
Over the past few weeks the AV industry has continued to focus its research efforts on the Stuxnet worm. We blogged about what we found while we were investigating the malware; our Stuxnet series may have come to an end, but that doesn’t mean we’ve stopped our research.
One of the things our research has identified is that Stuxnet uses several Windows zero-day vulnerabilities.
Yes, you read that correctly – several zero-day vulnerabilities.
Until now, most of the focus has been on the LNK/PIF vulnerability which Stuxnet exploits in order to spread via removable storage media and networks. But this has turned out not to be Stuxnet’s only surprise. The worm doesn’t just spread by using the LNK vulnerability. Once it’s infected a computer on a local network, it then attempts to penetrate other computers using two other propagation routines.
Firstly, Stuxnet is designed to exploit MS08-067, the same vulnerability used by Kido (aka Conficker) at the beginning of 2009. The exploit code that Stuxnet uses to target MS08-067 is slightly different to that used by Kido. However, what’s really interesting is the second propagation routine.
In addition to exploit code for MS08-067, Stuxnet contains an exploit for a previously unidentified vulnerability in the Print Spooler service; this vulnerability makes it possible for malicious code to be passed to, and then executed on, a remote machine. Two files (winsta.exe and sysnullevent.mof) appear on attacked systems. It’s not just the way in which the malicious code gets on to the remote machine which is interesting, but also how the code then gets launched for execution.
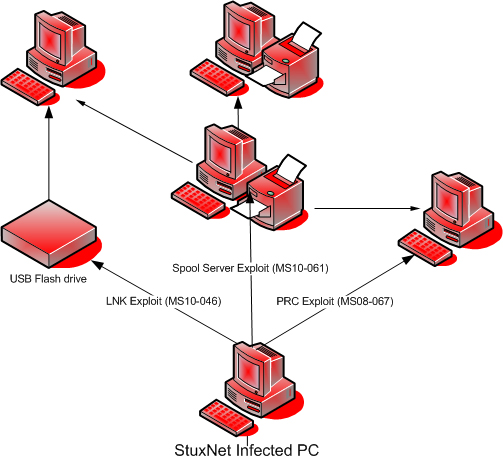
As soon as we identified the vulnerability we informed Microsoft about the problem and they confirmed our findings. The vulnerability has been identified as “Print Spooler Service Impersonation Vulnerability” and rated “critical”. Today Microsoft released MS10-061, a patch which fixes this vulnerability.
Analysis of the vulnerability shows that it’s computers with shared access to a printer which are at risk of infection.
During analysis, we searched our collection for other malicious programs capable of using this vulnerability. Happily, we didn’t find anything.
On top of all this, we’ve identified yet another zero-day vulnerability in Stuxnet’s code, this time an Elevation of Privilege (EoP) vulnerability. The worm uses this to get complete control over the affected system. A second EoP vulnerability was identified by Microsoft personnel, and both vulnerabilities will be fixed in a security bulletin in the near future.
The fact that Stuxnet uses four previously unidentified vulnerabilities makes the worm a real standout among malware. It’s the first time we’ve come across a threat that contains so many “surprises”. Add to this the use of Realtek and JMicron certificates, and remember that Stuxnet’s ultimate aim is to access Simatic WinCC SCADA systems.
Stuxnet was undoubtedly created by professionals who’ve got a thorough grasp of antivirus technologies and their weaknesses, as well as information about as yet unknown vulnerabilities and the architecture and hardware of WinCC and PSC7.
Together with Microsoft and other AV companies, so far we’ve spent more than two months looking at Stuxnet. We’ll be presenting our findings, including a detailed look at how the vulnerability works, at the end of the month at the Virus Bulletin conference.






















Myrtus and Guava, Episode MS10-061