
Money is the root of all evil, including cybercrime. Thus, it was inevitable that malware creators would one day begin not only to distribute malicious programs themselves, but also to sell them to less technically proficient attackers, thereby lowering the threshold for entering the cybercriminal community. The Malware-as-a-Service (MaaS) business model emerged as a result of this, allowing malware developers to share the spoils of affiliate attacks and lowering the bar even further. We have analyzed how MaaS is organized, which malware is most often distributed through this model, and how the MaaS market depends on external events.
Results of the research
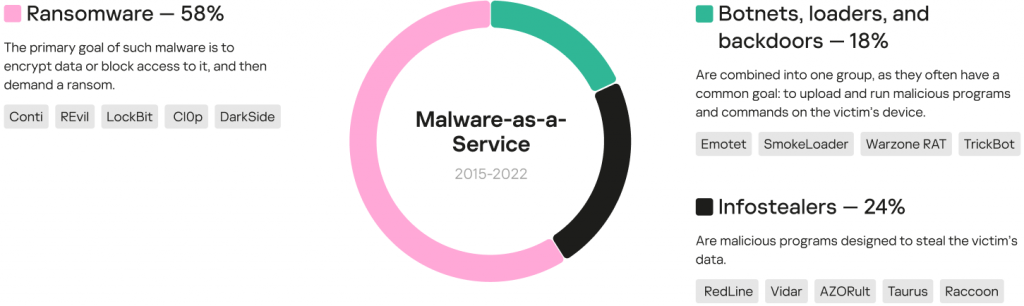
We studied data from various sources, including the dark web, identified 97 families spread by the MaaS model from 2015, and broke these down into five categories by purpose: ransomware, infostealers, loaders, backdoors, and botnets.
As expected, most of the malware families spread by MaaS were ransomware (58%), infostealers comprised 24%, and the remaining 18% were split between botnets, loaders, and backdoors.
Malware families distributed under the MaaS model from 2015 through 2022
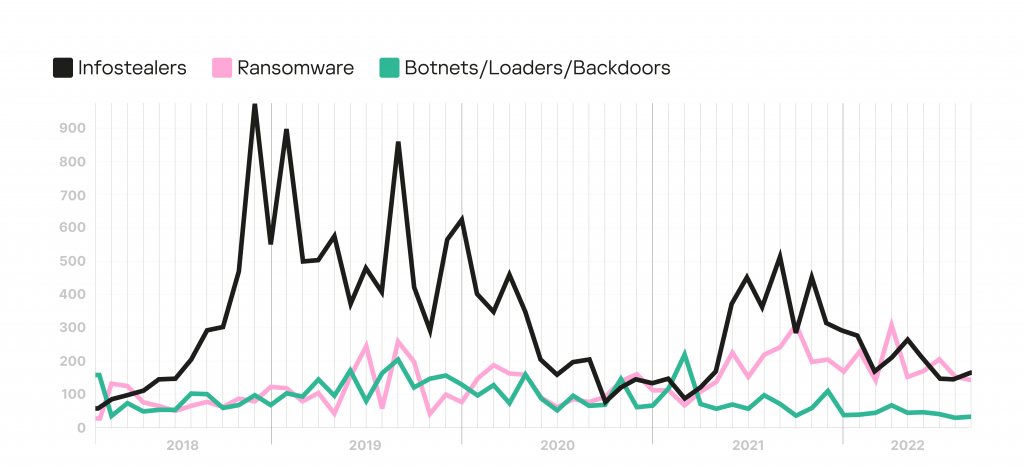
Despite the fact that most of the malware families detected were ransomware, the most frequently mentioned families in dark web communities were infostealers. Ransomware ranks second in terms of activity on the dark web, showing an increase since 2021. At the same time, the total number of mentions of botnets, backdoors, and loaders is gradually decreasing.
Trends in the number of mentions of MaaS families on the dark web and deep web, January 2018 – August 2022
There is a direct correlation between the number of mentions of malware families on the dark and deep web and various events related to cybercrime, such as resonant cyberattacks. Using operational and retrospective analysis, we identified the main events leading to a surge in the discussion of malware in each category.
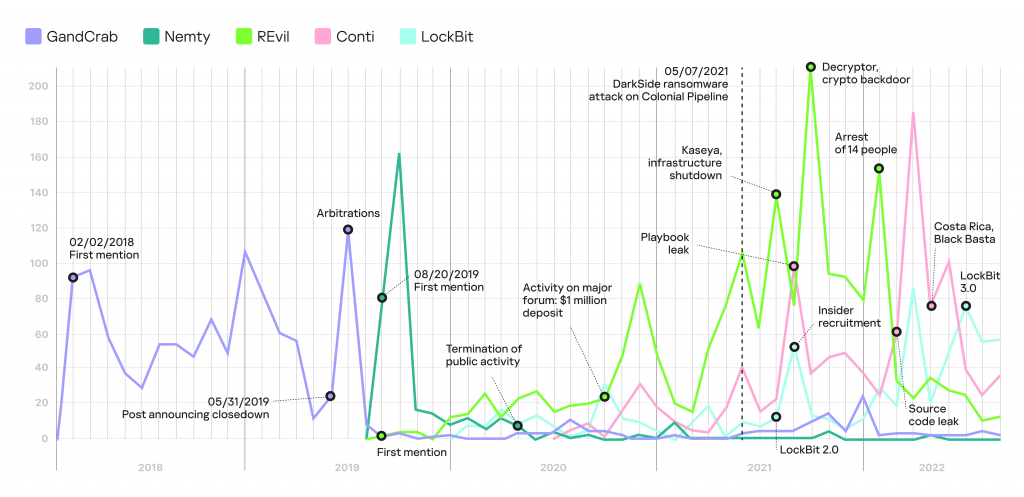
Thus, in the case of ransomware, we studied the dynamics of mentions using five infamous families as an example: GandCrab, Nemty, REvil, Conti, and LockBit. The graph below highlights the main events that influenced the discussion of these ransomware families.
Number of mentions of five ransomware families distributed under the MaaS model on the dark web and deep web, 2018–2022
As we can see in the graph above, the termination of group operations, arrests of members, and deletion of posts on hidden forums about the spread of ransomware fail to stop cybercriminal activity completely. A new group replaces the one that has ceased to operate, and it often welcomes members of the defunct one.
MaaS terminology and operating pattern
Malefactors providing MaaS are commonly referred to as operators. The customer using the service is called an affiliate, and the service itself is called an affiliate program. We have studied many MaaS advertisements, identifying eight components inherent in this model of malware distribution. A MaaS operator is typically a team consisting of several people with distinct roles.
For each of the five categories of malware, we have reviewed in detail the different stages of participation in an affiliate program, from joining in to achieving the attackers’ final goal. We have found out what is included in the service provided by the operators, how the attackers interact with one another, and what third-party help they use. Each link in this chain is well thought out, and each participant has a role to play.
Below is the structure of a typical infostealer affiliate program.
Infostealer affiliate program structure
Cybercriminals often use YouTube to spread infostealers. They hack into users’ accounts and upload videos with crack ads and instructions on how to hack various programs. In the case of MaaS infostealers, distribution relies on novice attackers, traffers, hired by affiliates. In some cases, it is possible to de-anonymize a traffer by having only a sample of the malware they distribute.
Translation:
Pontoviy Pirozhok (“Cool Cake”)
Off to work you go, dwarves!
Telegram profile of an infostealer distributor
Monitoring the darknet and knowing how the MaaS model is structured and what capabilities attackers possess, allows cybersecurity professionals and researchers to understand how the malicious actors think and to predict their future actions, which helps to forestall emerging threats. To inquire about threat monitoring services for your organization, please contact us at: dfi@kaspersky.com.
To get the full version of the report “Understanding Malware-as-a-Service” (PDF) fill in the form below.
Understanding Malware-as-a-Service























planido estrate
Very informative article. Want to complain a little about the PDF version. It’s too black, almost cant read it. Please, a more friendly version. Keep the good work, Thanks
Securelist
Hi Planido!
Thank you for your feedback!
Next time we will make our reports more friendly.
A B
I like to recieve the full report if possible
Securelist
Hi A B!
To download the report, please fill in the form in the post. If you don’t see any form except the comment form, try adding this page to the exceptions in you privacy settings or open it in another browser (e.g. Google Chrome)
TS
I want to read the full-report. Thanks.
Securelist
Hi TS!
To download the report, please fill in the form in the post. If you don’t see any form except the comment form, try adding this page to the exceptions in you privacy settings or open it in another browser (e.g. Google Chrome)
Andres Oliva
Excellent article, the information is very relevant. It would be worth adding information on the impact of the attacks and segregating it by country.
Ayuba Ahmed
An insightful piece
Djsjajajs syshshyw
Where is the pdf
Securelist
Hi Djsjajajs!
To get the PDF, please fill in the form in the post. If you don’t see any form except the comment form, try adding this page to the exceptions in you privacy settings or open it in another browser (e.g. Google Chrome)
Hassan
Nice
Sloane
I am interested in learning more about these crreps who have been hacking me for over 10 months as well as spreading to my family and friends through wifi, nearby shate and bluetooth infecting my town
Joel
Would love the report!
Securelist
Hi Joel!
To download the report, please fill in the form in the post. If you don’t see any form except the comment form, try adding this page to the exceptions in you privacy settings or open it in another browser (e.g. Google Chrome).
Darya
Despite the fact that I have a poor knowledge on the topic of cybersecurity, I found this article very interesting and thought-provoking.
Now I want to found out who botnets, loaders, and backdoors are and also to know about GandCrab, Nemty, REvil, Conti, and LockBit malware families and their history.
Thanks to the Author!
Frank
Hi, my friend! I’d like to study the full report if possible, reply to me at your leisure time! Thank you!
Securelist
Hi Frank!
To download the report, please fill in the form in the post. If you don’t see any form except the comment form, try adding this page to the exceptions in you privacy settings or open it in another browser (e.g. Google Chrome).