
In spite of their variety, all contemporary operating systems can be divided into two broad categories: Microsoft operating systems and Unix-type systems. This report provides an overview of malicious programs for Unix-type operating systems.
- Malware evolution
- Malware for Unix-type systems
- Mobile malware
- Internet attacks
- Spam in 2006
Linux is the most popular Unix-type system, and even though it is the main alternative to Windows, it is still predominantly used for server solutions. Like other Unix-type systems, Linux workstations are used by only a handful of enthusiasts and professionals. Virus writers and other cyber criminals have lost interest in Linux, since it is neither “underground” nor mainstream, which means there isn’t much money-making potential. This is why a large number of malicious programs for Linux in 2006 were proof of concept code and exploits for new vulnerabilities, in addition to recompiled versions of already extant malicious programs.
Truly new malware is rare in the *nix world, in spite of the fact that just as many vulnerabilities are found in Unix and Linux applications and kernels as are found in Windows. As long as the relatively limited popularity of such systems keeps cyber criminals focused on other operating systems, Unix users can sleep relatively peacefully. Of course, developers do attempt to patch vulnerabilities quickly and developers continue to release updates, but these updates have to be installed by the end user, who may not always follow through.
2006 overview
Every year, the total number of malicious programs increases. However, this does not apply to malware targeting Unix. Malicious programs for Unix represent just a small proportion of all malware, and in 2006 the number of malicious programs targeting Unix fell considerably.
In 2005 statistics for Unix malware were calculated on the basis of the number of malicious programs for Unix added to the Kaspersky Lab antivirus databases. This meant that all variants, even those which only differed slightly from each other, were counted as being new programs.
In 2006 the methods used to calculate the number of new malicious programs changed; only those programs which are not modifications of already existing programs count as new.
As a result, the total number of malicious programs targeting Unix systems fell 43% in 2006.
Malware for Unix platforms
The reduction in the number of new malicious files for Unix-type systems is even more pronounced when compared to the total amount of malicious programs in general, which climbed 41% over 2006. This figure is mainly composed of malware targeting Windows; the share of malware targeting Unix was even smaller. This is due to the low popularity of Unix among regular computer users (see above).
Linux is clearly the most popular Unix system, which is confirmed by the fact that the overwhelming majority of Unix malware is designed expressly for Linux. However, many malicious programs can easily be transferred to different Unix platforms, including OS X.
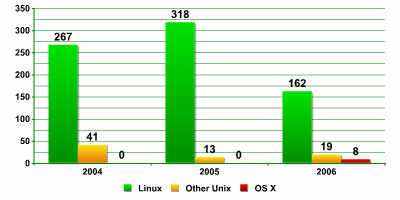
Number of malicious programs for Unix platforms
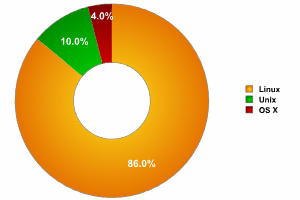
Breakdown of malware according to platform
The main difference in 2006 was the appearance of malware for OS X in the breakdown of malware targeting Unix-type systems. OS X is a relatively new operating system (it was first released in 2001) with a distinguished heritage (it evolved from Mach and FreeBSD). Apple’s transition to x86 processors greatly increased OS X’s popularity. In 2006 Kaspersky Lab also added OS X as a separate platform to its malware classification system.
Although malware for OS X represents just 4% of malware targeting Unix-type systems, this operating system is increasing in popularity and it seems that OS X will start edging in on the market share of other Unix systems, including Linux.
The downward trend in the number of malicious programs for Unix will continue until Unix systems become more popular among computer users. Virus writers and other cyber criminals currently have no incentive to write malicious code for Unix, since there isn’t much money to be made from just the relatively small number of users. This is also the reason why the search for Unix vulnerabilities is predominantly carried out by professional IT security researchers.
In November 2006 the Month of Kernel Bugs (MoKB) project was launched (http://projects.info-pull.com/mokb/). The aim of this project was to detect and disclose kernel vulnerabilities in various operating systems. This study showed that Linux ranked number one in terms of the number of vulnerabilities found (11), followed closely by OS X (10). The list also included FreeBSD, Sun OS, Microsoft and driver manufacturers.
The number of problems identified in both the Linux kernel itself and in Linux applications shows that virus writers are offered plenty of security loopholes to exploit using malicious code. It’s clear that in the future, Linux could face the same security issues as Windows.
Distribution of behaviors in malware targeting Unix platforms
Statistics show that the breakdown of different behaviors for Unix systems has not changed much over the past three years.
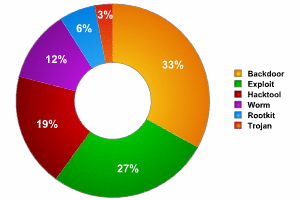
Distribution of behaviors in malware targeting Unix
Exploits and backdoors continue to make up the majority of malicious programs for Unix. Programs classified as Hacktool take third place in the list. Other behaviors – worms, Trojans and rootkits – have a share only slightly larger than hacktool programs. This breakdown is the same every year, and there were no surprises in 2006.
Backdoors represent such a large share because of some of the specific ways in which Unix machines are used: Unix is chiefly used for different servers. As a rule such servers provide remote access and other network services. A backdoor that is installed on one machine, and thus has root privileges, will provide full access both to the individual machine, and to all network resources as a result. Among other things, the infected computer can also be used as a spamming platform and to conduct subsequent attacks on other computers.
Exploits and hacker utilities can be used to identify vulnerabilities that malicious users can then take advantage of; this demonstrates that such programs can be used with both good and bad intentions. Security experts can use a program like Metasploit to test for vulnerabilities, but it can also be used by hackers. The network utility netcat can act as a backdoor on an infected computer, providing remote access.
Despite the fact that the source code of most malicious programs for Unix platforms can be found relatively easily, very few of them have evolved to any extent. New variants differ only very slightly from the original, and sometimes they have different binary code simply because the compiler options have been changed.
Just as with Windows, viruses for Unix are becoming rarer. Viruses are not even included in the breakdown in Figure 3 since there was just one virus for Unix found in 2006: Virus.Multi.Bi.
As the prefix ‘Multi’ in the name shows, this virus can infect more than one platform. Virus.Multi.Bi infects PE and Elf executable files. It is a non-resident virus written in assembler, and it’s relatively simple (it only infects files in the current directory). This is not the first cross-platform virus for Windows and Linux, although there are less than a dozen of this type of malicious programs.
Message displayed when the Bi dropper is launched on Windows
Contemporary networks are heterogeneous systems that use different platforms and operating systems. This is why there are more and more attempts to develop malicious code that will run on more than one platform. Cross-platform malicious programs may never become a common phenomenon, but the attempts to create them do allow us to make some conclusions about the evolution of malicious code in this area. The use of different script languages that make it possible to create code that will function on different operating systems (of course, the system must have a language interpreter) does enable the development of cross platform malicious code.
As noted above, most malicious code is designed in accordance with how specific platforms are used: for workstations, for home computers, or for servers. A change in usage will influence the evolution of malicious programs. If Linux suddenly becomes popular among desktop users, then cyber criminals will shift their focus towards this platform.
OS X — the platform of the future
Without a doubt, the transition to x86 architecture led to OS X becoming more popular. More and more users are looking towards Mac OS X as an alternative not only to Windows, but to Linux as well. Its appealing interface and stability will certainly attract a good number of new supporters. Security experts are also drawn to this relatively new platform – dyed in the wool researchers (both black and white hat) will always jump at the chance to study new platforms and technologies.
However, this very promising beginning did not have the expected ending: the transition to x86 architecture did not result in strong growth in the number of OS X users. As a result, OS X has not become a target of commercial interest among cyber criminals. But there have been some proof of concept malicious programs for this platform that deserve attention.
The first one appeared in February: IM-Worm.OSX.Leap. This worm spreads via the iChat instant messaging client and sends itself to those on the user’s contact list.
Message displayed when IM-Worm.OSX.Leap is launched
Another worm, Worm.OSX.Inqtana, appeared at roughly the same time as Leap. Inqtana is written in Java and spreads via Bluetooth, using the old CVE-2005-1333 vulnerability that was published back in May 2005.
Near the end of the year, Inqtana was followed by Worm.OSX.Niqtana, which was a variant of its predecessor and also spreads via Bluetooth. However it uses different vulnerabilities to do so: CVE-2005-0716 for OS X 10.3.x and CVE-2006-1471 for 10.4.x.
The appearance of another proof of concept program for OS X in November –Virus.OSX.Macarena – demonstrates new horizons in this field. Macarena was the first attempt to create a virus for Mac OS X that infects mach-o format executable files. The virus only infects files in the current directory and only runs on Intel platforms, i.e. it does not pose a threat to machines with ppc architecture.
These malicious programs are purely proof of concept code, i.e. they demonstrate that such programs can be created. In the future we can expect programs of this type to appear in the wild, and both users and developers of OS X will have to take a more serious approach to security issues. Even though the malicious programs mentioned above have not yet been found in the wild, the number of users which supported the view that Macintosh is safer than Windows fell markedly.
Conclusions and forecast
In terms of malicious code activity, the year 2006 was quite uneventful for the Unix community. There were no epidemics, major outbreaks, or other events which seriously threatened security.
However, Unix users should still take security seriously. There are just as many opportunities to write malicious code for Unix-type systems as there are for Windows. Software developers regularly issue updates that correct errors in their products, but users still have to install and configure them correctly.
To some extent 2006 was a year in which we expected to see the widespread introduction of new technologies such as Mac OS X for x86 and 64-bit processors and operating systems. While these technologies have not had a major impact on the computer world just yet, we definitely expect some changes in the future. And both computer security experts and malicious users are waiting in anticipation.
Below is our list of predictions for 2007:
- Mac OS X, which was eagerly anticipated, is still the operating system with the most potential and a certain percentage of both Windows and Linux users may shift to Mac OS X in 2007.
- Once Linux starts being used on other devices such as mobile phones, in on board car computers and gaming consoles such as PS3, we will start seeing more malicious programs targeting these types of devices.
- Cross-platform programs may also be developed further, since malicious users will want to reach as many users as possible.
- New infection vectors such as Bluetooth, WiFi and Skype will be used to spread malicious programs.
New technologies will continue to enter the market and they will in turn provide more opportunities for all kinds of use, including abuse by cyber criminals. Of course, we hope the number of malicious programs for Unix systems will continue to fall, but not at the cost of the popularity of Unix platforms.





















Kaspersky Security Bulletin 2006: Malware for Unix-type systems