched attacks using bots from two different families (used by one or more botnet masters) in just 0.25% of cases. In 0.01% of cases three or more bots were used, mainly from the Sotdas, Xor and BillGates families.
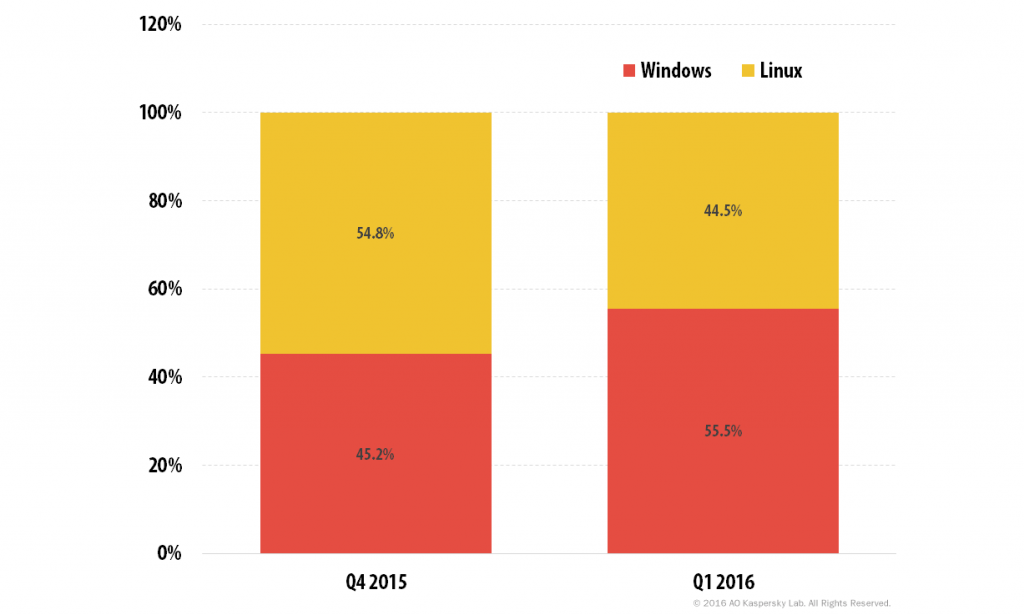
Correlation between attacks launched from Windows and Linux botnets
When it came to the number of attacks launched from Windows and Linux botnets in Q1 2016, Windows-based botnets were the clear leader. For the third quarter in a row, the difference between the share of Windows- and Linux-based attacks was approximately 10 percentage points.
Conclusion
The events of the first quarter of 2016 once again demonstrated that the attackers are not resting on their laurels and are increasing their computing resources to perform DDoS attacks. Amplification scenarios, which have de facto become the standard tool for carrying out a powerful attack, exploit vulnerabilities in new network protocols. The reasons for an attack can vary: from disrupting pre-election campaigns and attacking candidates’ resources to showdowns between competitors on the black market. There have been frequent incidents of DDoS attacks targeting the very organizations that specialize in countering them. With the spread of vulnerable devices and workstations and the abundance of configuration drawbacks at the application level, the cost of a significant attack is going down. Therefore, reliable protection is needed to ensure these attacks are financially unviable for the criminals.
Kaspersky DDoS Intelligence Report for Q1 2016


















_Ozeki
It is interesting to see that the lowest amount of DDOS attacks occurred on 06th February 2016, which marked the beginning of the weekend (Saturday) just before the-widely-celebrated-in-China, Lunar New Year on 8th February 2016.