
The setting is Tamel, the centre of Katmandu, the capital of Nepal. There are hundreds of little shops which sell everything, ranging from Buddha statuettes to full rigs for Himalayan expeditions. I’m off into the mountains myself, so I buy a Compact Flash card for my camera in one of the shops which specialises in photographic equipment.

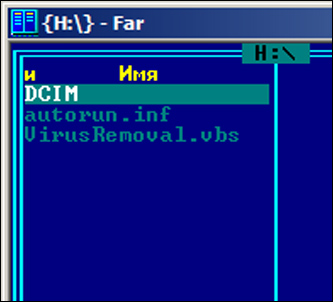
After three weeks of adventures at high altitude I return to Moscow and get ready to copy the photos from the memory card to my computer using a flash reader. And the first thing that I notice are two hidden files in the card’s root directory: they’re called autorun.inf and VirusRemoval.vbs.

We’ve already written more than once about viruses and worms which spread via removable storage media by launching automatically from autorun.inf. A number of users have also come across this type of malicious program. There are also a number of cases where hard disks, flash drives, MP3 players and other devices were already infected with malware when shipped by the manufacturers.
In this case, the Kingston card turned out to be infected with Worm.VBS.Small.n, a malicious program which was added to Kaspersky Lab antivirus databases on 14th November, 2 days after I bought the infected flash card in Nepal.
A detailed analysis of the worm’s code shows its Nepalese origins; as part of its payload, the worm changes the Internet Explorer home page to “sujin.com.np” – .np, of course, being the Nepal domain.
It seems unlikely that Kingston itself had anything to do with this incident. The worm probably ended up on the card once it was already in Nepal – possibly in the very same shop where I got it.
Or it could be that the card itself is counterfeit, and that it was produced in some underground factory in Nepal. So we’ve decided to publish the data shown on the card in the hope that it may help trace where it came from.
I didn’t encounter the Abominable Snowman in the Himalayas, but I did manage to bring a ‘Nepalese worm’ home with me. I think it’s a fitting entry for the Guinness Book of Records – Worm.VBS.Small.n surely qualifies for the ‘Computer Virus to Reach the Highest Altitude’ category. After all, it made it up as far as 6198 metres together with me and my camera.






















Adventures at altitude