
As cyberattacks become more sophisticated, and security solutions require more resources to analyze the huge amount of data gathered every day, many organizations feel the need for advanced security services that can deal with this growing complexity in real time, 24/7.
This article contains some analytical findings from Managed Detection and Response (MDR) operations during Q4 2020.
What is Kaspersky MDR
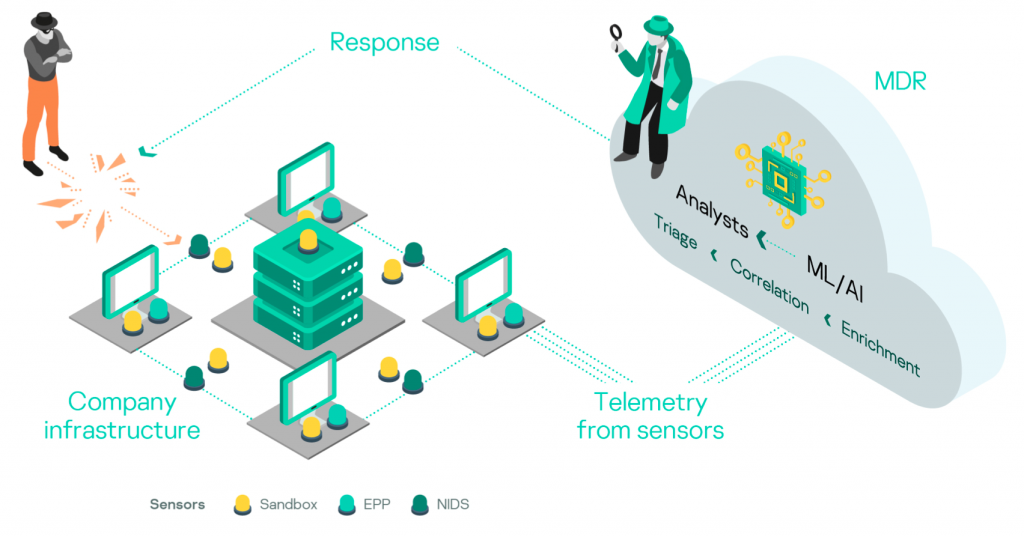
Kaspersky MDR uses Kaspersky Endpoint Security and Kaspersky Anti Targeted Attack Platform as low-level telemetry suppliers after MDR license activation. Raw telemetry is initially enriched and correlated in the cloud, then two levels of SOC analysis process the resulting alerts. The first level of SOC analysis is a neural network-based supervised ML model that is trained on alerts investigated by human analysts. The second level consists of on-duty SOC analysts, who triage alerts and provide recommendations on response to customers.
The MDR team also has a dedicated group for threat-hunting activities — proactive searching for threats through raw telemetry to find attacks that were not detected by automated logic, including ML/AI in the MDR cloud infrastructure. The threat-hunting team is responsible for detection engineering, so all threats found manually are then covered with automatic detection and prevention logic to speed up customer protection.
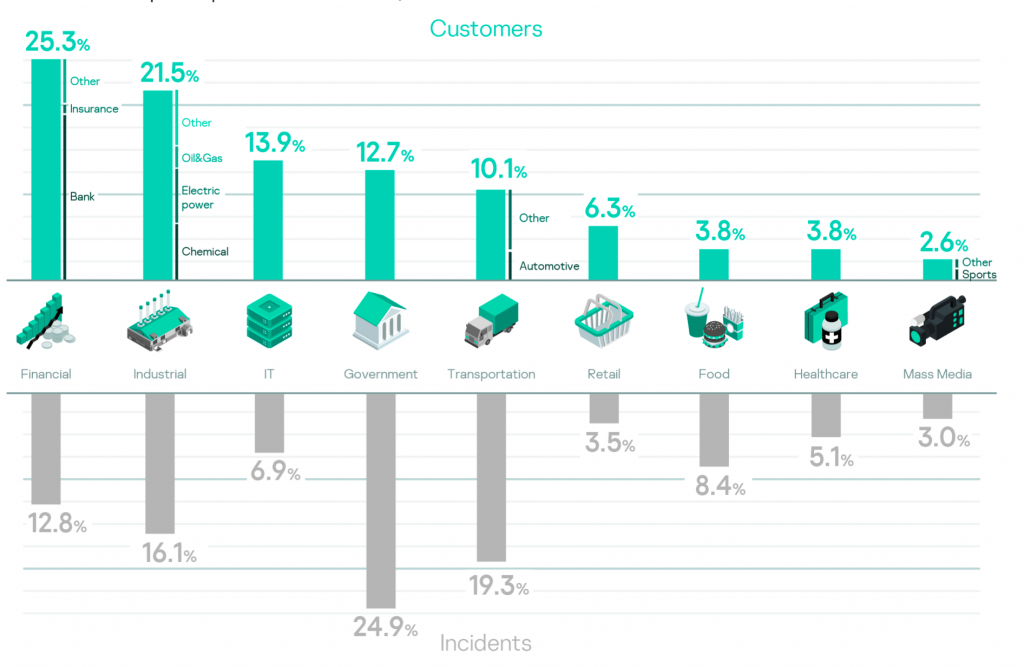
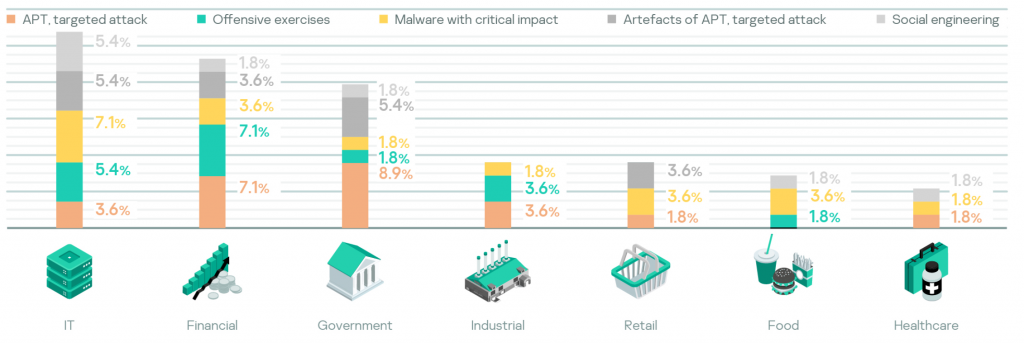
During the reporting period, Kaspersky MDR was used across all industry verticals as shown below along with the share of detected incidents for each.
Data processing pipeline and security operations
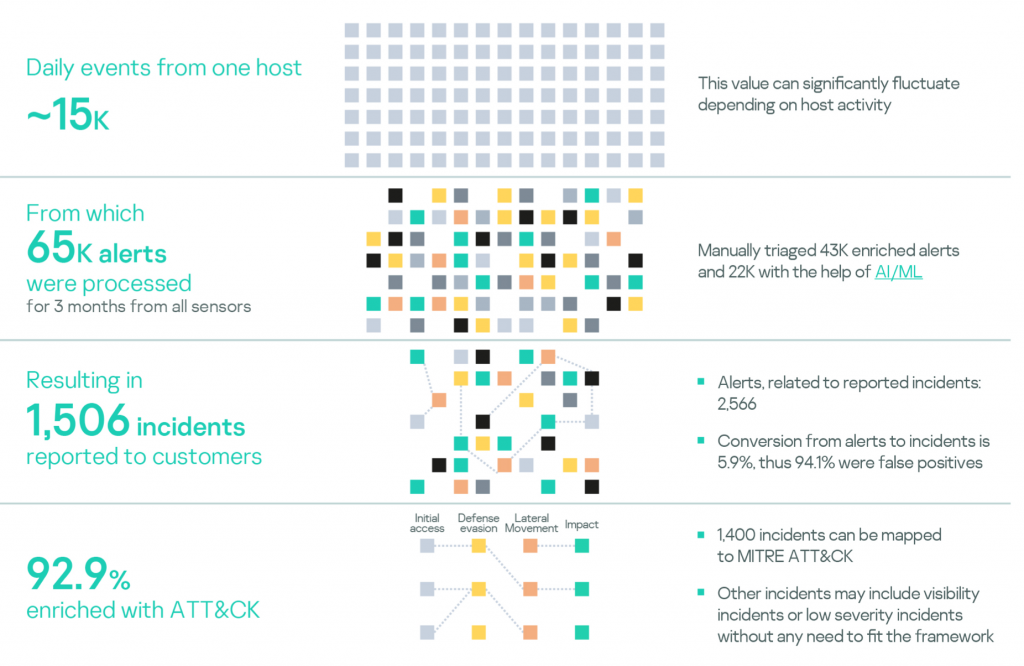
In Q4 2020, the average number of collected raw events from one host was around 15 000. This comparatively low amount is explained by comprehensive analysis performed by Kaspersky Endpoint Security right at the endpoint, such as objects reputation checks, and the fact that only a required minimum of telemetry is sent to the cloud for further analysis.
During the reported period, MDR processed approximately 65 000 alerts, followed by an investigation that resulted in 1 506 incidents reported to customers, approximately 93% of which were mapped to the MITRE ATT&CK framework.
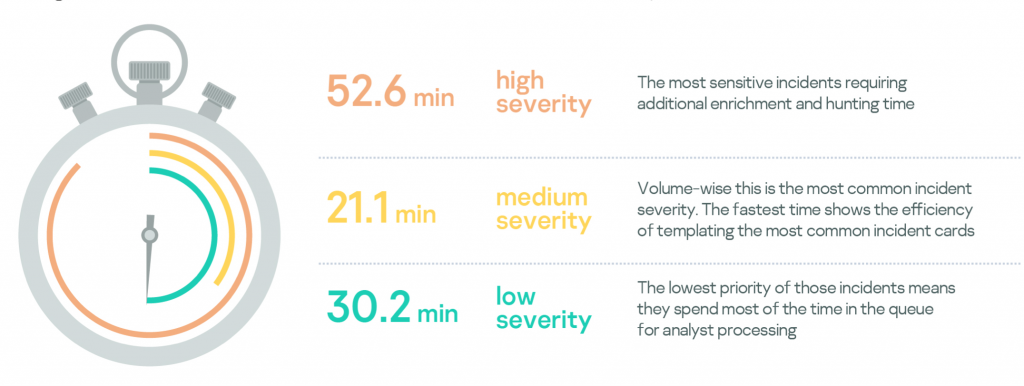
From a security operations standpoint, incident processing depends on alert severity. High severity typically requires more time to investigate and provide recommendations on remediation steps.
Incident remediation efficiency
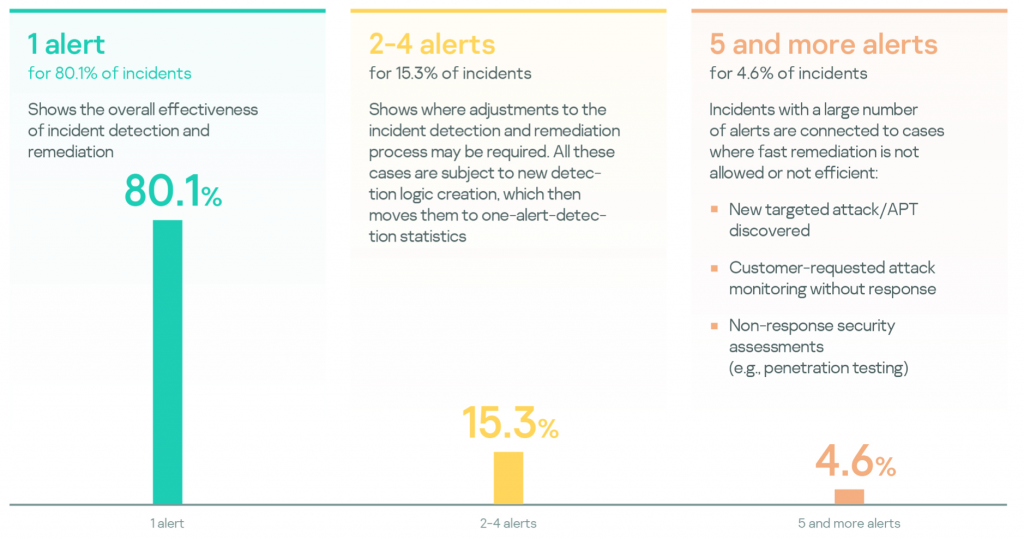
Most of the incidents (80.1%) were detected based on the first analyzed alert. This means that after the first true positive alert, remediation activities stopped the attack from happening and no new alerts were linked to the incident. This demonstrates that remediation is fairly efficient.
Incidents linked to 2-4 alerts account for 15.3%; they represent the main directions for detection engineering, both in new alert development and improvements to existing alerts.
Incidents linked with larger numbers of alerts are related to cases where fast remediation is not efficient or not allowed. Examples of these incidents include a new targeted attack that requires thorough investigation before active response, or security assessment engagements, where active counteraction to attacker is not allowed.
Incident severity
According to the MDR incident severity classification, High-severity incidents are related to human-driven attacks or malware outbreaks with a high impact. Medium severity is related to incidents that significantly affect the efficiency or performance of assets covered by MDR. Finally, Low severity is related to incidents without a significant impact, which still ought to be fixed, for example, infection with grayware, such as adware, riskware, etc.
High-severity incidents can be caused by a number of factors:
- APT, targeted attack
- Offensive exercise
- Artefacts of APT, targeted attack
- Malware with critical impact
- Likely-to-be-exploited vulnerability
- DDOS/DOS with impact
- Insider threat with impact (subversion, fraud)
- Social engineering
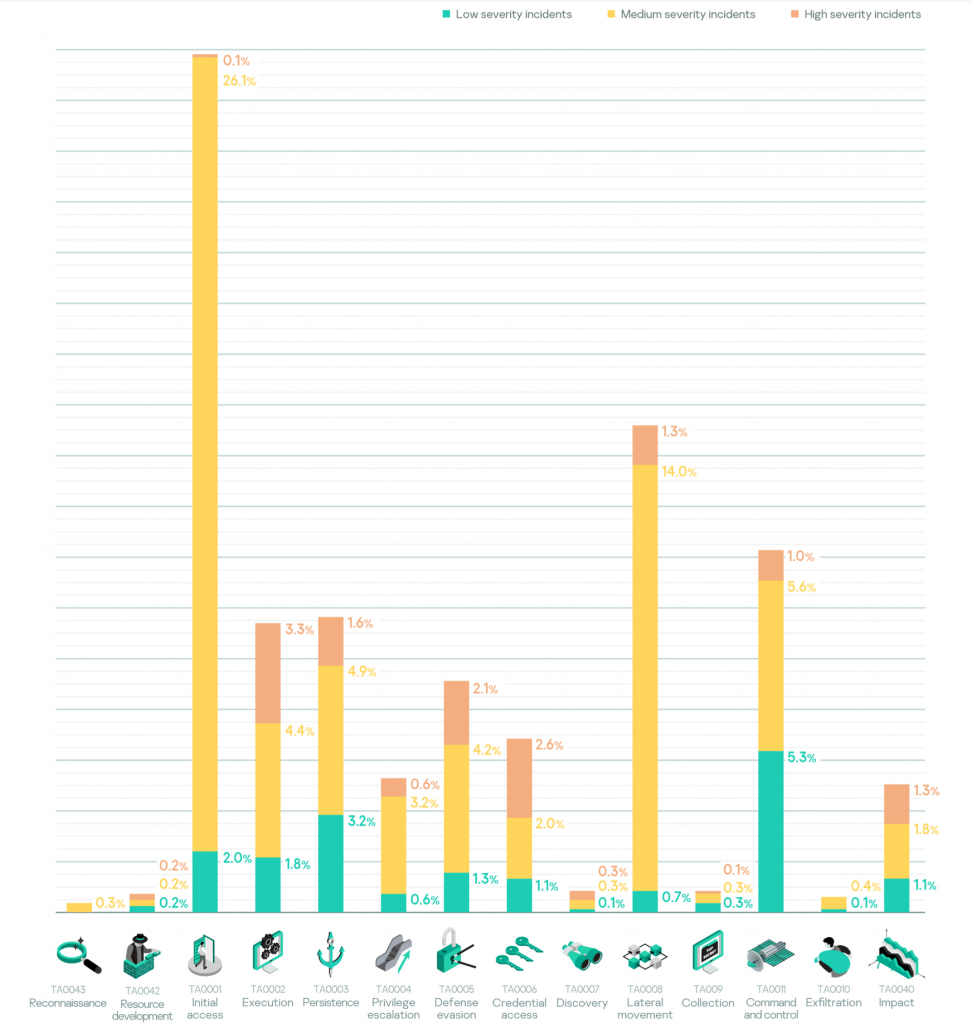
In the analyzed period, the incident severity statistics and distribution of High-severity incidents were as follows.
| Distribution of incidents by criticality | Types of High-severity incidents | |
 |
 |
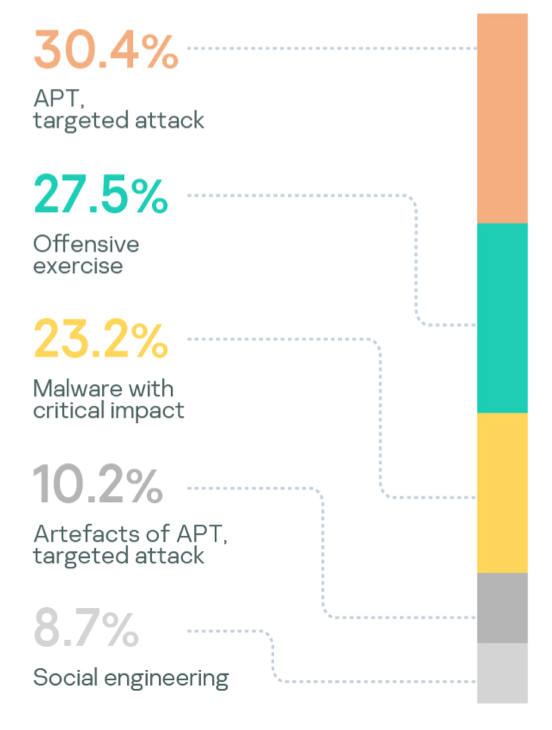 |
Almost all of the verticals in the analyzed period were victims of targeted attacks. IT, Government and Industrial are the TOP 3. Companies that suffered from targeted attacks typically engaged in offensive exercises, a sign of adequate risk assessment.
Adversary tactics, techniques and procedures
As for the attack kill-chain stage, we do not see any correlation between incident severity and tactics at the moment of detection, although it might be expected that more complex attacks would be detected at a later stage.
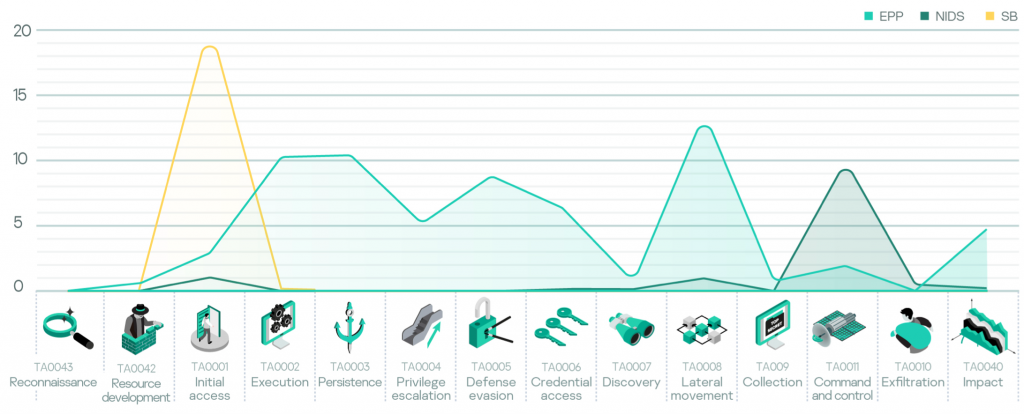
Analysis of the detection technology has confirmed that there is a need for a combination of different detection systems, because the endpoint tactics are efficiently detected by EPP; SB provides better results at analyzing content before it reaches the endpoint, and all network communications are subject to IDS.
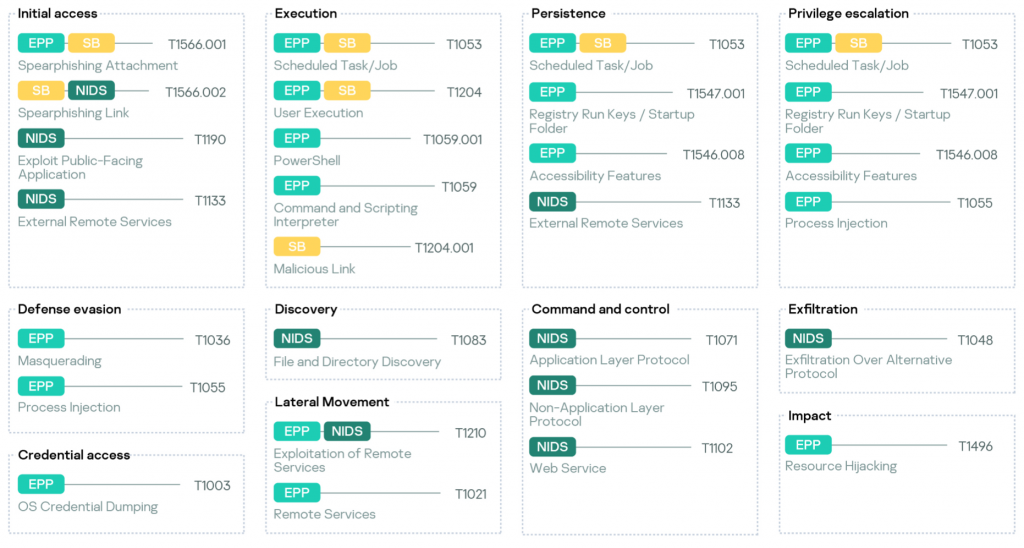
Next, there are the top performing (by the number of reported incidents) MITRE ATT&CK techniques, detected by telemetry from each sensor.
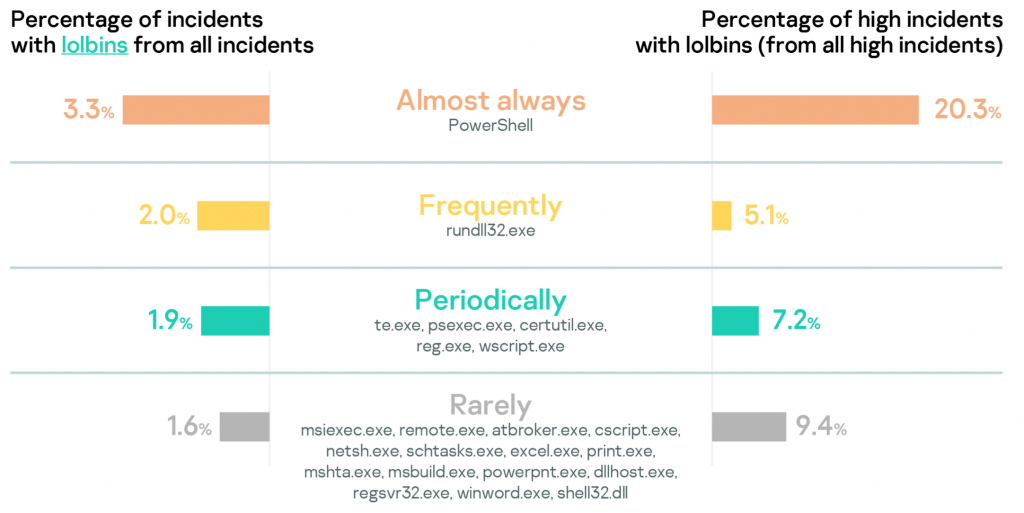
Analysis of tools that attackers use in the incidents shows that PowerShell is still number one and especially popular in High-severity incidents.
Recommendations
Analysis of incident statistics suggests the following recommendations on improving the security controls in place.
- One third of all high-severity incidents were human-driven targeted attacks. Automated tools are not enough for fully detecting these, so manual threat hunting in combination with classical alert-driven monitoring should be implemented.
- Professional red team exercises are very similar to advanced attacks and are thus a good approach to assessing the organization’s operational efficiency.
- Nine percent of reported High-severity incidents were successful social engineering attacks, which demonstrates the need for raising employee security awareness.
- Be ready to detect threats that use every tactic (attack kill chain phase).
- Even a complex attack consists of simple steps and techniques; the detection of a particular technique can expose the whole attack.
- Different detection technologies have different levels of efficiency with different attacker techniques. Maintain a variety of security technologies to increase the chances of successful detection.
- Monitor PowerShell with built-in Windows events or comprehensive EDRs.

















Managed Detection and Response in Q4 2020