
Modern technologies are becoming ever more integrated with each other. Mobile phones are becoming increasing intelligent, and handsets are growing ever more like computers in functionality. And smart devices, such as PDAs, on-board car computers, and new generation household appliances are now equipped with communications functions. We are entering a new era – the age of smart houses, global networks which encompass a wide range of devices, all of them exchanging data with each other via – as cyberpunk authors say – air saturated with bits and bytes. . Such trends clearly open new horizons to malicious users, and the potential threats are self evident.
This wired world is still evolving. We should be grateful for the fact that it still requires a bit more than a laptop and a wireless connection to gain control over someone else’s car. However, security for mobile devices is already an issue; and the first indication of trouble came, not surprisingly, in the form of a virus.
At first glance, the problem of malicious code appears only to be a part of the broader information security picture. However, malicious programs inevitably mutate from innocent amusements created by bored programmers and students who wish to show off their skills to professional solutions created expressly for financial gain. Today the boundary which previously existed between virus research on the one hand, and network security, program vulnerabilities, advertising software and criminal structures on the other, has effectively been eliminated. Therefore researching the techniques used by the authors of malicious code cannot be overestimated as an essential part of ensuring digital security.
This analysis is dedicated to the threat currently posed by malicious code to mobile devices which run under portable operating systems and are equipped with wireless technologies. In theory, the threats apply to all mobile devices. In practice however, these threats attack smartphones and communicators, the devices most attractive to virus writers. PDAs, in contrast, are not fertile ground for virus propagation as they do not come into contact with a large number of other devices to which they could transmit (potentially infected) data. The extent to which other mobile devices may be vulnerable to the threat of malicious code is difficult to quantify, as such devices are not yet commonly used.
A short history of mobile malware
This short history started in June 2004, when a group of professional virus writers known as 29A created the first virus for smartphones. The virus called itself ‘Caribe’. It was written for the Symbian operating system, and spread via Bluetooth. Kaspersky Lab classified the virus as Worm.SymbOS.Cabir.
Although a lot of media hype surrounded Worm.SymbOS.Cabir, it was actually a proof of concept virus, designed purely to demonstrate that malicious code could be created for Symbian. Authors of proof of concept code assert that they are motivated by curiosity and the desire to improve the security of whichever system their creation targets; they are therefore usually not interested either in spreading their code, or in using it maliciously. The first sample of Cabir was sent to antivirus companies at the request of its author. The source code of the worm was, however, published on the Internet, and this led to a large number of modifications being created. And because of this Cabir started to slowly but steadily infect telephones around the world.
| Although a lot of media hype surrounded Cabir, it was actually a proof of concept virus. |
A month after Cabir appeared, antivirus companies were startled by another technological innovation: Virus.WinCE.Duts. It occupies a double place of honour in virus collections – the first known virus for the Windows CE (Windows Mobile) platform, and also the first file infector for smartphones. Duts infects executable files in the device’s root directory, but before doing this, requests permission from the user.
It wasn’t long before virus writers struck the next blow in the virtual attack on Windows Mobile: a month after Duts was born, Backdoor.WinCE.Brador made its appearance. As its name shows, this program was the first backdoor for mobile platforms. The malicious program opens a port on the victim device, opening the PDA or smartphone to access by a remote malicious user. Brador will wait for the remote user to establish a connection with the compromised device.
With Brador, the activity of some of the most experienced in the field of mobile security – the authors of proof of concept viruses, who use radically new techniques in their viruses – comes almost to a standstill. Trojan.SymbOS.Mosquit, which appeared shortly after Brador, was presented as Mosquitos, a legitimate game for Symbian, but the code of the game had been altered. The modified version of the game sends SMS messages to telephone numbers coded into the body of the program. Consequently, it is classified as a Trojan as it sends messages without the knowledge or consent of the user – clear Trojan behaviour.
In November 2004, after a three month break, a new Symbian Trojan was placed on some internet forums dedicated to mobiles. Trojan.SymbOS.Skuller, which appeared to be a program offering new wallpaper and icons for Symbian was an SIS file – a installer for Symbian platform. Launching and installing this program on the system led to the standard application icons (AIF files) being replaced by a single icon, a skull and crossbones. At the same time, the program would overwrite the original applications which would cease to function.
Trojan.SymbOS.Skuller demonstrated two unpleasant things about Symbian architecture to the world. Firstly, system applications can be overwritten. Secondly, Symbian lacks stability when presented with corrupted or non-standard system files – and there are no checks designed to compensate for this ‘vulnerability’.
This ‘vulnerability’ was quickly exploited by those who write viruses to demonstrate their programming skills. Skuller was the first program in what is currently the biggest class of malicious programs for mobile phones. The program’s functionality is extremely primitive, and created simply to exploit the peculiarity of Symbian mentioned above. If we compare this to PC viruses, in terms of damage caused and technical sophistication, viruses from this class are analogous to DOS file viruses which executed the command ‘format c:’
The second Trojan of this class – Trojan.SymbOS.Locknut – appeared two months later. This program exploits the trust shown by the Symbian developers (the fact that Symbian does not check file integrity) in a more focused way. Once launched, the virus creates a folder called ‘gavno’ (an unfortunate name from a Russian speaker’s point of view) in /system/apps. The folder contains files called ‘gavno.app’, ‘gavno.rsc’ and ‘gavno_caption.rsc’. These files simply contain text, rather than the structure and code which would normally be found in these file formats. The .app extension makes the operating system believe that the file is executable. The system will freeze when trying to launch the application after reboot, making it impossible to turn on the smartphone.
Trojans exploiting the Symbian ‘vulnerability’ continue to appear. They differ from each other only in the approach which is used to exploit the ‘vulnerability’.
- Trojan.SymbOS.Dampig overwrites system applications with corrupted ones
- Trojan.SymbOS.Drever prevents some antivirus applications from starting automatically
- Trojan.SymbOS.Fontal replaces system font files with others. Although the replacement files are valid, they do not correspond to the relevant language version of the font files of the operating system, and the result is that the telephone cannot be restarted
- Trojan.SymbOS.Hoblle replaces the system application File Explorer with a damaged one
- Trojan.SymbOS.Appdiasbaler and Trojan.SymbOS.Doombot are functionally identical to Trojan.SymbOS.Dampig (the second of these installs Worm.SymbOS.Comwar)
- Trojan.SymbOS.Blankfont is practically identical to Trojan.SymbOS.Fontal
The stream of uniform Trojans was broken only by Worm.SymbOS.Lascon in January 2005. This worm is a distant relative of Worm.SymbOS.Cabir. It differs from its predecessor in that it can infect SIS files. And in March 2005 Worm.SymbOS.Comwar brought new functionality to the mobile malware arena – this was the first malicious program with the ability to propagate via MMS.
Summary of Mobile Device Malware
| Name | Date detected | Operating system | Functionality | Infection Vector | Number of Variants |
| Worm.SymbOS.Cabir | June 2004 | Symbian | Propogation via Bluetooth | Bluetooth | 11 |
| Virus.WinCE.Duts | July 2004 | Windows CE | File infector | — (File API) |
1 |
| Backdoor.WinCE.Brador | August 2004 | Windows CE | Provides remote access via network | — (Network API) |
1 |
| Trojan.SymbOS.Mosquit | August 2004 | Symbian | Sends SMS | SMS | 1 |
| Trojan.SymbOS.Skuller | November 2004 | Symbian | Replaces icon file | OS ‘vulnerability’ | 12 |
| Worm.SymbOS.Lasco | January 2005 | Symbian | Propogates via Bluetooth, file infector | Bluetooth, File API | 1 |
| Trojan.SymbOS.Locknut | February 2005 | Symbian | Installs corrupted applications | OS ‘vulnerability’ | 2 |
| Trojan.SymbOS.Dampig | March 2005 | Symbian | Replaces system applications | OS ‘vulnerability’ | 1 |
| Worm.SymbOS.Comwar | March 2005 | Symbian | Propogates via Bluetooth, MMS | Bluetooth, MMS | 2 |
| Trojan.SymbOS.Drever | March 2005 | Symbian | Replaces antivirus applications boot function | OS ‘vulnerability’ | 3 |
| Trojan.SymbOS.Fontal | April 2005 | Symbian | Replaces font files | OS ‘vulnerability’ | 2 |
| Trojan.SymbOS.Hobble | April 2005 | Symbian | Replaces system applications | OS ‘vulnerability’ | 1 |
| Trojan.SymbOS.Appdisabler | May 2005 | Symbian | Replaces system applications | OS ‘vulnerability’ | 2 |
| Trojan.SymbOS.Doombot | June 2005 | Symbian | Replaces system applications, installs Comwar | OS ‘vulnerability’ | 1 |
| Trojan.SymbOS.Blankfont | July 2005 | Symbian | Replaces font files | OS ‘vulnerability’ | 1 |
Graph 1. ‘Increase in the number of known mobile virus families’
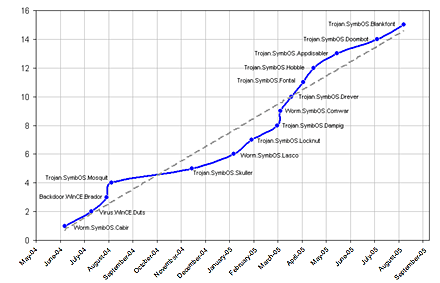
The history of mobile viruses can be divided into two eras; this is illustrated by the changing functionality of those malicious programs which appeared after Cabir. The first era is the initial six months which followed the appearance of the first mobile virus (June 2004 – January 2005), a period of technological breakthroughs. The following six months (January 2005 – present time) was a period dominated by primitive Trojans for Symbian. If we take into account the fact that the first mention of Worm.SymbOS.Comwar appeared on the Internet two months before samples were actually sent to antivirus companies, and the fact that Worm.SymbOS.Lasco is effectively a modified version of Worm.SymbOS.Cabir, this makes the boundary between the two eras even clearer.
Currently, mobile viruses are at a plateau in their evolution – the last virus which employed truly new techniques was Worm.SymbOS.Comwar, in March 2005. The quantitative increase remains stable: truly new malicious programs (excluding modifications of existing malware) for portable operating systems appear on average once a month.
Mobile device vulnerabilities
Smart mobile devices are still in their infancy, and consequently very vulnerable, both from a technical and a sociological point of view. On the one hand, their technical stability will improve only under arms race conditions, with a ceaseless stream of attacks and constant counter measures from the other side. This baptism of fire has only just begun for PDAs and smartphones, and consequently security for such devices is, as yet, almost totally undeveloped.
On the other hand, information security theory demonstrates that the human factor can negate all technical measures taken to secure systems. Usually, technical solutions to security issues will have little effect initially, due to lack of awareness among users. Rank and file computer users took years after the first virus epidemics to use antivirus utilities as standard, and months after the epidemics caused by email worms to learn not to launch unknown attachments which arrived via email.
- The worm does not exploit any vulnerability; for a smartphone to become infected, the user has to twice confirm that an unknown file should be uploaded and launched.
- There are several antivirus solutions for mobile devices available from a range of vendors
- The media hype which was raised around the appearance of the first worm for mobile devices should have reached the ears of even those mobile phone users who have no interest in technology
- Information about Cabir was published on all sites about viruses and antivirus solutions.
All these facts taken together lead us to the conclusion that it is only appropriate human behaviour which can guarantee the security of mobile devices at the moment.
We can estimate the technical level of smartphone security by how easy they are to destabilize – and this, in the worst case, may make it necessary to install new firmware on Symbian devices. The table above shows that the functionality of the majority of known mobile viruses simply exploits the peculiarities of the operating system: the fact that it is possible to rewrite any file, including system files, and the extreme instability of the system when it meets files which are unexpected (i.e. those which are corrupted, or non-standard for the current distributive).
Another example: the majority of vendors who produce Bluetooth technologies ensure that the function will be enabled by default. Taking into account the antipathy of the average user to documentation, the user may not even suspect that his mobile phone is visible to all Bluetooth owners within a range of 10 – 20 metres, and potentially open for data transmission and information exchange.
This situation is undoubtedly frightening, particularly if we take into account the fact that mobile devices are attractive to all types of virus writers. Mobile malware is more potentially profitable than that for computers for the following reasons:
- Improved quality in the contact between devices: mobile devices are, after all, called mobile devices, as they constantly maintain contact with the outside world (with mobile networks, the Internet, with computers and with each other). Given this, they have a great number of technologies for transmitting data, ranging from traditional mobile technologies (such as SMS and MMS) to Bluetooth and wireless technologies.
- Increased volume of contact between devices, as users normally carry their mobiles everywhere. When being carried, they establish Bluetooth contact with each other, making data transmission between devices possible. This means that a mobile which is carried around by the user will come into contact with thousands of other telephones in a matter of hours, and in highly populated or crowded areas this creates a powerful network for data exchange.
- Mobile technologies integrated with computer technologies are extremely fertile soil for mass mailings and for political, industrial and other types of espionage.
- Wireless data transmission technologies currently offer malicious users close to complete anonymity.
Points one and two create the necessary conditions for an instant and global epidemic, if a significantly powerful Bluetooth worm were to appear. Points three and four will attract professional virus writers working in conjunction with criminal groups to the area of mobile malware.
Threats
The most serious virus threat in terms of mobile security would be a self-replicating virus – a worm. Such malicious code is able to infect a large number of systems extremely quickly, disrupting the functioning of mobile networks or transforming a mobile network into a widely distributed network controlled by a malicious user.
We currently know of two worms (without including modifications) modified variants into account) for mobile phones: Worm.SymbOS.Cabir, where the propagation algorithm exploits Bluetooth technology, and Worm.SymbOS.Comwar, which replicates via both Bluetooth and MMS. A detailed analysis of these worms can be found in the Virus Encyclopaedia, but here we will confine ourselves to an examination of their self-replication mechanisms.
Worm.SymbOS.Cabir uses Bluetooth technology as it is meant to be used i.e. it does not exploit any vulnerability. When launched, it starts to scan the surrounding area, searching for other Bluetooth devices which are in discoverable mode, and then transmit data – in this case a copy of the worm – in the form of an SIS archive. Regardless of which operating system is installed on the telephone under attack, the screen will show notification of an incoming file and asks if the file should be accepted. If the user answers yes, the file will be saved in memory and automatically launched for execution. The system for installing SIS files will ask the user to confirm that installation should be carried out, and the worm will be installed to the system only once this confirmation has been received. The worm then starts a new cycle of scanning and infecting nearby devices. Users of Windows Mobile can download this file, but it represents no threat as the worm functions only under Symbian. There is also no threat to cars’ on-board computers which run Symbian OS: research has been conducted which shows it is impossible to infect these systems with a Bluetooth worm.
Worm.SymbOS.Comwar uses MMS technology to propagate (in addition to Bluetooth technology detailed above). It sends an MMS message to all telephone numbers in the address book. This message contains an embedded copy of the worm’s installation file. When sending infected messages, the worm is coded to pause – this may be why this worm which is functionally more dangerous than Worm.SymbOS.Cabir has not shown any dominance over Cabir in terms of speed of propagation.
The message subject and message body which the worm sends use tried and tested social engineering methods which were made classic by email worms. Topics such as ‘Nokia RingtoneManager for all models’ ‘Symbian security update’ etc. are expressly designed to lull the user into a false sense of security. Symbian telephones which receive such messages automatically launch the attached file, and the virus will be installed to the system. So far there are no recorded causes of Windows devices being infected.
It is difficult to say which propagation mechanism is more dangerous when used in mobile phone worms, Bluetooth or MMS. In terms of MMS, factors such as the greater number of telephones which use this technology over Bluetooth, and the fact that the worm’s replication mechanism does not depend on whether or not the infected phone is within contact distance of another Bluetooth mechanism play a significant role. On the other hand, Bluetooth has the unquestionable advantage of being universal, and able to unite a range of devices for data transmission. Transmission is also anonymous, and because of this it is impossible for the mobile operative scanning traffic to take concerted measures against the malicious program.
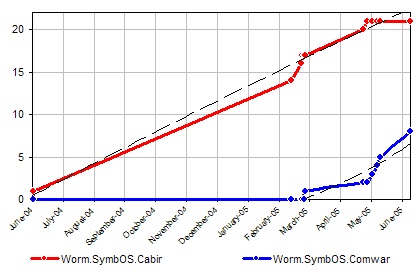
Graph 2: ‘F-Secure figures on the number of countries in which infections have been recorded’
Platforms
The commonest operating systems used in mobile devices today are Windows CE (Pocket PC, Windows Mobile), Symbian OS, Palm OS and Linux. However, Palm OS and Linux are rarely used in mobile devices. In the PDA and communicator sector Windows dominates, with Symbian more popular in the smartphone category.
It’s too early yet to judge how secure any platform is. However, testing conducted using mobile viruses already in existence raises the following interesting point. Symbian telephones automatically process (i.e. download, play, launch) any file which enters the Inbox, including files received via Bluetooth and MSS. And this applies to any file whether it is an image file, an audio file or an installer. This is in contrast to telephones running Windows mobile, which will simply save the received file in memory (usually in the folder ‘My Documents’). As we have not had the opportunity to test all the smartphones and communicators which are currently available, the probability exists that this difference may not be a difference between platforms, but rather between modules, even though in practice the two things are more or less the same.
On the basis of the evidence presented in the paragraph above, and the previously mentioned ‘vulnerability’ it would seem reasonable to conclude that Symbian is the platform most vulnerable to virus attack. However, objectively, this is nothing more than a reflection of the current state of the market, and does not say anything about the invulnerability of Windows Mobile to worms. Symbian is simply the most widely used platform for smartphones currently, and the most vulnerable to attacks from those testing the security of mobile devices with their malicious creations, as has already been demonstrated.
Protection against mobile viruses
At the moment there are several anti-virus solutions designed to protect mobile devices from viruses: Kaspersky Lab’s Anti-Virus for Windows CE (Pocket PC, Windows Mobile) Symbian (versions 6, 7 and 8 and UIQ) and also for Palm OS (no viruses have yet been discovered for this operating system). Other vendors such as Trend Micro, Network Associates and F-Secure produce similar programs, as do some of the younger companies which specialize in producing dedicated antivirus solutions for mobile devices (Airscanner, Simworks).
As for worms which propagate via MMS, the optimal solution is for the mobile network operator to install an antivirus product on the internet server through which MMS traffic passes. This will ensure protection for the network’s users.
Trends and forecasts
It is difficult to forecast the evolution of mobile viruses with any accuracy. This area is constantly in a state of instability. The number of factors which could potentially provoke serious information security threats is increasing more quickly than the environment – both technological and social – is adapting and evolving to meet these potential threats.
The following factors will lead to an increase in the number of malicious programs and to an increase in threats for smartphones overall:
- The percentage of smartphones in use is growing. The more popular the technology, the more profitable an attack will be.
- Given the above, the number of people who will have a vested interested in conducting an attack, and the ability to do so, will also increase.
- Smartphones are becoming more and more powerful and multifunctional, and beginning to squeeze PDAs out of the market. This will offer both viruses and virus writers more functionalities to exploit.
- An increase in device functionality naturally leads to an increase in the amount of information which is potentially interesting to a remote malicious user that isstored on the device. In contrast to standard mobile phones, which usually have little more than an address book stored on them, a smartphone memory can contain any files which would normally be stored on a computer hard disk. Programs which give access to password protected online services such as ICQ can also be used on smartphones, which places confidential data at risk.
However, these negative factors are currently balanced out by factors which hinder the appearance of the threats mentioned above: the percentage of smartphones remains low, and no single operating system is currently showing dominance on the mobile device market. This currently acts as a brake on any potential global epidemic – in order to infect the majority of smartphones (and thus cause an epidemic) a virus would have to be multiplatform. Even then the majority of mobile network users would be secure as they would be using devices with standard (not smartphone) functionality.
Mobile devices will be under serious threat when the negative factors start to outweigh the positive. And this seems to be inevitable. According to data from the analytical group SmartMarketing, the market share of Symbian on the Russian PDA and smartphone market has been steadily increasing over the last 2 to 3 years. By the middle of 2005 it had a market share equal to that of Windows Mobile, giving rise to the possibility that the former may be squeezed out of the market.
| Mobile devices will be under serious threat when the negative factors start to outweigh the positive. |
Currently, there is no threat of a global epidemic caused by mobile malware. However, the threat may become real a couple of years down the line – this is approximately how long it will take for the number of smartphones, experienced virus writers and platform standardization to reach critical mass. Nevertheless, this does not reduce the potential threat – it’s clear that the majority of virus writers are highly focussed on the mobile arena. This means that viruses for mobile devices will invariably continue to evolve, incorporating/ inventing new technologies and malicious payloads which will gradually become more and more widespread. The number of Trojans for Symbian which exploit the system’s weak points will also continue to grow, although the majority of them are likely to be primitive (similar in functionality to Fontal and Appdisabler).
The overall movement of virus writers into the mobile arena is an equal stream of viruses analogous to those which are already known with the very rare inclusion of technological novelties and this trend seems likely to continue for the next 6 months at minimum. An additional stimulus for viruses writers will be the possibility of financial gain, and this will come when smartphones are widely used to conduct financial operations and for interaction with epayment systems.



















An overview of mobile device security