
2006: an overview
In 2006 several important events relating to mobile malware took place, and these events will set the evolutionary trend for the next few years.
- Commercial Trojans created for Symbian
- Malicious users began to steal money from mobile users’ accounts
- Malicious programs for standard (i.e. non-smartphone) mobile phones appeared.
The Year in Statistics
In fall 2005, Kaspersky Lab analysts forecast that the future would bring a steady stream of malicious programs similar to those already known, with a very occasional technically innovative program. An additional motivation for virus writers would be economic gains which could, for instance, be made from the widespread use of mobile telephones to make e-payments. However, it was expected that a global epidemic of mobile malware wasn’t likely to be a real threat for a couple of years.
The following figures on mobile malware (according to Kaspersky Lab classification) prior to 2006 are as follows:
- Known number of mobile virus families: 22
- Known number of variants and modifications within these families: 10
- Known number of platforms /operating systems attacked: 2 (Symbian and WinCE)
In early 2006, a considerable increase in the number of malicious programs for mobile devices was noted. 43 variants of different mobile viruses appeared in February – April alone. At the peak of their activity, virus writers were providing antivirus companies with nearly ten new variants a week. Interestingly, Asian hackers turned out to be the most prolific. Overall, their programs stood out in terms of the platforms targeted and the moves made towards the relatively uncharted realm of mobile technologies.
It seemed that this rapid evolution would continue for some time, giving rise to the potential danger of mobile viruses being created in “assembly line” fashion, and reaching volumes similar to those shown by some computer viruses. However, in the second half of 2006, the appearance of new samples more or less came to a halt in terms of both known and new families.
This downward trend continued until the end of 2006, and resulted in a mere two to seven new variants of old malicious programs appearing each month. At the same time, the number of active mobile virus writers decreased considerably. At present, most new mobile malware is being created by just one or two people worldwide. This is why new variants do not tend to include technical innovations, leading to them being categorized as primitive Trojans.
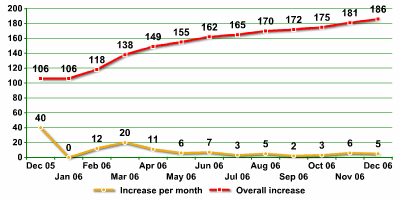
Increase in number of mobile virus variants in 2006
The statistics for mobile malware at the end of 2006 were as follows:
- Known number of mobile virus families: 35 (+13), up 37%
- Known number of variants and modifications: 186 (+80), up 45%
- Known platforms / operating systems: 4 (+2, J2ME and MSIL)
New technologies
Data theft
The era of commercial Trojans and spyware programs for Symbian has now dawned. The first fully functional spyware program was found in April. Its developers were selling it on their website for $50. Flexispy, once installed, has total control over a smartphone and sends cybercriminals information about calls made and SMS messages sent. In September 2006 a second, similar program for Symbian hit the scene: Acallno. This program harvests all text messages sent and received on the infected phone and forwards them to a designated number.
Financial theft
Virus writers have only demonstrated one of the many ways to steal money from mobile phone users. Unknown Russian hackers were the first to develop this technology; in February and September they were the ones who used premium number functionality ir order to steal money. In February they spread the RedBrowser Trojan, which was disguised as a utility that could be used to access the Internet via SMS. However, the program actually sent SMS to premium rate numbers, with $5 for every SMS being deducted from the subscriber’s account. Wesber, a Trojan with similar functionality, appeared in September 2006.
How mobile viruses spread
Previously, mobile viruses differed from computer viruses in using specific ways of propagating – via Bluetooth or MMS. However, the functionality of the .NET programming platform which is integrated into WinCE has enabled virus writers to exploit yet another, more traditional infection vector: email. The Letum worm behaves in exactly the same way as thousands of typical PC email worms, and once it gets onto a telephone, it sends itself to all the email addresses stored in the infected phone’s contact list. Furthermore, Letum could be classified as a cross-platform virus, as it is capable of running on computers running .NET.
Cross platform viruses
The Cxover virus is the first cross-platform malicious programs for mobile phones. When launched, it checks to see which operating system is running, and when launched on a PC, it looks for access to mobile devices via ActiveSync. The virus then copies itself to the mobile device using ActiveSync. Once it is on the telephone (or PDA), the virus attempts to perform the procedure in reverse, i.e. to copy itself to the PC. It can also delete user files on the mobile device.
The Mobler worm works a little differently. Once it’s launched on a PC (with a Win32 component), it creates a SIS file on the E: drive. The SIS file contains several empty files which are used to overwrite a number of system applications on the phone. The file also contains the worm itself which then copies itself to the phone’s memory card and adds a file called autorun.inf.
If a user connects a Mobler-infected phone to a computer and tries to access the phone’s memory card, the worm will automatically launch and infect the computer. Mobler is a clear example of a cross-platform virus capable of running on totally different operating systems: Windows and Symbian.
New platforms
Prior to 2006, the two most frequently attacked mobile platforms were Symbian and WinCE, which are the main smartphone platforms. The appearance of the RedBrowser Trojan in February 2006 was an unpleasant surprise. This was the first time that standard handsets (i.e. not smartphones) were infected. RedBrowser targeted mobiles which use the J2ME platform to run certain applications.
Although until recently it seemed an impossibility, infecting almost every kind of mobile phone is now a reality. The very appearance of Trojans for J2ME is just as worrying as the appearance of the first worm for smartphones in June 2004. It’s still difficult to assess all the potential threats. However, it’s a fact that the standard handsets still outnumber smartphones and malicious users have now worked out how to infect a standard phone and use it for criminal purposes. This means that antivirus protection for such devices is becoming a relevant issue.
In Spring the first proof of concept backdoor for BlackBerry devices was detected. However, it was written in Java, and therefore can’t really be classified as malicious code for a new platform.
Of the thirteen new families of mobile malware discovered by Kaspersky Lab in 2006, seven included technical innovations, and two of the seven were for new platforms.
| Innovation | Family | Month | OS | Functionality |
| + | Trojan-SMS.J2ME.RedBrowser | February 2006 | J2ME | Sends SMS |
| + | Worm.MSIL.Cxover | March 2006 | Windows Mobile / .NET | Deletes files, copies its body to other devices |
| – | Worm.SymbOS.StealWar | March 2006 | Symbian | Data theft, spreads via Bluetooth and MMS |
| + | Email-Worm.MSIL.Letum | March 2006 | Windows Mobile / .NET | Spreads via email |
| + | Trojan-Spy.SymbOS.Flexispy | April 2006 | Symbian | Data theft |
| – | Trojan.SymbOS.Rommwar | April 2006 | Symbian | Replaces system applications |
| – | Trojan.SymbOS.Arifat | April 2006 | Symbian | — |
| – | Trojan.SymbOS.Romride | June 2006 | Symbian | Replaces system applications |
| + | Worm.SymbOS.Mobler.a | August 2006 | Symbian | Deletes antivirus files, replaces system applications, replicates via memory cards |
| + | Trojan-SMS.J2ME.Wesber | September 2006 | J2ME | Sends SMS |
| + | Trojan-Spy.SymbOS.Acallno | September 2006 | Symbian | Data theft |
| – | Trojan.SymboS.Flerprox | October 2006 | Symbian | Replaces system boot files |
| – | not-a-virus:Tool.SymbOS.Hidmenu | October 2006 | Symbian | Application |
New mobile virus families in 2006
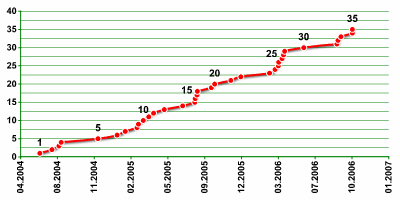
Increase in number of mobile virus families in 2006
Current situation
Cabir and ComWar are currently the main threats facing mobile users, and these worms have already been detected in about thirty countries around the world. They are not designed to steal money and do not cause direct financial damage (although ComWar spreads via MMS messages which the user is charged for). The authors of these programs have not yet found a way to benefit directly from their creations. Trojans which send text messages to premium numbers are simply aid numbers are really just the first attempts. Data stored on mobile phones is not of interest to most cybercriminals, and for the moment, it’s still easier to steal data from a PC than from a mobile phone.
Mobile viruses today are clearly in a state of calm before the storm. From a technical point of view, virus writers have already covered most of the bases in terms of virus functionality and environment. All popular mobile platforms are vulnerable to attack. The range of behaviors and functionality of known worms, Trojans and viruses have already reached a similar level to those demonstrated by computer viruses.
For now, the authors of mobile viruses are busy creating an insignificant stream of simple Trojan programs. As noted above, most activity is genereated by a few script-kiddies, which may lead to yet another wave of new variants of already known families (comparable to what we saw in December 2005 and Spring 2006). However, the factor that will determine exactly how mobile malware evolves in the future is still the number of smartphones on the market and the opportunities for making illegal profits using infected mobile phones.
Forecast
What will 2007 bring? The dangers for mobile users probably won’t increase very much. Mobile viruses are still at the initial “assembly line” stage of evolution and are likely to remain there for the next couple of years.
The threat to mobile users will increase in proportion to the popularity of smartphones. With time, the number of these devices will no doubt rise to hundreds of millions around the world. The inclusion of more and more new functions will lead to more people using smartphones the way people use their personal computers today. This will inevitably draw the attention of cybercriminals and ultimately lead to an increase in the number of Trojan programs for mobile phones.






















Kaspersky Security Bulletin 2006: Mobile malware