
Big fish bring big rewards for cybercriminals in 2016 but that doesn’t mean small fish are safe
In 2016 we continued our in-depth research into the financial cyberthreat landscape. We’ve noticed over the last few years that large financial cybercriminal groups have started to concentrate their efforts on targeting large organizations – such as banks, payment processing systems, retailers, hotels and other businesses where POS terminals are widely used.
For example, the financial cybercrime group Carbanak and its followers, the so-called SWIFT hackers, have been able to steal millions of dollars from its roster of victims, which has included banks and other financial institutions. The benefits of this type of cybercrime are clear – going after the big fish means criminals can reap greater rewards. Even when the costs of preparing for, and executing, attacks against large organizations like this, are high.
Despite this trend, regular users and smaller and medium businesses cannot rest on their laurels. The number of attacked users of this calibre started to grow again in 2016, following a decline in 2014 and 2015. Our report provides an overview of the types of attack users are up against as the financial cyberthreat landscape continues to evolve.
Financial phishing attacks
Financial phishing is one of the most widespread types of cybercriminal activity and in 2016 we saw it become even more prevalent, increasing both in volume and in professionalism.
For the first time in 2016, the detection of phishing pages which mimicked legitimate banking services took first place in the overall chart – as criminals sought to trick their victims into believing they were looking at genuine banking content or entering their details into real banking systems.
- In 2016 the share of financial phishing increased 13.14 percentage points to 47.48% of all phishing heuristic detections. This result is an all-time high according to Kaspersky Lab statistics for financial phishing caught on Windows-based machines.
- Every fourth attempt to load a phishing page blocked by Kaspersky Lab products was related to banking phishing.
The percentage of financial phishing detected by Kaspersky Lab in 2014-2016
Banking malware:
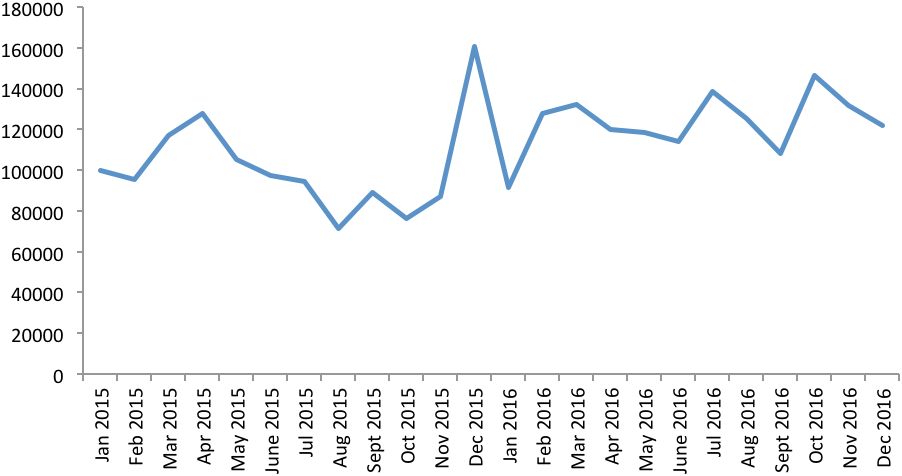
In 2016 the number of users attacked with malware targeting financial data started increasing once more, following a decrease in 2014 and 2015.
- In 2016 the number of users attacked with banking Trojans increased by 30.55% to reach 1,088,900.
- 17.17% of users attacked with banking malware were corporate users.
- Users in Russia, Germany, Japan, India, Vietnam and the US are the ones most often attacked by banking malware.
- Zbot remained the most widespread banking malware family (44.08% of attacked users) but in 2016 it was actively challenged by the Gozi family (17.22%).
The trends show us that although professional cybercriminal groups have indeed shifted a lot of their attention to targeted attacks against large companies, regular users and smaller firms are still being targeted with the help of widespread malware including Zbot, Gozi, Nymaim, Shiotob, ZAccess, Tinba, Shiz and more.
The dynamic change in the number of users attacked with banking malware 2015-2016
Android banking malware:
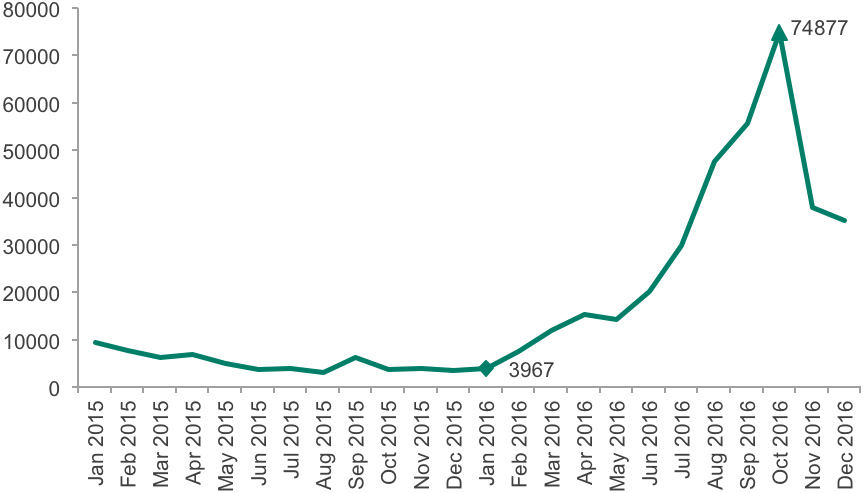
Android banking Trojans deserve a mention in our financial cyberthreat report due to some particularly interesting activity. From mid-2016 we discovered that the number of attacked Android users was increasing at an exponential rate, from just 3,967 attacked users in January to around 75,000 in October 2016.
- In 2016 the number of users that encountered Android malware increased 430% to reach 305,000 worldwide.
- Russia, Australia and Ukraine are the countries with the highest percentage of users attacked by Android banking malware.
Interestingly we discovered that just two families of malware were responsible for this sudden change: Asacub and Svpeng, which affected a large number of users, most of whom were in Russia. While Asacub was distributed actively via SMS, Svpeng was spread through Google AdSense and took advantage of a security issue in a popular mobile browser.
The change in the number of users attacked with Android banking malware 2015-2016
It’s clear that financial cybercriminals are increasingly on the look-out for new ways to exploit users and extract money from them. Owners of Android-based devices should be extremely cautious when surfing the web – especially if they have financial applications installed.
But caution is advised for everyone. As predators become more persistent and as their methods grow more convincing, corporate users and home users alike – whatever type of device they use – need to be aware of the dangers and understand how to protect themselves from this ever-evolving cyberthreat landscape.
Fill out the form below to receive the full text of the Financial cyberthreats landscape in 2016 report.
Financial cyberthreats in 2016
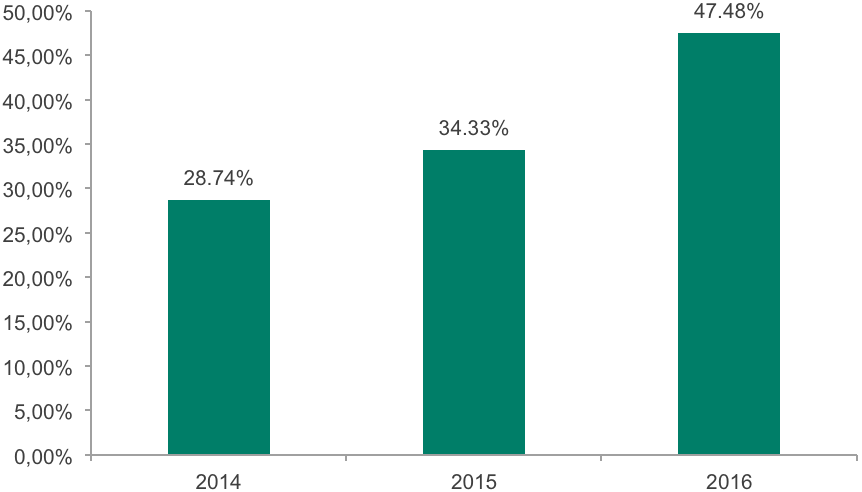




















Matthew Wu
Very comprehensive report
Dean Garnett
Thanks