
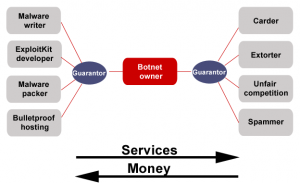
With the appearance of botnets, criminal gangs have gained access to millions of infected computers and the number of cybercrimes committed has risen sharply. Although the majority of Internet users understand that zombie networks pose a serious threat, many do not know how or why botnets are created and maintained.
Botnets act as a key link in the cybercrime chain. It doesn’t take any real technical skill to understand what role they play: cybercriminals do business with each other via the Internet and visiting the sites they use provides a wealth of information.
As botnets are particularly popular with Russian cybercriminals, the majority of botnet-related communication on the Internet is in Russian. As a result, the screenshots used in this article are in Russian.
Suppliers of cybercriminal services
The cybercriminal business has areas of specialization just like any other mature business. A search of the Internet for web resources offering cybercriminal goods and/or services reveals that botnet owners are the main consumers of these goods and services.
Developing malicious code
The lion’s share of Internet-based crime is directly or indirectly related to malicious programs – a wide range of viruses, Trojans, network worms and applications designed to attack remote computers via networks are the main tools used to commit cybercrime.
Botnet owners are the malware writers’ best customers, and use malware not only to create zombie networks but also to harvest confidential data, distribute spam, rogue antivirus applications and adware, and to transform infected computers into proxy servers.
Malware developers and botnet owners are closely linked and understand that their success depends on close cooperation. The owners of large botnets constantly need new malicious programs and malware writers are always on the lookout for regular clients.
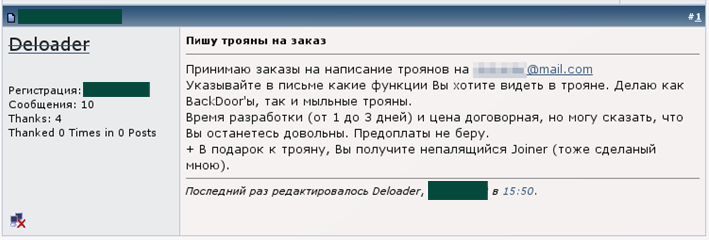
These days it’s easy to find people on the Internet who will develop malicious code to order – they usually offer their services on public hacker forums frequented by cybercriminals and scammers. Below is a typical post on a hacker forum:
The poster says he can develop Trojans; the customer should specify the functions desired. In addition, the poster offers potential customers a “Joiner” program which makes it possible to inject any malicious program into the executable file of a legitimate application.
Often, the customers on these hacker forums only want programs designed to steal passwords. However, there are resources apart from these forums which are used by cybercriminals who are far more skilled. They are often individuals who have studied Windows security in such detail that they could easily compete with Microsoft developers, and who use their knowledge to develop cybercriminal tools. These cybercriminals can create such sophisticated malicious programs that neutralizing and deleting them can represent a significant challenge for antivirus developers.
Fortunately, the majority of malware writers offering their services are relatively unskilled from a technical point of view. Unsurprisingly, there are also a lot of scammers on such forums, and posts are often flagged as “scam” by forum moderators. This means the poster has already tricked someone and a moderator has received negative feedback from a victim: hardly surprising, as petty criminals aren’t known for their honesty!
This lack of trust surrounding the suppliers of cybercriminal goods and services has led to the appearance of so-called guarantors, who, as their name suggested, ensure that customers receive the goods and services they order, and that the vendor is paid for them.
Guarantors
Guarantors are expected to be independent from all parties involved in the deal, and may test goods and services to see if they meet required standards. Someone offering malicious code or cybercriminal services has a much better chance of selling his wares if they have been tested by a well-known guarantor. Guarantors participate in both the purchase and sale of botnets and their components (e.g. bots).
Guarantors are usually moderators on popular hacker forums. The service offered by guarantors can range from an informal agreement between three people (e.g. the buyer, the seller and the guarantor) who know each other to a formal document which described both the guarantor’s role and the terms of the deal in pseudo-legal form.
Below are some excerpts from an agreement that describes a guarantor’s functions and the terms of payment for his services (translation from the Russian):
Sites where guarantors participate in deals list a range of cybercriminal goods and services, some of which are of particular interest to botnet owners: malware encryption and packing, browser exploits, traffic, and hosting.
Malware encryption and packing
In order to conduct a successful attack, it’s not enough to simply write or buy a malicious program because as soon as the program is used, antivirus vendors will get samples and start detecting the malware. That is why one of the most popular services is the encryption and packing of malware, which makes it possible for executables to evade detection while retaining the payload.
Sometimes suppliers of these services offer encryption for specific malware families. This is due to the fact that antivirus companies use heuristic detection for certain malware families, and this is much more difficult to evade than signature detection.
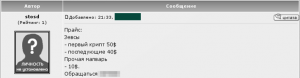
The author of the post shown above offers encryption for a bot known as Zeus as well as encryption for other, unspecified, malicious code. Encrypting Zeus is more expensive ($50 for the first encryption, $40 for subsequent encryption, as compared to $10 for the encryption of other malware) because it cannot be done using popular encryption programs.
Browser exploits
Exploits have always been a hot topic and systems such as ExploitPack are increasingly popular with cybercriminals. These systems make it possible to stealthily attack victim computers by exploiting software which has not been updated. Browsers and browser components (Adobe Flash etc.) are the targets of such attacks.
Whereas previously ExploitPack was sold as a product that did not require any “servicing”, now customers want support and updates.
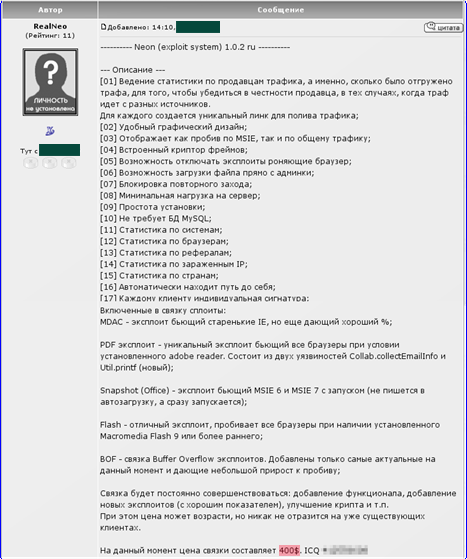
Internet forum entry in Russian with a description of the Neon exploit system
The appearance of new exploits has caused a renewed surge of interest in such malware and could lead to an increase in the prices charged for such packs. This is exactly what happened at the end of 2008 – the screenshot below shows an ExploitPack developer raising the price of a system from $400 to $500 because an exploit for a new vulnerability identified in Microsoft Internet Explorer 7 was added to the exploit pack.
“Traffic”
In cybercriminal parlance, “traffic” are user requests which are redirected from legitimate, but hacked, web resources to cybercriminal sites. Another way to increase the “traffic” is by getting users to click links in spam messages spread via email and IM (e.g. ICQ). Such spam campaigns are conducted by the cybercriminals themselves, which ensures that links will lead to their sites.
Cybercriminals can gain access to websites by buying stolen access data; there are cybercriminals who specialize in searching for, stealing and selling users’ passwords. Having gained access to sites, cybercriminals can then modify pages by adding an iframe HTML tag.
As a result of these modifications visitors to the site will be redirected from a modified, legitimate web page to cybercriminal sites. If a large number of pages are modified, thousands of visitors can be redirected to malicious sites, and cybercriminals can modify up to several thousand pages an hour by using automated tools.
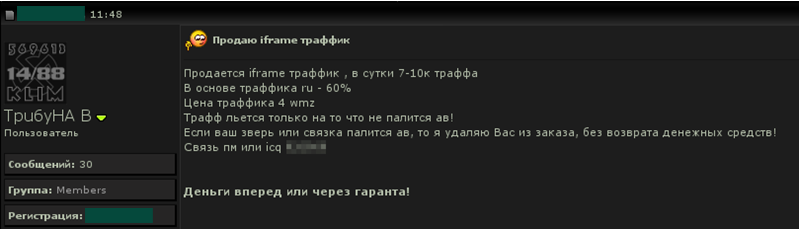
The screenshot above shows an Internet forum entry in Russian offering iframe “traffic” for sale. Payment needs to be made in advance or via a Garantor.
Generally “traffic’ is the cheapest service on offer, and is priced at between $0.50 to $1 per thousand visitors.
Botnet owners buy “traffic” and redirect users from hacked legitimate sites to web pages containing new exploits. If the attack targeting the browser following the redirect is successful, the victim machine will be infected and become part of a botnet.
Hosting
Bulletproof hosting is another profitable type of cybercriminal business. The owners of such hosting do not care about the content their clients place on web pages. Even more, they guarantee they will not listen to complaints made by visitors or other hosting providers.
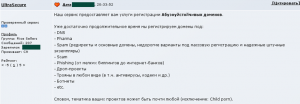
Internet forum entry in Russian offering bulletproof hosting services
RBN was one such hosting service which attracted a lot of attention from the Russian and Western mass media. It was shut down at the end of 2007. However many similar bulletproof hosting services, both large and small, continue to appear.

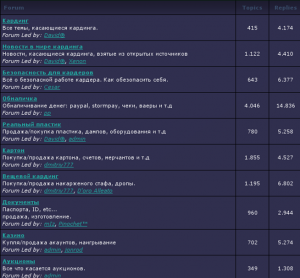
Menu page on a Russian Internet forum listing bulletproof hosting services
Bulletproof hosting is in great demand and where there’s demand, there’s supply. Forums are full of posts offering bulletproof hosting; such services are very popular with botnet owners who need reliable platforms to deploy botnet command and control center.
Customers
So far this article has examined those who supply goods and services to the cybercriminal market. However, the customers who use these services play an even bigger role in this underground economy: it’s the customers who are trying to gain unauthorized access to compromised computers’ data and resources. And it’s the customers who make huge profits by stealing e-currency and funds from victims’ credit cards. Generally these cybercriminals prefer to keep themselves to themselves and they are rarely connected to the more technically skilled criminals who write malicious programs.
It’s these customers who are often the ones most interested in botnets, and they can be split into the following groups:
- Carders
- Extortionists and unfair competition
- Spammers
Carders
Carding was one of the first types of cybercrime to appear on the Internet. Carders make a profit by using stolen credit cards and cardholders’ personal data. These cybercriminals have their own forums where they discuss ways of laundering money and converting it into cash. Such financial operations are, of course, illegal, which is why carders are very concerned about anonymity and security.
The screenshot above shows a typical carding forum with “virtual” credit cards (i.e. information about a credit card and the person it belongs to) for sale. There are also “real” cards on offer (i.e. physical duplicates of cards). In Russian cybercriminal parlance, “virtual” cards are called “cardboard” and “real” cards are called “plastic”.
“Real” cards can be used by criminals to withdraw money from ATMs. This will be done by a middleman who lives in the same area as the original owner of the card in order not to around the issuing bank’s suspicion.
If “cardboard” is used the money first has to be laundered in one of the following ways:
- using the stolen data to buy real goods in real shops in order to quickly sell the goods on; there will be high demand for the goods due to the low price being asked;
- using the stolen data in an online casino in order to transfer money from the card to another account;
- using the stolen credit card data on online auction sites in order to buy goods and resell them at a lower price (probably on the same site);
- using the stolen credit card data to rent hosting and then resell it at a very low price.
Carders in their turn need dedicated services which provide forged documents. This is yet another niche in the virtual market which cybercriminals are exploiting aggressively.
If a credit card is blocked, banks will usually ask the cardholder to send scanned documents to authenticate the owner of the account. Those offering forged documents offer to create whatever is required, with the resulting “product” looking like an exact copy of the original. Almost any document can be faked, including driving licenses, passports, utility bills, diplomas and even credit cards.
Carders play a very important role in the cybercriminal world. As they are the richest cybercriminals, they spend heavily on all sorts of illegal goods and services. Without botnets, they would not be able to get so many credit card details, so naturally, they will support the botnet owners who are able to get this data.
Extortion and unfair competition
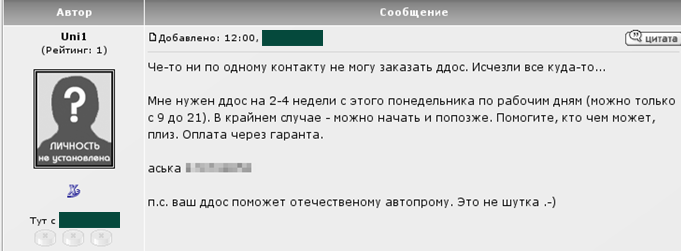
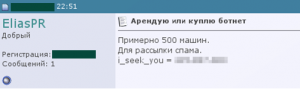
Internet forum entry in Russian from someone looking to carry out a DDoS attack during office working hours over a period of 2-4 weeks
This type of activity cannot be conducted without a botnet. Cybercriminals involved in extortion are entirely focused on incapacitating web sites by conducting a DDoS attack. The extortionists will ask for money in return for stopping the attack, while dishonest competitors will take advantage of the fact that their competitors’ site(s) and services are unavailable. Those who conduct DDoS attacks rarely advertise as they wish to remain anonymous. However, during the summer some customers who have failed to find a DDoS supplier publish posts looking for someone who can organize a DDoS attack.
Spammers
There are currently so many posts offering spam mailings from hacked servers that customers can easily find whatever they need. However, about 85% of spam is sent from botnets. As a rule, spammers are paid to distribute advertising, increase sales in online stores, or promote online casinos. Botnet owners are interested in customers like this because the money paid for services is not likely to be stolen, and therefore less likely to cause problems.
Conclusion
Botnets have a strong influence on the evolution of cybercrime as a business. On the one hand they incentivize the development of a range of cybercriminal services because botnet owners are the main consumers for encrypted malicious code, exploit packs, bulletproof hosting and “traffic”. On the other hand, botnets are essential to carders and spammers to enable them to conduct their business.
It’s botnets which unite all the disparate elements of cybercrime into an integrated system, and make it possible to transfer funds from those who make a profit from mass mailings and credit card thefts to malware writers and those who supply cybercriminal services.
The business of cybercrime evolves in cycles. Malware writers and other suppliers provide cybercriminal services to botnet owners. The botnet owners in their turn provide services to carders, spammers and others. Having made money by developing a piece of malware or another service, the supplier then starts on the next order, and the cycle begins again. Every new cycle involves more and more participants; the purchasers of services try to increase turnover, and rumors of profitable orders spread quickly across hacker forums and other channels of cybercriminal communication.
Today’s cybercriminals can use botnets to get unauthorized access to hundreds and thousands of computers. Botnets have a direct influence on the number of cybercrimes committed, and have resulted in a huge increase in credit card theft. DDoS attacks have become an everyday reality, and can be conducted by anyone with the help of a botnet.
Botnets are effectively the lifeblood of cybercrime, ensuring a continuous flow of funds between cybercriminals, and the continued evolution of cybercrime. The future of the Internet to a great extent depends on exactly how botnets evolve in the future.























The botnet ecosystem