
Introduction
Two-factor authentication (2FA) is a security feature we have come to expect as standard by 2024. Most of today’s websites offer some form of it, and some of them won’t even let you use their service until you enable 2FA. Individual countries have adopted laws that require certain types of organizations to protect users’ accounts with 2FA.
Unfortunately, its popularity has spurred on the development of many methods to hack or bypass it that keep evolving and adapting to current realities. The particular hack scheme depends on the type of 2FA that it targets. Although there are quite a few 2FA varieties, most implementations rely on one-time passwords (OTPs) that the user can get via a text message, voice call, email message, instant message from the website’s official bot or push notification from a mobile app. These are the kind of codes that most online scammers are after.
Malicious actors can obtain OTPs in a variety of ways including complex, multi-stage hacks. This article examines methods that rely on social engineering, where attackers manipulate the victim into giving away the OTP, and tools that they use to automate the manipulations: so-called OTP bots and administration panels to control phishing kits.
What is an OTP bot?
The use of OTP bots to bypass 2FA is a relatively recent online scam trend that poses a major threat to both users and online services. An OTP bot is a piece of software programmed to intercept OTPs with the help of social engineering.
A typical scam pattern that uses an OTP bot to steal 2FA codes consists of the following steps:
- The attacker gets hold of the victim’s credentials and uses these to sign in to their account;
- The victim gets an OTP on their phone;
- The OTP bot calls the victim and follows a script prepared in advance to talk them into sharing the code;
- The victim punches in the verification code on their phone without interrupting the call;
- The attacker receives the code through their administration panel or a Telegram bot;
- The attacker gains access to the victim’s account by entering the OTP on the website.
As you can see, the OTP bot’s key task is to call the victim. It is calls that scammers count on, as verification codes are only valid for a limited time. Whereas a message may stay unanswered for a while, calling the user increases the chances of getting the code. A phone call is also an opportunity to try and produce the desired effect on the victim with the tone of voice.
Bots may have functionality that varies from one script that targets the user of a certain organization to a highly tunable configuration with a wide range of scripts that let scammers replace a whole call center with bots. Bot developers compete by trying to include a maximum of features at a price that reflects the value.
For example, one OTP bot boasts more than a dozen features including 24/7 technical support, scripts in a variety of languages, female as well as male voices available and phone spoofing.
OTP bots are typically managed via a special browser-based panel or a Telegram bot. Let’s look at the example of how bots can be run via Telegram.
- You start by buying a subscription. There are several options depending on the included features. The cheapest plan will set you back 140 US dollars per week, and the most expensive one, 420 US dollars per week. The bot accepts payments in cryptocurrency only.
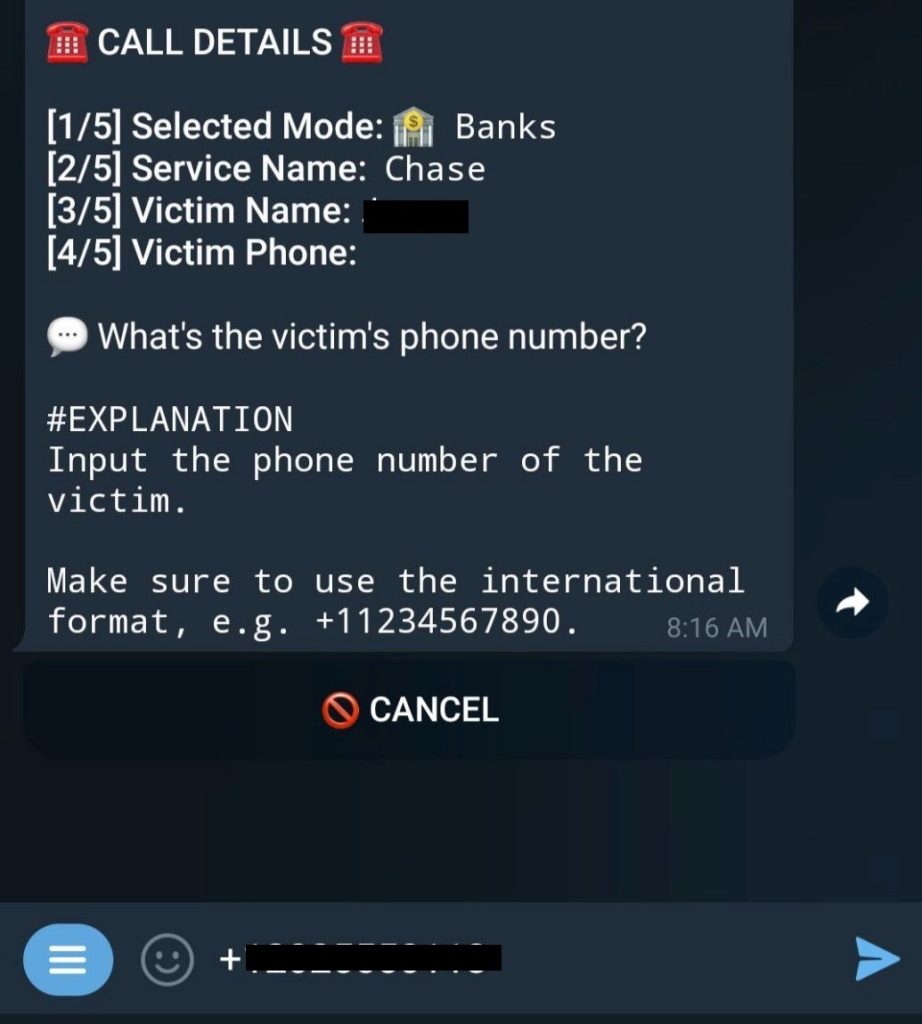
- After you have paid for a subscription, you are granted access to set up your first call. You typically do this after you get hold of the victim’s account credentials but before attempting to sign in to their account. First off, the scammer chooses what kind of organization they want the bot to impersonate.
The specimen at hand offers a variety of categories: banks, payment systems, online stores, cloud services, delivery services, cryptoexchanges and email services. While a call from the bank is something the victim might expect, a call from a cloud storage or email provider is not what we’d describe as completely normal. Yet, social engineering can be used to talk the victim into giving away a code provided by any type of organization.
A large number of available categories is admittedly more a marketing gimmick rather than anything else: scammers may feel inclined to pay for an OTP bot that offers more options. Most often, bots are used for bypassing 2FA required by financial organizations. - After selecting a category, you have to manually specify the name of the organization for the bot to impersonate.
- Next, you need to provide the name of the victim that you want the bot to call. This serves to personalize the call.
- The next step is an essential one: the scammer adds the victim’s phone number to make the call possible.
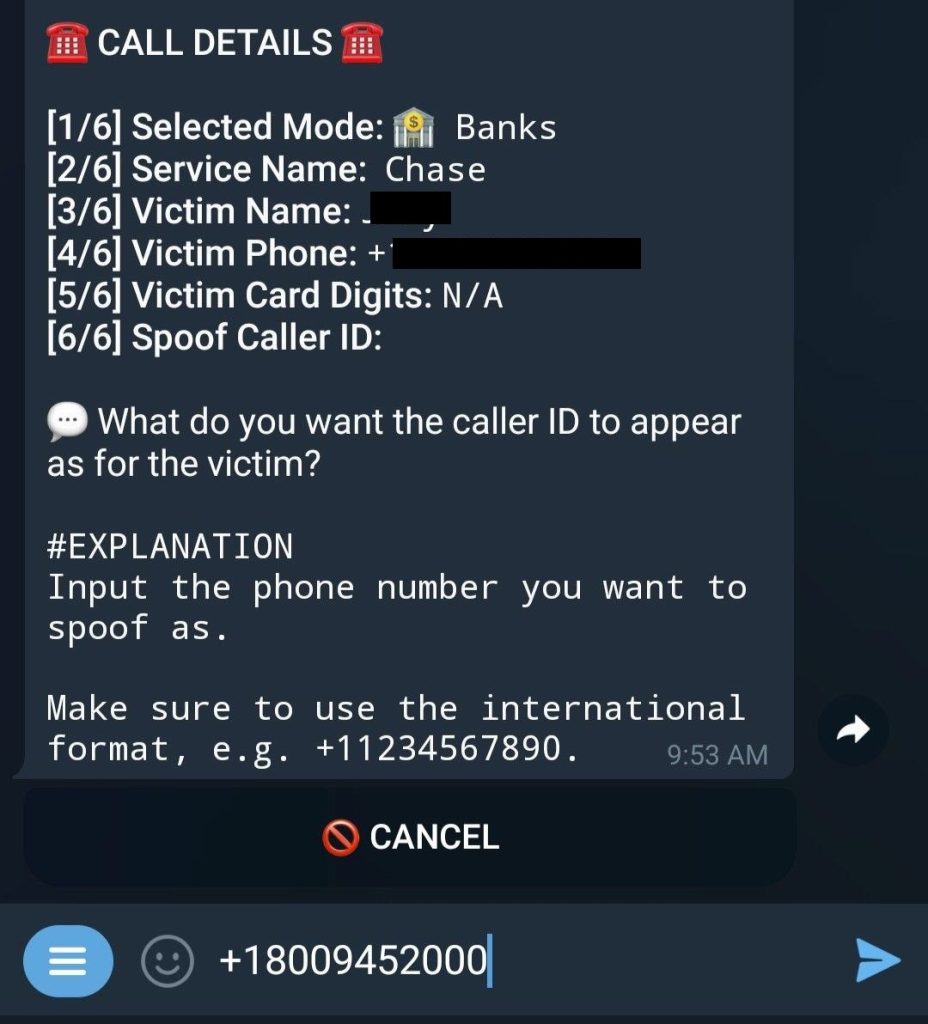
- The scammer has the option to provide the last four digits of the victim’s bank card number if they know what these are. This can help win more trust with the victim. After all, how would the caller know these numbers unless they were a bank employee?
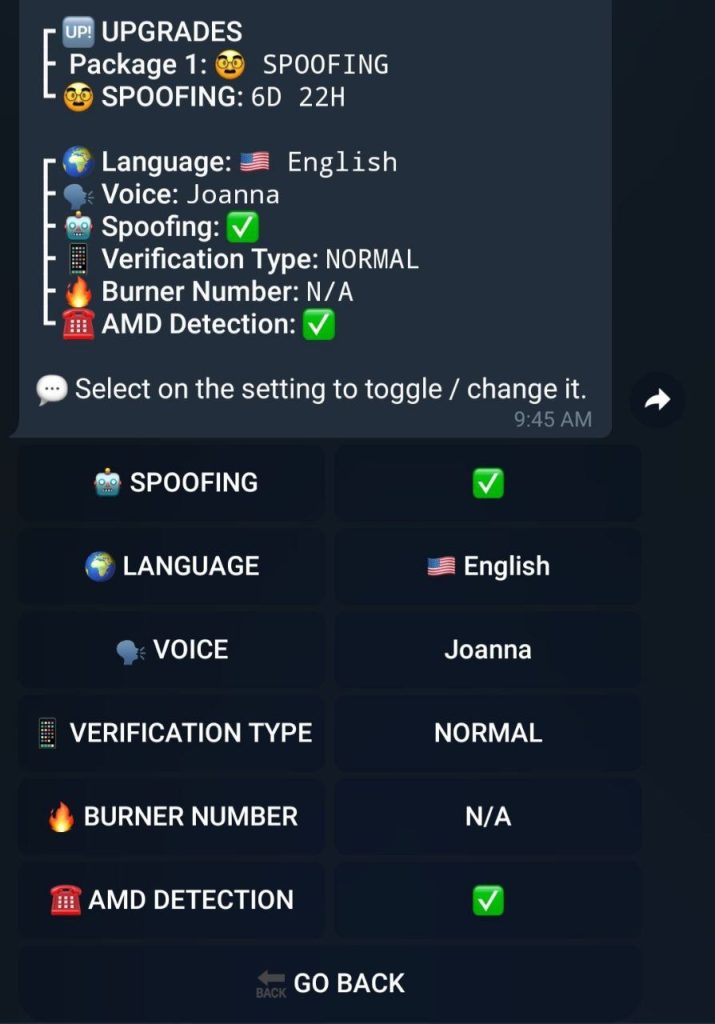
- Once all the details have been filled in, you can customize the call through advanced options.
- You can turn on spoofing, too, but you’ll need the official phone number for the organization that the OTP bot is set up to impersonate. This is the caller ID that will be displayed on the victim’s phone screen when they get the call. The bot uses a random number unless this feature is enabled.
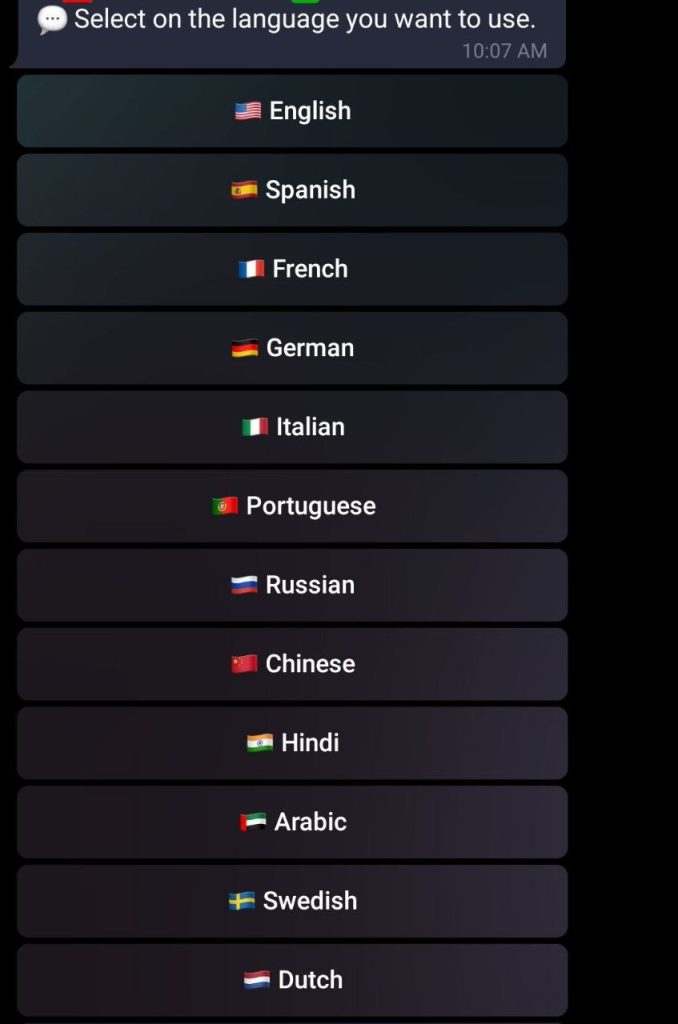
- You also can select a language for the bot to use when talking to the victim. The bot lets you choose from 12 languages of different language groups.
- After the scammer selects a language, the bot offers to choose a voice. All of the voices are AI-generated, and you can choose a female or male one. Six regional varieties are available for English: U.S., British, New Zealand, Australian, Indian and South African.
- The bot lets you make a test call by entering a disposable number from the attacker’s pool.
- The bot is also able to detect if the call is redirected to voice mail. The bot will hang up if it is.
- The OTP bot in question supports custom scripts. In other words, the scammer can import their own scripts designed to imitate organizations that are not available among the options offered by the bot. The bot voices these custom scripts while you set up the call.
- The last step is making the call with the set options.
Interesting options offered by other OTP bots
As mentioned above, functionality varies from bot to bot. Besides what we’ve already explored, we have seen several advanced features with other OTP bots, listed below.
- Sending a text message as a heads-up about the impending call from an employee of a certain company. This is a subtle psychological trick aimed at gaining the victim’s trust: promise and then deliver. Furthermore, a disturbing message might leave the victim waiting anxiously for the call.
- Asking for other details during the call, besides the OTP. These may include the card number and expiry date, CVV, PIN, date of birth, social security number, and so on.
How scammers get the victim’s credentials
Since the bot is designed for stealing 2FA codes, it only makes sense to employ it if the scammer already has some of the victim’s personal details: the login and password for their account as well as a phone number at least, and their full name, address, bank card details, email address and date of birth at most. Scammers may get this information in several ways:
- From personal data leaked online;
- From datasets purchased on the dark web;
- Through phishing websites.
Phishing is typically how they get the most up-to-date credentials. Scammers will often want to save time and effort by harvesting as much information as possible during a single attack. We have come across many phishing kits targeting seemingly unrelated types of personal data.
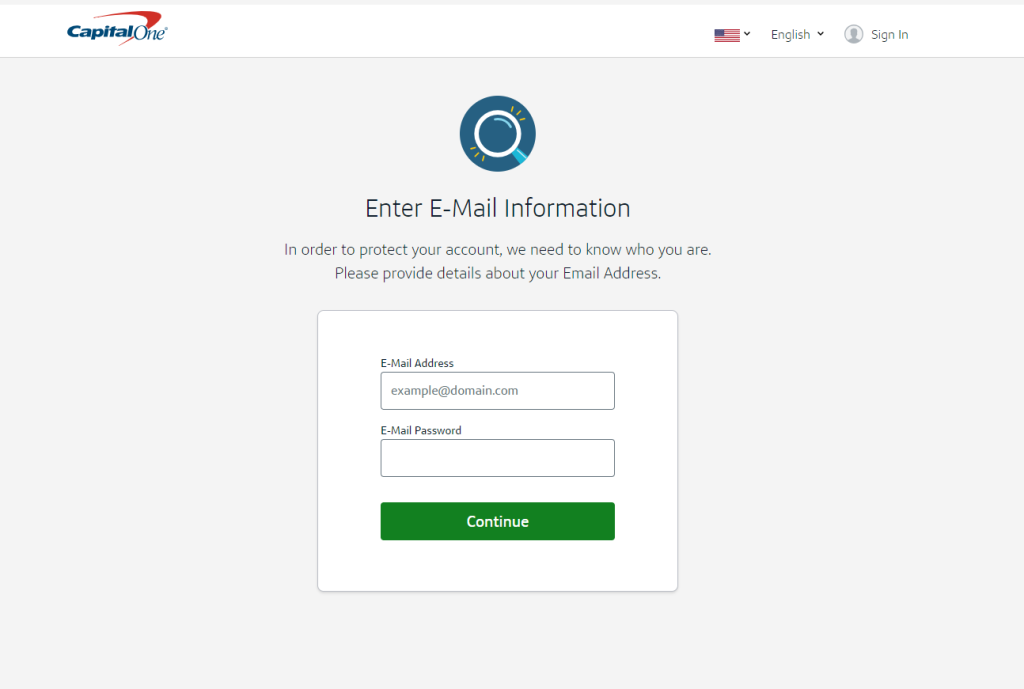
A kit may target a bank, but once the victim enters their login and password, they will be asked to provide their email address and the corresponding password. Equipped with that data and armed with an OTP bot, the scammer may be able to hack at least two of the victim’s accounts, and if the victim uses their email for authenticating with other websites, the scammer can inflict even more damage.
Phishing in real time
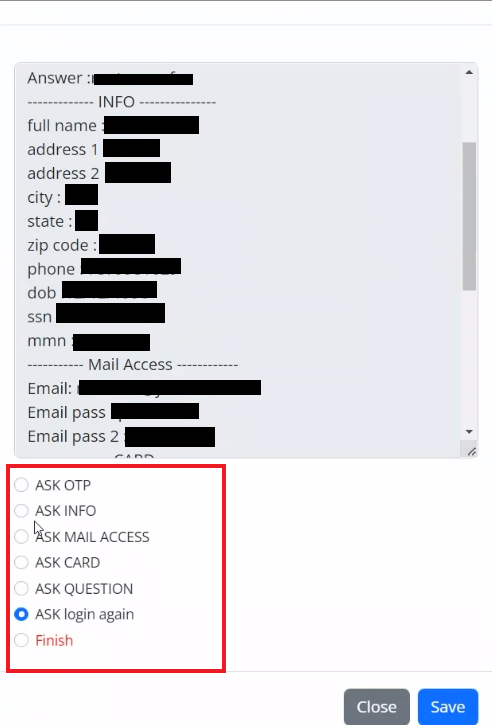
We have written about phishing kits that can be controlled via administration panels. As 2FA grew in popularity, the creators of phishing kits modified their admin panels by adding the functionality to intercept OTPs. This has enabled scammers to receive their victims’ personal data in real time to immediately use it.
These are multi-stage phishing attacks typically composed of the following steps.
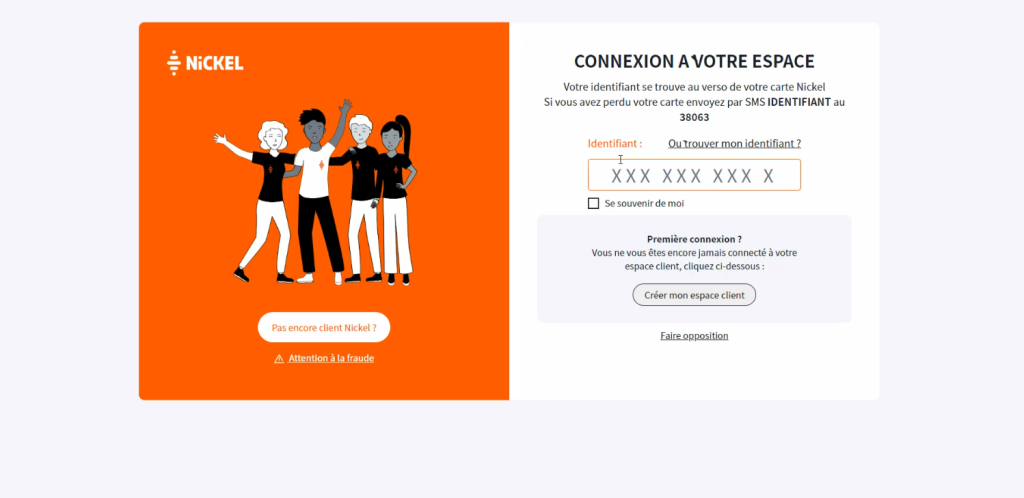
- The victim receives a message from, say, a bank, requesting that they update their account details. The message contains a link to a phishing website.
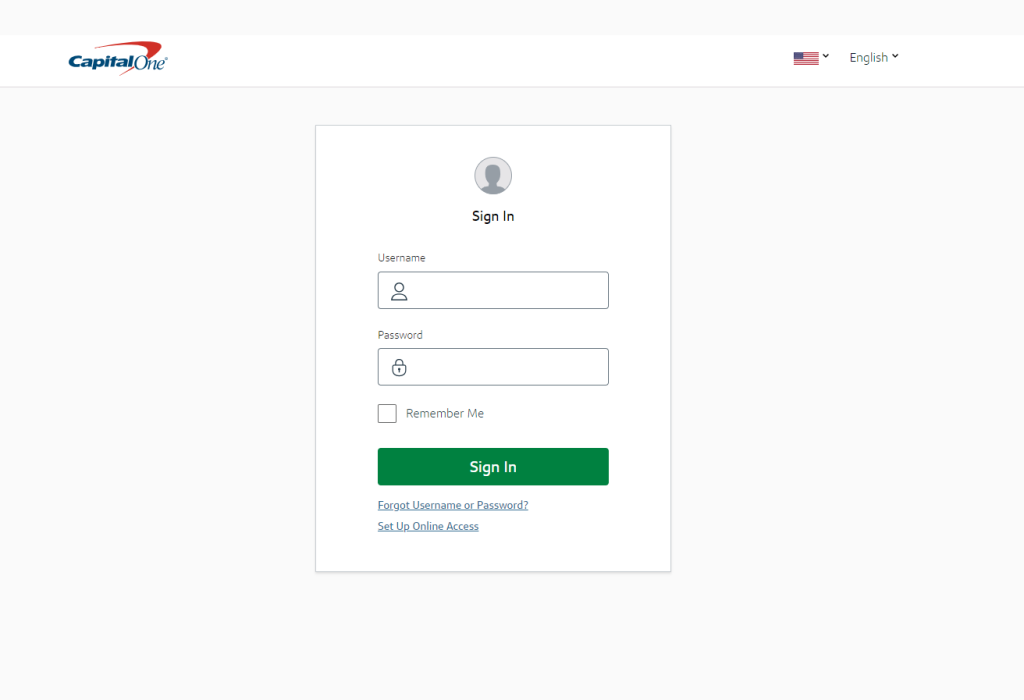
- The victim opens the link and enters their login and password. The scammer receives this data through Telegram and the administration panel. They try to use these details to sign in to the victim’s account on the official bank website.
- The bank sends the victim an OTP for additional verification. The scammer uses their admin panel to display an OTP entry form on the phishing site. They will be able to sign in to the victim’s real account once they get that verification code.
- The scammer may ask the victim for more details, which they might need for further activities in the victim’s account. Most banks require their clients to provide additional personal details to confirm transactions they detect as suspicious. These details may include the house number, secret word, passport number, and so on.
- The scammer then tells the user that their personal details have been confirmed. In reality, the details have been saved in the scammer’s admin panel, and they can immediately use this information to start siphoning off funds from the victim’s account.
Statistics
Our bank phishing kit detection statistics can help form an assessment of potential damage done by OTP bots. In May 2024, our products prevented 69,984 attempts at visiting sites generated by this type of phishing kits.
Detection statistics for phishing kits targeting banks, May 2024 (download)
As we researched the subject, we also closely examined 10 multi-purpose phishing kits used for real-time interception of OTPs. In May 2024, our technology detected 1262 phishing pages generated by the kits in question.
Detection statistics for multi-purpose phishing kits, May 2024 (download)
The peak level during the first week of the month coincides with a surge in activity by one of the phishing kits.
Takeaways
While 2FA is a popular way of added account protection, it, too, can be bypassed. Scammers steal verification codes by using various techniques and technologies, such as OTP bots and multi-purpose phishing kits that they control in real time with the help of administration panels. In both cases, the user agreeing to enter the one-time code on the phishing page or while on a call with the OTP bot, is the crucial factor when trying to steal the code. To protect your accounts from scammers, follow our best practices as outlined below.
- Avoid opening links you receive in suspicious email messages. If you need to sign in to your account with the organization, type in the address manually or use a bookmark.
- Make sure the website address is correct and contains no typos before you enter your credentials there. Use Whois to check on the website: if it was registered recently, chances are this is a scam site.
- Do not pronounce or punch in the one-time code while you’re on the phone, no matter how convincing the caller sounds. Real banks and other companies never use this method to verify the identity of their clients.
- Use a reliable security solution that blocks phishing pages.
Bypassing 2FA with phishing and OTP bots




























Jake Ghuile Jr.
Does this method work against Universal 2nd Factor (U2F) / FIDO authentication, like Yubico Yubikey ot Titan/ Feitian hardware tokens?
Olga Svistunova
Hi Jake!
No, OTP bots don’t target hardware tokens, only one-time passwords. Most likely, the scammers won’t even try to use this method if they see that a hardware token is required as the second factor.