
- Financial cyber threats in 2013. Part 1: phishing
- Financial cyber threats in 2013. Part 2: malware
Introduction: Money and risks in a multi-device world
It has been quite a few years since cybercriminals started actively stealing money from user accounts at online stores, e-payment systems and online banking systems. However, for much of that time the financial fraudsters’ sphere of activity was restricted by a number of factors, in particular the relatively limited scope of electronic payment tools.
In recent years, electronic money has been growing in importance. The convenience and universal accessibility of electronic payment systems and online banking services attract huge numbers of users, and in many countries banks and financial institutions are seriously considering the complete discontinuation of cash flow in favor of cash-free payments. A 2013 survey conducted by B2B International in cooperation with Kaspersky Lab also demonstrates the growing popularity of digital payments: 98% of those polled say they regularly use online banking or payment systems, or shop online.
This increasing popularity of cash-free transactions is accompanied by growing numbers of devices on which financial transactions can be made. As demonstrated by the same survey, PCs and laptops are still the “main” devices from which users access financial services: 87% of respondents said they conduct operations involving electronic money using a desktop or laptop computer. However, the share of mobile devices used for the same purposes is substantial: 22% and 27% of those polled respectively use tablets or smartphones for some financial operations.
Of course, these trends attracted unwanted attention. The dramatic growth in the number of users of all types of payment systems has attracted cybercriminals, and they are investing ever-growing resources into fraud schemes with which they can first gain access to users’ financial data and then to their actual money. Although financial attacks are among the most complicated and expensive types of attacks, they are also highly lucrative because, once successful, they provide direct access to the victims’ money. Once an online banking account is accessed, all that remains is to take the money and cash it in, whereas a malware writer or the owner of a botnet designed to launch DDoS attacks or send spam still has to find clients to buy their services.
For over 16 years, Kaspersky Lab has developed tools to protect against all types of cyber attacks, including financial attacks. The development of such technologies is impossible without routine detailed analysis of new malware samples, social engineering methods and other tools used by cybercriminals involved in financial fraud. One of the most general conclusions that can be drawn from this analysis is that, unlike many other types of attacks, financial malware attacks typically incorporate a highly diverse set of instruments – from phishing pages imitating the legitimate websites of financial institutions, to exploiting vulnerabilities in popular software and the writing of customized malicious programs.
Since financial cyber attacks are complex, an analysis of how they impact user security requires a comprehensive approach. That’s why when preparing this report, Kaspersky Lab’s experts considered Windows threats alongside threats targeting OS X and Android; “specialized” malware as well as other programs that are potentially capable of stealing financial data; and not only the spread of dangerous Trojans but also phishing attacks that can be an effective tool to coax valuable financial data from unwary users. In Kaspersky Lab’s view, this comprehensive approach is the only way to achieve the goal of this study, which was to give the broadest possible picture of the cyber-threat landscape aimed at online finances, and to attempt to evaluate the magnitude of the danger that such cyber threats pose.
Methodology of the report
The study used de-personalized data obtained from Kaspersky Security Network. The Kaspersky Security Network is a globally distributed cloud-based infrastructure designed for the real-time processing of data about threats that Kaspersky Lab users encounter. Kaspersky Security Network was created to ensure that information about the most recent threats is delivered to Kaspersky Lab product users as quickly as possible. With this network, an information for a new threat is added to databases within minutes of a previously unknown threat being discovered. KSN’s other function is to collect depersonalized statistics about threats which land on user computers. It is each user’s voluntary decision to provide their information to KSN. Data received in this way was used as the basis for this report.
The researchers studied data about the number of times Kaspersky Lab components successfully protected against phishing (under Microsoft Windows and Apple OS X), malware (under Windows) and mobile malware (under Google Android). In addition it looked at statistics about the number of users attacked. The research also analyzes information about the geographic spread of the attacks and their intensity.
The research covers the entire year of 2013; the data is analyzed in comparison to the equivalent data collected in 2012. The main subject of the research is the targets of phishing campaigns: the number of blocked attempts to download fake sites of payment systems, online banking systems, online stores and other targets associated with financial institutions. In addition, Kaspersky Lab’s experts selected a few dozen malware samples created specifically to steal financial data, and analyzed how frequently they were observed “in the wild” during the research period.
As the crypto-currency Bitcoin became extremely popular in 2013, Kaspersky Lab’s experts separated threats associated with the generation and stealing of this currency into a separate category, and followed their evolution.
Main findings
According to the information collected from the protection sub-systems of Kaspersky Lab products, 2013 saw a dramatic increase in the number of finance-related attacks.
Below are the main findings of the research:
- 31.45% of all phishing attacks in 2013 targeted financial institutions
- 22.2% of all attacks involved fake bank websites; the share of banking phishing doubled compared with 2012.
- 59.5% of banking phishing attacks exploited the names of just 25 international banks. The rest of the attacks used the names of 1000+ other banks.
- 38.92% of all instances that required intervention by Kaspersky security technologies on Mac computers were triggered by “financial” phishing sites.
Further on in the research text, we will discuss in more detail how attacks develop over time, look at their geographical distribution, and see the lists of their targets.
Phishing threats
Phishing, or creating fake copies of sites to obtain confidential user data, is a very common cyber threat. This is largely due to the fact that to deploy the simplest phishing campaign, cybercriminals do not need to have specific programming knowledge – it’s enough to have certain skills in creating web pages. The main purpose of phishing is to convince the victims they are visiting a real site, not a fake one. These attempts are often successful so phishing campaigns are used both as the main tool to obtain sensitive user information and as part of a complex attack to lure users to a site from which malware will be downloaded on to their device.
According to our study, phishing pages are frequently used in cyber attacks aimed at stealing user financial data. However, before proceeding to the detailed analysis of these attacks it would be helpful to present the general picture of phishing threats in 2013.
Attacks and users
Kaspersky Lab protection products have four sub-systems to combat phishing attacks. Phishing databases (similar to the malicious file signature databases) are stored on user devices and contain a list of the most common phishing links active when the database was released. The second sub-system is an anti-phishing cloud database that Kaspersky Lab protection products consult if a user notices a suspicious link that has not yet been included in the local anti-phishing database. The cloud database is updated faster than the local ones and is designed to detect the very latest phishing attacks.
Kaspersky Lab products also integrate two automatic systems for detecting phishing links and pages: Mail anti-phishing and Web anti-phishing. Mail anti-phishing monitors the links in users’ emails if they work with one of the popular email clients (Microsoft Outlook, etc.). Web anti-phishing checks everything that appears in the users’ browsers, utilizing a set of heuristic rules, and is capable of detecting new phishing pages even if there is no information about them in any database.
For this report, Kaspersky Lab used just the data obtained from Web anti-phishing because this is generally only called upon when information about a new phishing page is missing from Kaspersky Lab’s databases. Moreover, it makes it possible to determine the target of the phishing attack.
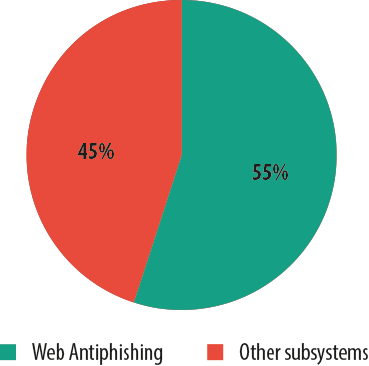
Web anti-phishing share in overall number of detects in 2013
According to Kaspersky Lab, in 2013 about 39.6 million users faced phishing attacks, an increase of 2.32% from 2012.
Over 600 million notifications about the phishing links and pages encountered by our users arrived from all four Kaspersky Lab anti-phishing sub-systems. In 2012 this figure was almost the same. At the same time the number of attacks blocked by heuristic Web anti-phishing increased by 22.2% over the same period – from 270 million in 2012 to about 330 million in 2013. This may be due to the constant improvements made to the heuristic detection system.
Geography of attacks
In 2013, the majority of phishing attacks blocked by Kaspersky Lab (30.8%) targeted users in the USA. Second came Russia (11.2%) followed by Germany (9.32%).
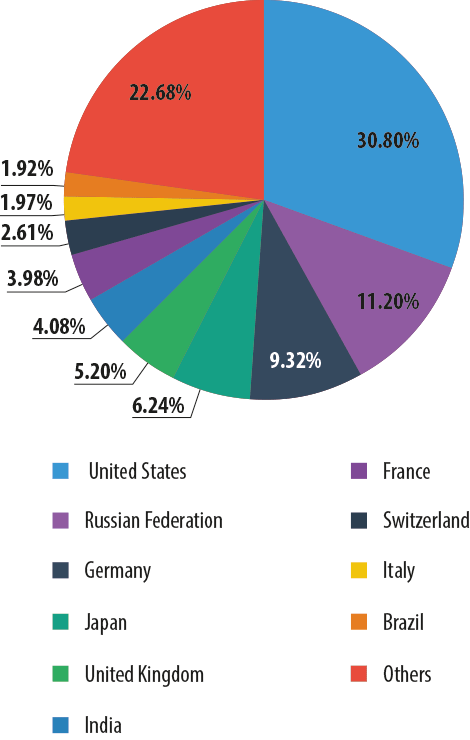
Most frequently attacked countries in 2013
Here and below, the data is provided by Kaspersky Security Network.
Compared to the previous year, in 2013 the list of the most frequently attacked countries saw significant changes. For example, the share of attacks on Russian users declined by 9.19 percentage points while the percentage of attacks on users in the USA increased considerably – from 17.56% in 2012 to 30.8% in 2013. The proportion of attacks on German users also grew by 3.49 pp, from 5.83% to 9.32%.
There could be several reasons for this geographical distribution. We have already seen a reduction in the amount of attacks in some countries and increases in other countries. The decline might be the result of such factors as enhancing measures to combat cybercrime, more complex domain name registration procedures, etc. The growth may be triggered by a “natural” increase in the total number of Internet users and individual Web resources: social networking sites, Internet stores, etc. The more often people download web pages, the more likely they are to encounter phishing pages.
Targets
As seen from the chart below, the majority of attacks in 2013 mimicked social networking sites – about 35.4%. Financial and phishing targets – fake banking sites, payment systems and online stores – accounted for 31.45%. Mail services came third with 23.3% of attacks.
Noticeably, in comparison with 2012, the distribution of targets by type changed significantly in 2013. The share of attacks using fake social networking pages increased by 6.79 pp and reached 35.39%, while the percentage of financial attacks grew by 8.5 pp and accounted for 31.45%. At the same time, the proportion of attacks exploiting fake websites of mail services decreased by 10.5 pp to 23.3% and online games dropped from 3.14% in 2012 to 2.33% in 2013.
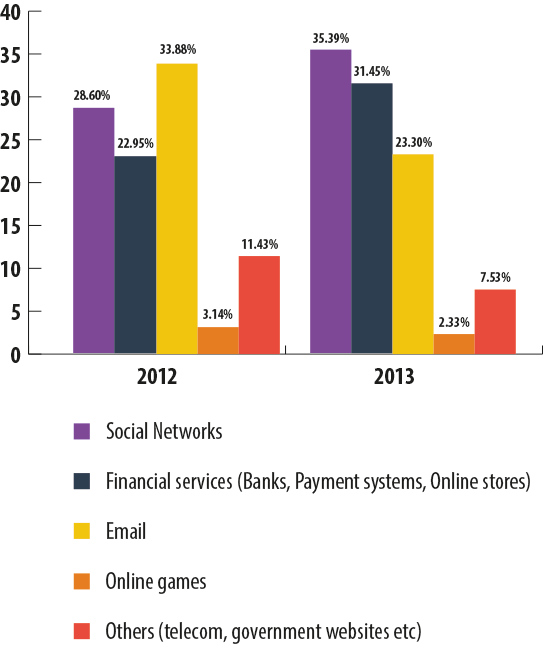
Phishing targets in 2012 and 2013
Financial attacks demonstrated the most notable growth in 2013 compared to 2012, which gives rise to a more detailed analysis of the dynamics of such attacks.
Financial attacks: worrying trend
In 2012, 22.95% of all phishing attacks targeted financial services of one kind or another: 11.92% of all attacks were performed using fake bank and online banking sites, 5.66% targeted online stores, and 5.37% targeted payment system sites.
However, in 2013 the distribution of attacks within the ‘Online Finance’ category changed dramatically. The percentage of phishing targeting banks almost doubled and reached 22.2%. The share of online stores increased insignificantly – from 5.66% to 6.51% – while the proportion of payment systems dropped by 2.63 pp. The conclusion here is obvious: the attackers are increasingly focusing on bank web services and this is one of the strongest trends in the area of phishing threats.
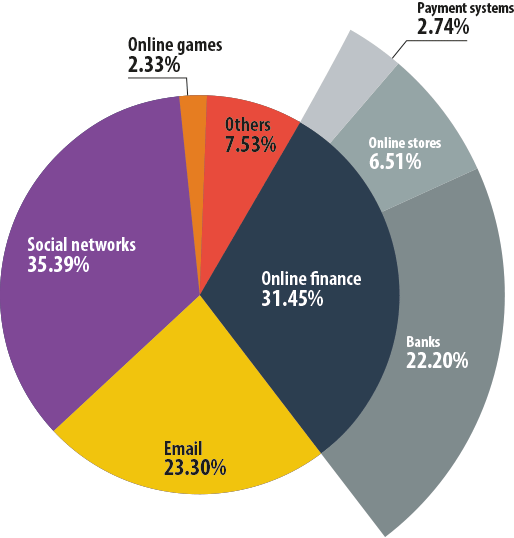
Financial phishing targets in 2013
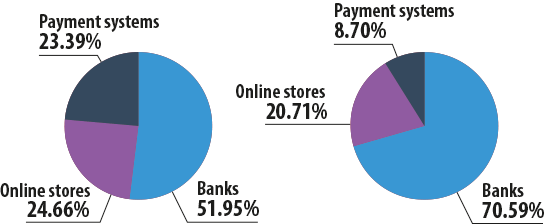
The trend is even more clear-cut when financial phishing is separated from the other categories. In 2013, fake bank pages made up 70.59% of all Kaspersky Lab Web anti-phishing detections in the Online Finance category, but one year earlier the share of bank phishing was only 51.95%.
The percentage of attacks on online stores decreased from 24.66% in 2012 to 20.71% in 2013 while the proportion of attacks on payment systems fell from 23.39% to 8.7%.
Financial phishing only in 2012 | Financial phishing only in 2013
A closer look at financial phishing targets
Banks
Although Kaspersky Lab anti-phishing databases contain more than a thousand names of banks that have been attacked or are at risk of being attacked due to their popularity, the vast majority of all phishing attacks using fake bank pages exploited the names of just 25 organizations.
In 2013, these 25 banks attracted about 59.5% of all “bank” attacks. However, most of these organizations are the largest international banking brands, operating in dozens of countries worldwide. Widespread brand recognition is one of the main tools of the phishers: the more popular the brand, the easier it is for cybercriminals to use its name to lure users to a fake website.
Payment systems
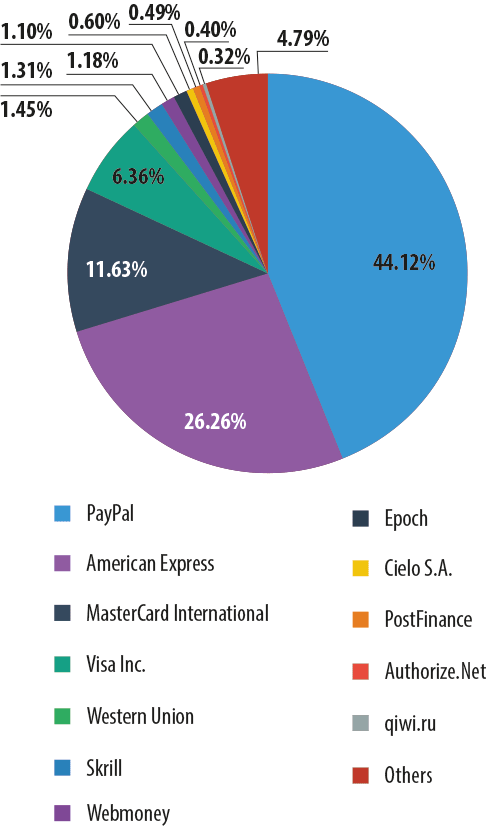
As with attacks on banks, the distribution of attacks on payment systems largely depends on brand awareness – almost 90% of phishing attacks in this category fell on one of five international brands: PayPal, American Express, MasterCard International, Visa or Western Union.
Attacks against payment systems in 2013
PayPal, being an extremely popular system for making online payments, is equally popular with hackers – the amount of attacks on this system reached 44.12%.
fin-threats-2013-p1-10s An example of a phishing page imitating the PayPal website
A significant proportion of attacks imitated American Express – 26.26%. MasterCard International and Visa Inc. pages are targeted much less often: these systems accounted for 11.63% and 6.36% of attacks respectively.
An example of a phishing page imitating the Visa website
Online shops
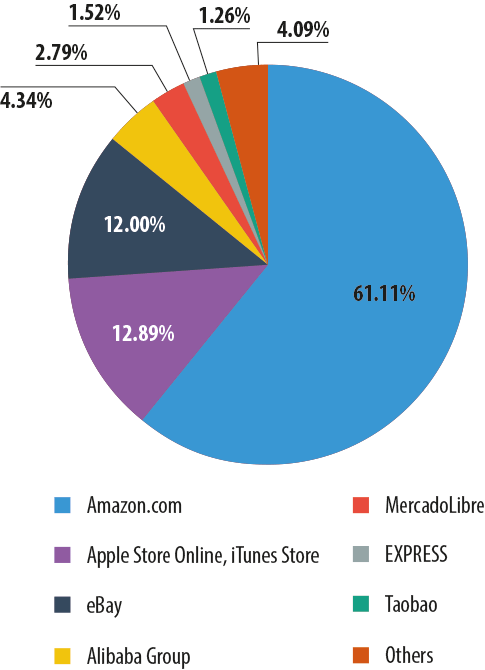
For several years in a row Amazon.com (61.11% in 2013) has been the most popular cover for phishing attacks in the Online Stores category.
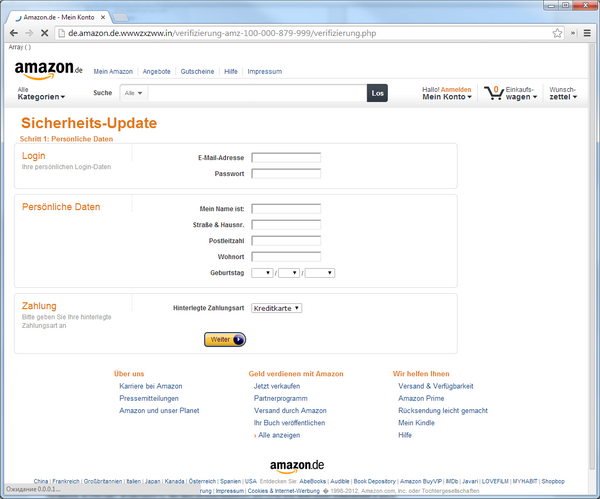
An example of a fake Amazon page targeting users in Germany
As the world’s largest online store, offering a wide range of goods, Amazon is familiar to many users. Therefore, it is popular with fraudsters who create fake pages.
A significant proportion of attacks (12.89%) use the Apple brand name. Generally, the attackers try to imitate the pages of online stores selling Apple devices as well as App Store and iTunes Store.
Attacks against online shops in 2013
Among the traditional phisher targets is the Internet auction site eBay (12%), and the Chinese online store Alibaba (4.34%) is becoming increasingly attractive for scammers. In 2013 it was joined by another Chinese online store – Taobao (1.26%). Almost 3% of all attacks on online stores fell on MercadoLibre.com, a South American version of eBay. The diagram above illustrates the “international” character of financial phishing. As can be seen, the victims of attacks are not only English-speaking users but also people who speak Chinese, Spanish, Portuguese, and several other languages.
Deeper into the dynamics of attacks
The professional and marketing activities of the companies that are exploited in phishing schemes also affects the number of attacks.
This trend can be illustrated by the graph of attacks which exploited the Apple brand name.
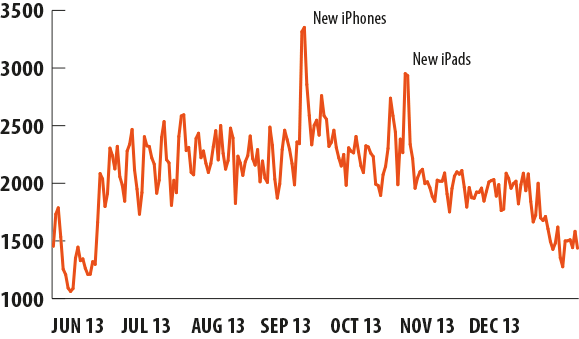
Attacks exploiting the Apple brand name in the 2nd half of 2013
Over the year, the dynamics of Kaspersky Lab security technology detections of threats that exploit Apple’s trademark had been a series of peaks and troughs ranging from 1 to 2,500 operations per day. However, as seen from the chart above, there were two noticeable peaks which coincided with the date iPhone 5s and 5c were announced on 10 September 2013 and the announcement of iPad Air and iPad Mini with retina-display on 22 October 2013.
The logic in this case is clear: Apple devices are always a hot topic for news and discussion on the Internet, particularly when a new product is about to be released. For the fraudsters, using “hot” keywords is the usual way of attracting audiences to fake sites and, as the graph shows, this method works.
Apple is not the only phisher target that shows a correlation between the number of attacks and the company’s activities. Natural disasters and high-profile international events attract active coverage and discussion in the media and on the Internet, giving rise to the emergence of so-called thematic phishing and spam. Similarly, large-scale marketing campaigns held by a bank, an e-store or other commercial or financial organizations may become a pretext for phishing.
The logical conclusion for banks, payment systems and other financial institutions regularly conducting online marketing activities is simple: when initiating an advertising campaign to attract new business, don’t forget to warn customers about potential cyber threats.
Phishing against OS X: first signs of a growing threat
The number of malicious attacks on the owners of computers running OS X has always been significantly lower than the number of attacks on Windows users. This can be easily explained: although Apple actively promotes its Mac computers and laptops all over the world, the number of users of these devices is a long way short of the number of computers running under Windows. Since criminals are keen to maximize their profits, they naturally pay more attention to Windows users. However, this statement is only valid when it comes to malware. The attacker does not need to do anything special to attack a Mac user via phishing: although Windows and OS X have fundamental differences which make it impossible to write “universal” malicious programs for both platforms, the users of both PCs and Mac download the same web pages and phishing threats which spread with the help of social engineering techniques are as dangerous for Mac users as they are for Windows users. The results of Kaspersky Lab’s study confirm this fact.
However, it should be noted here that for technical reasons Kaspersky Lab only became capable of collecting relevant statistics from Mac users in November 2013 and all Mac-related information in this study was harvested in November and December 2013. Although the observation period is short, the data obtained provides some insight into the landscape of threats jeopardizing OS X users and helps to define differences compared with the overall picture.
In 2013, 7.8% of Kaspersky Lab anti-phishing detections protected Mac computers. Almost half of these attacks targeted US users (47.55%); 11.53% of attacks were registered in Germany and 5.47% in the UK. The list of the most frequently attacked countries also included Sweden and Australia.
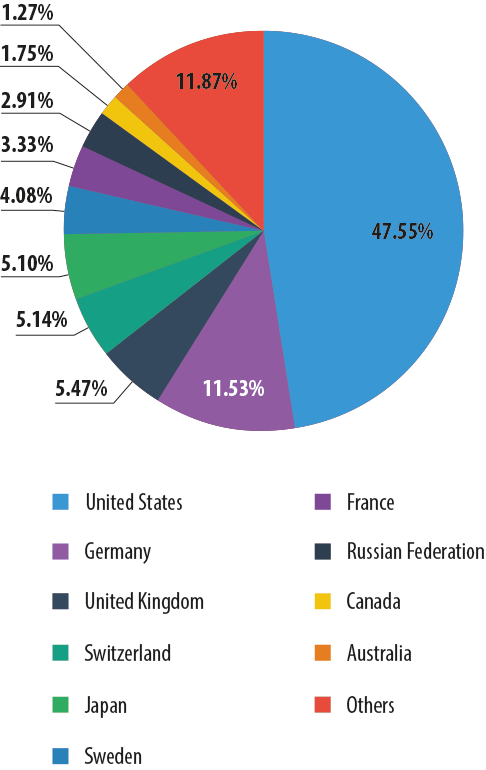
Most frequently attacked countries: Mac users
The differences in the distribution of attacks by country can be explained by the relative use of Apple computers in these countries. Traditionally, the USA and the developed European countries are the largest markets for Apple devices.
Mac owners faced phishing attacks as often as the users of computers running Windows, but their chances of becoming a victim of a financial attack are even greater.
Over the reporting period, about 38.92% of all Kaspersky Lab anti-phishing detections on Apple computers involved “financial” phishing pages. That is almost 7.5 percentage points more than the “financial” share of the total volume of attacks. 29.86% of the total number of attacks occurred when users were trying to enter fake bank sites; online stores and auctions accounted for 6.6%, while payment systems accounted for 2.46% of all anti-phishing detections.
That was the view Kaspersky Lab’s experts took on financial phishing in the year 2013. Although phishing is a fairly common threat, when it comes to financial cybercrime it forms a relatively small part of the overall landscape of financial cyber threats. The key role here is played by financial malware, dangerous software capable of obtaining user details to access online accounts and steal the victim’s money. This will be discussed in the next part of the Kaspersky Lab report.
To be continued…
























Financial Cyber Threats in 2013. Part 1: Phishing