
This annual report provides an overview the evolution of malware, adware and potentially malicious programs in 2007, and compares this data to that of 2006. A new statistical method was used to prepare this report; the 2006 figures used in this report were also recalculated using the new method. As a result, they may not match the figures given in last year’s annual report.
The report contains a large amount of statistical data and is primarily aimed at IT security professionals who specialize in malware. It may also be of interest users with an interest in computer virology.
- Malware evolution in 2007
- Trend of the year: the evolution of malicious programs targeting players of online games
- Spam report
- Malware which spreads via email
2007 in Review
The year 2007 will be remembered as the year that saw the demise of so-called noncommercial malware. Whether or not it truly marked the disappearance of such malicious programs remains to be seen. For now, all we can say is that in 2007, the motives behind all major epidemics and the malicious programs which became widespread were financial. This is a shift from 2006, when such vandal viruses did still make appearances – one example is the epidemic caused by Nyxem.E, a worm which did nothing but spread itself and delete files.
Nearly all of the epidemics in 2007 were short-lived and limited to specific regions and countries rather than spreading across the entire Internet. This trend has become the de-facto standard for epidemics.
There’s no doubt that the Storm Worm (classified by Kaspersky Lab as Zhelatin) stands out among the many new malicious programs of 2007. This worm made its debut in January 2007. Throughout the year, it demonstrated a wide range of different behaviors, interaction between its varied components, methods of propagation and social engineering tactics. The worm left antivirus experts tearing their hair each time a new version of the unknown authors’ creation appeared.
Zhelatin was the embodiment of nearly all the achievements of virus writers over the past few years, many of which had previously appeared only as proof of concept code. These include rootkit technologies, garbage code and botnets capable of protecting themselves against analysis and study, and interaction among infected computers via P2P networks without a single control center. The worm utilized all existing propagation methods, ranging from the traditional (email and instant messaging systems) to Web 2.0 services (social networks, blogs, forums and RSS feeds). Cyber criminals also took advantage of Internet users’ growing interest in video by disguising Zhelatin as a video file.
The Storm Worm’s primary function was to create networks for subsequent use as spamming platforms launching DoS attacks. A separate in-depth report covers the changes in spam trends in 2007. As far as DoS attacks are concerned, they became one of the key themes of information security in 2007.
After their active use in 2003-2004, DoS attacks have not been a particularly common tool among cyber criminals – until 2007, that is. They made a comeback last year, although not so much as a tool for extorting money from victims as a means of waging political and competitive battle. The DoS attack against Estonia in May 2007 enjoyed full media coverage, and many experts consider this the first ever instance of cyberwar. It was clear that victims’ business competitors stood behind a number of the DoS attacks in 2007. Just four years ago, DoS attacks were used exclusively by extortionist hackers and malicious users. Today, however, they have become as much of a product as spam mailings and made-to-order malware. Advertisements for DoS attack services have become a run-of-the-mill occurrence, and prices are comparable to those for organizing spam mailings.
In 2007, the cybercrime business produced several new types of criminal activity. The made-to-order malware business grew rapidly, with technical support being offered to buyers. Probably the most remarkable example of this line of business involves the Trojan-Spy program Pinch. The authors created over 4,000 variants of this Trojan over the course of several years. Most of the variants were made to order for other malicious users. This story has probably come to an end now; in December 2007, the head of Russia’s Federal Security Service announced that the identities of Pinch’s authors had been established.
Another similar example involves the virus Fujack. This malicious Chinese creation is designed to steal data from the users of online games and was sold by its authors to anyone who was interested. There are now several hundred variants of Fujack. Fujack’s author made approximately $12,000 – at least, that was the amount announced by the Chinese law enforcement officials who arrested the cyber criminal along with several of his customers.
Fujack was one of the most notable malicious programs in terms of gaming Trojan families in 2007. In 2006, Banker Trojans (designed to steal data from bank accounts) dominated the scene, and Kaspersky Lab predicted that 2007 would see competition between Banker Trojans and gaming Trojans in terms of the number of new programs.
In qualitative terms, the year-end results show that gaming Trojans won the competition hands down: the number of gaming Trojans clearly exceeded that of Banker Trojans. It is important to note that there isn’t yet any direct competition between these two Trojan families, as the target audiences still remain discrete. This is confirmed by the fact that we still have not seen any gaming Trojans capable of stealing bank account data. While theoretically it would be simple to create this kind of hybrid, the absence of such programs seems to indicate that virus writers do not view this as either critical or even particularly appealing.
The most notable events of 2007 involve the mass hacking of websites and the subsequent placing of malware (or links to infected sites) on the hacked websites. One of these events was the hacking of nearly 10,000 Italian sites in June, in which the Mpack bundle of exploits was placed on victim websites. These types of hack attacks were seen around the world all throughout the year, and the largest attack was recorded towards the end of 2007 when over 70,000 websites in different countries around the world were found to have been infected with malicious code that would download yet another gaming Trojan to the victim machine.
The Mpack incident in Italy drew attention to yet another cyber criminal operation: during investigations, it was established that malware had been placed on Russian Business Network (RBN) websites. An in-depth analysis found that RBN had been used as a platform for spreading malicious programs hundreds of times. Effectively, this was so-called bullet-proof hosting, with the service providers guaranteeing the anonymity of their customers, protection against prosecution and the absence of any log files.
A huge scandal erupted around RBN and lasted throughout the summer and early autumn of 2007, when RBN faded into the shadows. The network had spun off into several smaller hosting platforms in different countries around the world in an effort to minimize the true scale of its operations.
Those were the main events of 2007, which turned out to be the most virus-ridden year to date. The figure below shows the numbers of all malicious programs, AdWare and potentially malicious programs which were added to the Kaspersky Lab antivirus database in 2007:

Total number of all new programs in 2006 and 2007
| Total percentage | 2007 | 2006 | Growth |
| TrojWare | 201958 | 91911 | 119,73% |
| VirWare | 12416 | 6282 | 97,64% |
| MalWare | 5798 | 4558 | 27,20% |
| AdWare | 14382 | 2583 | 456,79% |
| RiskWare | 2690 | ||
| Total | 237244 | 105334 | 125,23% |
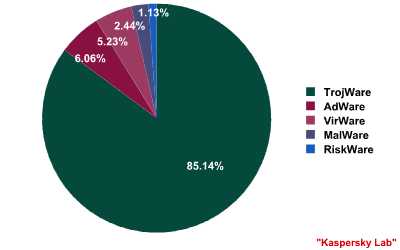
Breakdown of the distribution of malicious programs,
AdWare and potentially malicious programs in 2007
The total number of threats in 2007 more than doubled. In the big picture, Kaspersky Lab added almost as many new programs to its antivirus databases in 2007 as it had done in the course of the previous 15 years.
The Internet had never experienced anything like this onslaught of threats, and Kaspersky Lab was pressed to do everything in its power – and sometimes even perform the impossible – in order to combat these threats. This is a cause for serious concern; if the situation does not change in 2008 (and there is no cause to think that it will), then the number of threats will again have doubled by the end of the year.
Malicious programs
Kaspersky Lab’s classification system has three classes of malicious program:
- TrojWare – these are Trojans which are not capable of self-replication (backdoors, rootkits and all kinds of Trojans);
- VirWare – malicious programs capable of self-replication (viruses and worms);
- Other MalWare – software which is actively used by malicious users to create malicious programs and conduct attacks.
Increased numbers of new malicious programs. In 2007, the average number of new malicious programs detected each month grew 114.28% from 2006 and amounted to 18,347.67 (compared to 8,562.50 in 2006). Over the reporting period, 220,172 new malicious programs were detected.
A total of 119.73% more new Trojans were detected in 2007 than in 2006. The key reasons behind the increase in the number of Trojans on the Internet remain unchanged: it is relatively simple to create TrojWare (as opposed to worms and viruses), and these programs can be used to steal data, create botnets, and conduct mass mailings.
In 2007, the number of new malicious programs in the VirWare class increased 97.64% from 2006. This was due to a something of a renaissance of classic file viruses (discussed in more detail below).
The increase in the number of new malicious programs in the Other MalWare class did not exceed 30% over the year. This is clearly less than the increase in the other classes, which demonstrated a growth of 90% and higher. There is a possibility that Other MalWare will exhibit negative growth in 2008.

Number of new malicious programs detected by Kaspersky Lab in 2007
Distribution of malicious programs by class. No major changes took place in terms of class percentages in 2007. The trend which had been observed over the course of several years remains constant: while TrojWare continues to increase in number, the VirWare and Other MalWare classes are showing gradually decreasing figures.


Breakdown of malicious programs according to class in 2006 and 2007
| Total | 2007 | 2006 | % in 2007 | % in 2006 | % change | Growth |
| TrojWare | 201958 | 91911 | 91,73% | 89,45% | +2,28% | 119,73% |
| VirWare | 12416 | 6282 | 5,64% | 6,11% | -0,47% | 97,64% |
| MalWare | 5798 | 4558 | 2,63% | 4,44% | -1,80% | 27,20% |
| Total | 220172 | 102751 | 100% | 100% | 114,28% |
The percentage of Trojans in the total number of malicious programs increased 2.28% over the year, giving a total of 91.73%.
The decrease in the total number of worms and viruses (VirWare) in 2006 continued into the first six months of 2007 (-2.26%), although there was some growth towards the end of the year. Overall, in 2007 the share of VirWare fell 0.47% and represented 5.64% of all malicious programs.
The percentage of Other MalWare fell to just 1.95% of all malicious programs by mid-year. By the end of 2007 the situation had changed, and Other MalWare reached 2.63%. However, the drop in the percentage share of all malicious programs was somewhat more significant at -1.80%.
The sections below will address the developments in each category of MalWare in more detail.
Trojans
The chart below illustrates the number of new Trojans detected by Kaspersky Lab on a monthly basis:

The number of new TrojWare programs detected by Kaspersky Lab
The chart clearly shows two peaks in May and August 2007, immediately followed by declines. This movement is nothing at all like the movement in 2006, when numbers were continuously on the rise. It’s possible that the Trojan class achieved stabilization, and that similar movement will become a regular feature. If this prediction turns out to be correct, then we can expect to see the next peak in TrojWare activity at the very beginning of 2008.
The following pie chart portrays a breakdown of different Trojan behaviors:

TrojWare: distribution of behaviors within the class
By examining how different behaviors have increased in number, we can better understand the changes taking place within the TrojWare class. Nearly all types of Trojan have experienced an active growth in number:

Number of new malicious programs in the TrojWare class, by behavior

Trends in the number of new malicious programs in the TrojWare class
| TrojWare | 2007 | 2006 | % change | %% |
| Backdoor | 64900 | 22444 | 189,16% | 32,135 |
| Trojan-PSW | 44218 | 14747 | 199,84% | 21,895 |
| Trojan-Downloader | 43751 | 23443 | 86,63% | 21,663 |
| Trojan-Spy | 19035 | 10479 | 81,65% | 9,425 |
| Trojan | 18592 | 11699 | 58,92% | 9,206 |
| Trojan-Dropper | 4224 | 3771 | 12,01% | 2,092 |
| Trojan-Proxy | 3415 | 2859 | 19,45% | 1,691 |
| Trojan-Clicker | 2294 | 1641 | 39,79% | 1,136 |
| Rootkit | 1381 | 639 | 116,12% | 0,684 |
| Trojan-DDOS | 89 | 59 | 50,85% | 0,044 |
| Trojan-SMS | 15 | 3 | 400,00% | 0,007 |
| Trojan-IM | 15 | 37 | -59,46% | 0,007 |
| Trojan-Notifier | 13 | 15 | -13,33% | 0,006 |
| Trojan-AOL | 9 | 67 | -86,57% | 0,004 |
| Trojan-ArcBomb | 7 | 8 | -12,50% | 0,003 |
| Total | 201958 | 91911 | 119,73% | 100% |
In 2007, the most significant increase in the TrojWare class was demonstrated by Trojan-PSW and Backdoor programs. The growth of 400% shown by Trojan-SMS programs will not be examined as the actual number of such programs is extremely small.
The increase in the number of Backdoor programs amounted to nearly 190%, putting this type of Trojan in first place in terms of numbers (replacing Trojan-Downloader programs which led in 2006). This increase is comparable only with the rapid evolution of email worms in 2002 – 2004. Today, backdoors represent nearly one-third of all malicious programs created around the world, with the backdoors created in China accounting for the great majority.
In 2007, China decisively earned the title of viral superpower. In addition to backdoors, in 2007 Chinese virus writers were active in developing a variety of Trojans designed to steal user data, primarily account data for popular online games. This was reflected in the 200% growth of Trojan-PSW programs. This behavior, as in 2006, occupies second place in terms of numbers and has remained in stiff competition with Trojan-Downloader programs for the leading position.
There are currently three main groups of behavior within the TrojWare category:
- Backdoor, Trojan-PSW, Trojan-Downloader. These are the most widespread Trojan behaviors and represent 75% of the entire TrojWare category (each behavior makes up more than 20% within the TrojWare class).
- Trojan, Trojan-Spy. These behaviors account for nearly 9% of TrojWare and demonstrate average growth rates. There is little to no chance that these behaviors will achieve the increase in number needed to join the first group, and it is also unlikely that their numbers will drop down to the level of the third group.
- Trojan-Proxy, Trojan-Dropper, Trojan-Clicker, Rootkit. This group of behaviors falls within a range of 0.7% – 2.1%. Except for Rootkit, the growth rate of the behaviors in this group does not exceed 40%. Rootkit joined this group in 2007 due to a rapid growth rate of 116.1%. It’s possible that the number of programs demonstrating one particular behavior could grow to reach the level of the second group of behaviors, although it is much more likely that the share of malicious programs in this group will continue to decline due to pressure from behaviors in the first group.
The Trojan-Spy programs which pose the most serious threat to users, and which are most actively evolving are those programs from families which are designed to steal user data relating to online games and banking systems.
Rootkits
A certain amount of attention should be given to rootkits. Often, such programs serve to mask other Trojan programs in an infected system, and one and the same rootkit can be used by more than one malicious user.

Number of new rootkits detected by Kaspersky Lab
In 2005 (when Kaspersky Lab first included this behavior in its classification), rootkits were one of the hottest topics in the antivirus industry, and virus writers started actively developing such types of program: in the space of just one year, the number of new rootkits increased 413%. After such a strong surge, one might expect a slight decline in the growth rate. However, numbers remained strong in 2006 at +74%.
This trend continued in 2007, and the growth recorded for the full year reached over 116%. However, the figure above clearly shows that during the first six months of 2007, the number of new rootkits exceeded numbers from other periods. Kaspersky Lab recorded growth at 178% for the first six months of the year. This was followed by a decline, for which there isn’t a clear explanation yet. The decline could have been caused by decreased activity on the part of Zhelatin’s (a.k.a. the Storm Worm) authors, which was one of the main programs using rootkits in 2007.
Currently, the situation regarding programs exhibiting such Trojan behaviors makes it difficult to predict what may happen next. A great deal depends on the prevalence of Windows Vista.
Worms and viruses
The figure below shows the number of new VirWare programs detected by Kaspersky Lab month by month:

Number of new VirWare programs detected by Kaspersky Lab
The lack of any movement in this class, which was seen in 2004 – 2005, transitioned into growth in late 2006. This growth continued into 2007, although absolute figures still have not surpassed the record high hit in October 2006, when the Internet was struck with hundreds of new variants of the Warezov worm.
The chart shows that in 2007, the emergence of new VirWare programs was unstable, with three periods of upward movement followed by subsequent declines. Currently, these fluctuations are continuing to level out, and 2008 will likely bring more stable trends.
Overall, based on the developments in 2007, the VirWare category demonstrated nearly 98% growth in the number of new malicious programs (in 2006, the number of new malicious programs in the VirWare class increased by just 8%). However, this did not turn out to be enough even to maintain the category’s share in the total number of malicious programs: VirWare’s percentage dropped from 6.11% in 2006 to 5.64% in 2007.
The figure below illustrates the distribution of different behaviors within the VirWare class:

VirWare: distribution of behaviors within the class
By examining how different behaviors have increased in number, we can better understand the changes taking place within the VirWare category. Nearly all types of malicious program in this class experienced an active growth in numbers:

Number of new malicious programs in the VirWare class, by behavior

Movement in the number of new malicious programs in the VirWare class
| VirWare | 2007 | 2006 | % Change | %% |
| Email-Worm | 4758 | 3490 | 36,35% | 38,32 |
| Virus | 3437 | 704 | 389,60% | 27,68 |
| Worm | 2778 | 1311 | 111,80% | 22,37 |
| IM-Worm | 681 | 245 | 178,19% | 5,48 |
| Net-Worm | 426 | 283 | 50,42% | 3,43 |
| P2P-Worm | 282 | 215 | 31,28% | 2,27 |
| IRC-Worm | 54 | 34 | 60,71% | 0,43 |
| Total | 12416 | 6282 | 97,64% | 100,00 |
Remarkably, all of the behaviors in the VirWare class demonstrated growth in 2007. This is the only class of malicious program with such figures.
Email-Worm programs, the most widespread behavior, demonstrated the highest growth rates in 2007. Their growth in 2006 amounted to 43%, and 36.35% in 2007. This allowed this type of malicious program to remain in first place, although the gap between other behaviors did narrow to less than 11%. The large number of email worm variants is caused by representatives of all three of the main families: Warezov, Zhelatin and Bagle.
In reports for the first six months of 2007, Kaspersky Lab predicted that the Virus behavior would move into second place, and this did in fact happen: based on the year-end results, the percentage of programs exhibiting this behavior amounted to nearly 28%, putting them in second place in the VirWare class in terms of numbers.
Classic viruses demonstrated the strongest growth in 2007 among all malicious programs with 389.6%. This surge is due primarily to the common method of spreading viruses via removable flash drives. This huge growth is even more surprising considering that growth for this type of malicious program in 2006 was -29%.
This upward trend is alarming: it is more difficult to remove viruses than it is to remove Trojans. Furthermore, many popular antivirus products which claim to be effective at detecting standard malicious programs often perform poorly when it comes to detecting complex polymorphic viruses. This could lead to major problems in the near future, since virus writers have already focused on this weakness.
Malicious programs exhibiting Worm behavior experienced impressive growth in 2006 with 220%. In 2007, the growth rate slowed a little, and by the end of the year it was less than half of the figures for 2006 (this was likely triggered by the arrest of the author of the Viking family of worms in China). However, by the end of the year their numbers were still high at 111.8%.
Another group of malicious programs that created a stir in 2007 were worms that spread using instant messaging systems. In 2006, we noted that IM-Worms were unable to gain a real foothold on the virus scene. A decrease of 45% in the number of new IM-Worms was recorded in 2006, and it looked as though such programs were heading for extinction in 2007. Contrary to expectation, they not only survived, but flourished. This was due to such worms changing their propagation vector, moving away from AOL and MSN in favor of Skype. Furthermore, the widespread usage of IM clients as a means of spreading malicious programs facilitated the active spread of Zhelatin via ICQ. As a result, IM-Worms unexpectedly took fourth place in quantity among all VirWare (5.5%) and second place in terms of growth rate (178.2%).
The VirWare category can be divided into two main groups of behavior:
- Email-Worm, Worm, Virus. This group of behaviors represents just under 90% of all VirWare. Each behavior accounts for over 20% of VirWare. While the leader (Email-Worm) has not evolved much, the Virus and Worm behaviors experienced considerable surges.
- IM-Worm, Net-Worm, P2P-Worm, IRC-Worm. With the exception of IM-Worm, the percentage of each of these behaviors represents less than 5% of all VirWare. In 2007 they demonstrated average growth rates. Of these behaviors, only IM-Worm is likely to increase in number due to the rapid evolution of IM services, including Skype. The situation continues to look bad for Net-Worms; the absence of any critical vulnerabilities in Windows network services has prevented virus writers from implementing anything new.
Overall, growth rates in the VirWare class are lagging slightly behind TrojWare (98% against 120%), and are significantly higher than growth rates in Other MalWare, which will be addressed below.
Other MalWare
The Other MalWare class is the least widespread in terms of number of malicious programs detected, but it boasts the widest range of different behaviors.
Slow-moving growth in the number of new malicious programs in this class in 2004-2005 (13% and 43%, respectively) moved into negative territory in 2006 (-7%). However 2007 demonstrated that the previous year had probably been a plateau period; malicious programs in this class strengthened their positions prior to moving to the next level. By the end of 2007, Other MalWare had experienced over 27% growth in the number of new malicious programs. However, this growth did not turn out to be enough even to maintain the classes’ share in the total number of malicious programs, and the year closed at 2.63%, down from 4.44% in 2006.

Number of new Other MalWare programs detected by Kaspersky Lab
The figure below gives a breakdown of behaviors within the Other MalWare class:

Other MalWare: distribution of behaviors within the class
By examining the increase in numbers of Other MalWare behaviors, we can better understand the changes in this class:

Number of new malicious programs in the Other MalWare class, by behavior

Trends in the number of new malicious programs in the Other MalWare class
| Other Malware | 2007 | 2006 | Growth | %% |
| Hoax | 1315 | 341 | 285,63% | 22,68 |
| Exploit | 1219 | 1860 | -34,46% | 21,02 |
| Packed | 753 | 0 | 0,00% | 12,99 |
| FraudTool | 617 | 0 | 0,00% | 10,64 |
| HackTool | 520 | 360 | 44,44% | 8,97 |
| SpamTool | 501 | 263 | 90,49% | 8,64 |
| Constructor | 353 | 948 | -62,76% | 6,09 |
| IM-Flooder | 110 | 128 | -14,06% | 1,90 |
| BadJoke | 100 | 112 | -10,71% | 1,72 |
| Flooder | 92 | 88 | 4,55% | 1,59 |
| VirTool | 79 | 46 | 71,74% | 1,36 |
| DoS | 68 | 28 | 142,86% | 1,17 |
| Nuker | 27 | 19 | 42,11% | 0,47 |
| Email-Flooder | 13 | 346 | -96,24% | 0,22 |
| Spoofer | 12 | 5 | 140,00% | 0,21 |
| Sniffer | 11 | 6 | 83,33% | 0,19 |
| SMS-Flooder | 8 | 8 | 0,00% | 0,14 |
| Total | 5798 | 4558 | 27,2% | 100 |
The most dominant behavior in this class is no longer Exploit. This behavior has been losing ground over the past two years. In 2006, it accounted for more than 30%, while its growth rate fell to 21%. In 2007, it represented less than one-quarter of all Other MalWare (21.02%) with an even larger decline of – 34% over the year. The once unshakable Exploit lost its leading position due to developers of web browsers and operating systems – first and foremost Microsoft. In contrast to previous periods, no critical vulnerabilities were found which were comparable those exploited by virus writers in 2003-2005.
Hoax demonstrated the highest growth rate (+284.63%). This is the second year in a row that this behavior has experienced growth of over 150%. Hoax surpassed Exploit (with 22.68% of all VirWare), but just barely (with a gap of a mere 1.56%).
Packed and Fraud Tool are two new behaviors which were incorporated into the Kaspersky Lab classification system in 2007 and took third and fourth places in terms of prevalence among all Other MalWare. The Fraud Tool behavior includes fake antivirus products, which have fooled hundreds of Internet users by allegedly detecting a Trojan on their computers and asking for a small fee for the removal of the so-called infection. (This is essentially fraud based on scare tactics.)
Spam and DoS attacks made headlines in information security news in 2007. In 2006, the growth in the number of Spam Tool behaviors skyrocketed +107% and took fifth place among all Other MalWare. During the first six months of 2007, SpamTool was the absolute leader in terms of growth rates in this class: growth of 222% helped SpamTool reach second place in terms of quantity in this class. By the end of the year, the situation was once again that of 2006 numbers (6th place). Growth in the number of new programs within this behavior was quite high by the end of the year, and that trend is not likely to change in 2008.
As regards DoS attacks, the quantitative indicators of this behavior are still small, but the growth rate very clearly indicates that programs exhibiting this behaviour will number in the hundred in 2008.
Potentially unwanted programs (PUPs)
Potentially Unwanted Programs (PUPs) are programs which are developed and distributed by legitimate companies but which also have functions which can be abused by malicious users. These programs cannot be labeled as strictly malicious or completely safe – it all depends who is using them.
Kaspersky Lab classifies RiskWare, PornWare and AdWare as PUPs. For several years, Kaspersky Lab offered the option to detect PUPs. However, such data was not included in our reports. This was partly due to the low number of such programs and partly due to the changing criteria used to determine whether or not software was considered potentially malicious. In 2007, the antivirus industry managed to reach a general definition of what a PUP is, and this has allowed Kaspersky Lab to classify such programs in more detail.
RiskWare and PornWare
The RiskWare class includes legitimate software which, in the hands of malicious users, can be used to inflict damage on users and their data by destroying, blocking, modifying or copying data, or disrupting the performance of computers or computer networks. Currently, the amount of RiskWare is not yet even equal to the amount of Other MalWare, but an overall increase in the number of such programs does give cause for concern. More and more software is starting to balance the very fine line between “harmless” and “malicious.” This creates many additional problems, both for users and for antivirus companies. Furthermore, it is in this very field that legal disputes have arisen between RiskWare developers and antivirus companies. In 2007, this led to a number of lawsuits, many of which were won by antivirus companies.
The term PornWare refers to utilities which are related in one way or another to the display of pornographic material. This class includes a range of software related to pornography, such as Dialers, Downloaders and PornTool. PornWare programs are not particularly widespread, and the number of new PornWare programs detected by Kaspersky Lab in 2007 does not exceed 500, which is why the decision was made to combine this class with RiskWare.
The figure below illustrates the number of new RiskWare and PornWare programs detected by Kaspersky Lab on a monthly basis.

Number of new RiskWare and PornWare programs detected by Kasperky Lab each month
The figure below shows the breakdown of the behaviors within the RiskWare and PornWare classes.

RiskWare+Pornware: distribution of behaviors within the class
There are two clear leaders among the behaviors in the RiskWare and PornWare classes: Monitor (36.65%) and Porn-Dialer (13.98%).
Monitor includes an array of so-called legal keyloggers. Such software is officially manufactured and sold, although its ability to hide its presence in an infected system means that such programs can be used in the same way as fully functional Trojan spy programs.
Porn-Dialers are programs which call fee-based resources of pornographic materials. They make telephone connections with fee-based telephone numbers, which often leads to a lawsuit between subscribers and telephone companies. In 2007, programs classified as Dialer and Porn-Dialer took the lead among the most widespread based on the data provided by Kaspersky Lab’s online scanner.
The figure below shows the number of programs in these two classes by behavior.

Number of new RiskWare and PornWare programs, by behavior
| RiskWare & PornWare | 2007 | %% |
| Monitor | 986 | 36,65 |
| Porn-Dialer | 376 | 13,98 |
| PSW-Tool | 213 | 7,92 |
| RemoteAdmin | 198 | 7,36 |
| Dialer | 163 | 6,06 |
| Downloader | 162 | 6,02 |
| AdTool | 122 | 4,54 |
| Net-Tool | 112 | 4,16 |
| RiskTool | 90 | 3,35 |
| Server-FTP | 61 | 2,27 |
| Server-Proxy | 38 | 1,41 |
| Tool | 23 | 0,86 |
| Porn-Downloader | 21 | 0,78 |
| Porn-Tool | 17 | 0,63 |
| Client-IRC | 13 | 0,48 |
| Server-Web | 8 | 0,30 |
| Client-SMTP | 2 | 0,07 |
| Server-Telnet | 1 | 0,04 |
| Other | 84 | 3,12 |
| Total | 2690 | 100 |
In addition to Monitor and Porn-Dialer, other behaviors such as PSW-Tool and RemoteAdmin are also very widespread. PSW-Tool programs can be used to restore forgotten passwords, but malicious users can easily take advantage of them to extract these passwords from the computers of unsuspecting victims. Programs with RemoteAdmin behavior are very popular among system administrators have a very similar dual function; although they have legitimate applications, these programs are used by hackers in order to exercise control over hacked computers. The legal status of RemoteAdmin programs provides malicious users with a certain guarantee that some antivirus programs will not be able to detect their presence in the system.
This is the first time Kaspersky Lab published statistics on these classes, which is why there is no prior data with which to compare these findings. Kaspersky Lab will continue to track RiskWare and PornWare in detail.
AdWare
AdWare includes software designed to display advertisements (most often banner ads), redirect search requests to advertising websites and collecting marketing data about the user (for example, the kinds of websites the user visits).
AdWare is a large class of programs which have been detected by antivirus companies for some time. The battle against AdWare has resulted in both the birth and demise of the anti-adware software industry.
The figure below shows the number of new AdWare programs detected by Kaspersky Lab on a monthly basis.

Number of new AdWare programs detected by Kaspersky Lab
| 2007 | 2006 | Difference, % | |
| AdWare | 14382 | 2583 | +456,79% |
In 2007 AdWare experienced truly revolutionary growth of 456%. This was due to the “unbalanced” response from the developers of these programs to the efforts of the governments of a number of countries (primarily the US) to put an end to illegal and intrusive Internet advertising. Despite the adoption of laws which have set out clear regulations for AdWare manufacturers and stipulate fines for violations, the situation has actually deteriorated.
Platforms and operating systems
In last year’s annual report, Kaspersky Lab did not publish detailed statistics on the breakdown of malicious programs, AdWare or PUPs by operating system or platform. Instead the report featured an analysis of the most interesting non-Windows systems (*nix, Mac OS and Symbian). However, the 1H2007 report addressed the situation in depth, providing the data needed to analyze the changes over the course of the year.
An operating system or application may be vulnerable to malware attacks if it is capable of launching a program that is not a component of the system. This condition is met by all operating systems, many office applications, graphic editors, design software and other types of software package that have built-in script languages.
In 2007, Kaspersky Lab detected malicious programs, AdWare and potentially malicious programs for 43 different platforms and operating systems.
Naturally, the overwhelming majority of existing malicious programs are executable binary files designed to run in a Win32 environment. Programs designed for other operating systems and platforms represent less than 4% of the total.

Number of malicious programs, AdWare and
potentially malicious programs targeting different platforms
Despite the fact that the share of malicious programs for the Win32 environment amounted to 96.36% in 2007, it began to slowly but surely decline. The percentage of threats targeting platforms other than Win32 increased from 3.18% to 3.42% in the first six months of 2007, and exceeded 4% in the second half of the year. Growth for the full year amounted to 3.64%.
In the last six months of 2007, the number of malicious programs, AdWare and potentially malicious programs for Win32 increased 36% from the first half of the year. However, the increase in malicious code for other platforms and applications amounted to 63% which speaks of a change in the priorities of virus writers as well as the increased threat to users of other systems.
The figure of 63% was primarily achieved due to continued growth demonstrated by a range of malicious programs, primarily those written in Java Script and Visual Basic Script. It is clear that they also target Windows systems. There are several reasons for their increased prevalence. However, the main reason seems to be the efforts of antivirus companies to develop newer and better technologies based on heuristic analysis, code emulation and process virtualization when working with executable Win32 files, while script-based malware has remained beyond the companies’ focus for in-depth analysis. A second reason is the active use of script languages in implementing a number of exploits for vulnerabilities in popular web browsers. Penetrating vulnerable browsers is currently the most common tactic for spreading malicious programs.
| №№ | Platforms | 1H2007 | 2H2007 | Total | Growth |
| 1 | Win32 | 96967 | 131626 | 228593 | 36% |
| 2 | JavaScript | 1182 | 2240 | 3422 | 90% |
| 3 | Visual Basic Script | 576 | 748 | 1324 | 30% |
| 4 | HTML | 398 | 930 | 1328 | 134% |
| 5 | BAT | 334 | 553 | 887 | 66% |
| 6 | PHP | 84 | 186 | 270 | 121% |
| 7 | MSWord | 145 | 83 | 228 | -43% |
| 8 | ASP | 45 | 135 | 180 | 200% |
| 9 | Linux | 121 | 45 | 166 | -63% |
| 10 | Perl | 113 | 37 | 150 | -67% |
| 11 | IRC | 51 | 86 | 137 | 69% |
| 12 | .NET | 33 | 31 | 64 | -6% |
| 13 | MS_DOS | 14 | 44 | 58 | 214% |
| 14 | WinREG | 19 | 39 | 58 | 105% |
| 15 | Symbian | 19 | 30 | 49 | 58% |
| 16 | MacOS | 2 | 33 | 35 | 1550% |
| 17 | Java | 12 | 25 | 37 | 108% |
| 18 | NSIS | 15 | 17 | 32 | 13% |
| 19 | MSPPoint | 17 | 16 | 33 | -6% |
| 20 | MSExcel | 19 | 10 | 29 | -47% |
| 21 | SunOS | 18 | 2 | 20 | -89% |
| 22 | Multi | 8 | 11 | 19 | 38% |
| 23 | RAR | 4 | 12 | 16 | 200% |
| 24 | HTA | 6 | 4 | 10 | -33% |
| 25 | Win16 | 3 | 7 | 10 | 133% |
| 26 | Python | 5 | 9 | 14 | 80% |
| 27 | Ruby | 3 | 5 | 8 | 67% |
| 28 | MSAccess | 5 | 4 | 9 | -20% |
| 29 | AutoCad | 1 | 5 | 6 | 400% |
| 30 | MSOffice | 3 | 3 | 6 | 0% |
| 31 | Unix | 4 | 3 | 7 | -25% |
| 32 | Boot | 5 | 0 | 5 | -100% |
| 33 | SWF | 3 | 3 | 6 | 0% |
| 34 | Win9x | 1 | 3 | 4 | 200% |
| 35 | WMA | 1 | 3 | 4 | 200% |
| 36 | AutoLISP | 0 | 3 | 3 | |
| 37 | ZIP | 3 | 0 | 3 | -100% |
| 38 | BeOS | 1 | 0 | 1 | -100% |
| 39 | Boot-DOS | 1 | 0 | 1 | -100% |
| 40 | FreeBSD | 0 | 1 | 1 | |
| 41 | SAP | 1 | 0 | 1 | -100% |
| 42 | SQL | 0 | 1 | 1 | |
| 43 | Win64 | 1 | 0 | 1 | -100% |
The figure below shows the growth rate in the number of malicious programs, AdWare and potentially malicious programs for all platforms. The platforms and applications for which there were fewer than 20 malicious programs, AdWare programs or potentially malicious programs in 2007 were not included in this chart. This chart was prepared based on comparative figures from the first and second halves of 2007.

Growth rate in 2007 in the number of malicious programs,
AdWare and potentially malicious programs for various platforms
In the first six months, the leaders in terms of growth (exceeding 150%) were the script languages: Java Script, PHP, Ruby, and the MS Office platform. In the last six months of the year, however, the picture changed dramatically. The irrefutable leader (+1550%) was the MacOS X operating system, which was attacked 35 times in 2007, and 33 of those attacks took place in the second half of the year. Our half-yearly report observed the strange absence of any new malicious programs targeting that platform, despite the fact that it was targeted more and more often (over the course of one year, from June 2006 through May 2007, no new malicious programs were created for this platform). But towards the end of the year, the situation changed and matched expert predictions. The most prevalent types of malicious program designed for Macs in 2007 were Trojans, including those which substitute user DNS requests and which are designed to conduct phishing attacks to steal data.
The emergence of new viruses for MS-DOS can likely be put aside as a curiosity of modern virology, particularly in light of the actual numbers. The figures show that there are only about five dozen ‘remakes’ of programs which are effectively historical curiosities.
On the other hand, the increase in the number of malicious programs in the form of HTML pages or written in ASP is very serious. As a rule, HTML-based malware consists of phishing websites or fake greeting cards. If a user falls for the ploy, it could lead to the infection of his computer, or the theft of his private data. In China, ASP is one of the most common means used to manage infected websites and the backdoors installed via a web interface.
Overall, the threat landscape for different platforms and operating systems in 2007 experienced only minor changes. The steady growth in 2006 of Trojans which exploited Microsoft Office (Word, Excel, PowerPoint, etc.) vulnerabilities has currently stopped and the growth rates of those malicious programs experienced something of a decline. This comes as the result of Microsoft having apparently patched all the critical vulnerabilities in these products. Nevertheless, over 200 malicious programs were created for MS Word alone, posing a formidable threat. Many of these programs were used in 2007 in order to launch a series of much-talked-about attacks, which Chinese hackers were suspected of organizing.
The main breakthrough of the year turned out to be JavaScript, which became the most innovative environment for developing and implementing malicious programs. Now, in addition to the most basic-Trojan Downloader, programs written in JavaScript also include exploits for browser vulnerabilities, email worms, a variety of spambots and phishing grabbers. By the end of the year, the number of new malicious programs for JavaScript had more than doubled the numbers of its so-called twin, Visual Basic Script.
One could try to group all 43 of the operating systems and platforms that were attacked in 2007 according to a common factor, such as by the operating system which is ultimately attacked. For example, we could group JavaScript and Visual Basic Script with Windows, and Ruby and Perl with *nix. This gives us an idea of the actual situation in the endless debate on whether or not those who do not use Windows are at risk from malicious code.
| Operating system | Quantity | %% |
| Windows | 236430 | 99,660 |
| Nix | 602 | 0,254 |
| Mac | 35 | 0,015 |
| Mobile | 63 | 0,027 |
| Other | 106 | 0,045 |
*Nix includes: FreeBSD, Linux, Perl, PHP, Ruby, Unix.
Mobile includes: Python and Symbian.
Other includes:BeOS, Boot, Boot-DOS, MS-DOS, Multi, SAP, SQL, SunOS.
Readers are invited to draw their own conclusions based on these statistics.
Antivirus database updates
Kaspersky Lab responded to increased numbers of threats and the increased frequency of new threats by accelerating the release of antivirus database updates and response time.
New antivirus database records
The number of new antivirus database records added to Kaspersky Anti-Virus each month in 2007 varied from approximately 8000 in the beginning of the year to 28000 mid-year and 23000 towards the end of the year. Year-end results show a monthly average of 19770 new records.

Statistics: new antivirus database records each month in 2007
As the chart above shows, the number of new records in the antivirus databases each month increased at varying rates throughout the year. There are two clear peaks in May and August 2007, when Kaspersky Lab processed record numbers of new malicious programs and set the monthly figures at 27847 and 31305, respectively.
Regular and urgent updates
Kaspersky Lab reacts to the emergence of new malicious programs by releasing two types of antivirus database updates: regular and urgent (in the event of an epidemic). The total number of regular database updates exceeded 10,000 in 2007 with an average of nearly 900 updates per month.

Number of regular database updates each month
The figure above shows the rapid increase in the number of updates which began in October 2007. It was just at this time that Kaspersky Lab rolled out a new update release system. Previously, updates were released approximately once per hour. Now, the interval between updates has been reduced to just once every 30 minutes.
This amounts to approximately 40-50 updates over 24 hours, which is the highest update rate in the entire antivirus industry.

Number of urgent database updates each month
There were 51% fewer incidents which required urgent updates in 2007 than in 2006, and 88% fewer in the second half of 2007 than during the first six months. This was due in part to the transition to the thirty-minute update system.
The average number of urgent updates per month came to 9.17.
Forecast
1. MalWare 2.0
The evolution of the ways in which malware operates – from solitary malicious programs to complex projects which interact with one another – began four years ago with the modular system of components used in the Bagle worm. This new malware model, which took shape in late 2006 in the form of the Warezov worm and demonstrated its longevity and effectiveness as the Storm Worm (Zhelatin) in 2007, will not only become the de facto standard for a huge number of new malicious projects, but will also continue to evolve.
Its key features are:
- the absence of a single control center for infected computers;
- methods which actively counteract attempts to study and intercept control;
- huge flash mailings of malicious code;
- skilled use of social engineering tactics;
- the use of a range of propagation methods and a move away from some of the more obvious (i.e. email);
- different modules to fulfill different functions (rather than an all-in-one program).
The new generation of malware can be classified as Malware 2.0 in an analogy with the widely-used term Web 2.0.
At present, the tactics listed above are employed by all three of the aforementioned malicious programs: Bagle, Zhelatin and Warezov. None of these are designed so much to steal data as they are to conduct a large number of today’s mass mailings. However, some families of Banker and gaming Trojans have already started exhibiting some of these traits.
2. Rootkits and bootkits
Techniques used to conceal the presence of a malicious program in the system (rootkits) will soon be used not only by Trojans, but by file viruses as well. As a result, it seems as if we are returning to the era of MS-DOS together with its resident stealth viruses. This is the logical evolution of the methods used to combat antivirus software. Malicious programs are now striving to survive in a system even if they are detected.
There will be another dangerous method used to conceal the presence of a malicious program on a computer. This involves the active use of infection technologies in the boot sector: bootkits. Such programs are the latest reincarnation of older tactics which allow a malicious program to gain control even before the main part of the operating system (which includes antivirus protection) boots. This tactic, which appeared as proof of concept code in 2005, was fully implemented in 2007 as Backdoor.Win32.Sinowal and caused several thousand infections around the world during the last two weeks of the year. This method poses an increased threat to users, and in 2008 it could become a major information security problem.
3. File viruses
File viruses will continue to make a comeback. As before, they will primarily be created by Chinese malicious users, and most will target users of online games. It is possible that the authors of Zhelatin and Warezov will also start to use file infection techniques – after all, that would give them yet means by which to spread their malicious code.
In 2008 we can expect a surge in the number of incidents with games and software infected by distributors and placed on popular websites and file exchange networks. Viruses will aim to infect the very files which users send to others. In many cases, this propagation method may turn out to be even more effective than sending malicious files via email.
4. Attacks on social networks
In 2008, phishing is expected to undergo major changes and to increasingly target social networks. Subscriber account data for services such as Facebook, MySpace, LiveJournal, Blogger, and other similar services, will become more frequently targeted by malicious users. This will become an important alternative method to infecting hacked sites with malware. In 2008, a number of Trojan programs will spread via the blogs and profiles of social network user accounts.
Another problem related to social networks are XSS/PHP/SQL attacks. In contrast to phishing, which employs exclusively fraudulent methods and social engineering, these attacks are based on errors and vulnerabilities in Web 2.0 services and may even affect highly computer-literate users. As always, the goal is to obtain private data and create several databases or lists in order to launch subsequent attacks using more traditional methods.
5. Mobile device threats
As far as mobile devices are concerned – primarily mobile phones – threats will mainly fall into the category of primitive Trojans like the Skuller family for Symbian and the “first Trojan” for iPhone. In addition, a variety of vulnerabilities in smartphone operating systems and applications will also pose a threat. It still isn’t very likely that we will see a global epidemic of a mobile worm, although the technical prerequisites are all in place. The consolidation observed on the smartphone operating systems market between Symbian and Windows Mobile was disrupted in 2007 by the appearance of the iPhone and the announcement of Android, a new mobile platform from Google. Most probably, this newcomer and the popularity of the iPhone will draw more attention from malicious users than other mobile devices. This will hold particularly true if the means for developing applications for the iPhone (SDK) becomes publicly accessible, as Apple announced it would in late 2007.






















Kaspersky Security Bulletin 2007: Malware evolution in 2007