
In response to numerous requests for comments and clarifications after our presentation at the Kaspersky Security Analyst Summit 2014, we have created this FAQ with some answers to the most commonly asked questions.
1. Why did you decide to expand this research after the presentation about Absolute Computrace in 2009?
Kaspersky Lab decided to undertake full research on this topic after discovering several privately owned laptops of Kaspersky Lab security researchers had the Computrace agent running without prior authorization. Such unauthorized activations quickly became alarming when our reverse engineering revealed serious vulnerabilities in the Computrace agent protocol design.
Absolute Software’s press release from 2009 claims that “The Computrace BIOS module is activated by the installation of Absolute Software by our customers, and is never forced upon any user. Computrace is designed to be activated, deactivated, controlled and managed by the customer using encrypted channels.”
However, we found signs of unauthorized activations on our hardware. Our research paper shows that actual versions of Computrace agent still use unencrypted channels. Due to this fact, we were able to conduct a live demo of a hijack of the Computrace agent at the SAS 2014 conference.
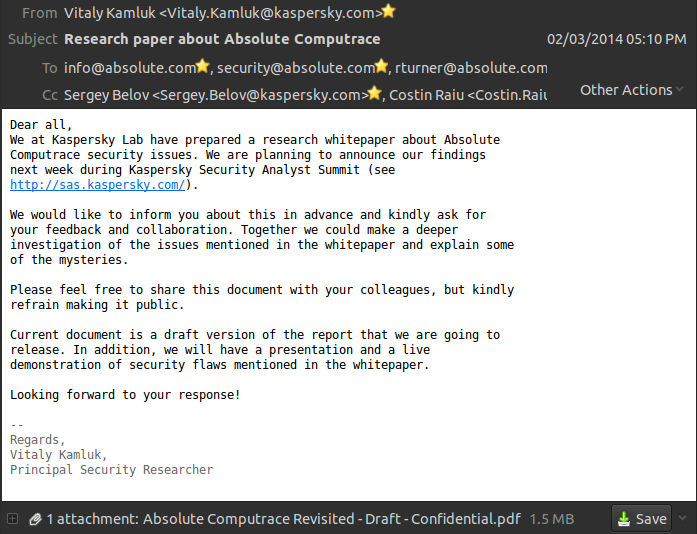
2. Did you contact Absolute Computrace before making your research public?
We notified Absolute Software via email and attached the full research paper draft. Here is a screenshot of the email message sent to Absolute Software on February 3, 2014:
Later that day we have received an automatic email from the Absolute Software mail server: “Delivery has failed to these recipients or distribution lists: security@absolute.com”
There were no other error messages which means that the email should have reached Absolute Software on other addresses in the list, however we have never received a formal response.
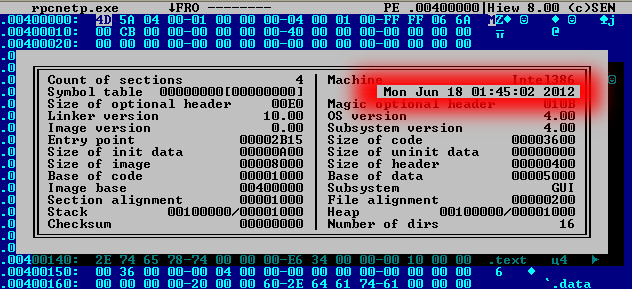
3. How recent was the Computrace agent variant you analyzed?
We analyzed several executables and laptops during the course of this research. The analyzed laptops were brand-new, purchased in 2012 with the top configurations available on the market according to the laptop owners.
The variant of the Computrace agent we used in our live demo was compiled in 2012:
4. How can I detect Computrace on a system?
The Simplest and most efficient way is to search for rpcnet.exe process in Task Manager or a file with the same name in your C:WindowsSystem32 directory. If found – you have Computrace activated. For an extended list of Computrace agent activity please see Appendix A of our research paper.
5. Should non-Windows users worry about unauthorized activations of Computrace?
As of now, we are not aware of EFI Firmware or BIOS Optional ROMS that have executables for non-Windows platforms, which means that the agent code will not be installed on non-Windows partitions. For details on how the agent is installed from BIOS please see our full research paper.
6. Does Computrace security issues affect non-Windows platforms?
Our research shows a security flaw in the Computrace agent protocol design which means that theoretically all agents for any platform may be affected. However, we have only confirmed the vulnerability in the Windows agent.
We are aware of Computrace products for Mac OS X and Android tablets. However, we have not analyzed the protocols they use.
Absolute Computrace: Frequently Asked Questions





















davie curry
Is there a way of removing this or if I force stop on my galaxy s5 will that stop it until I force restart can I ask Samsung to send a new hand set out ?
Peter Jackson
i am using ABSOLUTE in an enterprise environment . How does my Absolute console know?
Patrick
I have my laptop Lenovo t490s, it has computrace how can I remove it
Securelist
Hi Patrick!
To solve this problem, contact Absolute Software (https://www.absolute.com/), the Computrace developer, or the previous owner of your laptop.