
Introduction
In recent years, the number of malicious programs has been increasing exponentially. Even the most effective antivirus technologies developed by different vendors are not always capable of coping with this rising number of threats. While 10 or 15 years ago a detection rate of 99.9% meant that an antivirus product missed one or two malicious programs out of the 10,000 or so created that year, today the same percentage represents thousands of malware samples among millions of new malicious programs. Cybercriminals are also increasingly exploiting zero-day vulnerabilities in the software installed on target machines.
This is already forcing large companies to change their approach to security systems. In the course of their work, employees handle corporate data stored on the corporate network. As a result, gaining access to one computer on the network gives attackers a potential opportunity to gain access to the company’s trade secrets, as well. This is particularly dangerous for large companies, as it can result in the loss of millions of dollars. It is increasingly common for information security products on the corporate network to be based on an approach that is completely different from that used in antivirus solutions. The concept is quite simple: only programs included on a certain approved list are allowed to run, while all other applications are blocked. For many organizations, network security is becoming a major priority. As a result systems lose some flexibility: employees are restricted to running only approved, work-related software on their workstations. This approach is not new and is known as the Default Deny Mode or Lock-down Mode.
Default Deny solutions are often used without antivirus protection, but Kaspersky Lab experts are convinced that the most effective approach is to combine Default Deny components with antivirus components. This is due to several important factors: exploits that perform malicious actions without creating any files on the computer; macro viruses distributed in office documents (which cannot be controlled by Default Deny, since they are constantly modified); and riskware, i.e., programs that are legitimate in themselves but are specially configured by cybercriminals to perform malicious functions. For example, special settings in the configuration file can turn legitimate keypress logging programs into Trojan-Spy malware. This is why integrated protection is more effective than using a single approach.
The Default Deny approach is effective for large companies with closed infrastructure, but small companies and ordinary computer users also need reliable protection for their data. User identification data in electronic payment systems and on social networks, the computer’s hardware resources and Internet traffic are valuable and hence attract cybercriminals.
It’s important to remember that PC users want to be able to install new software and update existing programs on a regular basis, as well as downloading files from the Internet and P2P networks and viewing websites. Unfortunately, Default Deny solutions designed for the corporate market are rarely flexible enough for home-user needs. Many companies gave up the idea of using Default Deny for this very reason: the Default Deny solutions available do not provide the flexibility required by their business processes.
This paper describes the “trusted environment” concept, which combines the advantages of the protection provided by Default Deny solutions with the flexibility offered by antivirus solutions.
How Default Deny works
To find out why security systems based on the Default Deny concept are not sufficiently flexible, one needs a good understanding of their operating principles (a detailed description of the Default Deny technology is provided in a separate article).
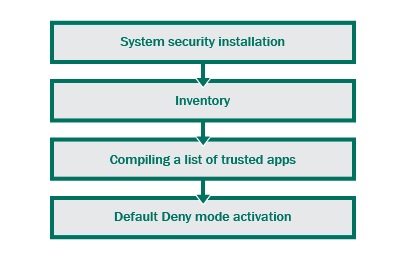
In the process of deployment, a standard Default Deny solution performs the following sequence of operations:
- makes an inventory, i.e., searches for files capable of executing code: applications, dynamic libraries and scripts;
- makes decisions on whether each of the files found can be trusted;
- activates the Default Deny mode.
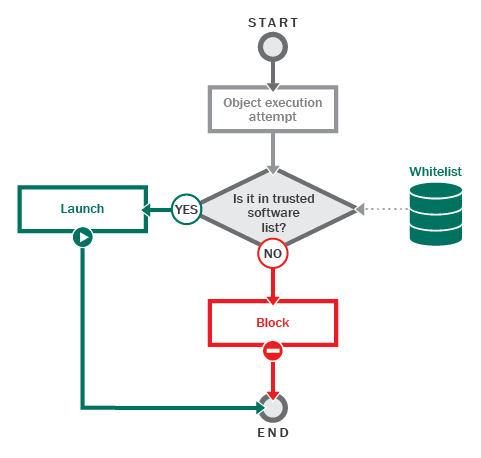
After activating the Default Deny mode, applications and scripts are executed and dynamic libraries are loaded according to the following algorithm:
- the operating system initiates the launch of an application, script or library;
- the security system checks the application, script or library against a list of trusted objects to determine whether it is trusted;
- if the object is confirmed as trusted, it is allowed to launch, otherwise it is blocked.
Denying the execution of untrusted code: no flexibility
One indisputable advantage of the Default Deny approach is that it creates an isolated system in which untrusted applications cannot be executed. The classic Default Deny mode sacrifices flexibility in favor of security. A major drawback of this approach is that it makes it impossible to install new and update existing software. This is why today’s Default Deny solutions use special categories of programs – “Trusted Updaters” and “Trusted Installers”. These programs are allowed to create other programs in the system, which inherit their trusted status.
This approach is successfully applied by organizations where the list of programs used on workstations is explicitly defined by a system administrator, who creates an isolated system from the corporate network. The system allows only listed programs to be updated or installed.
However, most information systems are open in nature and interact with each other. Each computer performs numerous tasks, the range of which can expand with time. In addition, nearly all computers have Internet access.
For home computers and for those organizations which do not strictly control the software installed on workstations, creating the trusted categories described above is clearly not enough to provide the required level of flexibility for the system.
From blocking the execution of untrusted code to maintaining a trusted environment
So how can the system be made sufficiently flexible and at the same time well-protected? One solution is to move from blocking the execution of untrusted code to maintaining a trusted environment.
So what is a trusted environment?
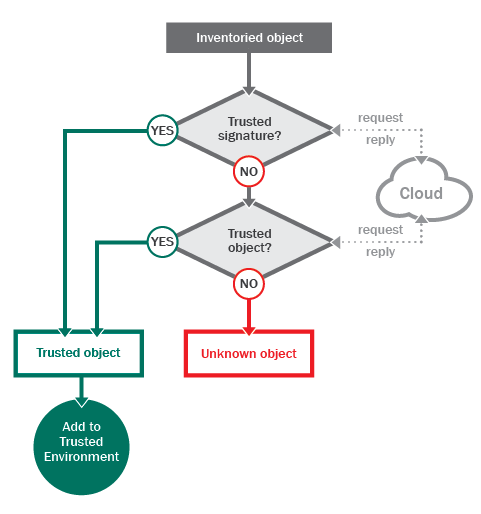
In the process of making a software inventory, a list of trusted objects (applications, dynamic libraries and scripts) which can be executed in the system is created. All other objects will be blocked from executing their code.
Where does the information on whether a file is trusted or not come from in the process of making an inventory?
Clearly, some kind of proof that a file is trusted is required. This proof comes in the form of a digital signature, which certifies that the file being verified was created by a trusted developer and has not been modified by third parties.
However, there are numerous applications created by large software vendors which do not have a digital signature. As for small software developers, they rarely ‘sign’ their products. In addition, the theft of digital certificates and their use by cybercriminals is becoming an increasingly common problem.
How does one obtain accurate information as to whether an unsigned file or a certificate used to sign a file is trusted? One solution is to use a knowledge base which contains data on all legitimate software and which is provided by a security system vendor.
Databases of trusted software are often so large and are updated so frequently that it is impossible to keep them up to date with the kind of regular updates used for antivirus database updates. This is where cloud technologies and dynamic allowlisting come in. If information about an object is required, the security system requests it from the cloud. The cloud responds with a verdict about whether the file in question is trusted or not.
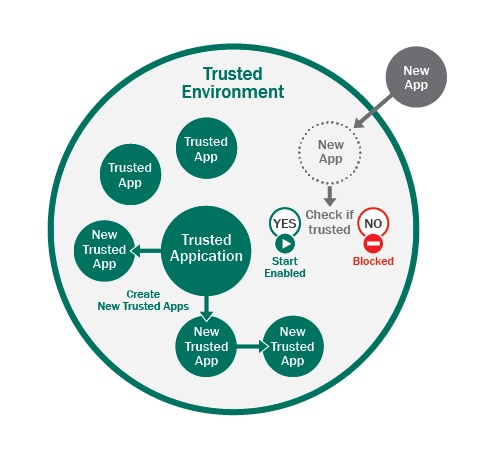
When the process of making an inventory and defining a set of trusted files is complete, all the code allowed to run in the system can be considered trusted and, consequently, the entire system is trusted.
At the same time, if a system is trusted, then, in the absence of contacts with the external, untrusted environment, trusted applications create only trusted objects without affecting the entire system’s status. This means the system as a whole can be considered a trusted environment.
Support for program installation and updates
In order to decide how the system should manage updates and the installation of new software, it is essential to understand how new applications are added to the system. In most cases, new applications are downloaded from the web or copied from removable media. As a result, a file created by a trusted application which is in contact with the external environment cannot be guaranteed to be trusted. For example, a browser is a trusted application, but it can be used to download untrusted applications from the Internet. Such applications cannot be considered trusted without additional verification. A verification algorithm which guarantees that an application is trusted is described below.
If an application is already installed in the system and is trusted, its new version downloaded from a trusted source will also be trusted by virtue of having been acquired in a trusted environment. This enables programs that are already installed in the system to update without hindrance and without affecting the system’s trusted status. In other words, updating installed software does not cause any problems.
But what about installing new programs?
The three most popular methods of installing software are:
- via a web installer
- via a single installation package
- via a fragmented installation package.
When a web installer is used, the logic of a trusted update program applies: it is sufficient for the security system to ‘know’ that the installer program is trusted and, consequently, will download updates from a trusted web resource. As a result, all the files brought into the system in the process of installing the application will be trusted according to the main property of trusted environments.
In the case of a single installation package, it is sufficient to check that the installation package is trusted. Installation packages are installed using dedicated installation programs that are part of the operating system, such as msiexec.exe. Since the application is part of the operating system, it is trusted. If an installation package used by an installer program is trusted, any files extracted from the package will not affect the environment’s trusted status, which means that they can be considered trusted.
If an installer uses several files in the process of installation, e.g., when installing software using CAB files, this scenario is also in line with trusted environment properties: if all the files used for installation are trusted, the resulting files will also be trusted.
Using trusted sources from the external environment
While it’s relatively easy to deal with installers located on the PC itself, software is often downloaded from the local network or the Internet. The security system cannot identify whether these objects are trusted. In addition, installers can access Internet resources for additional information required for installation, but accessing the network violates the basic concept of the trusted environment as it is unknown whether the network node is trusted.
The problem can be resolved as follows. The product vendor pre-defines a list of the trusted nodes (both local and on the Internet). When connecting to these nodes any application which is a part of the trusted environment remains trusted and can create trusted objects in the system.
What is the best way to create a list of trusted network nodes while ensuring that the nodes are not compromised? Each individual vendor of Default Deny solutions deals with this task according to their expertise and continuous monitoring of the network resources that have been recognized as trusted.
Maintaining the integrity of the trusted environment
After the trusted environment has been created and Default Deny is activated, it is crucial to maintain the integrity of the trusted environment. It is necessary to ensure that the existing applications are not changed and new ones do not appear while bypassing the security system.
Let us suppose that a company or a large number of PC users are using the proposed protection system. The cybercriminals are aware that these users are using new protection methods, so that common techniques to launch the malicious code will not work.
So what will cybercriminals do if they want to get hold of confidential user information or use PC resources? Obviously, in this case they will consider other ways to execute malicious code in an attempt to bypass the security system. The most dangerous alternative is to exploit vulnerabilities in the trusted software.
If a software vulnerability has been successfully exploited, the cybercriminal will be able to use the properties of a trusted environment against the security system itself: by executing malicious code within a trusted process, all the actions this code performs will be regarded as trusted. For example, when a malicious website which contains an exploit is visited, the malicious code begins to execute in the user’s browser. Since the malware is running in a trusted process, everything the browser does at this point will be allowed. However, if the exploit attempts to run a downloaded malicious file, it will be blocked. Therefore, the scope for malicious code to cause infection will be limited.
To do more damage, attackers will try to trick the security, perhaps by modifying the boot sector of the disk or installing a driver that starts before the protection system launches. The range of activities that the attacker can perform in this case is quite extensive, and all of them lead to the loss of user data or some other misuse of the computer.
How can this be stopped? When observing trusted programs, it is clear that most applications have a rather limited working logic and potentially dangerous activities are not included. For instance, a browser’s working logic is to display webpages and download files. Actions such as changing system files or disk sectors are inherently alien to the browser. A text editor is designed to open and save text documents on a disk, but not save new applications onto the disk and launch them.
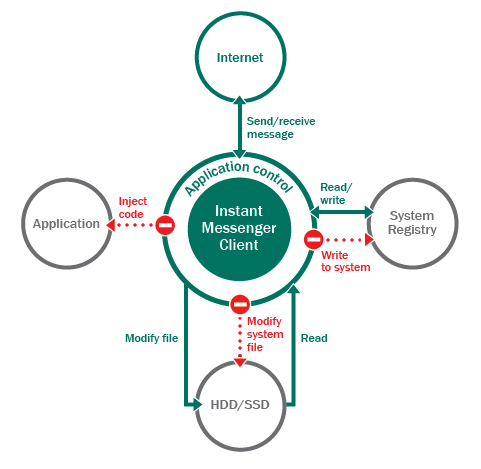
This leads us to the idea of maintaining the integrity of a trusted environment by controlling the activities of potentially vulnerable applications: web browsers, IM clients, office applications, P2P clients, file managers, etc. For each potentially vulnerable application, a list of allowed actions is created based on its use, as originally intended by the developers. Any other activity that goes beyond the developers’ specifications will be blocked by the security system.
For example, instant messaging programs are allowed to send and receive data on the Web, create files on the hard drive (which are later checked to see if they are trusted), and open existing files. These programs will not be allowed to inject code into other processes, modify system files or sections of Windows registry.
This approach helps restrict the potential activities open to malicious code, based on judgments about the intended functionality and use of a vulnerable application.
Receiving information about new applications
What should happen when a file previously unknown to the system is received from an source whose credentials are also unknown, e.g., is copied from a removable drive or arrives via Skype’s file transfer service?
Upon receiving a message that new software is attempting to launch, the security system contacts the cloud to check whether or not that application is trusted. If it is, the launch is allowed; if the application is not trusted or unknown to the cloud, its launch is denied. This approach introduces extra flexibility into the system, still honoring the basic concept of a trusted environment and without compromising on protection levels.
The same routine is followed when an application is launched that is signed with an unknown digital signature: the security system contacts the cloud and receives information on whether that signature is trusted or not.
Conclusion
In the first section of this article, we set out a security approach that retains the protection level offered by Default Deny-type solutions while providing the flexibility required in the everyday use of the computer. This approach is based on the concept of creating and subsequently maintaining a trusted environment.
The proposed security approach can be applied to both home users and organizations, regardless of the size of the latter. The task of creating and maintaining a trusted environment is fulfilled by the protection system, which bases its actions on:
- the results of creating an inventory of files in the system;
- the principle of trust inheritance: an file created by a trusted application is trusted;
- information received from the cloud about the reputation of files;
- lists of trusted digital signatures;
- lists of trusted websites on the Internet.
That said, the concept of a trusted environment does not eliminate the need for antivirus protection systems. Combining these two will help build an effective protection system for the computer.
No theory or approach can be fully assessed until it is put into practice. To find out how the concept of a trusted environment was implemented by Kaspersky Lab in its new product, Kaspersky Internet Security 2014, please read the second part.
Implementation of the trusted environment technology in Kaspersky Internet Security 2014
Introduction
In part one of this article, we discussed an extension of the Default Deny technology – the trusted environment concept which involves making a transition from blocking unknown objects to creating a trusted system and maintaining its trusted status, i.e., the status which guarantees that there is no malicious code in it.
In this part of the article, we go on to discuss implementation of the trusted environment as a protection component in Kaspersky Lab products. The first product to include this protection component is Kaspersky Internet Security 2014, in which the trusted environment is implemented as Trusted Applications Mode.
Activating Trusted Applications Mode
Trusted Applications Mode is enabled in Kaspersky Internet Security 2014 automatically. However, the computer needs to undergo a preparation procedure prior to activation the mode.
As described in part one of the article, Trusted Applications Mode functionality is based on blocking unknown applications, dynamic libraries and scripts. But what will happen if Trusted Applications Mode is enabled immediately upon installing the security product on a computer where several unknown applications are installed? According to Trusted Applications Mode logic, such applications, dynamic libraries and scripts will be blocked. At the same time, since the user may be accustomed to using these applications, blocking them might disrupt routine activities on the computer. The security solution therefore verifies whether its activation on the computer would lead to the blocking of programs which the user was working with prior to activating Trusted Applications Mode.
The computer’s compatibility with Trusted Applications Mode is verified in several stages, using a special intelligent mode. Below, we look at these stages in greater detail.
Stage 1. Analyzing applications that are launched
In the first stage, which takes several weeks, programs launched by the user are analyzed. Each application or script being launched is analyzed according to the following scenario:
- Does the application have a digital signature and is the signature trusted?
- If the application is not signed, the Kaspersky Lab knowledge base, available through the Kaspersky Security Network (KSN), is searched for information on whether it has the trusted status.
This does not involve blocking any unknown applications: the security solution simply saves information on whether the applications in question are trusted or not and hence whether they will be launched if the Trusted Applications Mode is activated on the computer.
As mentioned above, a file or certificate’s trusted status is verified using the KSN trusted programs knowledge base. This is why participation in the Kaspersky Security Network program is a prerequisite for activating Trusted Applications Mode – without it the security solution will be unable to decide whether a file being launched is guaranteed to be trusted or not.
After working for several weeks, the security solution looks at the total number of programs launched on the computer and the number of programs that would be blocked in Trusted Applications Mode. If there are no programs that could potentially be blocked, the second stage of verifying that the Trusted Applications Mode is suitable for the computer kicks in.
But what happens if there are unknown programs that are liable to be blocked? In this case, applications being launched on the computer will continue to be monitored. Perhaps new legitimate applications have not as yet been included in the KSN knowledge base and information on these programs will be added in the near future. It is also possible that unknown applications being launched are new modifications of viruses or Trojans. In this case, the anti-malware solution will remove the programs in question after updating antivirus databases, enabling it to move on to the second stage of verification.
In addition to monitoring applications, the security solution creates a list of libraries that are loaded on the computer, which is extended every time a new application is launched. The list is subsequently used at the stage when the dynamic libraries being loaded are analyzed.
Stage 2. Analyzing dynamic libraries being loaded
Importantly, Trusted Applications Mode blocks not only applications and scripts but also dynamic libraries loaded by applications. If an application is launched but a library loaded by it is blocked, the application will not be able to perform some of its functions or may become completely non-operational. This is why it is important to verify that the libraries loaded by trusted applications are also trusted before activating Trusted Applications Mode.
In the second stage, the libraries on the list created during the first stage are analyzed according to the algorithm described above. Note that this is done gradually, in the background. Any new libraries and applications launched during the second stage are also added to the list and analyzed.
The stage of analyzing the dynamic libraries that are loaded is completed when no unanalyzed libraries remain on the list. If unknown libraries are found, these libraries are re-analyzed later. As in the case of unknown applications, there are two possible scenarios:
- the file is a new version of a trusted library and will soon be included in the KSN knowledge base;
- the file is a new version of a malicious program and will be removed by the security solution next time the antivirus databases are updated.
Upon completing the second stage, the third and most important stage begins – analyzing system files.
Stage 3. Analyzing system files
In order to provide reliable protection, Trusted Applications Mode becomes operational immediately after turning on the computer. This means that if an attempt is made to launch an unknown system file during system startup, the file will be blocked, potentially resulting in the operating system failing to load correctly.
To prevent situations of this kind, the trusted status of all system files involved in the operating system’s startup and operation is verified in the third stage of preparation for enabling the Trusted Applications Mode. Like the first two stages, the third continues until all the files in the system are identified as trusted or malicious.
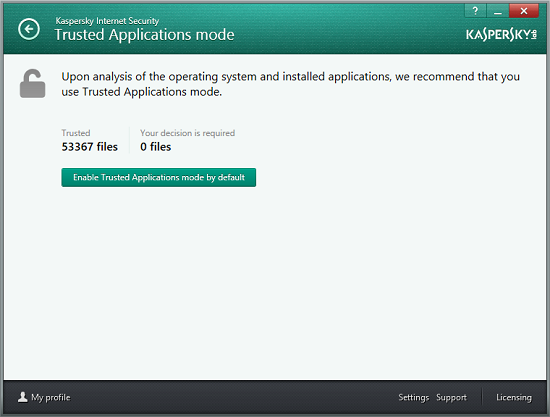
Upon completion of the third phase, the security solution makes the decision that the Trusted Applications Mode is fully compatible with the computer and will not interfere with the user’s day-to-day activities. After this, the user is notified that the computer is working in Trusted Applications Mode. The main window of Kaspersky Internet Security 2014 also provides an indication that the computer has entered Trusted Applications Mode by displaying a closed padlock icon on the image of a computer screen.
From that moment, Kaspersky Internet Security operates based on a completely different algorithm: only objects on the trusted applications list are allowed to run; any new objects appearing in the system are checked for their trusted status when being launched and are only allowed to run if trusted. Those objects which are not trusted are blocked.
Manually activating the Trusted Applications Mode
The preparation process for enabling the Trusted Applications Mode takes quite a long time – the security solution must make sure that all the files in the system are trusted before Trusted Applications Mode can be activated.
This scenario is particularly suited for home users. But what about experienced users who want to use the new protection tool immediately after installing the security solution?
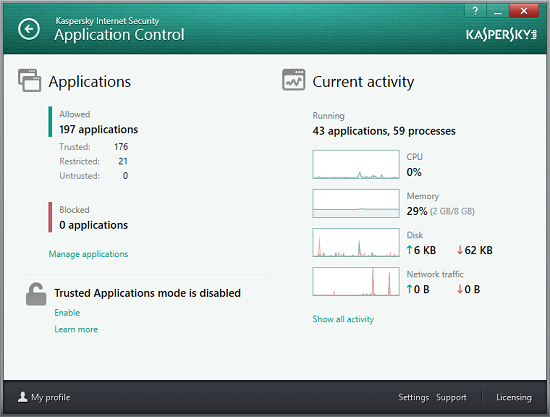
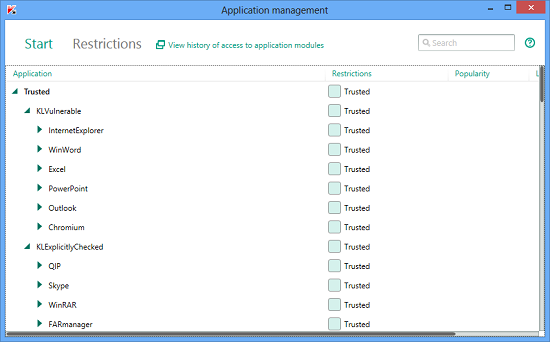
In such cases, Trusted Applications Mode can be manually enabled in the Application Control menu.
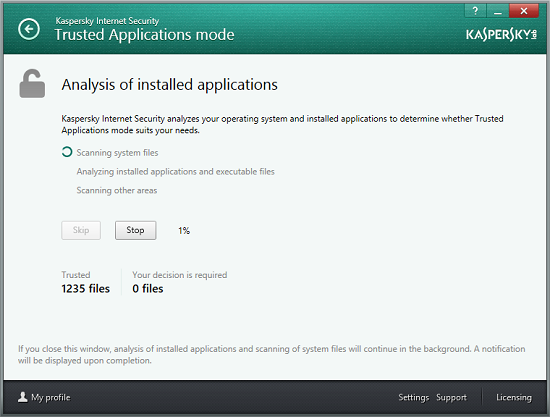
Even if Trusted Applications Mode is enabled manually, the security solution still needs to check that it will not interfere with users’ work. This is why the procedure of verifying the computer’s compatibility with Trusted Applications Mode starts immediately after clicking on the Enable link. Since the security solution has no information as yet on the programs launched by the user, libraries loaded or system files, the system is analyzed using a different sequence:
- system files;
- programs installed on the operating system;
- other files previously launched by the user, e.g., files launched from network drives.
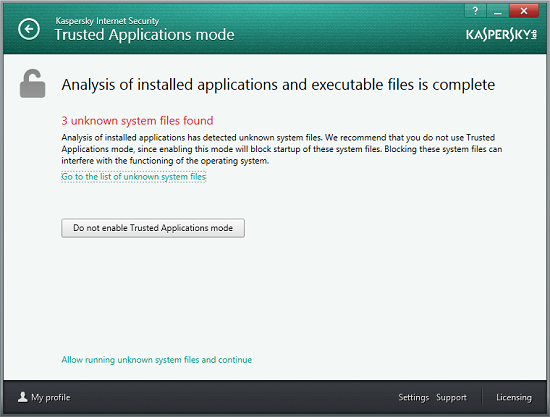
Upon completing the analysis (inventory), a list of programs that are currently unknown and will be blocked by Trusted Application Mode is displayed to the user.
The option of manually enabling the Trusted Applications Mode is a feature designed for experienced users. Such users can make informed decisions regarding the few unknown files detected in their systems. They should either allow execution of these files or block them. To make it easier for experienced users to make decisions regarding unknown files, Kaspersky Lab offers an online service that provides access to information on any file stored in the Kaspersky Lab knowledge base. The Kaspersky Security Network knowledge base includes records on each file’s digital signature, its trusted status, vendor, number of users across the globe who use the file and other helpful information.
If no unknown files are detected on the computer, the user will be prompted to activate Trusted Application mode.
When Trusted Applications Mode has been activated, the security solution operates based on the trusted environment algorithms described in the first part of this article. Below we discuss the implementation of these algorithms in Kaspersky Internet Security 2014.
Maintaining a trusted environment
Once the trusted environment has been built, launching applications that are part of the environment is straightforward: the antivirus solution knows that a file is trusted and allows it to load. If the system launches a new file that comes from outside the trusted system, e.g., from a removable data carrier, the file is checked to see whether it:
- has a trusted digital signature;
- was downloaded from a trusted source;
- has a trusted status in Kaspersky Security Network knowledge base.
If a positive answer is returned for one of those conditions, the file is permitted to launch; otherwise, the launch will be blocked and the user will be notified that an unknown object was blocked.
If a new file is created within the trusted environment, it is given trusted status – all applications created in the trusted environment with no contact with the external environment are considered to be trusted. This scenario permits unhindered updating of existing applications to newer versions and the installation of new applications.
However, the restrictions placed on vulnerable applications should not be forgotten: a vulnerable trusted application is capable of creating malicious objects as a result of an exploit being triggered. In order to increase security and maintain a trusted environment, Kaspersky Internet Security divides all trusted applications into three categories:
- Trusted applications. Applications that run using trusted environment properties;
- Potentially vulnerable applications. Each application has a specific profile of permitted activities, limiting its business-logic. A list of potentially vulnerable applications, set by Kaspersky experts, is based on a statistical analysis of vulnerabilities detected in various applications. All objects created by these applications are subject to additional controls;
- Applications with contact to the external environment. Applications that are not considered potentially vulnerable, but which have contact with the external environment and might be used to penetrate into a system. For instance, a file received by the Skype file transmission service may turn out to be a new, unknown type of malware. Objects created in the system by such applications are also subject to additional controls and are checked in the same way as all applications created outside the trusted environment.
Moreover, all the objects created by trusted applications are subject to the antivirus controls that make up the comprehensive protection concept used in Kaspersky Internet Security products, which all contributes to effective computer protection.
Kaspersky Lab’s experts decided against implementing the trusted environment concept as a separate security solution, believing that embedding it in existing Kaspersky Lab products to be the most efficient approach. There are several reasons for this: the existence of exploits capable of malicious activity without actually creating files on a computer; macro viruses that spread in Office documents (such files cannot be controlled with Default Deny as they are continuously modified); and use of legitimate software that has been customized by cybercriminals for malicious use. The latter includes specific settings in configuration files that turn keystroke logging programs into Trojan-Spies.
This approach makes it possible to create a reliable, comprehensive protection system for home computers or the corporate networks of small and medium-sized businesses.
Conclusion
The second part of the article covers the trusted environment technology as it is implemented in Kaspersky Internet Security 2014 – a product for home users. This implementation is called “Trusted Applications Mode”.
We discuss two different methods of activating Trusted Applications Mode:
- automated activation, when the security solution makes the decision to activate Trusted Applications Mode based on an intelligent algorithm. This activation method is best suited for home users;
- manual activation. This activation method can be used to create a trusted environment for a standalone computer or for a small network, helping to enhance the security of data circulating on the network.
This part of the article also covers methods of maintaining a trusted environment, which play an important role in making decisions when new programs appear in the system, as well as when updating existing and installing new programs. The methods of controlling vulnerable applications described above provide effective control over vulnerable applications and can be used to make decisions regarding the trusted status of files created by vulnerable applications.
The trusted environment concept described in this article and its implementation as Trusted Applications Mode in Kaspersky Internet Security 2014 is an important aspect of protecting PC users who value their information resources. The integrated security solution developed by Kaspersky Lab experts, which offers the combined advantages of the anti-malware approach and the Default Deny approach, can be used to create a trusted environment where cybercriminals’ chances of executing malicious code are next to none.

















Computing Securely: The Trusted Environment Concept