
In 2013 we conducted our first in-depth research into the financial cyber-threat landscape. At that time we registered a sudden surge in the number of attacks targeting users’ financial information and money. The financial cyber threats landscape was discussed in detail in Kaspersky Lab’s “Financial Cyber-threats in 2013” report.
In 2014, the situation changed considerably: the number of attacks and attacked users significantly decreased, as did the amount of financial phishing. The key findings of the study into the financial cyber-threat landscape in 2014 are as follows:
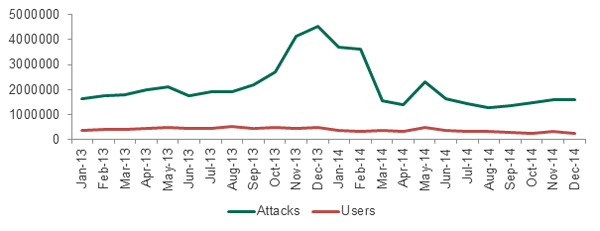
Attacks with Financial malware in 2013 and 2014
Financial phishing attacks
- In 2014 financial phishing attacks, which include phishing that targets Banks, Payment Systems and E-shops, accounted for 28.73% of all phishing attacks (a decrease of 2.72 percentage points).
- Bank-related phishing accounted for 16.27% of all attacks.
- The amount of phishing against Payment Systems increased 2.4 p.p. (from 2.74% in 2013 to 5.14% in 2014)
Financial malware attacks
- In 2014 Kaspersky Lab products detected 22.9 million attacks involving financial malware against 2.7 million users. This represents a YoY decrease of 19.23% for attacks and 29.77% of users.
- Among the total number of users subjected to all types of malware attacks, 4.86% of users encountered attacks involving some kind of financial threat – that’s 1.34 percentage points less than in 2013.
- The amount of Banking malware rose 8.89 percentage points to 75.63% of all financial malware attacks in 2014.
- The number of attacks involving Bitcoin mining malware tripled: from 360,065 attacks in 2013 to 1,204,987 in 2014
There are several possible reasons for these changes. First of all, law enforcement agencies around the world actively prosecuted cybercriminals who were spreading financial malware and phishing. In particular, last summer, law enforcement agencies in the US and the UK stopped the activities of two dangerous malicious campaigns – Gameover / Zeus and Shylock.
The second reason for the decline in the number of attacks might be a shift in the cybercriminals’ focus – instead of attacking end-users they are now pursuing organizations that work with financial information and payment tools. Throughout the year there were frequent reports of malicious attacks on large stores, hotel chains and fast food restaurants that serve millions of customers a day. In each case the fraudsters used malicious software that could steal bank card data directly from the memory of the POS terminals used by the organizations under attack. Banks became yet another “new” cybercriminal target. In 2014, Kaspersky Lab investigated several attacks targeting banks rather than their users’ accounts. Neither of these “new” types of attack prompted a rash of new AV detections simply because there are so few organizations involved compared with the number of private users running antivirus solutions, so it is difficult to compare the number of attacks. Nevertheless, the damage from such attacks amounted to millions of dollars so this threat can hardly be dismissed.
#Cybercriminals are less interested in “mass” malicious attacks, preferring fewer, more “targeted” #attacks #KLreport
Tweet
A third possible reason for the reduced number of cyberattacks lies in a general trend observed by Kaspersky Lab specialists in 2014. According to the company’s experts, cybercriminals are less interested in “mass” malicious attacks on users, preferring fewer, more “targeted” attacks. This is shown by the increased levels of targeted phishing: fraudsters only go after a specific group of users (for example, online banking users) rather than spreading mass mailings with malicious links.
This tactic suggests that a selective malicious mailing is less likely to be detected by IT security specialists and the lifespan of malicious links and malware samples will be extended. The trick is not always successful, but one consequence of its use is a decline in the absolute number of registered cyberattacks.
Android financial malware attacks
And what about mobile financial threats?
First of all, when we talk about mobile cyberthreats we focus on Android cyberthreats. According to Kaspersky Lab experts, more than 99% of mobile malware they are aware of is designed to attack Android devices.
48.15% of the attacks against #Android users utilized malware targeting financial data (Trojan-SMS, Trojan-Banker)
Tweet
In 2014 Kaspersky Lab and INTERPOL released a joint study on Mobile Cyberthreats which – among others – covered financial malware targeting Android users. According to the findings, there were 3,408,112 attacks against 1,023,202 users recorded in the period from August 1st, 2013 to July 31st 2014. About 500,000 users have encountered Android malware designed to steal money at least once. More than half a year has passed since the end of the period covered by the Kaspersky Lab / INTERPOL study and here is how things changed since:
- 48.15% of the attacks against users of Android-based devices blocked by Kaspersky Lab products utilized malware targeting financial data (Trojan-SMS and Trojan-Banker)
- In comparison with 2013 the number of financial attacks against Android users increased 3.25 times (from 711,993 to 2,317,194 attacks) and number of attacked users was up 3.64 times (from 212,890 to 775,887 users)
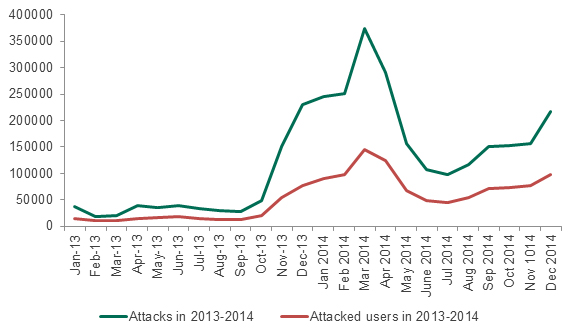
Attacks against users of Android-based devices in 2013 and 2014
In other words, the ever-increasing numbers of financial attacks against users of Android-based devices is a strong trend that shows no sign of declining.
Read more about financial cyber-threats in 2014 in our whitepaper.





















Financial cyber threats in 2014: things changed