
Kaspersky Lab has an acknowledged, long-standing expertise in counteracting DDoS attacks of different types, varying degrees of complexity and strength. This is combined with Kaspersky Lab’s real-time expert monitoring of botnet activities with the help of its DDoS Intelligence system (part of the solution Kaspersky DDoS Protection) and secures the company’s cutting-edge reputation in DDoS protection.
Q2 events
Of all Q2 2015 events in the world of DDoS attacks and tools with which to launch them, we picked out those which, in our opinion, best illustrate the main trends with which these threats evolve. Cybercriminals do the following:
- Invent and use new techniques aimed at launching more powerful attacks without increasing botnet sizes;
- Create botnets of devices connected to the Internet, and use them to carry out DDoS attacks;
- Develop DDoS modules for malware toolkits with which to carry out targeted attacks.
A DDoS Module in the Animal Farm toolkit
In March, Kaspersky Lab’s experts published the results of their research of APT attacks launched by a cybercriminals’ group dubbed Animal Farm. The cybercriminals used a number of malicious components, each one performing a specific task. One of these components was the Trojan NBot, which is designed to arrange a botnet and has the functional capability to carry out DDoS attacks. NBoT maintains a large number of distributed attack scenarios – this is evidence that the botnet has been arranged by the cybercriminals to launch large-scale DDoS attacks.
Another way to boost the power of a DDoS attack
Some scenarios rely on the exploitation of shortfalls in the configurations of various network services. These scenarios have already established their position in the repertory of techniques used by botnet owners. In Q2 2015, researchers identified another trick for boosting the power of a DDoS attack – exploiting the shortcomings in the configuration of software implementations of the multicast Domain Name System (mDNS) protocol. Under certain conditions, a service using the mDNS protocol may return a response much greater in size than the query. Thus, botnet owners can send a specially crafted query to such services, and the services would redirect it to the victim user in a much greater quantity.
The “Great Cannon”
The “Great Cannon” is a technology that was used to carry out the DDoS attack on GitHub. On 6 March, the owners of the website GreatFire.org noticed that their servers had become the target of a DDoS attack. The GitHub owners acknowledged it was a powerful DDoS attack from the servers of the search engine Baidu.
The administration of the search engine ruled out the possibility that their servers were compromised. This occasioned researchers to contemplate an attack scenario involving the use of the resources of the Great Firewall of China. This firewall was presumably used as a tool with which to implement a man-in-the-middle (MitM) attack, and redirected Chinese visitors to the attacked web resource.
This incident is yet another demonstration that not only a botnet, but just a great number of unwitting users may be the source of DDoS attacks.
A botnet made of routers
In Q2, a botnet was detected that was made of home and small-business routers – cybercriminals used it to launch DDoS attacks.
Infecting home routers is not a new technique, it is often used by cybercriminals. Ensuring the security of home communications equipment has so far remained the responsibility of its manufacturer. As practice shows, a considerable number of vulnerabilities and configuration shortcomings exist, allowing cybercriminals to seize control over routers. In this incident, the bad guys used the victim routers to launch DDoS attacks.
For cybercriminals, the option of creating botnets made of routers looks quite attractive. For these devices, it is simple to implement automated tools with which to exploit vulnerabilities; this makes the cybercriminals’ task substantially easier. In addition, very few users turn their routers off, so devices that are always on help build larger bots with members that are online pretty much all of the time.
Statistics of botnet-assisted DDoS attacks
Methodology
This report presents statistics collected by DDoS Intelligence (part of the solution Kaspersky DDoS Protection) from 1 April to 31 June 2015 (or Q2 2015), which are analyzed in comparison with the equivalent data collected within the previous 3-month period (Q1 2015).
The DDoS Intelligence system is designed to intercept and analyze the commands to bots from command and control (C&C) servers. For its operation, it does not require any user device to get infected, or cybercriminal commands to be in fact executed.
In this report, a single (separate) DDoS attack is defined as an incident during which there was no break in botnet activity lasting longer than 24 hours. Thus, if the same web resource was attacked by the same botnet after a 24-hour gap that would be regarded as two separate DDoS attacks. Attacks on the same web resource from two different botnets are also regarded as individual attacks.
The geographical distribution of DDoS victims and C&C servers is determined according to their IP addresses. In this report, the number of DDoS targets is calculated based on the number of unique IP addresses reported in the quarterly statistics.
It is important to note that DDoS Intelligence statistics are limited to those botnets that were detected and analyzed by Kaspersky Lab. It should also be highlighted that botnets are only one of the tools used to carry out DDoS attacks; thus, the data presented in this report does not cover every DDoS attack that has occurred within the specified time period.
Q2 Summary
- In Q2 2015, botnet-assisted DDoS attacks targeted victims in 79 countries across the world.
- 77% of botnet-assisted attacks targeted resources located in 10 countries.
- The largest numbers of DDoS attacks targeted victims in China and the USA. South Korea has risen to the third place.
- The longest DDoS attack in Q2 2015 lasted for 205 hours (or 8.5 days).
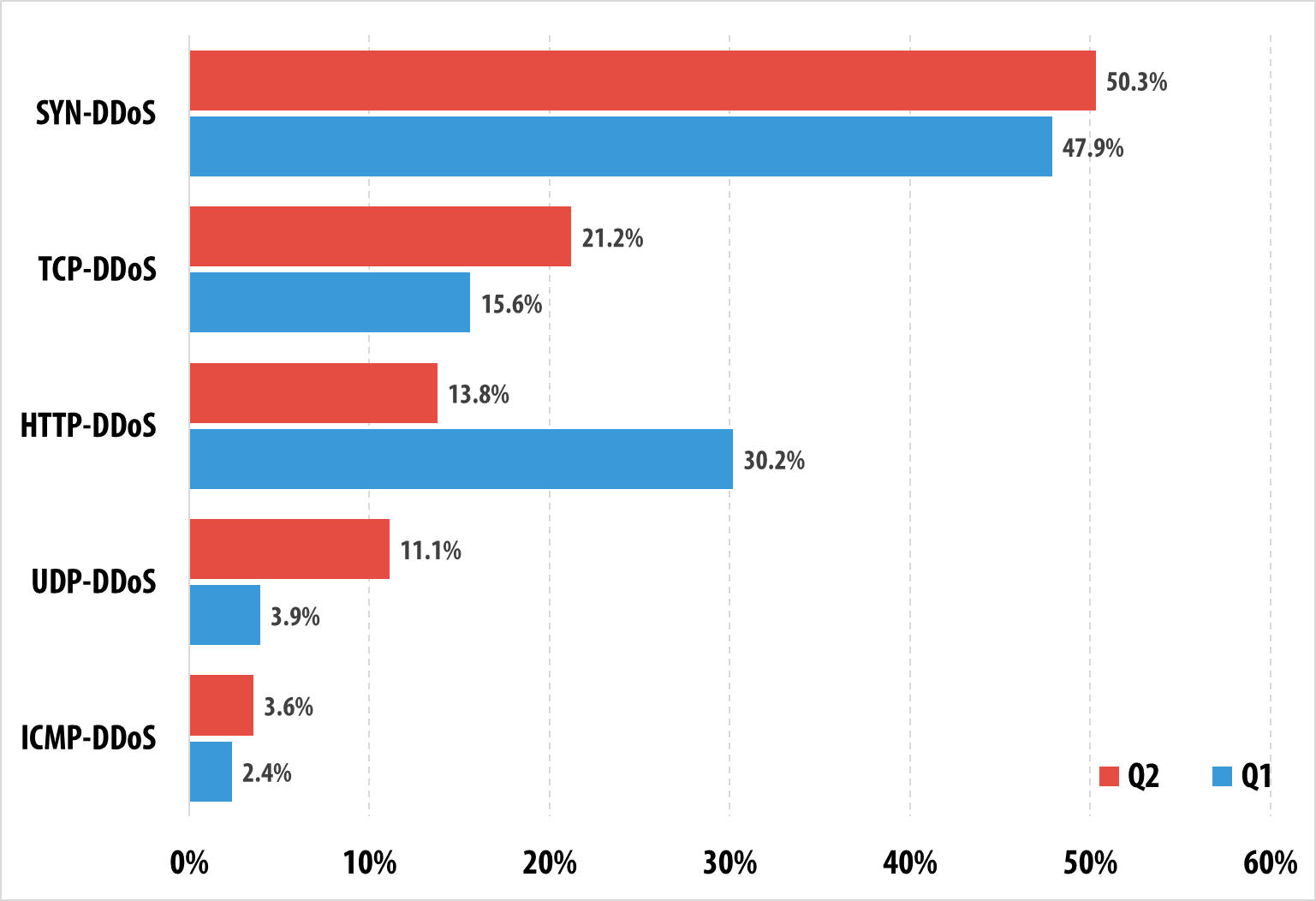
- SYN DDoS and TCP DDoS and were the most common scenarios of DDoS attacks. HTTP DDoS was displaced to the third position.
Geography of attacks
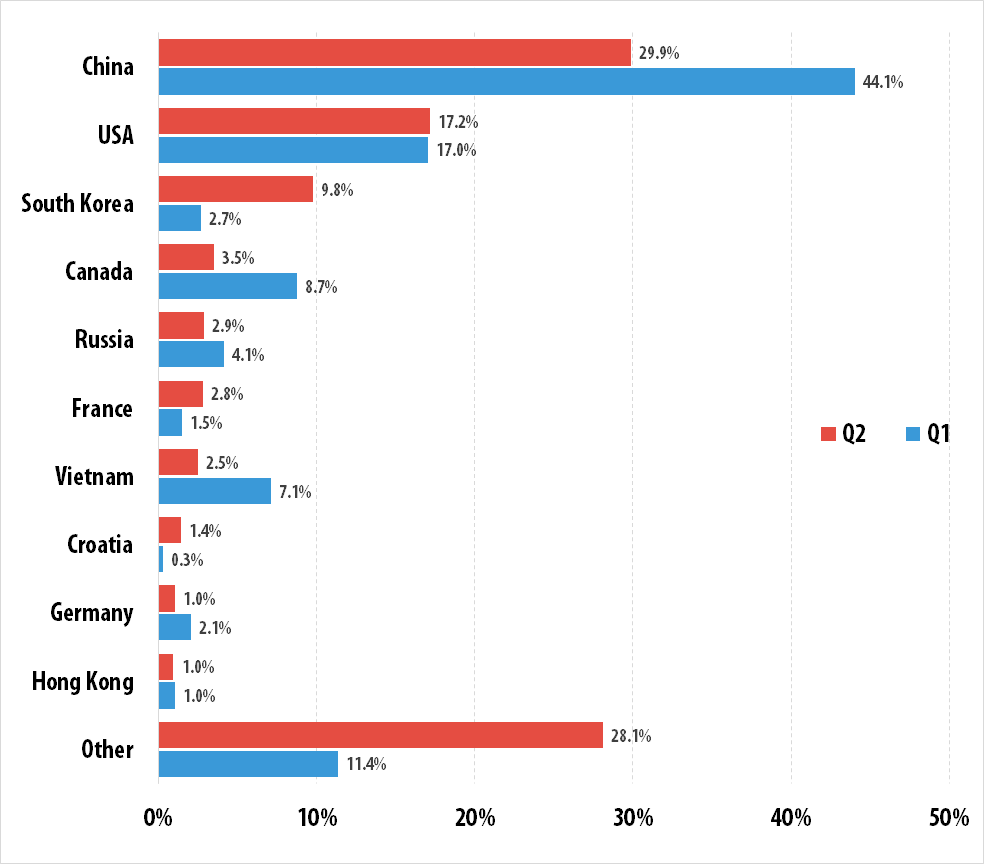
In Q2, the geography of attacked targets has somewhat expanded as compared to Q1: attacked targets were located in 79 countries around the world (against 76 countries in Q1 2015). 71.9% of attacked resources were located in 10 countries.
Distribution of unique DDoS attack targets by country, Q2 vs Q1 2015
The list of TOP 10 countries has changed only slightly (Croatia has joined, the Netherlands has left). As before, China (29.9%) and the USA (17.2%) lead the ranking; and South Korea (9.8%) has risen from the sixth to the third place, displacing Canada.
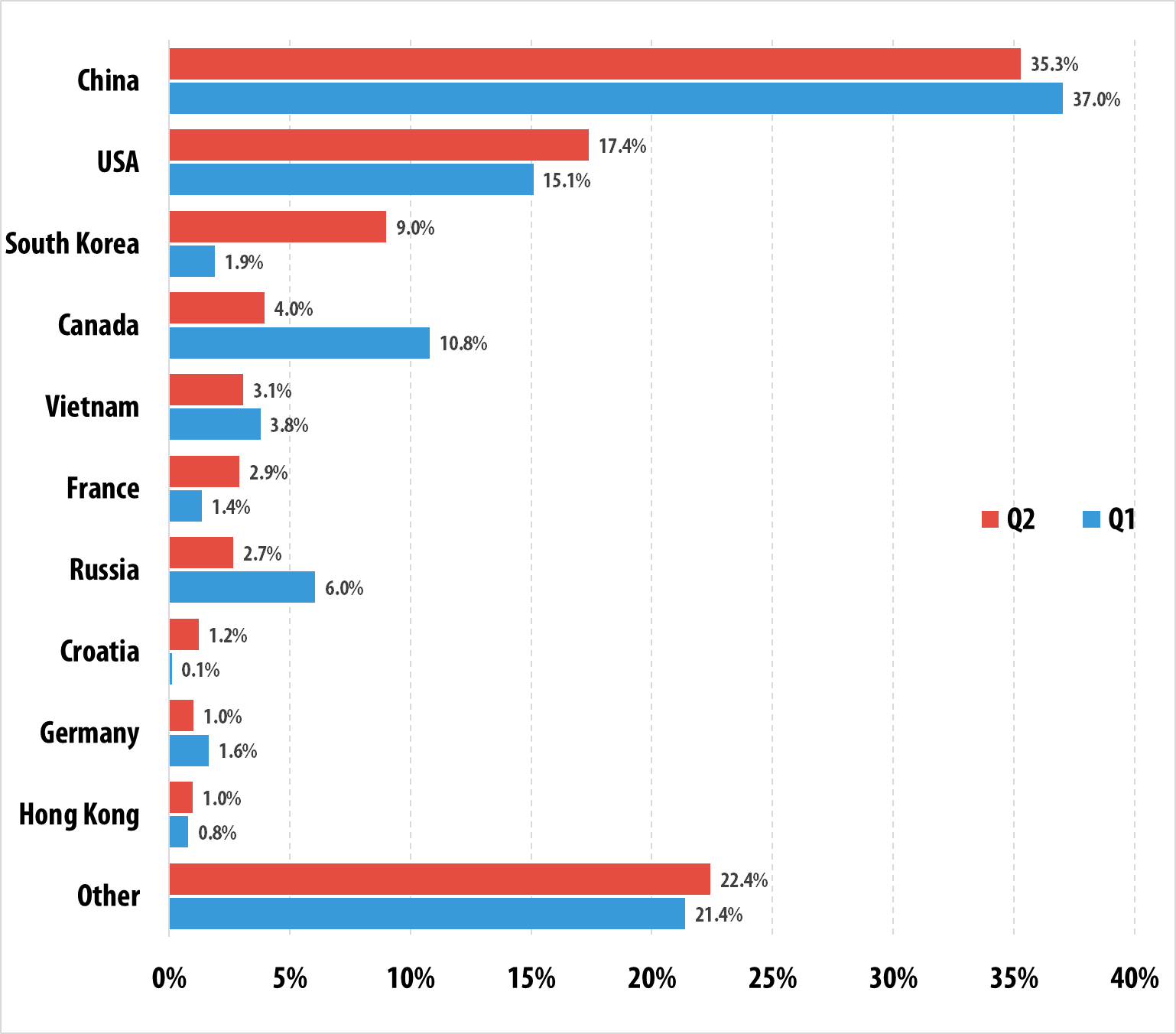
If we look at the number of reported attacks, 77.6% of all attacks had targets within the same TOP 10 countries:
Distribution of DDoS attack by countries, Q2 vs Q1 2015
This ranking is also led by China (35.3%) and the USA (17.4%).
As seen in the above charts, China has lost some of its presence in both rankings against Q1; but the shares of the USA and South Korea have increased.
Most of the world’s web resources are located in the USA and China – where there is cheap web hosting available. This explains their long-standing leadership in the rankings in terms of attack counts and the number of attacked targets.
In Q2 we observed a surge in the activity of several families of bots – they mostly attacked targets in South Korea. As a result, this country has risen to the third place in both rankings.
It is also worth mentioning that Russia and Canada have experienced lower percentages in Q2. This is especially noticeable if we look at the percentage of all attacks that targeted these two countries.
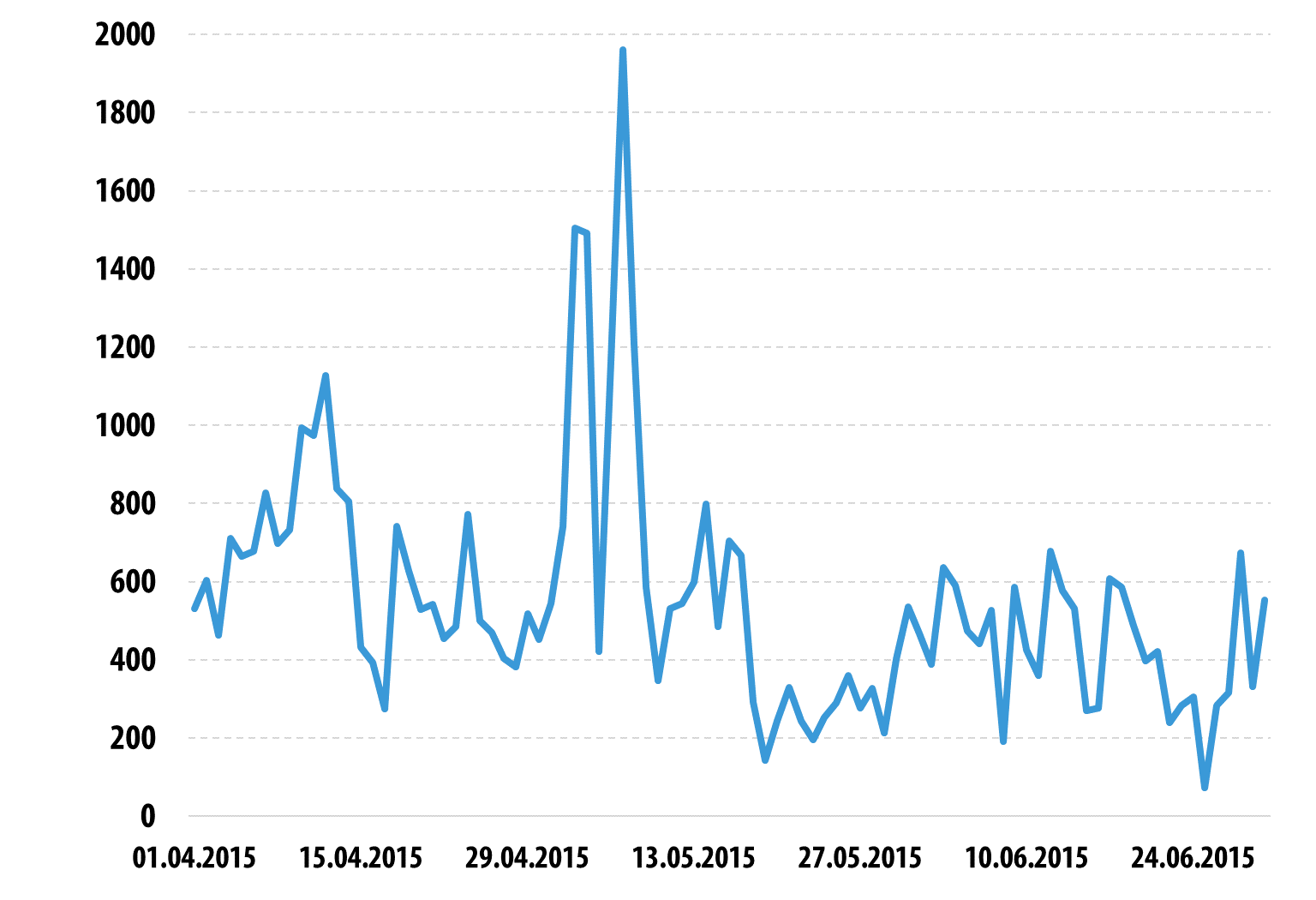
Changes in DDoS attack numbers
There was a dramatic rise in the number of DDoS attacks in the first week of May; the low was in late June.
The peak number of attacks in one day was 1960, which were recorded on 7 May. The low was on 25 June, which saw only 73 attacks.
Number of DDoS attacks over time* in Q2 2015.
*DDoS attacks may last for several days. In this plot, the same attack may be counted several times, i.e. one time for each day of its duration.
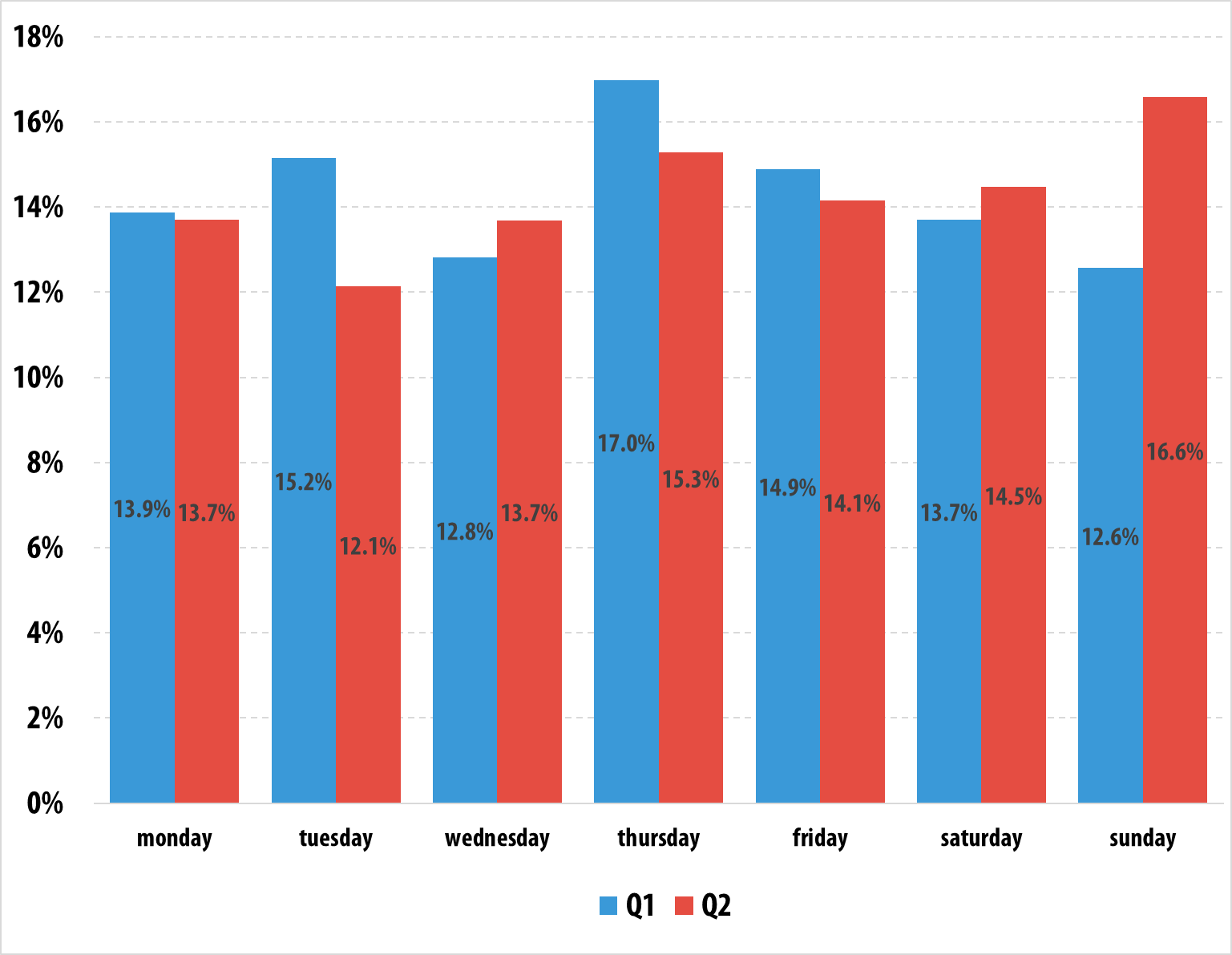
In Q2 2015, Sunday became the most active day of the week in terms of DDoS attack numbers – 16.6% of all attacks occurred on a Sunday. The lowest number of attacks were reported on Tuesdays.
Distribution of DDoS attack numbers by days of the week
On Sunday 3 May, we observed a sudden surge in the activity of one of the botnets. This suggests that on that day, the cybercriminals were possibly testing their botnet.
Types and duration of DDoS attacks
The effect of a DDoS attack is determined by its duration and scenario – these two elements define the scope of damage inflicted on the target.
In Q2 2015, 98.2% of DDoS targets (vs. 93.2% in Q1) were attacked by bots belonging to one family. In only in 1.7% of all cases the cybercriminals launched attacks using bots belonging to two different families (or the clients used the services of several attack agents). In 0.1% cases, three or more bots were used (respectively 6.2% and 0.6% in Q1).
In Q2 2015, SYN DDoS (50.3%) has remained the most popular attack method. TCP DDoS (21.2%) has returned to the second position in the ranking, displacing HTTP DDOS (13.8%).
The distribution of DDoS attacks by types
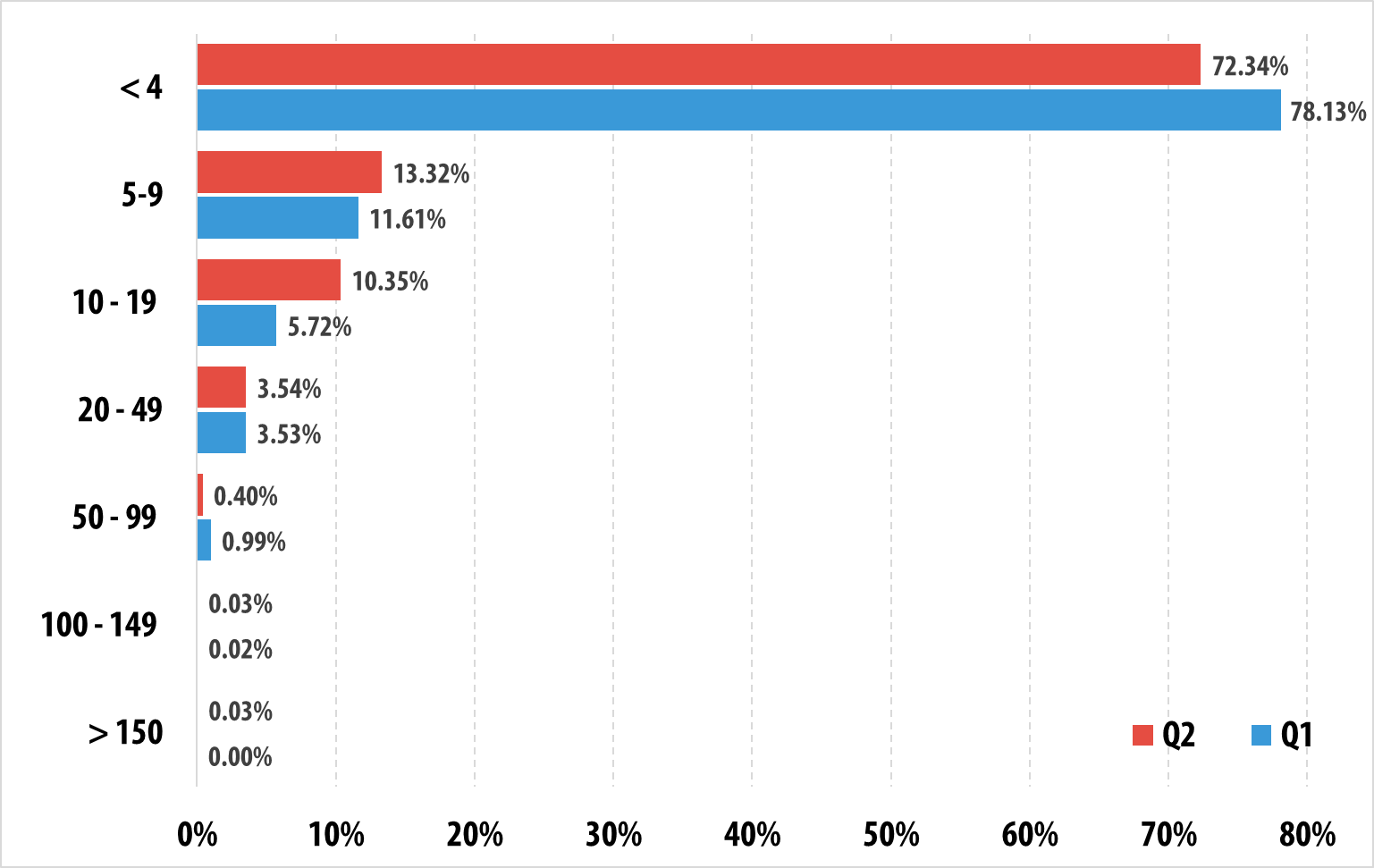
Most attacks in Q2 2015 lasted no longer than 24 hours. However, there were some attacks that lasted a week or even longer.
The distribution of DDoS attacks by duration (hours)
The longest DDoS attack in Q2 2015 lasted for 205 hours (8.5 days).
C&C servers and botnet types
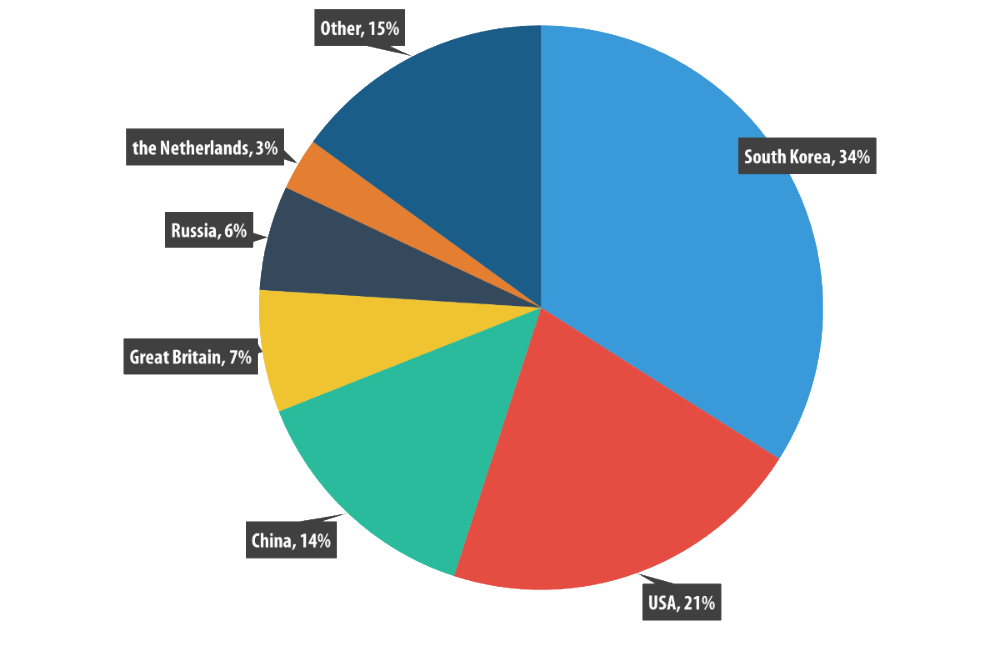
In Q2 2015, South Korea (34%) spurted into the lead in terms of the number of C&C servers located in its territory, leaving behind the USA (21%), China (14%) and the United Kingdom (7%). This was accompanied by a dramatic increase in the number of attacks and targets located in South Korea.
Distribution of botnet C&C servers by countries in Q2 2015
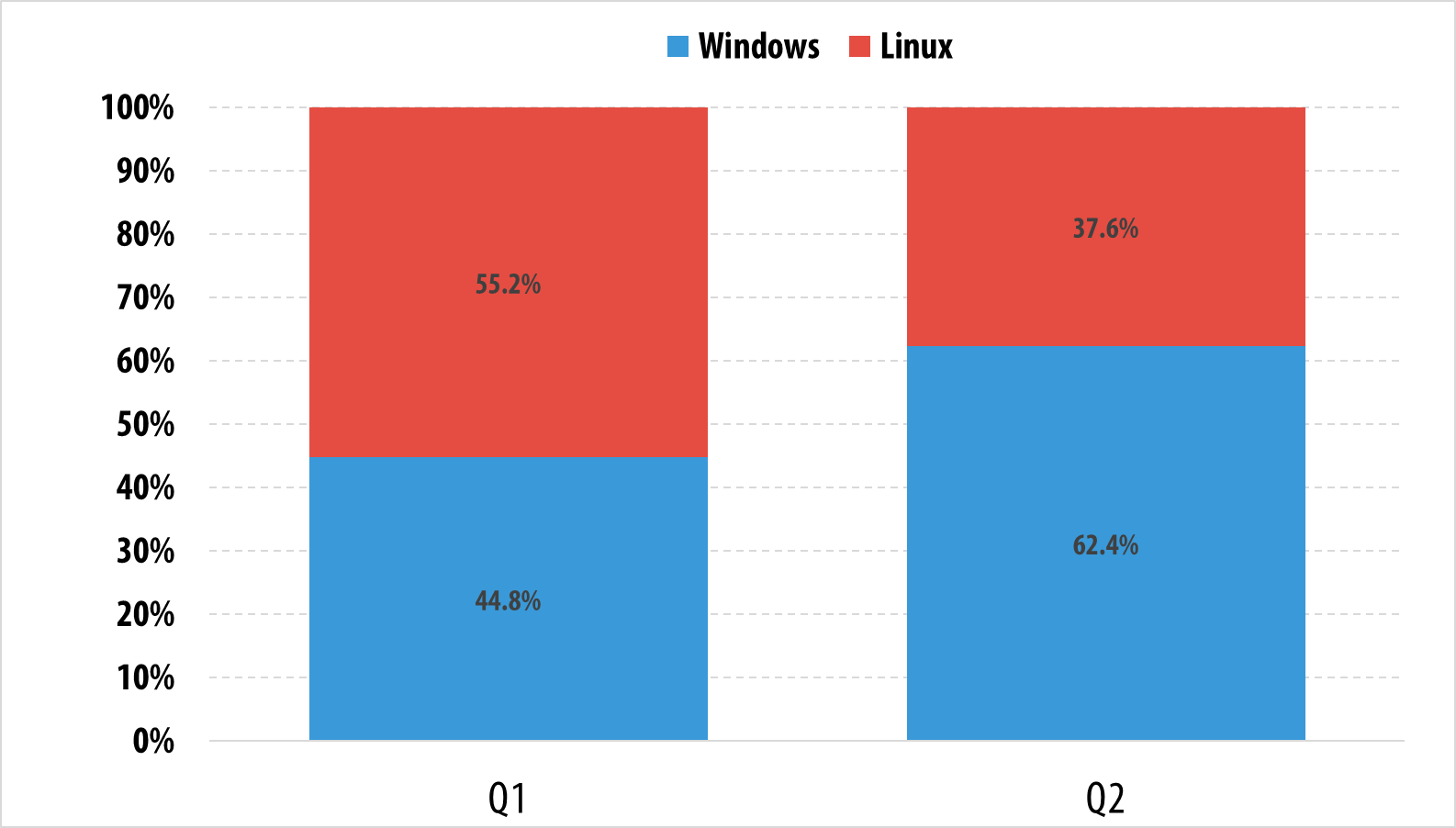
In Q2 2015, there was a dramatic growth in the number of attacks launched from bots for Windows computers. The activity of Windows bots has significantly surpassed that of Linux bots.
The ratio of the number of attacks launched from Windows and Linux botnets
The balance between the activities of Linux and Windows botnets changes all the time, since each botnet type has its advantages and disadvantages in the eyes of cybercriminals.
Linux-based botnets offer cybercriminals the opportunity to manipulate network protocols, while infected servers have high-speed Internet channels (so attacks launched from them are potentially more powerful than those from Windows botnets). However, to create and operate a Linux botnet, a cybercriminal needs to have a good knowledge of Linux as well as find a suitable bot on the black market or in free access.
Windows bots are widely available both on the black market and in free access; they are marketed using tried-and-true tools. On the other hand, malware protection is also well developed on PCs (unlike on infected Linux servers, which typically lack any security whatsoever), so botnets don’t typically live long on infected PCs.
Thus, it is easier and cheaper to use Windows bots but such a botnet does not typically last long. When there are many Windows botnets, their total attacking capacity exceeds that of infected Linux servers.
Complex attacks
The clients ordering DDoS attacks on large organizations are typically ready to pay well to see their goal achieved, so such attacks are well organized and technically complex.
While repelling one attack, Kaspersky DDoS Protection experts identified four methods employed by the attackers:
- A powerful NTP amplification;
- SSDP amplification – a relatively recent method but gaining in popularity;
- SYN flood;
- HTTP flood.
All these methods were used simultaneously and targeted several infrastructure components:
- NPT amplification and SSDP amplification attacks cause overloading of data communication channels with spurious traffic.
- SYN flood attacks target the infrastructure, create high load on firewalls and exhaust the resources of the operating system.
- HTTP flood most efficiently affects the target web server by creating a surge of requests, responding to which induces the web server to draw on a lot of hardware resources.
Should any of these components have achieved their goal, the attack would have been successful. If that had happened, the targeted organization would have suffered dramatic financial and serious reputational losses. However, it took the attackerss 20 minutes to convince themselves that the target was reliably protected, after which they the ceased the attack.
That was the most powerful of all attacks that KDP experts came across in Q2 – its peak capacity was 92 Gbit/sec. Such powerful attacks pose a threat not only to specific web resources but also to the data centers hosting them and to the infrastructures of Internet service providers, since the communication channels of upstream providers and data centers may become exhausted before the Internet channel of the actual web resource.
Conclusion
In Q2 2015, more than 77% of botnet-assisted attacks targeted web resources in ten countries across the world. The top two countries in the ranking – China and the USA – have retained their positions. The monitoring system has recorded a surge in the activity of several bot families whose targets were mostly located in South Korea – this explains the third position in the ranking this country takes in Q2.
Let us focus on the technologies carrying out these attacks. Cybercriminals who create DDoS botnets, along with creating regular botnets consisting of PCs and servers, also invest into creating botnets made of network devices – most typically routers and DSL modems. Obviously, the expansion of IoT devices and the current situation around their security adds extra impetus to the development of this type of botnet.
Cybercriminals continue to exhibit a growing persistence in carrying out DDoS attacks. In Q2, attacks lasting up to 8.5 days were observed. That said, even one short-term attack may inflict serious damage to a business both in terms of direct financial loss and reputational loss.
DDoS attacks often serve as a camouflage for a targeted attack, which could result in leaks of important data or stolen money. The DDoS module detected by Kaspersky Lab’s experts is part of the toolkit employed by the cybercriminal group Animal Farm; once again demonstrating the fact that DDoS attacks are an effective tool for cybercriminals.
All kinds of organizations become targets of DDoS attacks. Customers protecting themselves with the services of Kaspersky DDoS Protection experts include: state organizations, large financial companies and banks, mass media, small and medium businesses and even education institutions.
To protect an organization reliably from this type of threat, the organization needs to consider its defense strategy and tactics, take all required actions, and subscribe to a junk traffic filtration service. Bear in mind that when an attack starts, it will be much more difficult to escape the losses.
Kaspersky DDoS Intelligence Report Q2 2015




















Vinicius Alves
Achei muito interessante vocês da Kaspersky Lab estarem atualizando o site com informações vitais e importantes.
Os ataques são realizados todos os dias, faça chuva ou sol. Com isso, temos de estar preparado e combater diariamente essas pragas virtuais ou ataques. Esses tipos de ataques denominado como DDOS não são atuais e a cada dia os criminosos estão aprimorando as formas de atacar.
Parabéns pela postagem.