
In the past year, many users have been forced to deal with an extremely aggressive multi-component system which is difficult to completely remove without professional assistance, although technically it comes with uninstallers. This is BitGuard, a system designed to change home pages and search engine results.
BitGuard is a malicious system: it modifies browser settings without the user’s knowledge, has the functionality of two Trojan families – Inject (injects its code into third-party processes) and StartPage (changes browser starting pages and search pages) – and also has Trojan-Downloader functionality (downloads malicious files from the Internet).
For convenience, in this article we use the name of one of the executable modules – BitGuard – as a generic name for an entire family of programs and modules that show similar behavior.
BitGuard is distributed together with search toolbars (MixiDJ, Delta Search, Iminent, Rubar, etc.), whose owners get paid when users follow links displayed in the modified search results. We believe that BitGuard is used by several affiliate networks at the same time.
Search toolbars
One improper method of promoting websites is to present users with search results in which the pages being promoted are displayed at the top. This involves using custom search engines and special browser add-ons – search toolbars that redirect users to pages with irrelevant search results. This scheme is used by several affiliate programs.
The scheme is implemented as follows:
- A search engine and a browser add-on with a search query entry field (search toolbar) are developed.
- An installer for the search toolbar is uploaded to a hosting provider’s servers and becomes available for download by affiliate program installers.
- A user searches for and tries to download music, software or video files, but downloads an intermediary installer belonging to an affiliate program. When the installer is executed, a search toolbar is installed (in some cases, with the user’s consent).
- Users enter the search terms in the toolbar’s text field and are redirected to the search results page of the search engine associated with the toolbar.
- The site being promoted is listed at the top of the search result pages.
- Users click on the paid links and are taken to the advertiser’s web page.
- The advertiser gains an audience.
- The search toolbar’s owners receive an income.
Additionally, paid advertising space may be available on the search results page, creating an additional source of income for the search engine’s developers.
Depending on the affiliate program, toolbars are distributed in different ways.
In most cases, search toolbars are distributed via websites offering free software – they can be bundled either with a stub installer package or with legitimate freeware programs.
For example, a certain organization might create a website serving as a platform used by freeware and shareware developers to distribute their applications. As a rule, the same installer is used for all applications distributed through the site. It includes a browser search add-on, which will be installed on the user machine when installing applications from the site. This will earn the platform’s owners commission from the affiliate network’s owners.
In this distribution scheme, a user downloads the installer for an application and launches the installation process. In some cases, the installer will download legitimate software; in some it will just imitate the installation of a useful program. As part of the installation process, the user is offered to install a toolbar.
A search toolbar can also be downloaded and installed directly, not as an addition to a third-party installer. Any webmaster can download a toolbar constructor and configure additional functionality. A completed search toolbar is uploaded to the website for users to download and the webmaster is paid by the affiliate network’s owners every time the toolbar is downloaded.
Since in this case users have to download the search toolbar on their own, the owners try to attract potential ‘customers’ with nice-looking web pages from which the toolbar can be downloaded, as well as big promises about the toolbar’s functionality (easy to use, reliable, ‘ultimate online search experience’, ‘ the best of what the web has to offer’, etc.).
Toolbar installation
elow, we demonstrate the toolbar installation process using the Delta Search Toolbar and Mixi.DJ as examples. Both toolbars belong to the same affiliate program and often use the same storage (set of servers) for their components. The toolbars are distributed via different websites, including mixi.dj anddeltasearchtoolbar.loyaltytoolbar.com.
After the installer is launched, the toolbar installation window opens.

Delta Search Toolbar installer window
To minimize the chances of the user skipping the installation of additional software, the Skip button is made all but invisible:
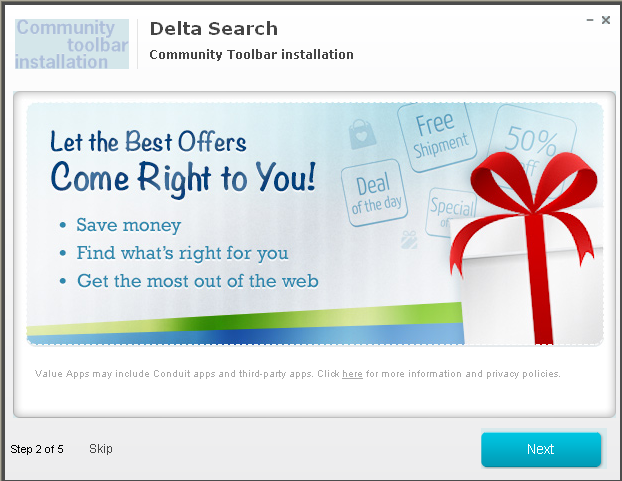
Delta Search Toolbar installer window
The Mixi.DJ installer’s interface (button proportions, fonts, installation sequence) is similar to that of the Delta Search installer, indicating that these installers and toolbars may have the same owner.
As we can see, the toolbar owners use a variety of tricks to get users to install the software on their computers.
However, any software which redirects to sites that do not offer anything useful will be treated as undesirable by users and be removed. This is why toolbars are bundled with modules designed to prevent the user from modifying browser settings once the search toolbar is installed. In this way, toolbar owners make their victims visit the target pages with the links being promoted – even when the toolbar itself has been removed.
BitGuard is one such module. Its function is to keep changing configurable addresses used by the browser (including the home page and the search page addresses) to those of pages with irrelevant search results containing links to the sites promoted using the toolbar.
BitGuard installation
BitGuard can be downloaded with any toolbar associated with an affiliate program. The installation is performed using a single installer, with the toolbar installed first and BitGuard installed after it (as part of the same installation process).
The user is not notified of this action – BitGuard is installed and launched without the user’s knowledge or consent. The address and name of the folder in which the components are installed can be different each time (e.g., “BitGuard”, “Browser Defender”, “BProtect”, etc.).
The name of the executable file that is installed depends on the installer and the toolbar version. For example, Delta Search Toolbar launches the application as browserprotect.exe.
Examples of possible paths to the BitGuard application folder are shown below:
…appdatalocaltempnsv96a4.tmp
…local settingstempnsi19.tmp
The component pack usually includes:
- the main executable module (it can have one of the following names: browserprotect.exe, bprotect.exe, bitguard.exe, browserdefender.exe, etc.);
- a library used to inject code into other processes (browserprotect.dll, browserdefender.dll, bprotect.dll, bitguard.dll, etc.);
- a settings file containing encrypted links to target search pages and update files (BitGuard receives settings from the installer and they usually match the settings for the toolbar installed by the same installer);
- scripts for Firefox or Chrome extensions (depending on the version).
The library and executable module are signed with a “Performer Soft LLC” signature issued to ForwardTech Inc. The signature has now been revoked and is not treated as trusted by Kaspersky Lab antivirus products.
After being first launched, the executable module installs itself and related components in the Application Data folder. The EXE-файл can rename itself to browserprotect.exe, browserdefender.exe or another name, depending on its version. It does the same to other components:
browserprotect2.6.1249.132{c16c1ccb-7046-4e5c-a2f3-533ad2fec8e8}browserprotect.exe
browserprotect2.6.1249.132{c16c1ccb-7046-4e5c-a2f3-533ad2fec8e8}browserprotect.dll
browserprotect2.6.1339.144{c16c1ccb-7046-4e5c-a2f3-533ad2fec8e8}browserprotect.settings
It should be noted that the original toolbars can be removed in the standard way, but BitGuard is extremely difficult to uninstall without additional tools (such as an antivirus product or a dedicated utility designed to remove unwanted browser add-ons). The application’s operation is not dependent on the presence of the toolbar in the system. All it has in common with the original search add-on are the settings. The folder containing BitGuard modules also contains a fake uninstaller (uninstall.exe), which in fact is an exact copy of browserprotect.exe. In reality, the entire removal process involving the fake uninstaller consists of removing BitGuard from the installed programs list without physically removing any objects from the system.
Registering in the system and preparing for operation
After copying files, some browserprotect.exe versions can register themselves as a Windows service, enabling them to load before winlogon.
Next, browserprotect.exe creates a task to launch itself using standard Windows Task Scheduler functionality.
system32schtasks.exe”,””system32schtasks.exe” /delete /f /tn “BrowserProtect”
system32schtasks.exe” /delete /f /tn “BrowserProtect”
system32schtasks.exe” /create /tn “BrowserProtect” /ru “SYSTEM” /sc minute /mo 1 /tr
“system32sc.exe start BrowserProtect” /st 00:00:00
system32schtasks.exe”,””$system32schtasks.exe” /create /tn “BrowserProtect” /ru “SYSTEM” / sc minute /mo 1 /tr “system32sc.exe start BrowserProtect” /st 00:00:00
The BitGuard system stores target URLs used to replace the start page and search page addresses. The addresses are stored in encrypted form in the file browserprotect.settings, as well as in the application’s own registry keys.
“hkcusoftware5e2d9dce63abf472.6.1339.144” -> “iexplore homepages” ->home.mywebsearch.com/index.jhtml?n=77DE8857&p2=^Z7^xdm354^YY^in&ptb=F2FA09DD-6451-49C9-AF7B-B9E9D2D44840&si=124514_race_gcIND
“hkcusoftware5e2d9dce63abf472.6.1339.144” -> “firefox homepages” -> “home.mywebsearch.com/index.jhtml?ptb=F2FA09DD-6451-49C9-AF7B-B9E9D2D44840&n=77fcbc67&p2=^Z7^xdm354^YY^in&si=124514_race_gcIND”, “home.mywebsearch.com/index.jhtml?ptb=F2FA09DD-6451-49C9-AF7B-B9E9D2D44840&n=77fd0772&p2=^Z7^xdm354^YY^in&si=124514_race_gcIND”
“hkcusoftware5e2d9dce63abf472.6.1339.144” -> “firefox keywords” -> “search.mywebsearch.com/mywebsearch/GGmain.jhtml?st=kwd&ptb=F2FA09DD-6451-49C9-AF7B-B9E9D2D44840&n=77fcbc67&ind=2013052007&p2=^Z7^xdm354^YY^in&si=124514_race_gcIND&searchfor=”
“hkcusoftware5e2d9dce63abf472.6.1339.144” -> “firefox search engines” -> “My Web Search”
Monitoring operations
The executable module (browserprotect.exe) registers the path to browserprotect.dll library in registry key AppInit_DLLs, enabling the library to be injected into any process launched on the user machine. When loading, the library identifies the parent process and hooks a number of functions, including reading from and writing to a file. BitGuard monitors the file operations of all processes, but only shows interest in operations involving browser settings files.
When a read/write operation is performed, the library usually checks for any changes to the settings of the browsers installed in the system. For example, when Chrome is exiting, it saves the current configuration to a file. BitGuard detects the operation, immediately opens the configuration file and inserts the addresses of the target search pages. The same will happen if the user attempts to change the browser’s configuration manually using text editing software.
The library supports many popular browsers (Internet Explorer, Chrome, Mozilla, Opera, etc.) and uses an individual approach for each of them. For example, when it is closing, Chrome saves data on the tabs that were open at that time. BitGuard can register the target search page as the start page or as the last tab opened.
Updating settings
The hook function regularly checks for updates to components and settings (the main executable module does this from time to time, as well). All the content is downloaded from Amazon Web Services and/or Cloudfront. Settings are saved as encrypted files named dwl.bin and bl.bin. Links used for downloads are not stored explicitly but are generated from encrypted fragments in the course of the application’s operation.
Link examples:
http://protectorlb-1556088852.us-east-1.elb.amazonaws.com/service/dwl.php
http://protectorlb-1556088852.us-east-1.elb.amazonaws.com/service/kbl.php
Extending the functionality and downloading additional components
The system can download additional modules to keep itself from being removed/damaged and to extend the set of methods used when working with different browsers.
One example of additional software that can be downloaded is modules for Firefox. Below we discuss how this works.
BitGuard regularly communicates with the server, attempting to download a text file containing links to archives with additional modules. A link to the text file is generated dynamically based on string elements stored in the library’s resources:
d1js21szq85hyn.cloudfront.net/ib/138/fflist.txt.Note that each version of BitGuard uses its own values instead of ib and 138 in the URL string. As a result, if the text file is successfully downloaded, each BitGuard version receives its own set of links to updates. The contents of the text file are as follows:
3;http://d1js21szq85hyn.cloudfront.net/ib/154/3.7z
5;http://d1js21szq85hyn.cloudfront.net/ib/154/5.7z
6;http://d1js21szq85hyn.cloudfront.net/ib/154/6.7z
7;http://d1js21szq85hyn.cloudfront.net/ib/154/7.7z
8;http://d1js21szq85hyn.cloudfront.net/ib/154/8.7z
9;http://d1js21szq85hyn.cloudfront.net/ib/154/9.7z
10;http://d1js21szq85hyn.cloudfront.net/ib/154/10.7z
11;http://d1js21szq85hyn.cloudfront.net/ib/154/11.7z
12;http://d1js21szq85hyn.cloudfront.net/ib/154/12.7z
13;http://d1js21szq85hyn.cloudfront.net/ib/154/13.7z
14;http://d1js21szq85hyn.cloudfront.net/ib/154/14.7z
15;http://d1js21szq85hyn.cloudfront.net/ib/154/15.7z
16;http://d1js21szq85hyn.cloudfront.net/ib/154/16.7z
18;http://d1js21szq85hyn.cloudfront.net/ib/154/18.7z
Each archive is numbered according to the number of the corresponding link on the list and contains a version of the library designed for a specific Firefox version. For example, the 16th archive contains a library named “bprotector-16.0.dll” .
BitGuard chooses the relevant link to an add-on module, downloads and registers it. This provides BitGuard with additional tools for working with Firefox.
Sometimes, BitGuard also downloads additional components (if available) which enable it to download updates from domains other than AmazonAws or Cloudfront.

Installation and behavior of the application on the user machine
Example of an add-on module
Trojan-Downloader.Win32.MultiDL.c, a Trojan discovered on July 9, 2013, updates browserprotect.dll from alternative servers. This software has been actively distributed: we blocked about 500,000 attempts to infect user machines in July 2013 alone. With time, its popularity waned – the number of infection attempts blocked in January 2014 did not exceed 26,000. In total, from July 2013 to January 2014 infection attempts were blocked on 982,950 user machines.
The file is saved on user machines in a bundle with the NSIS (Nullsoft Scriptable Install System) installer. It is downloaded by BitGuard from AmazonAws (e.g., protectorlb-1556088852.us-east-1.elb.amazonaws.com) and is saved in a temporary folder with the name setup_fsu_cid.exe.
Next, BitGuard launches a silent install process (no windows are displayed):
“…setup_fsu_cid.exe” /S
The installer contains two programs. As a rule, one has nothing to do with the DLL update scheme described above. In the case of the MultiDL.c variant, this is File Scout. The application is never found separately from the installer and is probably used to create an illusion that some useful program is being installed. The program offers details on unknown file formats, but it does not include an offline file format database, redirecting instead to a third-party website (it is not impossible that somebody is paying for the redirect, too).
The second application is a fake Adobe Flash Player, which is actually used to download the library that is part of the BitGuard system. The Trojan is masked as Adobe Flash Player Update Service version11.6 r602. First, installer setup_fsu_cid.exe unpacks the executable (.exe) file of the fake player in a temporary folder, naming the file with a short name, e.g., usvc.exe (C:userstestwo~1appdatalocaltempnsy5f4f.tmpusvc.exe).
Next, the executable module is launched. It moves itself to the following folder:C:WindowsSyswow64macromedflashflashplayerflashplayerupdateservice.exe and registers a task to have itself launched, using the standard Windows Task Scheduler service (i.e., it uses the same approach as BitGuard).
…system32schtasks.exe” /create /tn “AdobeFlashPlayerUpdate” /ru “SYSTEM” /sc hourly /mo 1 /tr “…system32flashplayerupdateservice.exe /w” /st 00:00:0
After this, the Trojan begins to download DLL updates. Each MultiDL modification downloads from several domains. Links to updates are different from those we see in BitGuard (AmazonAws and Cloudfront are not used). The list of sites varies depending on the modification. Links are stored using the same method as in browserprotect.dll – as encrypted fragments. The resulting link is generated in the process of the program’s operation. Below are several examples of domains from which DLLs are downloaded:
autoavupd.net
autodbupd.net
srvupd.com
srvupd.net
updsvc.com
updsvc.net
Most of the domains were registered in Russia, although some were registered in Ukraine and the UK.
Content hosted on the servers can be unavailable from time to time. At the time of publication (March 2014), nothing could be downloaded from the sites.
Such add-on modules are used as a backup in case the library (browserprotect.dll / browserdefender.dll / bprotect.dll, etc.), which is the main BitGuard browser control tool, is removed or damaged. If the user somehow finds a way to remove the library, the backup modules will download it again and the browser settings modification process will continue.
Conclusion
BitGuard modifies browser settings without the user’s knowledge, injects its code into third-party processes, changes browser start and search pages and downloads malicious files from the Web. This entire set of malicious functions is used for financial gain: BitGuard owners are members of an affiliate network which uses improper methods to promote websites (links to the web pages being promoted are displayed among the top search results).
We believe that the BitGuard owners and the search engine and toolbar owners are different people/organizations. Somebody gets paid for supplying an SDK or engine used to maintain the browser settings on user machines in a state that is advantageous for search engine owners.
First of all, the parametrization logic implemented in BitGuard hints at this: the system itself does not ‘know’ which search engine should be enabled in the browser – the page addresses are listed in the BitGuard configuration file, which comes with the toolbar. Secondly, there are significant differences between some toolbars, but at the same time there are no conceptual differences between BitGuard components.
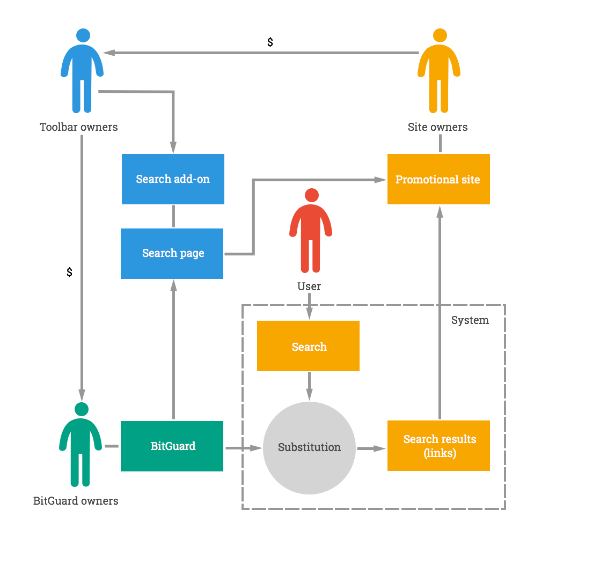
Overall scheme for making money from BitGuard installations
BitGuard can be downloaded with any search toolbar associated with an affiliate network, and toolbars have many sources of distribution. This explains the large number of infected computers across the globe:

Geographical distribution of attempts to infect computers with BitGuard components
Starting from August 25, 2013, BitGuard files have been blocked on computers of 3.8 million users. Given that the owner of a website being advertised pays an average of 2 to 10 cents for each target page hit, a rough estimate of affiliate program participants’ income can be made.
We detect:
BitGuard components as:
Trojan.Win32.Bromngr and Trojan-Downloader.Win32.MultiDL
Search toolbars as:
not-a-virus:PDM:WebToolbar.Win32.Cossder
not-a-virus:WebToolbar.Win32.Dsearch
BitGuard: a System of Forced Searches




















Marc Van der Beken
How can I remove this files ?