
- Malware evolution in 2007
- Trend of the year: the evolution of malicious programs targeting players of online games
- Spam report
- Malware which spreads via email
Email is known to be one of the most popular infection vectors. Besides malicious programs attached to messages, email is linked to other threats such as phishing and messages containing links to infected web pages. Finally, spam which uses social engineering techniques to get users to perform specific actions is also a threat. This article specifically analyses malware which is distributed via email.
Countries which act as a source of email malware
First of all it is important to get an overview of which countries act as a source of infected messages. The figure below shows countries ranked according to the quantity of malicious files sent from servers located in a specific geographical location.
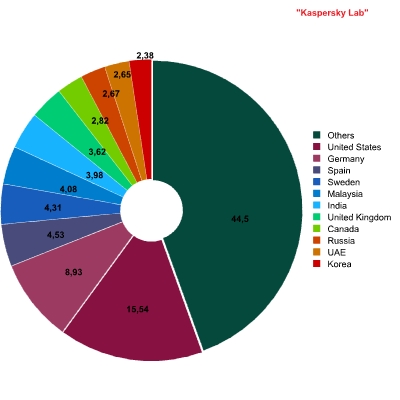
Source countries of infected emails
The Top Five includes the USA, Germany, Sweden, Spain and Malaysia. It should be noted that infected emails may stay within the country from which they are sent. It therefore wouldn’t be justified to conclude that the leaders of the rating pose as much of a threat to the rest of the world as they do to users in the country concerned.
Malicious programs distributed via email
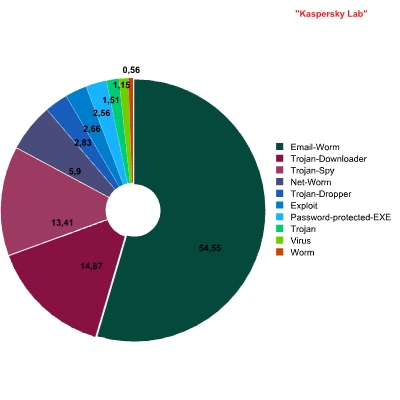
Malicious mail traffic: breakdown of malicious programs by behavior
Kaspersky Anti-Virus is installed on mail servers around the world. The figure above shows the Top 10 verdicts returned by the solution, giving a picture of the most widespread malicious behaviors of programs distributed via email. These leading behaviors represent an overwhelming majority of malicious programs detected in mail traffic, with other detections making up 1% of the total volume of infected attachments.
The Top 10 behaviors are examined in more detail below.
Email worms
Email worms make up more than half of all malware spread via email (55%). This leading position is justified; this type of malicious program is not only circulated via mass mailings by cyber criminals but is also capable of self-propagation.
It should be noted that according to the Kaspersky Lab classification system, programs which have functionality in addition to Email worm functionality, such as Net-Worm and Worm, are viewed as
being more of a threat. In such cases, distribution via email is an additional function. Consequently, representatives of the Net-Worm (6%) and Worm (0.56%) behaviors detected in mail traffic can be considered as self-replicating programs. This means that in actual fact, the percentage of malicious programs with email worm functionality is higher than 55 %. Among malware spread via email, more than 61% of the total is made up of are self-replicating programs.
In 2007, the general trend of email worm propagation was marked by sharp peaks and troughs in the number of email worms. The figure below shows the number of new malicious programs which exhibit Email-Worm behavior.
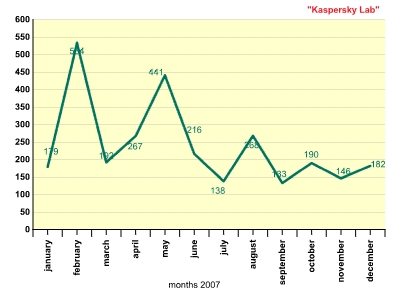
Number of new malicious programs with Email-Worm behavior
The three peaks illustrate bursts of activity on the part of the authors of Email-Worm.Win32.Zhelatin. This worm, known also as the Storm Worm, became the leader in 2007 among email worms for the number of variants of new malicious files.
Distribution of email worms by family
Zhelatin (Storm Worm)
The authors of Zhelatin chose a new strategy to ensure that their creation would manage to survive. The cyber criminals must have created a malicious code production line, which made it possible to release new versions of the malicious code faster than antivirus database updates. New malicious programs developed on the production line were tested against an antivirus program. Samples which were detected by the program were rejected as defective, and those which successfully passed the test, were automatically copied to several special web servers in the Internet used to distribute new versions of the program.
Zhelatin has become a kind bench mark in the evolution of malicious programs. The authors have implemented all their achievements from the past few years. From the very beginning, Zhelatin was designed to harvest email addresses from a victim computer and send them to the Internet (with these addresses clearly being harvested for onward sale to spammers). Later, the virus writers used the updated version of Zhelatin to develop a network of zombie computers (botnet). Such botnets are, in some senses, unique. These are peer-to-peer zombie networks, where zombie computers connect to the command and control center only is if it available. If the server is not found or is not currently functioning, the zombie machines can connect to each other, transmitting data onwards. Each zombie computer has a short list of the nearest neighbors which it communicates with. The virus writers did not include any malicious payload in the worm, but they made in invisible to the user by using rootkit technology within their malicious program.
A year before the so-called Storm Worm appeared we anticipated the appearance of a production line for malicious code. We didn’t publicize this fact due to the potential threat, and we were getting ready in preparing ourselves to resist the threat. The core of the problem is in the malicious code used to create new versions of the malicious program. This code is physically inaccessible to us, meaning it can’t be analyzed in order to produce a subprogram to detect it as we usually do in case of polymorphic viruses. This was a cause for concern long before Email-Worm.Win32.Zhelatin appeared.
It should be noted that Zhelatin wasn’t the first to use such an approach. Last year, Email-Worm.Win32.Warezov, which was very similar, started spreading actively September-October. On some days we were detecting dozens of new variants of this worm. It was clear that a new era had started. In 2007 Warezov and Zhelatin were the main culprits to blame for the increased number of new families of malicious programs with Email-Worm functionality. This is shown in the graph below.
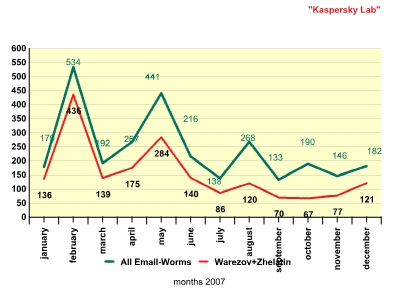
Number of new Email-Worm programs: Warezov and Zhelatin
As the graph shows, the line illustrating the number of new Zhelatin and Warezov files is practically the same as the line showing the number of new Email-Worm programs.
The email worm situation is fairly clear: such programs exist and they are not going to disappear in the near future, although there is no clear trend that indicates that numbers will suddenly increase. Such increases occur spontaneously, as is shown in the graph above.
Malicious programs exhibiting other behaviors
Second place in the list of the most widespread behaviors is occupied by Trojan-Downloader (15%). These are universal downloading programs designed to download any malicious code from the Internet. The tactic of mass mailing a Trojan-Downloader rather than a specific malicious program increases the chances of virus writers finding an infectable machine. Trojan-Downloader programs first disable antivirus protection and then download another malicious program via the Internet and launch it on the victim machine. If the Trojan-Downloader succeeds in disabling the antivirus program on an infected computer, it can download any program including well-known ones that could be detected by any antivirus program. So the writers of malicious code do not have to develop new versions of a specific malicious program; it’s enough to use a compact and simple Trojan-Downloader instead. Developing such programs require a minimum of effort which is why they are so widely used.
Trojan-Downloader is closely followed by Trojan-Spy programs (13%). These programs are designed to steal confidential information both from corporate computers with the aim of accessing a corporate network and from personal computers so that cyber criminals can use the data for their own ends.
The next three behaviors are far behind the leaders, each making up 3% of malicious code in mail traffic.
Trojan-Dropper. Programs with this behavior are similar to Trojan-Downloader programs; they are designed to install malicious programs on the victim machine. The only difference is the method used to deliver the malicious program: Trojan-Dropper programs carry another malicious program inside themselves, while Trojan-Downloader programs (as the name suggests) download it from the Internet. Statistics show that cyber criminals prefer to use Trojan-Downloader programs, which provide the opportunity to update the malicious code which is placed online.
Exploit. Interestingly enough, this behavior is fairly rare in mail traffic, and messages containing such code are usually mailed in the course of targeted hacker attacks. Today exploits are gaining popularity because the number of users who launch executable files from attachments is decreasing. Exploit programs are used by cyber criminals to run code on a user’s computer when he opens a message. The user does not need to save an executable file and launch it from disk; everything happens automatically, without the user’s knowledge or consent. We anticipate that in the future the share of exploit code in malicious mail traffic will increase and more than likely, in a few years, exploit code will be in the leading position among malware sent via email.
It is rather surprising that the Top 10 includes Password-protected-EXE. The verdict itself does not indicate specifically that the file itself is malicious. This special verdict is returned by the antivirus program to warn the user of a potential risk. Password-protected-EXE denotes self unpacking archives with a password. To launch this program, the user is required to enter a password so that the program can extract one or more files to be executed. Many malicious programs are distributed in just such self unpacking archives with the password given in the text of the message. This is done to prevent antivirus programs which scan mail traffic from unpacking the archive and detecting the malicious program it contains.
The Top 10 rankings are closed by programs which fall into the TrojWare (1.51%) and VirWare (1.15%) classes. TrojWare includes a range of Trojan programs for which the behavior cannot be otherwise categorized in another class. Consequently, these are of little interested. Files exhibiting Virus behavior are usually files which become infected on the victim machine. This means that they are mailed by a user who is not aware that s/ he is sending infected files.
The most widespread families in infected mail traffic
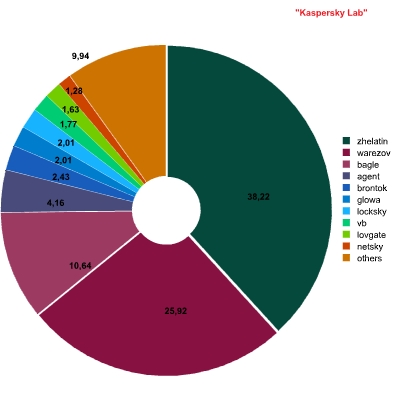
The figure below shows a breakdown of the Top 10 malicious programs by family (behavior is not taken into account here):
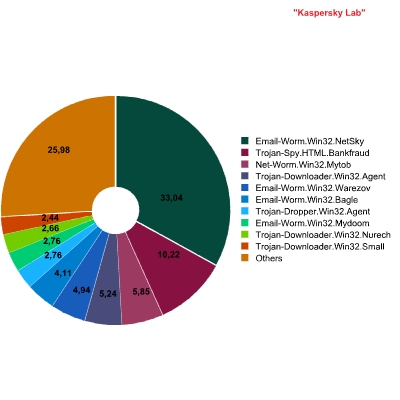
Breakdown of malicious programs in mail traffic by family
In spite of the fact that in 2007 Zhelatin was the undoubted leader in terms of the number of variants of malicious files, it does not fall into the Top 10 when this ranking is calculated according to the total number total number of files in mail traffic. The leader here is a veteran – Worm.Win32.Netsky. Next are mailings of fraudulent messages, allegedly sent by banks, which are classified as Trojan-Spy.HTML.Bankfraud.
Out of the two email worms which caused the greatest stir this year, Zhelatin and Warezov, only Worm.Win32.Warezov makes the list, and then only in fifth place.
Zhelatin was unable to beat Warezov. More than likely, the authors of Zhelatin authors were not attempting to make their program a dominant force in infected mail traffic. However, their implementation of the email worm function can hardly be called successful when compared to other functions of the malicious program.
Conclusion
Given the data above, there are some points which should be highlighted in conclusion.
First of all, in 2006 the approach to creating malicious code changed. Cyber criminals started developing programs which could automatically create malicious code at specified intervals. Although it wasn’t anticipated that such a production line would stay in existence long, it has and the mechanism used to create new variants of Warezov continues to function. In 2007, the successor to Warezov – Zhelatin – made an appearance, and this program was developed in a similar way. However, the epidemics caused by these two worms are on the wane, meaning that antivirus companies have found ways of neutralizing such malicious activity.
Another significant change is the growing interest in the active use of exploit code. The share of exploits spread via email is growing; this is an alarming trend because the widespread use of such code presents a threat to all users. Such code can be used both by beginners and more experienced malicious users to infect victim machines.
Overall, the level of interest in using email as an infection vector is declining. This is a result of the growing number of new Internet services. Malicious programs are released into the vastness of the Internet rather than the narrower channels of mail traffic. But this does not mean that we can forget about malicious programs which spread via email. If we let our guard down for a minute, we could miss changing trends which are critical in combating malicious code.





















Kaspersky Security Bulletin 2007. Malware which spreads via email