
More information about BlackOasis APT is available to customers of Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
Introduction
Kaspersky Lab has always worked closely with vendors to protect users. As soon as we find new vulnerabilities we immediately inform the vendor in a responsible manner and provide all the details required for a fix.
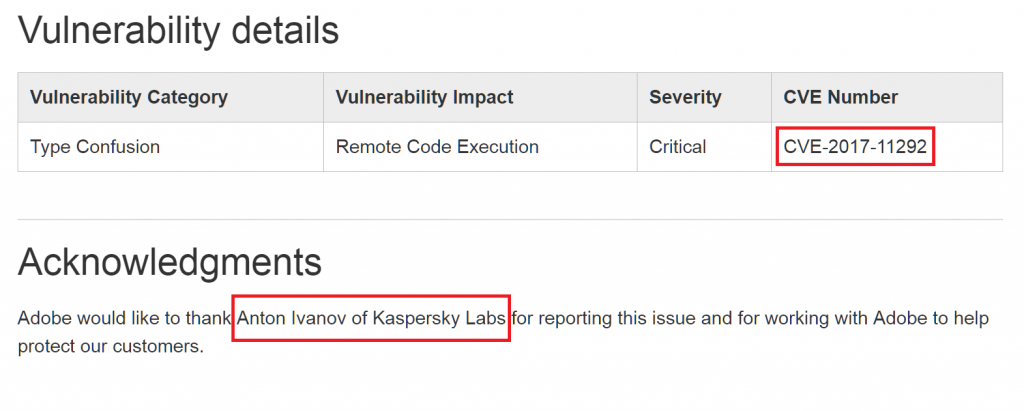
On October 10, 2017, Kaspersky Lab’s advanced exploit prevention systems identified a new Adobe Flash zero day exploit used in the wild against our customers. The exploit was delivered through a Microsoft Office document and the final payload was the latest version of FinSpy malware. We have reported the bug to Adobe who assigned it CVE-2017-11292 and released a patch earlier today:
 So far only one attack has been observed in our customer base, leading us to believe the number of attacks are minimal and highly targeted.
So far only one attack has been observed in our customer base, leading us to believe the number of attacks are minimal and highly targeted.
Analysis of the payload allowed us to confidently link this attack to an actor we track as “BlackOasis”. We are also highly confident that BlackOasis was also responsible for another zero day exploit (CVE-2017-8759) discovered by FireEye in September 2017. The FinSpy payload used in the current attacks (CVE-2017-11292) shares the same command and control (C2) server as the payload used with CVE-2017-8759 uncovered by FireEye.
BlackOasis Background
We first became aware of BlackOasis’ activities in May 2016, while investigating another Adobe Flash zero day. On May 10, 2016, Adobe warned of a vulnerability (CVE-2016-4117) affecting Flash Player 21.0.0.226 and earlier versions for Windows, Macintosh, Linux, and Chrome OS. The vulnerability was actively being exploited in the wild.
Kaspersky Lab was able to identify a sample exploiting this vulnerability that was uploaded to a multi scanner system on May 8, 2016. The sample, in the form of an RTF document, exploited CVE-2016-4117 to download and install a program from a remote C&C server. Although the exact payload of the attack was no longer in the C&C, the same server was hosting multiple FinSpy installation packages.
Leveraging data from Kaspersky Security Network, we identified two other similar exploit chains used by BlackOasis in June 2015 which were zero days at the time. Those include CVE-2015-5119 and CVE-2016-0984, which were patched in July 2015 and February 2016 respectively. These exploit chains also delivered FinSpy installation packages.
Since the discovery of BlackOasis’ exploitation network, we’ve been tracking this threat actor with the purpose of better understanding their operations and targeting and have seen a couple dozen new attacks. Some lure documents used in these attacks are shown below:
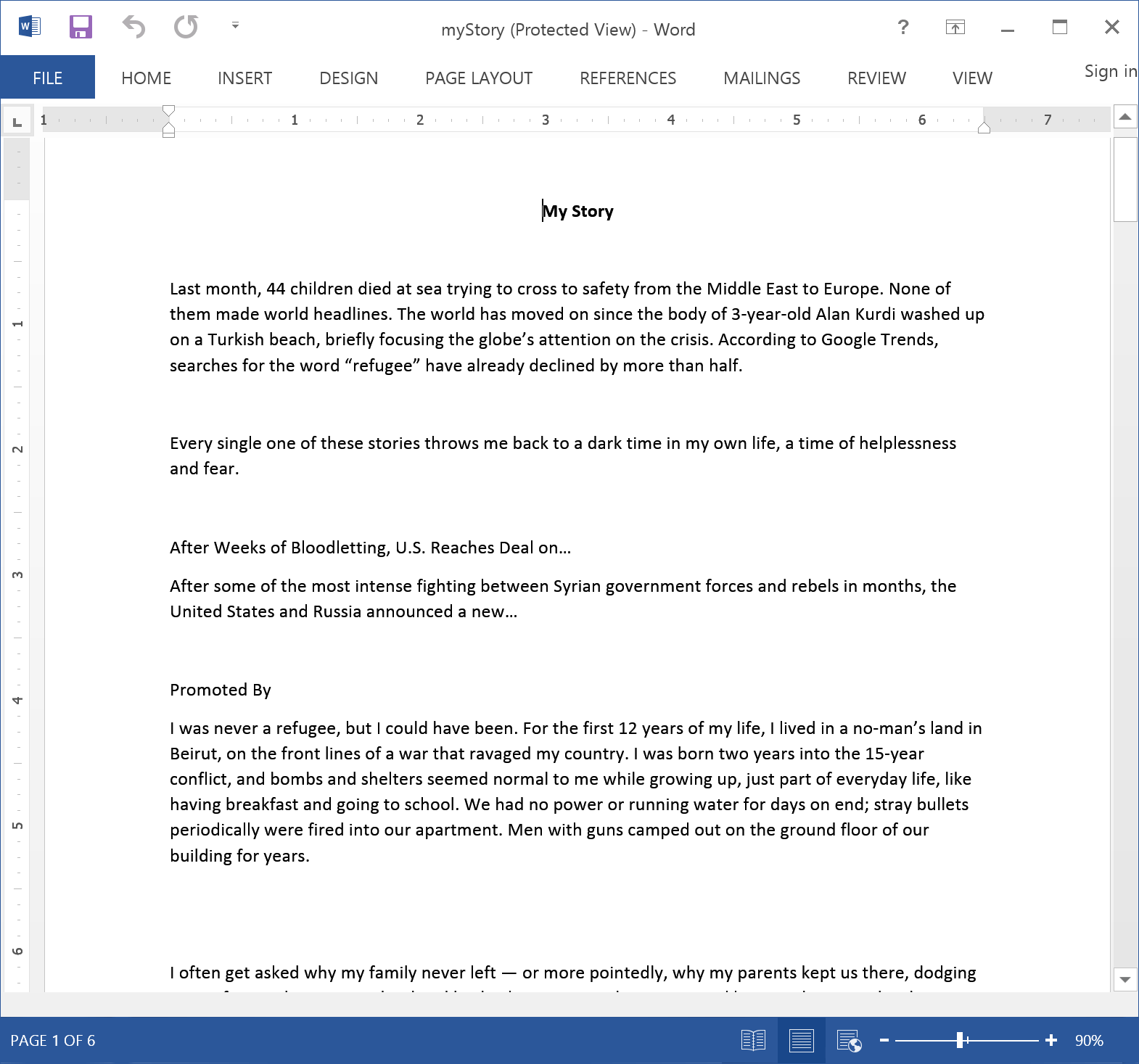
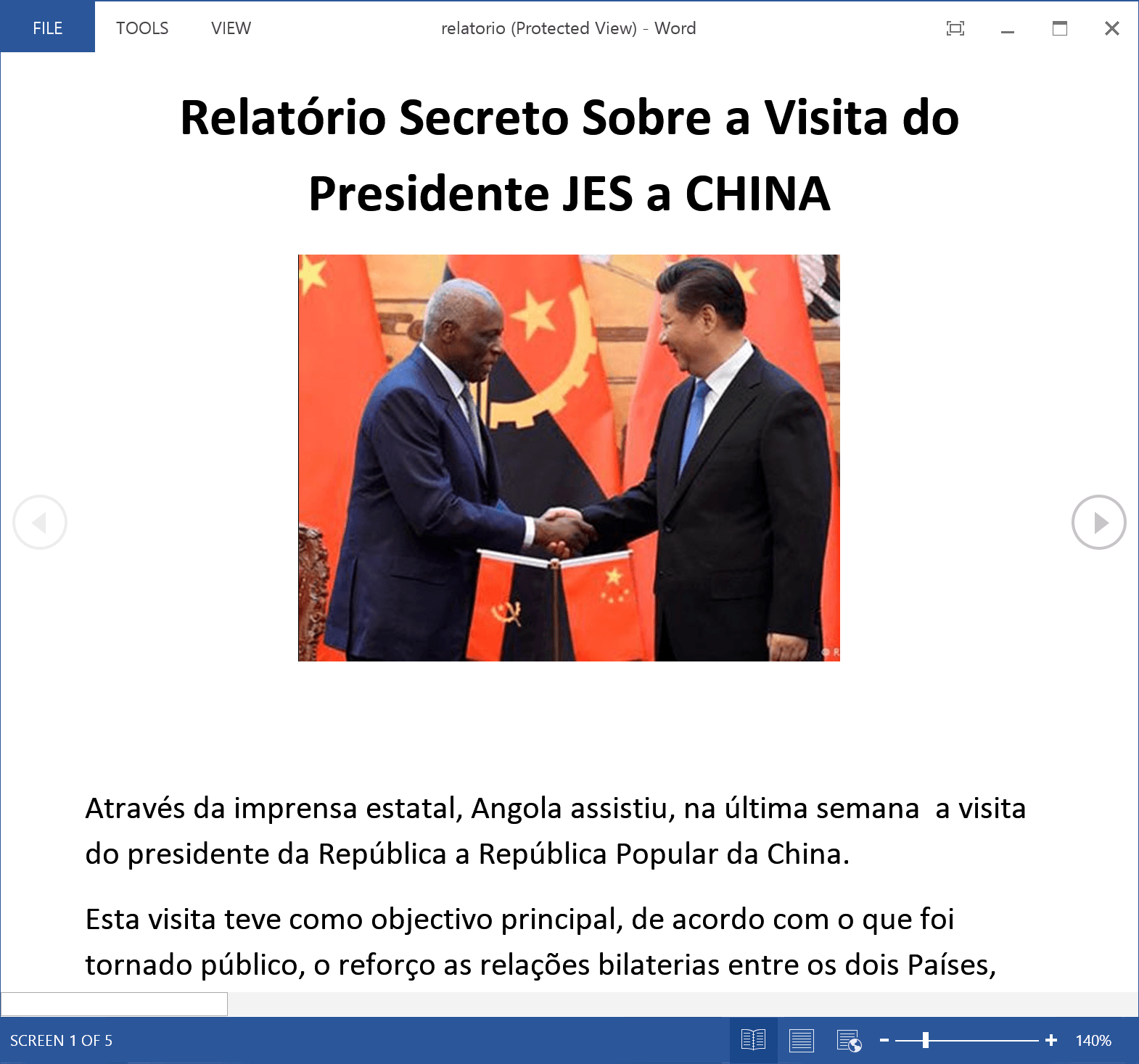 Decoy documents used in BlackOasis attacks
Decoy documents used in BlackOasis attacks
To summarize, we have seen BlackOasis utilizing at least five zero days since June 2015:
- CVE-2015-5119 – June 2015
- CVE-2016-0984 – June 2015
- CVE-2016-4117 – May 2016
- CVE-2017-8759 – Sept 2017
- CVE-2017-11292 – Oct 2017
Attacks Leveraging CVE-2017-11292
The attack begins with the delivery of an Office document, presumably in this instance via e-mail. Embedded within the document is an ActiveX object which contains the Flash exploit.
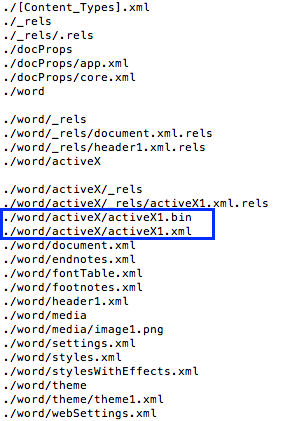
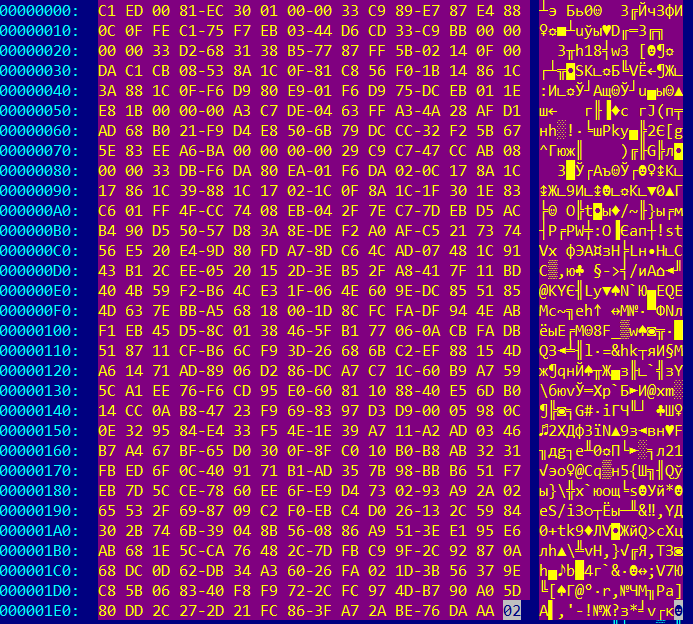
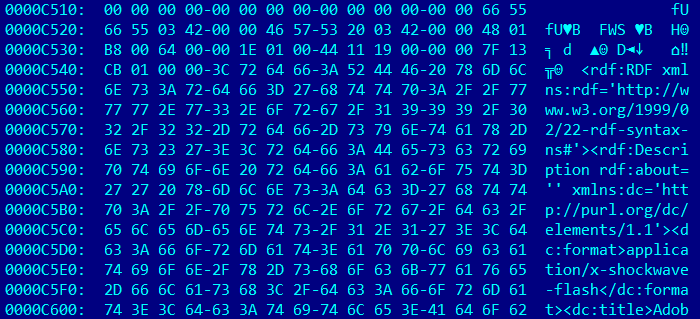 Flash object in the .docx file, stored in uncompressed format
Flash object in the .docx file, stored in uncompressed format
The Flash object contains an ActionScript which is responsible for extracting the exploit using a custom packer seen in other FinSpy exploits.
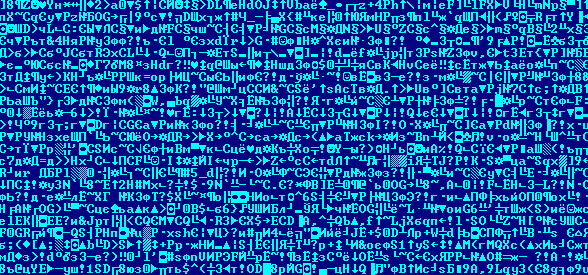
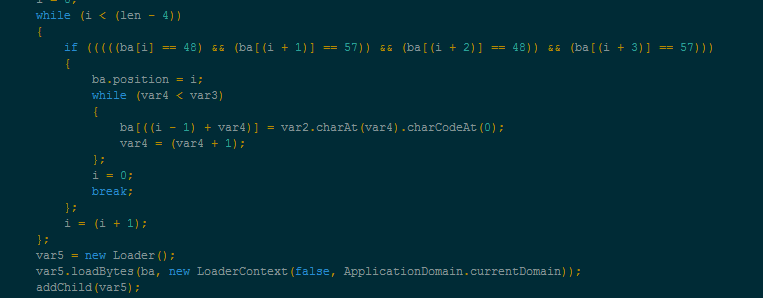 Unpacking routine for SWF exploit
Unpacking routine for SWF exploit
The exploit is a memory corruption vulnerability that exists in the “com.adobe.tvsdk.mediacore.BufferControlParameters” class. If the exploit is successful, it will gain arbitrary read / write operations within memory, thus allowing it to execute a second stage shellcode.
The first stage shellcode contains an interesting NOP sled with alternative instructions, which was most likely designed in such a way to avoid detection by antivirus products looking for large NOP blocks inside flash files:
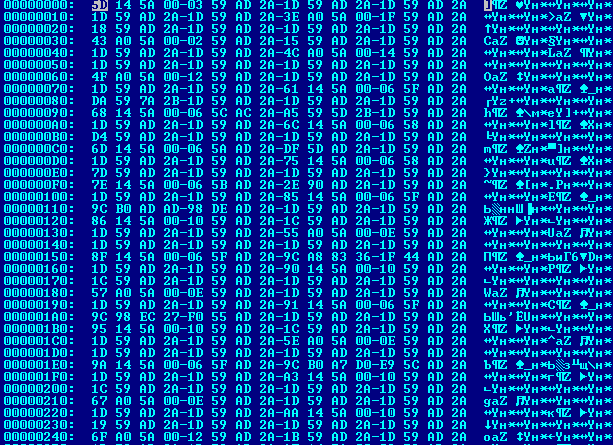
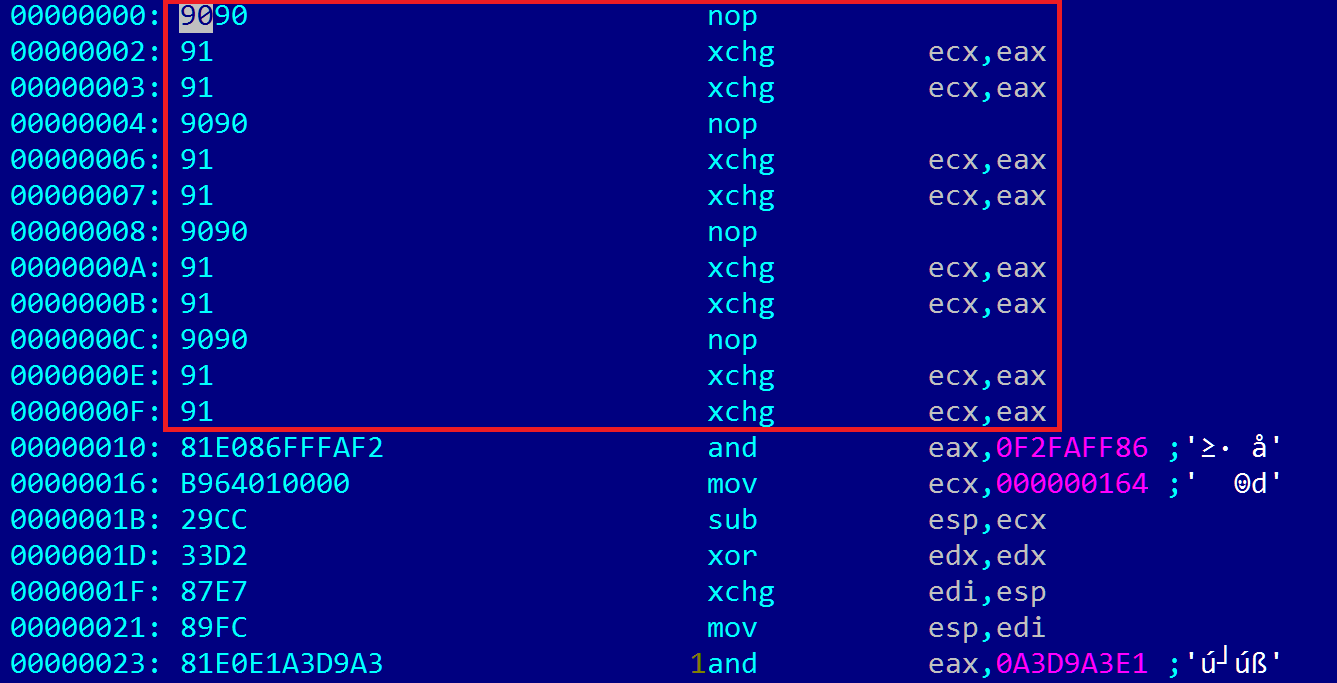 NOP sled composed of 0x90 and 0x91 opcodes
NOP sled composed of 0x90 and 0x91 opcodes
The main purpose of the initial shellcode is to download second stage shellcode from hxxp://89.45.67[.]107/rss/5uzosoff0u.iaf.
The second stage shellcode will then perform the following actions:
- Download the final payload (FinSpy) from hxxp://89.45.67[.]107/rss/mo.exe
- Download a lure document to display to the victim from the same IP
- Execute the payload and display the lure document
Payload – mo.exe
As mentioned earlier, the “mo.exe” payload (MD5: 4a49135d2ecc07085a8b7c5925a36c0a) is the newest version of FinSpy malware, typically sold to nation states and other law enforcement agencies to use in lawful surveillance operations. This newer variant has made it especially difficult for researchers to analyze the malware due to many added anti-analysis techniques, to include a custom packer and virtual machine to execute code.
The PCODE of the virtual machine is packed with the aplib packer.
After unpacking, the PCODE it will look like the following:
After unpacking the virtual machine PCODE is then decrypted:
The custom virtual machine supports a total of 34 instructions:
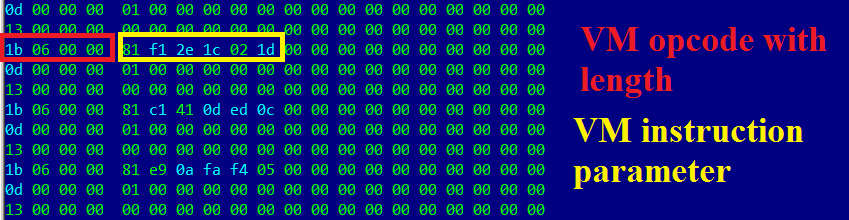
In this example, the “1b” instruction is responsible for executing native code that is specified in parameter field.
Once the payload is successfully executed, it will proceed to copy files to the following locations:
- C:\ProgramData\ManagerApp\AdapterTroubleshooter.exe
- C:\ProgramData\ManagerApp\15b937.cab
- C:\ProgramData\ManagerApp\install.cab
- C:\ProgramData\ManagerApp\msvcr90.dll
- C:\ProgramData\ManagerApp\d3d9.dll
The “AdapterTroubleshooter.exe” file is a legitimate binary which is leveraged to use the famous DLL search order hijacking technique. The “d3d9.dll” file is malicious and is loaded into memory by the legit binary upon execution. Once loaded, the DLL will then inject FinSpy into the Winlogon process.
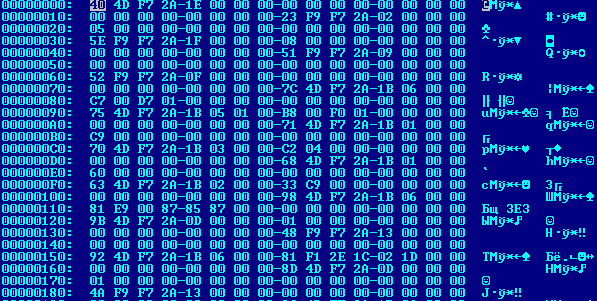
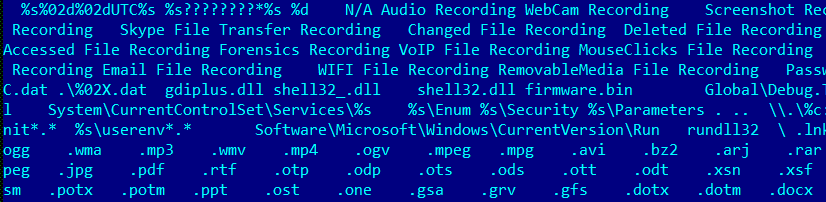 Part of injected code in winlogon process
Part of injected code in winlogon process
The payload calls out to three C2 servers for further control and exfiltration of data. We have observed two of them used in the past with other FinSpy payloads. Most recently one of these C2 servers was used together with CVE-2017-8759 in the attacks reported by FireEye in September 2017. These IPs and other previous samples tie closely to the BlackOasis APT cluster of FinSpy activity.
Targeting and Victims
BlackOasis’ interests span a wide gamut of figures involved in Middle Eastern politics and verticals disproportionately relevant to the region. This includes prominent figures in the United Nations, opposition bloggers and activists, and regional news correspondents. During 2016, we observed a heavy interest in Angola, exemplified by lure documents indicating targets with suspected ties to oil, money laundering, and other illicit activities. There is also an interest in international activists and think tanks.
Victims of BlackOasis have been observed in the following countries: Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, Netherlands, Bahrain, United Kingdom and Angola.
Conclusions
We estimate that the attack on HackingTeam in mid-2015 left a gap on the market for surveillance tools, which is now being filled by other companies. One of these is FinFisher with their suite of tools.
We believe the number of attacks relying on FinFisher software, supported by zero day exploits such as the ones described here will continue to grow.
What does it mean for everyone and how to defend against such attacks, including zero-day exploits?
For CVE-2017-11292 and other similar vulnerabilities, one can use the killbit for Flash within their organizations to disable it in any applications that respect it. Unfortunately, doing this system-wide is not easily done, as Flash objects can be loaded in applications that potentially do not follow the killbit. Additionally, this may break any other necessary resources that rely on Flash and of course, it will not protect against exploits for other third party software.
Deploying a multi-layered approach including access policies, anti-virus, network monitoring and allowlisting can help ensure customers are protected against threats such as this. Users of Kaspersky products are protected as well against this threat by one of the following detections:
- PDM:Exploit.Win32.Generic
- HEUR:Exploit.SWF.Generic
- HEUR:Exploit.MSOffice.Generic
More information about BlackOasis APT is available to customers of Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
Acknowledgements
We would like to thank the Adobe Product Security Incident Response Team (PSIRT) for working with us to identify and patch this vulnerability.
References
Indicators of compromise
4a49135d2ecc07085a8b7c5925a36c0a
89.45.67[.]107
BlackOasis APT and new targeted attacks leveraging zero-day exploit






















Ryan
Does EMET block the flash exploit?
Faron Faulk
fixed
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV170018
eyal
office sample hash?