
Vulnerability registrations in Q2 2025 proved to be quite dynamic. Vulnerabilities that were published impact the security of nearly every computer subsystem: UEFI, drivers, operating systems, browsers, as well as user and web applications. Based on our analysis, threat actors continue to leverage vulnerabilities in real-world attacks as a means of gaining access to user systems, just like in previous periods.
This report also describes known vulnerabilities used with popular C2 frameworks during the first half of 2025.
Statistics on registered vulnerabilities
This section contains statistics on assigned CVE IDs. The data is taken from cve.org.
Let’s look at the number of CVEs registered each month over the last five years.
Total vulnerabilities published each month from 2021 to 2025 (download)
This chart shows the total volume of vulnerabilities that go through the publication process. The number of registered vulnerabilities is clearly growing year-on-year, both as a total and for each individual month. For example, around 2,600 vulnerabilities were registered as of the beginning of 2024, whereas in January 2025, the figure exceeded 4,000. This upward trend was observed every month except May 2025. However, it’s worth noting that the registry may include vulnerabilities with identifiers from previous years; for instance, a vulnerability labeled CVE-2024-N might be published in 2025.
We also examined the number of vulnerabilities assigned a “Critical” severity level (CVSS > 8.9) during the same period.
Total number of critical vulnerabilities published each month from 2021 to 2025 (download)
The data for the first two quarters of 2025 shows a significant increase when compared to previous years. Unfortunately, it’s impossible to definitively state that the total number of registered critical vulnerabilities is growing, as some security issues aren’t assigned a CVSS score. However, we’re seeing that critical vulnerabilities are increasingly receiving detailed descriptions and publications – something that should benefit the overall state of software security.
Exploitation statistics
This section presents statistics on vulnerability exploitation for Q2 2025. The data draws on open sources and our telemetry.
Windows and Linux vulnerability exploitation
In Q2 2025, as before, the most common exploits targeted vulnerable Microsoft Office products that contained unpatched security flaws.
Kaspersky solutions detected the most exploits on the Windows platform for the following vulnerabilities:
- CVE-2018-0802: a remote code execution vulnerability in the Equation Editor component
- CVE-2017-11882: another remote code execution vulnerability, also affecting Equation Editor
- CVE-2017-0199: a vulnerability in Microsoft Office and WordPad allowing an attacker to gain control over the system
These vulnerabilities are traditionally exploited by threat actors more often than others, as we’ve detailed in previous reports. These are followed by equally popular issues in WinRAR and exploits for stealing NetNTLM credentials in the Windows operating system:
- CVE-2023-38831: a vulnerability in WinRAR involving improper handling of files within archive contents
- CVE-2025-24071: a Windows File Explorer vulnerability that allows for the retrieval of NetNTLM credentials when opening specific file types (
.library-ms) - CVE-2024-35250: a vulnerability in the
ks.sysdriver that allows arbitrary code execution
Dynamics of the number of Windows users encountering exploits, Q1 2024 — Q2 2025. The number of users who encountered exploits in Q1 2024 is taken as 100% (download)
All of the vulnerabilities listed above can be used for both initial access to vulnerable systems and privilege escalation. We recommend promptly installing updates for the relevant software.
For the Linux operating system, exploits for the following vulnerabilities were detected most frequently:
- CVE-2022-0847, also known as Dirty Pipe: a widespread vulnerability that allows privilege escalation and enables attackers to take control of running applications
- CVE-2019-13272: a vulnerability caused by improper handling of privilege inheritance, which can be exploited to achieve privilege escalation
- CVE-2021-22555: a heap overflow vulnerability in the Netfilter kernel subsystem. The widespread exploitation of this vulnerability is due to the fact that it employs popular memory modification techniques: manipulating
msg_msgprimitives, which leads to a Use-After-Free security flaw.
Dynamics of the number of Linux users encountering exploits, Q1 2024 — Q2 2025. The number of users who encountered exploits in Q1 2024 is taken as 100% (download)
It’s critically important to install security patches for the Linux operating system, as it’s attracting more and more attention from threat actors each year – primarily due to the growing number of user devices running Linux.
Most common published exploits
In Q2 2025, we observed that the distribution of published exploits by software type continued the trends from last year. Exploits targeting operating system vulnerabilities continue to predominate over those targeting other software types that we track as part of our monitoring of public research, news, and PoCs.
Distribution of published exploits by platform, Q1 2025 (download)
Distribution of published exploits by platform, Q2 2025 (download)
In Q2, no public information about new exploits for Microsoft Office systems appeared.
Vulnerability exploitation in APT attacks
We analyzed data on vulnerabilities that were exploited in APT attacks during Q2 2025. The following rankings are informed by our telemetry, research, and open-source data.
TOP 10 vulnerabilities exploited in APT attacks, Q2 2025 (download)
The Q2 TOP 10 list primarily draws from the large number of incidents described in public sources. It includes both new security issues exploited in zero-day attacks and vulnerabilities that have been known for quite some time. The most frequently exploited vulnerable software includes remote access and document editing tools, as well as logging subsystems. Interestingly, low-code/no-code development tools were at the top of the list, and a vulnerability in a framework for creating AI-powered applications appeared in the TOP 10. This suggests that the evolution of software development technology is attracting the attention of attackers who exploit vulnerabilities in new and increasingly popular tools. It’s also noteworthy that the web vulnerabilities were found not in AI-generated code but in the code that supported the AI framework itself.
Judging by the vulnerabilities identified, the attackers’ primary goals were to gain system access and escalate privileges.
C2 frameworks
In this section, we’ll look at the most popular C2 frameworks used by threat actors and analyze the vulnerabilities whose exploits interacted with C2 agents in APT attacks.
The chart below shows the frequency of known C2 framework usage in attacks on users during the first half of 2025, according to open sources.
TOP 13 C2 frameworks used by APT groups to compromise user systems in Q1–Q2 2025 (download)
The four most frequently used frameworks – Sliver, Metasploit, Havoc, and Brute Ratel C4 – can work with exploits “out of the box” because their agents provide a variety of post-compromise capabilities. These capabilities include reconnaissance, command execution, and maintaining C2 communication. It should be noted that the default implementation of Metasploit has built-in support for exploits that attackers use for initial access. The other three frameworks, in their standard configurations, only support privilege escalation and persistence exploits in a compromised system and require additional customization tailored to the attackers’ objectives. The remaining tools don’t work with exploits directly and were modified for specific exploits in real-world attacks. We can therefore conclude that attackers are increasingly customizing their C2 agents to automate malicious activities and hinder detection.
After reviewing open sources and analyzing malicious C2 agent samples that contained exploits, we found that the following vulnerabilities were used in APT attacks involving the C2 frameworks mentioned above:
- CVE-2025-31324: a vulnerability in SAP NetWeaver Visual Composer Metadata Uploader that allows for remote code execution and has a CVSS score of 10.0
- CVE-2024-1709: a vulnerability in ConnectWise ScreenConnect 23.9.7 that can lead to authentication bypass, also with a CVSS score of 10.0
- CVE-2024-31839: a cross-site scripting vulnerability in the CHAOS v5.0.1 remote administration tool, leading to privilege escalation
- CVE-2024-30850: an arbitrary code execution vulnerability in CHAOS v5.0.1 that allows for authentication bypass
- CVE-2025-33053: a vulnerability caused by improper handling of working directory parameters for LNK files in Windows, leading to remote code execution
Interestingly, most of the data about attacks on systems is lost by the time an investigation begins. However, the list of exploited vulnerabilities reveals various approaches to the vulnerability–C2 combination, offering insight into the attack’s progression and helping identify the initial access vector. By analyzing the exploited vulnerabilities, incident investigations can determine that, in some cases, attacks unfold immediately upon exploit execution, while in others, attackers first obtain credentials or system access and only then deploy command and control.
Interesting vulnerabilities
This section covers the most noteworthy vulnerabilities published in Q2 2025.
CVE-2025-32433: vulnerability in the SSH server, part of the Erlang/OTP framework
This remote code execution vulnerability can be considered quite straightforward. The attacker needs to send a command execution request, and the server will run it without performing any checks – even if the user is unauthenticated. The vulnerability occurs during the processing of messages transmitted via the SSH protocol when using packages for Erlang/OTP.
CVE-2025-6218: directory traversal vulnerability in WinRAR
This vulnerability is similar to the well-known CVE-2023-38831: both target WinRAR and can be exploited through user interaction with the GUI. Vulnerabilities involving archives aren’t new and are typically exploited in web applications, which often use archives as the primary format for data transfer. These archives are processed by web application libraries that may lack checks for extraction limits. Typical scenarios for exploiting such vulnerabilities include replacing standard operating system configurations and setting additional values to launch existing applications. This can lead to the execution of malicious commands, either with a delay or upon the next OS boot or application startup.
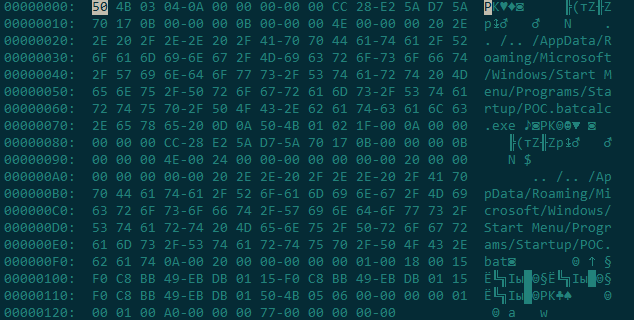
To exploit such vulnerabilities, attackers need to determine the location of the directory to modify, as each system has a unique file layout. Additionally, the process is complicated by the need to select the correct characters when specifying the extraction path. By using specific combinations of special characters, archive extraction outside of the working directory can bypass security mechanisms, which is the essence of CVE-2025-6218. A PoC for this vulnerability appeared rather quickly.
As seen in the file dump, the archive extraction path is altered not due to its complex structure, but by using a relative path without specifying a drive letter. As we mentioned above, a custom file organization on the system makes such an exploit unstable. This means attackers will have to use more sophisticated social engineering methods to attack a user.
CVE-2025-3052: insecure data access vulnerability in NVRAM, allowing bypass of UEFI signature checks
UEFI vulnerabilities almost always aim to disable the Secure Boot protocol, which is designed to protect the operating system’s boot process from rootkits and bootkits. CVE-2025-3052 is no exception.
Researchers were able to find a set of vulnerable UEFI applications in which a function located at offset 0xf7a0 uses the contents of a global non-volatile random-access memory (NVRAM) variable without validation. The vulnerable function incorrectly processes and can modify the data specified in the variable. This allows an attacker to overwrite Secure Boot settings and load any modules into the system – even those that are unsigned and haven’t been validated.
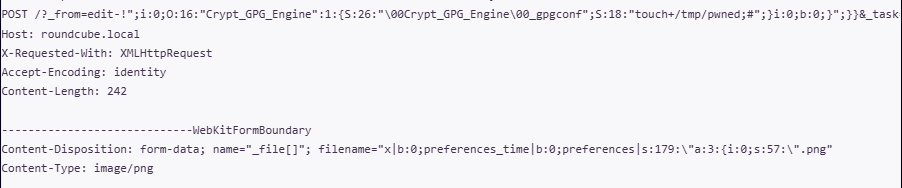
CVE-2025-49113: insecure deserialization vulnerability in Roundcube Webmail
This vulnerability highlights a classic software problem: the insecure handling of serialized objects. It can only be exploited after successful authentication, and the exploit is possible during an active user session. To carry out the attack, a malicious actor must first obtain a legitimate account and then use it to access the vulnerable code, which lies in the lack of validation for the _from parameter.
Post-authentication exploitation is quite simple: a serialized PHP object in text format is placed in the vulnerable parameter for the attack. It’s worth noting that an object injected in this way is easy to restore for subsequent analysis. For instance, in a PoC published online, the payload creates a file named “pwned” in /tmp.
According to the researcher who discovered the vulnerability, the defective code had been used in the project for 10 years.
CVE-2025-1533: stack overflow vulnerability in the AsIO3.sys driver
This vulnerability was exploitable due to an error in the design of kernel pool parameters. When implementing access rights checks for the AsIO3.sys driver, developers incorrectly calculated the amount of memory needed to store the path to the file requesting access to the driver. If a path longer than 256 characters is created, the system will crash with a “blue screen of death” (BSOD). However, in modern versions of NTFS, the path length limit is not 256 but 32,767 characters. This vulnerability demonstrates the importance of a thorough study of documentation: it not only helps to clearly understand how a particular Windows subsystem operates but also impacts development efficiency.
Conclusion and advice
The number of vulnerabilities continues to grow in 2025. In Q2, we observed a positive trend in the registration of new CVE IDs. To protect systems, it’s critical to regularly prioritize the patching of known vulnerabilities and use software capable of mitigating post-exploitation damage. Furthermore, one way to address the consequences of exploitation is to find and neutralize C2 framework agents that attackers may use on a compromised system.
To secure infrastructure, it’s necessary to continuously monitor its state, particularly by ensuring thorough perimeter monitoring.
Special attention should be paid to endpoint protection. A reliable solution for detecting and blocking malware will ensure the security of corporate devices.
Beyond basic protection, corporate infrastructures need to implement a flexible and effective system that allows for the rapid installation of security patches, as well as the configuration and automation of patch management. It’s also important to constantly track active threats and proactively implement measures to strengthen security, including mitigating risks associated with vulnerabilities. Our Kaspersky Next product line helps to detect and analyze vulnerabilities in the infrastructure in a timely manner for companies of all sizes. Moreover, these modern comprehensive solutions also combine the collection and analysis of security event data from all sources, incident response scenarios, an up-to-date database of cyberattacks, and training programs to improve the level of employees’ cybersecurity awareness.
Exploits and vulnerabilities in Q2 2025


















Sunil
Please send as attached
Securelist
Hi Sunil,
This report is only available as a webpage. You can, however, save it in the desired format, depending on your browser’s settings.
Ba Duy
I want to get the IoCs to enrich the information on the SOC
Securelist
Hi Ba,
There are no relevant IoCs for this report in particular, being a descriptive piece. However, our Threat Intelligence service provides Threat Data Feeds that can be integrated with your system. They are constantly updated with indicators of compromise and actionable context.
You can learn more here: https://www.kaspersky.com/enterprise-security/threat-data-feeds