
In recent times we’ve been seeing a lot of file-encrypting ransomware activity.
One of the new ones we’ve seen pop up in the last couple weeks is called ZeroLocker. There’s indication the C&C configuration contains some errors which would prevent successful decryption. This is why we urge people not to pay up even more so than normal.
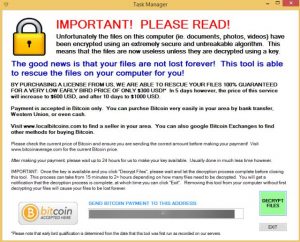
So far we’ve observed a limited amount of detections through our Kaspersky Security Network. The actors behind ZeroLocker are initially asking $300 worth of BTC for decrypting the files. This goes up to $500 and $1000 as time passes:
ZeroLocker adds a .encrypt extension to all files it encrypts. Unlike most other ransomware ZeroLocker encrypts virtually all files on the system, rather than using a set of pre-defined filetypes to encrypt. It doesn’t encrypt files larger than 20MB in size, or files located in directories containing the words “Windows”, “WINDOWS”, “Program Files”, “ZeroLocker” or “Desktop”. The malware gets executed at boot from C:\ZeroLocker\ZeroRescue.exe.
Though there’s a Bitcoin wallet hardcoded inside the binary the malware tries to fetch a new wallet address from the C&C. This is most likely done to make it more difficult to trace how successful the operation is and where the money goes.
We’ve gathered several Bitcoin wallet addresses and at the time of writing none had any transactions associated with them. As the C&C server is providing the Bitcoin wallet information it’s possible the attackers are able to use a unique wallet for each victim.
The malware generates one random 160-bit AES key to encrypt all the files with. Due to the way the key is generated the key space is somewhat limited, though still large enough to make general brute forcing unfeasible. After encryption the malware runs the cipher.exe utility to remove all unused data from the drive, making file recovery much harder. The encryption key, together with a CRC32 of the computer’s MAC address, and the associated Bitcoin wallet is sent to the server.
Interestingly enough, the encryption key along with the other information is sent through a GET request, rather than a POST. This results in a 404 on the server. This could mean that the server is not storing this information. That means victims who pay up may likely not see their files restored.
Several other URLs that the malware tries to get result in 404s as well, which indicates this particular operation may still be in its infancy. When those errors are fixed we may see ZeroLocker deployed on a larger scale. These operations rely on people paying up. Don’t do it. Make sure you have backups instead.
We detect current ZeroLocker samples as Trojan-Ransom.MSIL.Agent.uh.
ZeroLocker won’t come to your rescue




















Darren Chaker
Great points raised about ransomeware, the increased key length, and frequency of attacks! Good to see you’re on top of things!