
Introduction
In our crimeware reporting service, we analyze the latest crime-related trends we come across. If we look back at what we covered last month, we will see that ransomware (surprise, surprise!) definitely stands out. In this blog post, we provide several excerpts from last month’s reports on new ransomware strains.
Luna: brand-new ransomware written in Rust
Last month, our Darknet Threat Intelligence active monitoring system notified us of a new advertisement on a darknet ransomware forum.
As one can see from the advertisement, the malware is written in Rust and runs on Windows, Linux and ESXi systems. Armed with this knowledge, we went hunting for samples, finding a few via the Kaspersky Security Network (KSN).
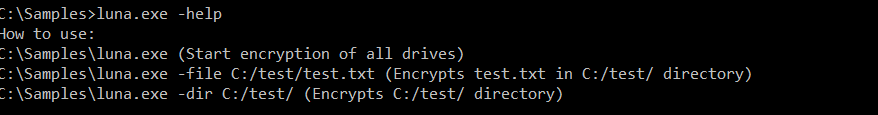
Command line options available in Luna
Judging by the command line options available, Luna is fairly simple. The encryption scheme it uses, however, is not so typical, as it involves x25519 and AES, a combination not often encountered in ransomware schemes.
Both the Linux and ESXi samples are compiled using the same source code with some minor changes from the Windows version. For example, if the Linux samples are executed without command line arguments, they will not run. Instead, they will display available arguments that can be used. The rest of the code has no significant changes from the Windows version.
The advertisement states that Luna only works with Russian-speaking affiliates. Also, the ransom note hardcoded inside the binary contains spelling mistakes. For example, it says “a little team” instead of “a small team”. Because of this, we assume with medium confidence that the actors behind Luna are speakers of Russian. Since Luna is a freshly discovered group, there is still little data on its victimology, but we at Kaspersky are following Luna’s activity.
Luna confirms the trend for cross-platform ransomware: current ransomware gangs rely heavily on languages like Golang and Rust. A notable example includes BlackCat and Hive. The languages being platform agnostic, the ransomware written in these can be easily ported from one platform to others, and thus, attacks can target different operating systems at once. In addition to that, cross-platform languages help to evade static analysis.
Black Basta
Black Basta is a relatively new ransomware variant written in C++ which first came to light in February 2022. The malware, the infrastructure and the campaign were still in development mode at the time. For example, the victim blog was not online yet, but the Black Basta website was already available to victims.
Black Basta supports the command line argument “-forcepath” that is used to encrypt only files in a specified directory. Otherwise, the entire system, with the exception of certain critical directories, is encrypted.
Two months after the first encounter, in April, the ransomware had grown more mature. New functionality included starting up the system in safe mode before encryption and mimicking Windows Services for persistence reasons.
The safe-mode reboot functionality is not something we come across every day, even though it has its advantages. For example, some endpoint solutions do not run in safe mode, meaning the ransomware will not be detected and files in the system can be “easily” encrypted. In order to start in safe mode, the ransomware executes the following commands:
- C:\Windows\SysNative\bcdedit /set safeboot networkChanges
- C:\Windows\System32\bcdedit /set safeboot networkChanges
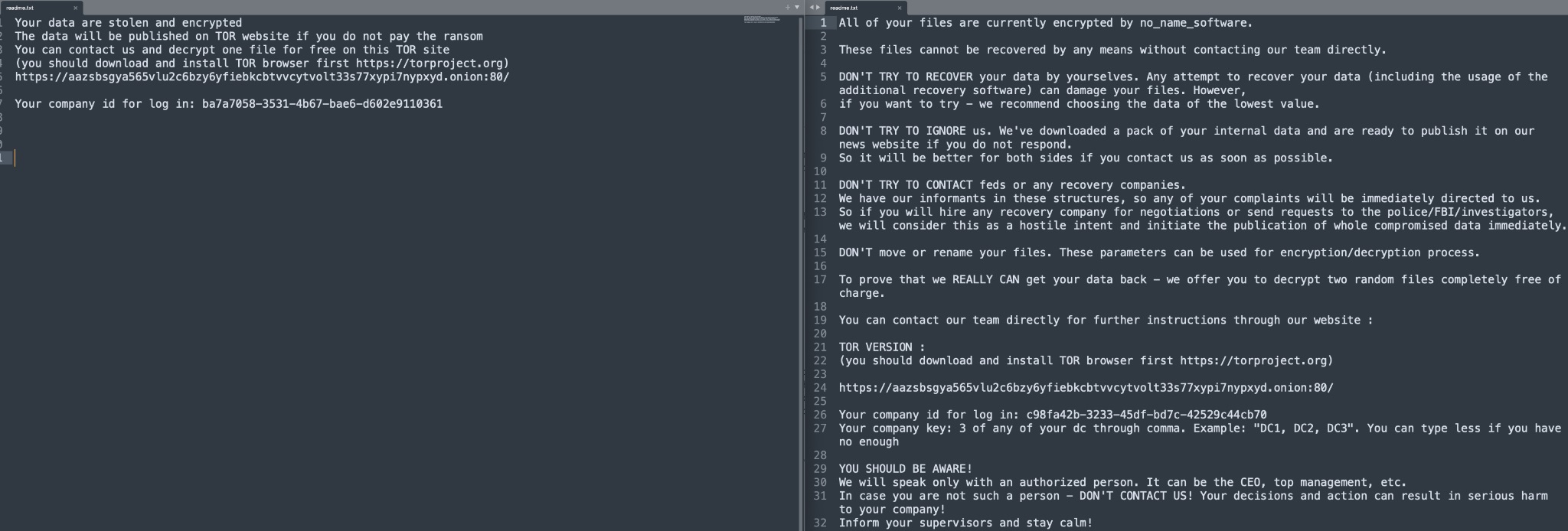
Earlier versions of Black Basta contained a different rescue note from the one currently used, which showed similarities to the ransom note used by Conti. This is not as odd as it may seem, because Black Basta was still in development mode at the time.
Rescue notes comparison
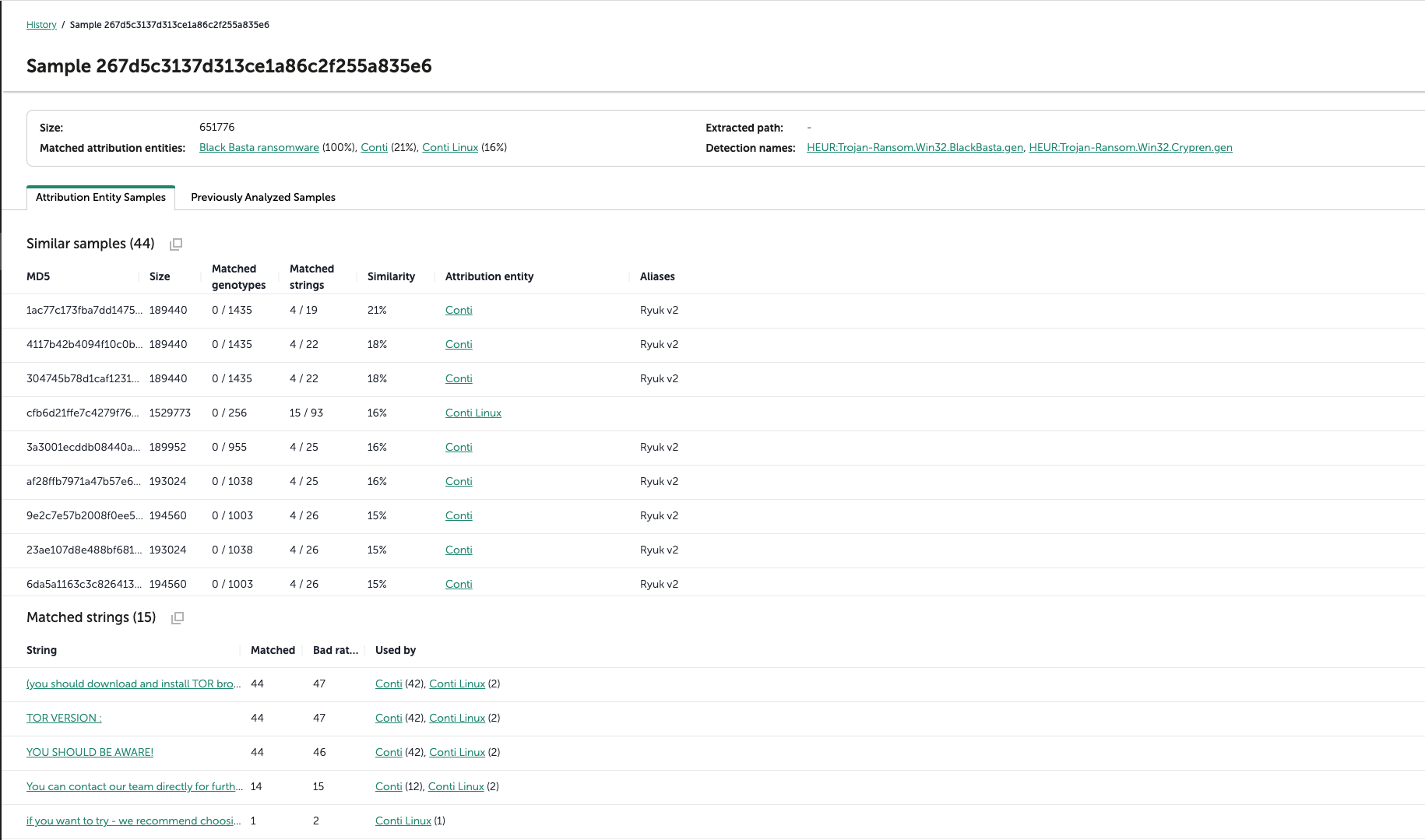
To ascertain that there was indeed no code overlap between Conti and the earlier versions of Black Basta, we fed a few samples to the Kaspersky Threat Attribution Engine (KTAE). Indeed, as shown below, only the strings overlap. There is thus no overlap in code per se.
Overlap with Conti ransomware
Black Basta for Linux
In another report we wrote last month, we discussed the Black Basta version for Linux. It was specifically designed to target ESXi systems, but it could be used for general encryption of Linux systems as well, although that would be a bit cumbersome.
Just like the version for Windows, the Linux version supports only one command line argument: “-forcepath”. When it is used, only the specified directory is encrypted. If no arguments are given, the “/vmfs/volumes” folder is encrypted.
The encryption scheme for this version uses ChaCha20 and multithreading to speed up the encryption process with the help of different processors in the system. Given that ESXi environments typically use multiple CPUs to execute a VM farm, the malware’s design, including the chosen encryption algorithm, allows the operator to have the environment encrypted as soon as possible. Prior to encrypting a file, Black Basta uses the chmod command to get access to it in the same context as the user level.
Black Basta targets
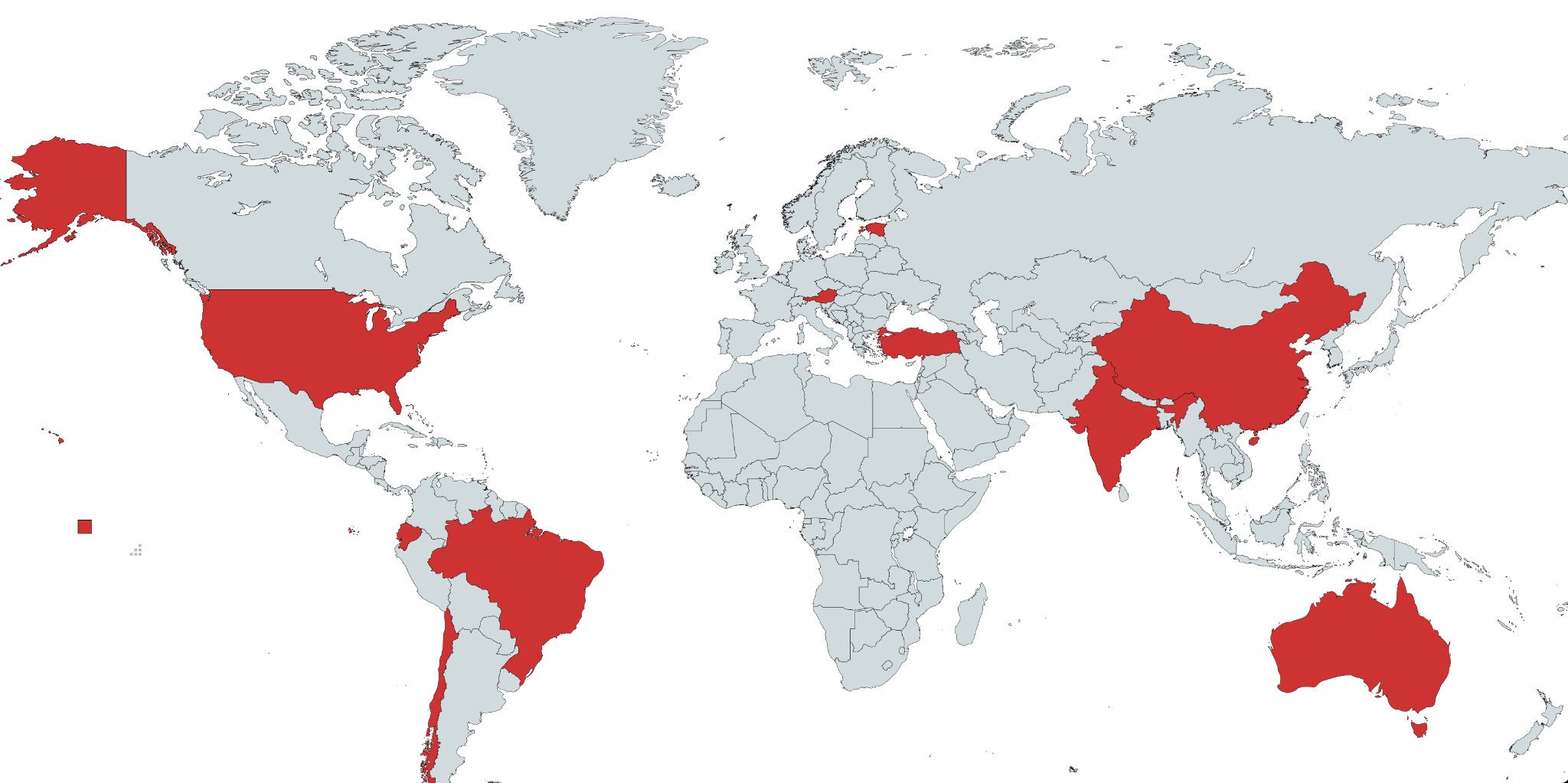
Analysis of the victims posted by the Black Basta group revealed that to date, the group has managed to attack more than forty different victims within a very short time it had available. The victim blog showed that various business sectors were affected including manufacturing, electronics, contractors, etc. Based on our telemetry, we could see other hits across Europe, Asia and the United States.
Conclusion
Ransomware remains a big problem for today’s society. As soon as some families come off the stage, others take their place. For this reason, it is important to stay on top of all developments in the ransomware ecosystem, so one can take appropriate measures to protect the infrastructure.
A trend, which we also discussed in our previous blog post, is that ESXi systems are increasingly targeted. The aim is to cause as much damage as possible. Luna and Black Basta are no exceptions. We expect that new variants will support encryption of VMs by default as well.
For questions or more information about our crimeware reporting service, please contact crimewareintel@kaspersky.com.
Luna and Black Basta — new ransomware for Windows, Linux and ESXi






















gnanasekar
share report
Securelist
Hi Gnanasekar!
If you want to receive private reports on Luna and Black Basta, please, contact our crimeware reporting service: crimewareintel@kaspersky.com