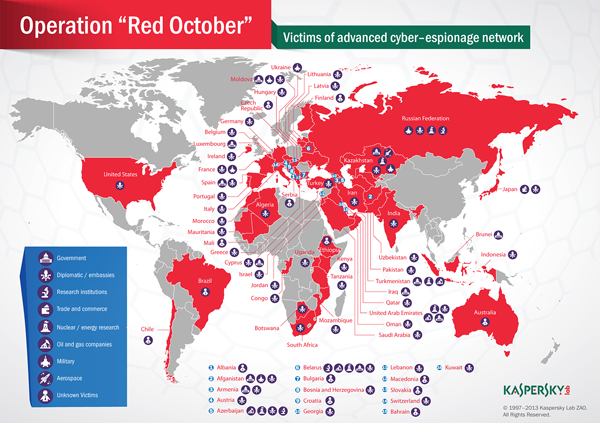
Since the publication of our report, our colleagues from Seculert have discovered and posted a blog about the usage of another delivery vector in the Red October attacks (http://blog.seculert.com/2013/01/operation-red-october-java-angle.html).
In addition to Office documents (CVE-2009-3129, CVE-2010-3333, CVE-2012-0158), it appears that the attackers also infiltrated victim network(s) via Java exploitation (35f1572eb7759cb7a66ca459c093e8a1 – NewsFinder.jar), known as the Rhino exploit (CVE-2011-3544).