
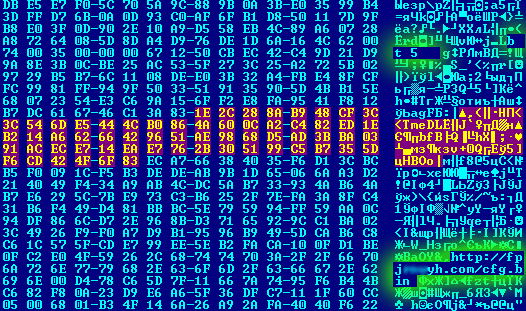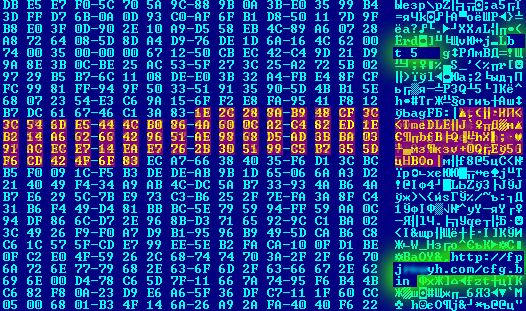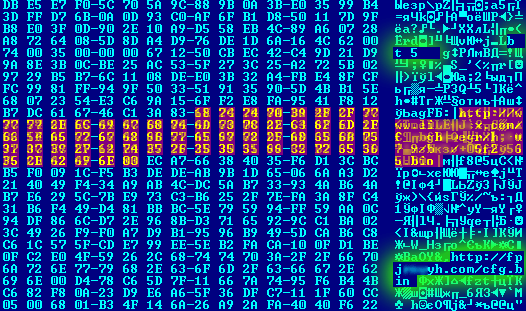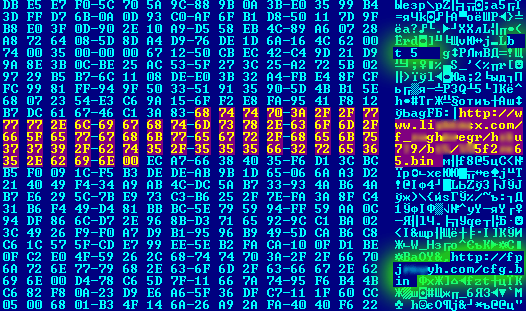
A little while ago it became clear that the ZeuS program design had been passed on to the creator of another competitor Trojan called SpyEye. Now everyone is waiting to see when these two spyware programs combine to create a monster. The author of SpyEye will most probably extract the most valuable things from ZeuS and implement them in SpyEye. Some researchers have already found a code piece from ZeuS in a SpyEye sample.
Section of SpyEye code identical to that in ZeuS
We didn’t expect new modifications of ZeuS to appear after it had been transferred to the new owner. Of course, we are still seeing a steady stream of ZeuS samples, but virtually all of them are well known versions of the malicious program. The new variants are usually the result of rebuilding that can be carried out with minimum fuss using programs known as ZeuS Builder kits. But from time to time I come across some rather unusual variants of the Trojan and I now have very good reason to believe that ZeuS is still to some extent being maintained and developed.
Two months ago we noted that ZeuS had new functionality: it was checking to see if it was being launched on a test platform, e.g. in the sandbox of a research company. The launch of the Trojan was stopped if there were signs that it was being executed in an environment set up to analyze its behavior.
Here is an example of one such check – ZeuS verifies if it is being launched on a VMware system by opening a specific device for that virtual machine:
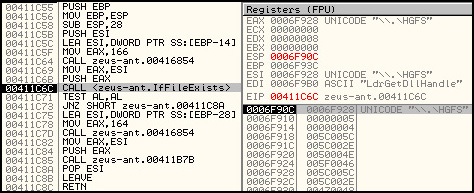
1st check to see if ZeuS is launched on a VMware virtual machine
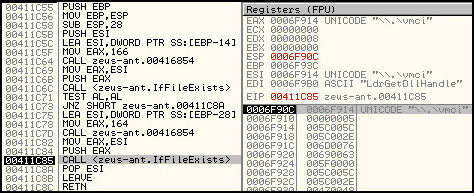
2nd check to see if ZeuS is launched on a VMware virtual machine
A few weeks ago a different ZeuS variant appeared that displayed unusual behavior for that family. All the latest variants of ZeuS had the same algorithm to decrypt a section in their code which contained the Trojan’s initial internal settings (a link used to download the configuration file, traffic encryption key, etc.). In the new, unusual sample there was double encryption. First of all, data was decrypted using the standard algorithm, but the address to the configuration file was a fake. The genuine link to the configuration file, which contained the address of the botnet command center, was only revealed at the second decryption.
Below you can see what this looks like in practice. After the first decryption you can see the initial settings (highlighted in green), but the link at the bottom is a fake. The real link is hidden in the area highlighted in red that only appears after the second decryption.
Decryption section of primary data
A few days ago I found a ZeuS sample that also checks if it is being analyzed, for example, by antivirus companies. The functionality is basically the same but with minor modifications – another criterion for detecting a new test platform had been added.
In this variant of ZeuS there are also modifications to the structure in pieces of code, which had remained unchanged for over 6 months and been used in thousands of samples of the Trojan.
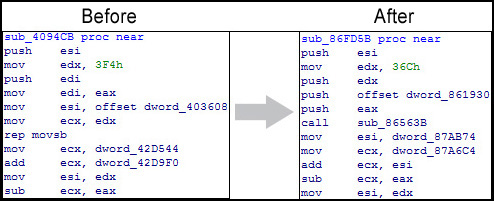
Modifications to a previously unchanged piece of ZeuS code
The changes to the code show that the sample was created using a new, recompiled version of the ZeuS Builder.
Functionality that is capable of detecting a test platform is unique. It looks like it was probably added to the standard ZeuS functionality as an optional extra. This suggests that technical support is still available for the last few VIP clients using ZeuS.
So, what exactly do we have here: the death throes of a ‘god’ or a reawakening? Maybe ZeuS will become less widespread, more exclusive, for a chosen few instead of the masses. No doubt, time will tell…

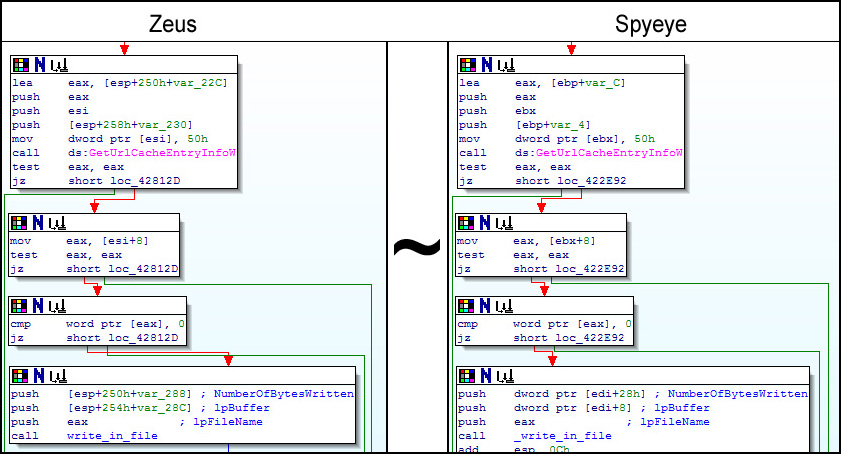



















ZeuS lives!