
On 9 April, 2015 Kaspersky Lab was involved in the synchronized Simda botnet takedown operation coordinated by INTERPOL Global Complex for Innovation. In this case the investigation was initially started by Microsoft and expanded to involve a larger circle of participants including TrendMicro, the Cyber Defense Institute, officers from the Dutch National High Tech Crime Unit (NHTCU), the FBI, the Police Grand-Ducale Section Nouvelles Technologies in Luxembourg, and the Russian Ministry of the Interior’s Cybercrime Department “K” supported by the INTERPOL National Central Bureau in Moscow.
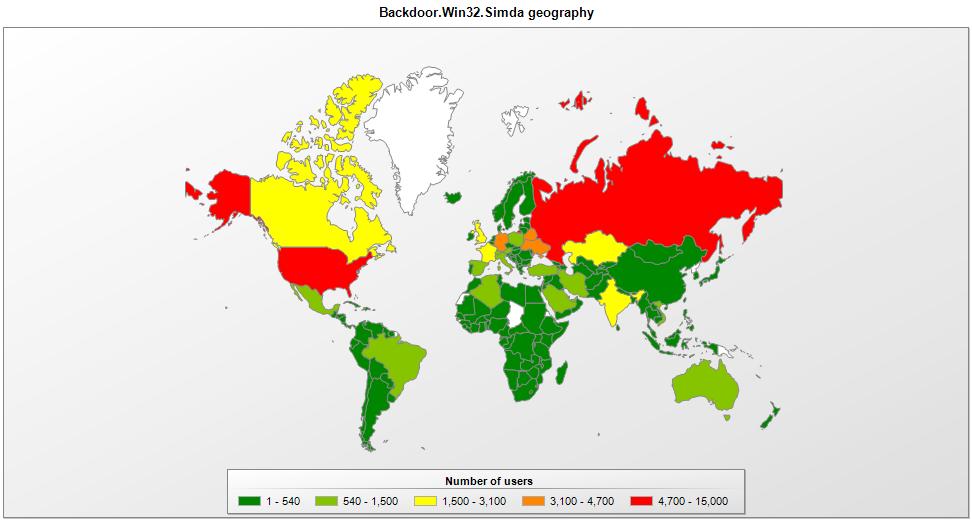
As a result of this takedown 14 C&C servers were seized in the Netherlands, USA, Luxembourg, Poland and Russia. Preliminary analysis of some of the sinkholed server logs revealed a list of 190 countries affected by the Simda botnet.
Simba character, courtesy of Walt Disney Productions, has nothing to do with Simda botnet
Simda is a mysterious botnet used for cybercriminal purposes, such as the dissemination of potentially unwanted and malicious software. This bot is mysterious because it rarely appears on our KSN radars despite compromising a large number of hosts every day. This is partly due to detection of emulation, security tools and virtual machines. It has a number of methods to detect research sandbox environments with a view to tricking researchers by consuming all CPU resources or notifying the botnet owner about the external IP address of the research network. Another reason is a server-side polymorphism and the limited lifetime of the bots.
Simda is distributed by a number of infected websites that redirect to exploit kits. The bot uses hardcoded IP addresses to notifying the master about various stages of execution process. It downloads and runs additional components from its own update servers and can modify the system hosts file. The latter is quite an interesting technique, even if it seems deceptively obvious at first glance.
Normally malware authors modify host files to tamper with search engine results or denylist certain security software websites, but the Simda bot adds unexpected records for google-analytics.com and connect.facebook.net to point to malicious IPs.
KL detected the #Simda #bot as Backdoor.Win32.Simda, it affected hundreds thousands victims worldwide
Tweet
Why is that, one might ask? We don’t know, but we believe that the answer is connected with Simda’s core purpose – the distribution of other malware. This criminal business model opens up the possibility of exclusive malware distribution. This means that the distributors can guarantee that only the client’s malware is installed on infected machines. And that becomes the case when Simda interprets a response from the C&C server – it can deactivate itself by preventing the bot to start after next reboot, instantly exiting. This deactivation coincides with the modification of the system hosts file. As a farewell touch, Simda replaces the original hosts file with a new one from its own body.
Now, curious mind may ask: how does it help them? Those domains are no longer used to generate search results, but machines infected by Simda in the past might occasionally continue to send out HTTP requests to malicious servers from time to time, even in when exclusive 3rd-party malware is supposed to have been installed.
We need to remember that these machines were initially infected by an exploit kit using a vulnerability in unpatched software. It’s highly likely that 3rd-party malware will be removed over time, but a careless user may never get round to updating vulnerable software.
If all those hosts keep coming back to the malicious servers and asking for web resources such as javascript files, the criminals could use the same exploits to re-infect the machines and sell them all over again – perhaps even ‘exclusively’ to the original client. This confirms once again – even criminals can’t trust criminals.
In this investigation Microsoft and various law enforcement bodies completed the sinkholing process and Kaspersky Lab willingly contributed to the preparations for the takedown. That work included technical analysis of malware, collecting infection statistics, advising on botnet takedown strategy and consulting our INTERPOL partners.
Kaspersky Lab detected the Simda bot as Backdoor.Win32.Simda and according to our estimations based on KSN statistics and telemetry from our partners it affected hundreds thousands victims worldwide.
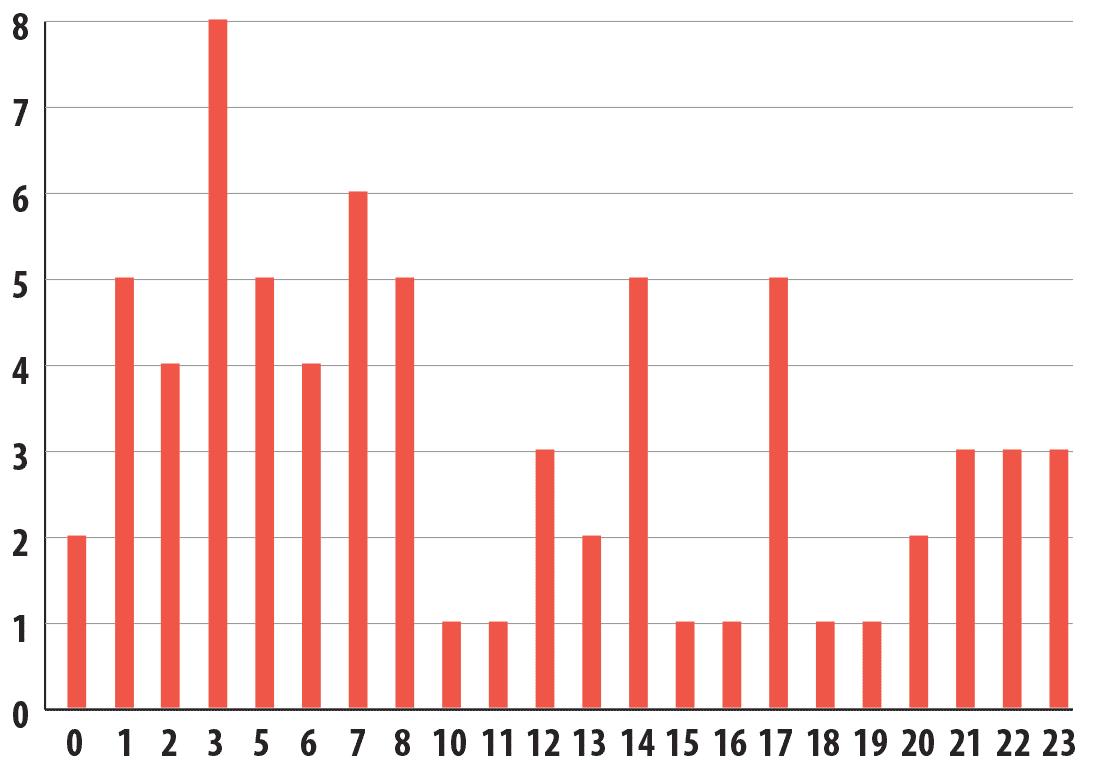
Simda is automatically generated on demand and this is confirmed by the absence of any order in compilation link times. Below is a chart generated from a small subset of about 70 random Simda samples:
Samples link times in UTC timezone
The increase in link times is most likely related to the activity of the majority of Simda victims located somewhere between UTC-9 and UTC-5 timezones, which includes United States.
Thanks to the sinkhole operation and data sharing between partners we have put up a page where you can check if your IP has connected to Simda C&C servers in the past. If you suspect your computer was compromised you can use one of our free or trial solutions to scan your whole hard drive or install Kaspersky Internet Security for long-term protection.
Kaspersky Lab products currently detect hundreds of thousands of modifications of the Simda together with many different 3rd-party malware distributed during the Simda campaign.
References:






















Simda’s Hide and Seek: Grown-up Games